Plan your StoreFront deployment
StoreFront integrates with your Citrix Virtual Apps and Desktops deployments, providing users with a single, self-service access point for their desktops and applications.
The figure shows a typical StoreFront deployment.
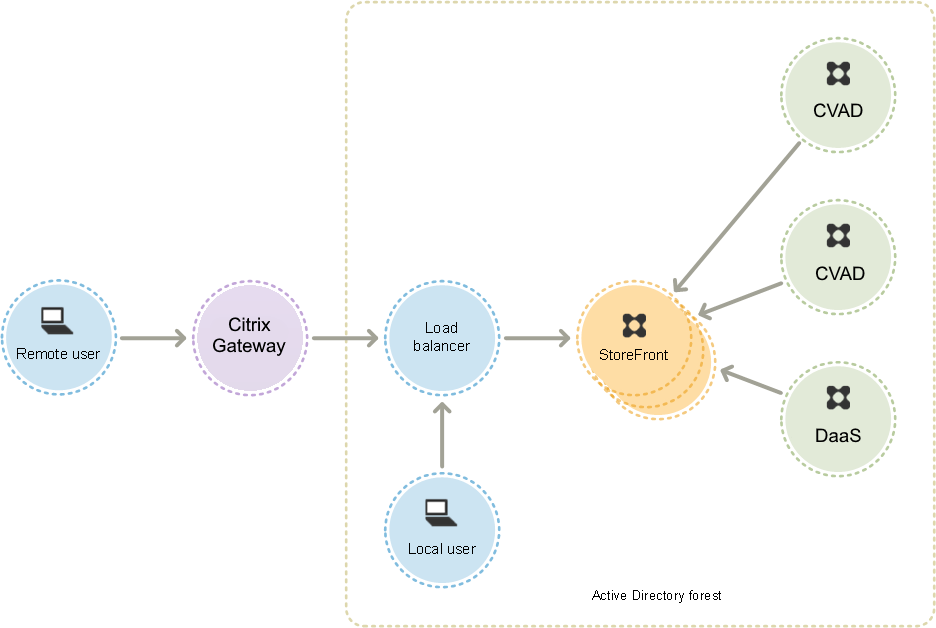
Active Directory
StoreFront uses Active Directory for authenticating users and looking up group membership and other details and for synchronizing data between StoreFront servers.
For single server deployments you can install StoreFront on a non-domain-joined server but certain functionality will be unavailable; otherwise, StoreFront servers must reside either within the Active Directory domain containing your users’ accounts or within a domain that has a trust relationship with the user accounts domain unless you enable delegation of authentication to the Citrix Virtual Apps and Desktops sites or farms. All the StoreFront servers in a group must reside within the same domain.
StoreFront Server groups
StoreFront can be configured either on a single server or as a multiple server deployment called a StoreFront server group. Server groups not only provide additional capacity, but also greater availability. StoreFront ensures that configuration information and details of users’ application subscriptions are stored on and replicated between all the servers in a server group. This means that if a StoreFront server becomes unavailable for any reason, users can continue to access their stores using the remaining servers. Meanwhile, the configuration and subscription data on the failed server are automatically updated when it reconnects to the server group. Subscription data is updated when the server comes back online but you must propagate configuration changes if any were missed by the server while offline. In the event of a hardware failure that requires replacement of the server, you can install StoreFront on a new server and add it to the existing server group. The new server is automatically configured and updated with users’ application subscriptions when it joins the server group.
Citrix® recommends a maximum of six servers in a server group. In case of more than six servers, the overhead of synchronizing data outweighs the benefit of the additional servers, and the performance is degraded.
StoreFront server group deployments are only supported where links between servers in a server group have latency of less than 40 ms (with subscriptions disabled) or less than 3 ms (with subscriptions enabled). Ideally, all servers in a server group should reside in the same location (data center, availability zone), but server groups can span locations within the same region provided that links between servers in the group meet these latency criteria. Examples include server groups spanning availability zones within a cloud region, or between metropolitan area data centers. Note that latency between zones varies by cloud provider. Citrix do not recommend spanning locations as a disaster recovery configuration, but it may be suitable for high availability.
Load balancing
For multiple servers in a StoreFront server group, you must configure external load balancing. Use a load balancer with built-in monitors and session persistency, such as Citrix ADC. For more information about load balancing with Citrix ADC, see Load Balancing.
Citrix Gateway for remote access
If you plan to enable access to StoreFront from outside the corporate network, a Citrix Gateway is required to provide secure connections for remote users. Deploy Citrix Gateway outside the corporate network, with firewalls separating Citrix Gateway from both the public and internal networks. Ensure that Citrix Gateway is able to access the Active Directory forest containing the StoreFront servers.
Global Server Load Balancer
In large Citrix deployments you may have StoreFront and NetScaler deployments in multiple data centers. Using a Global Server oad Balancer (GSLB) you can configure a single global URL which the GSLB redirects to the specific URL of a gateway in one of the regions. Typically the GSLB chooses the closest gateway based on a load balancing algorithm such as round trip time (RTT) or Static Proximity.
