Scenario 1
This scenario covers how to enable App Protection for external users coming through the Access Gateway.
- Configure adaptive access based on your network location,
-
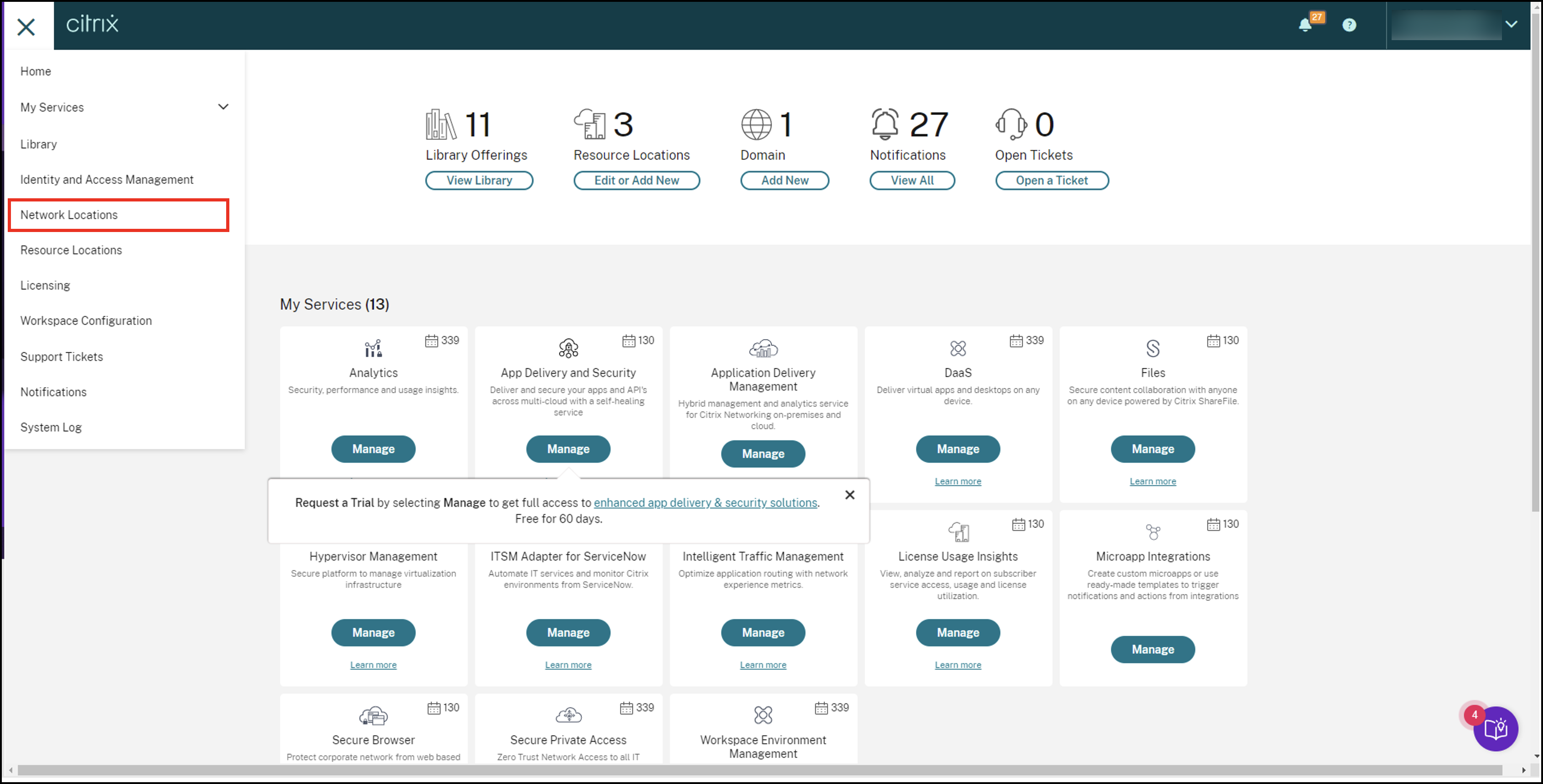
Sign in to Citrix Cloud and navigate to Network Locations.
-
Click Add Network location.
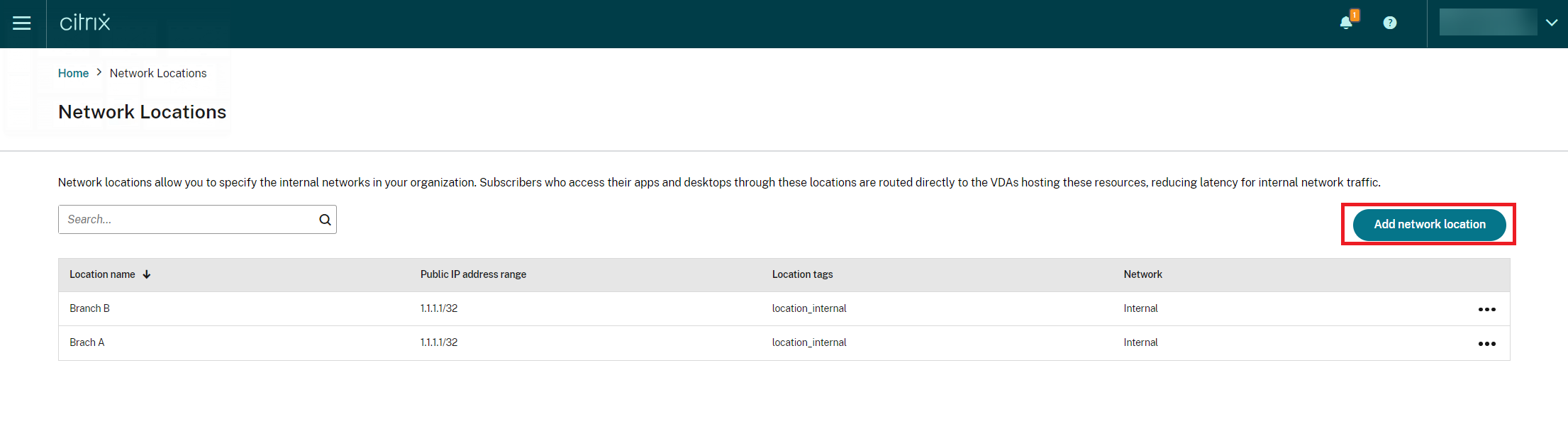
Add a Network Location screen appears.