For example you may have 3 regional gateways:
emeagateway.example.com - Europe gateway
usgateway.example.com - US gateway
apacgateway.example.com - Asia Pacific gateway
Along with a GSLB:
gslb.example.com
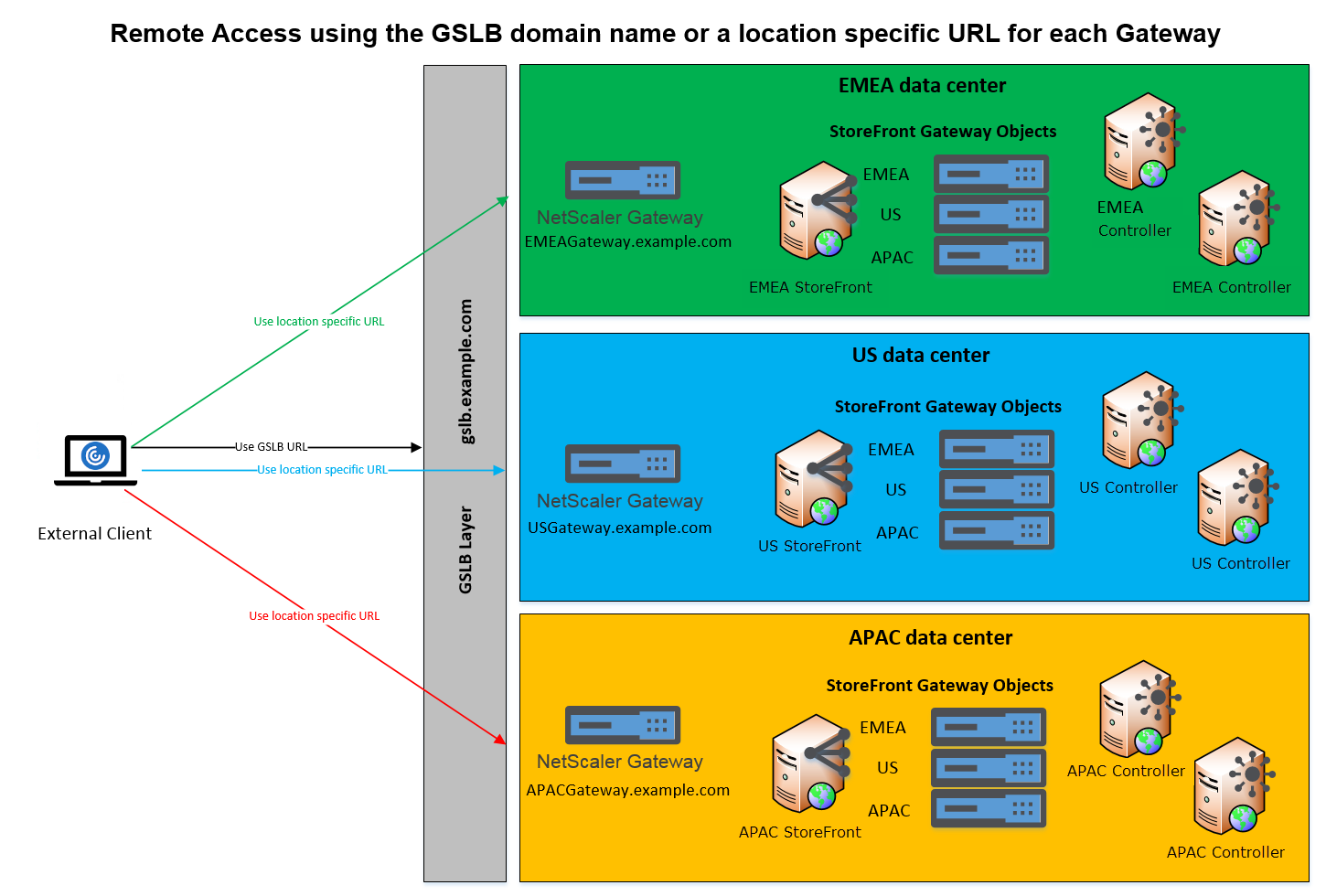
Before configuring a GSLB, review what server certificates you have in place and how your organization performs DNS resolution. Any URLs that you want to use in your Citrix Gateway and StoreFront deployment must be present in your server certificates.
StoreFront does not have any built-in mechanism to synchronize configuration between server groups; instead it is up to the administrator to ensure that each StoreFront Server Group is configured in the same way so the users get a consistent experience whichever server group they connect to.
StoreFront can periodically synchronize subscriptions (favorites) between server groups, see Subscription synchronization.
When you add a store to Citrix Workspace app, it identifies the store by base URL and store name. Therefore, if you have multiple StoreFront deployments behind a GSLB then each deployment must have the same base URL.
Note:
When Citrix Workspace app roams between different StoreFront deployments behind a GSLB, the user is required to re-authenticate. Therefore you should configure persistence so a user’s requests are always routed to the same deployment if possible.
User access
See User access options.