-
In the Location name field, enter the relevant location name.
-
In the Public IP address range field, enter the network IP address or subnet that you want to consider as an internal network.
-
In the Location tags field, enter location_internal. For more information about the location tag, see Location tags.
-
Under Choose a network connectivity type, select Internal.
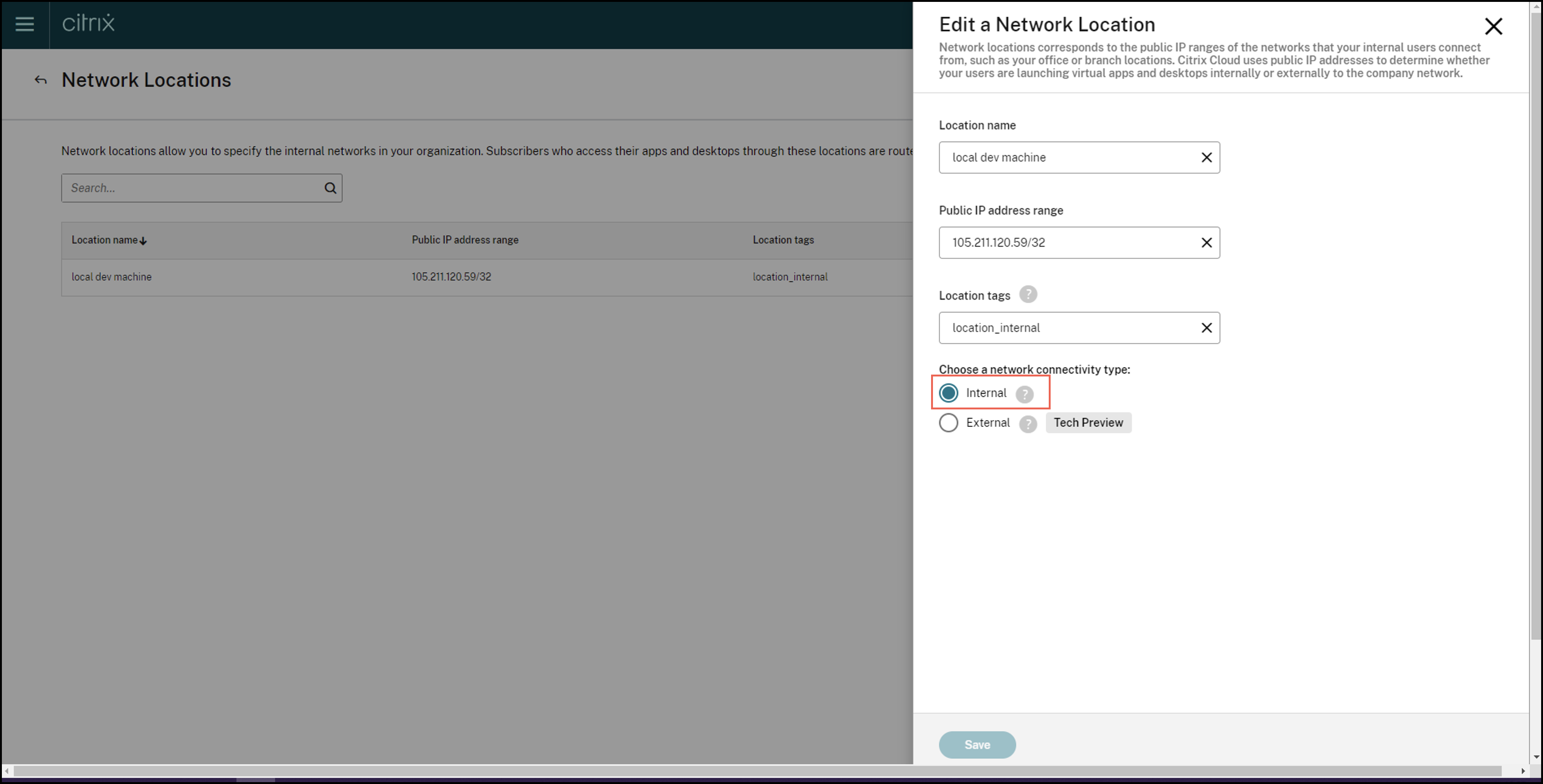
If you sign in to the Cloud store from a device whose IP address is configured as Internal under Choose a network connectivity type setting, then the connection is considered as an internal connection.
-
-
Configure Broker Access policy rules
For every delivery group, two broker access policies are created by default. One policy is for connections coming through the Access gateway, and the other policy is for direct connections. You can enable App Protection only for the connections coming through the Access gateway, which is the external connections. Use the following steps to configure the Broker Access policy rules:
-
Install the Citrix PowerShell SDK and connect to the cloud API as explained in the Citrix blog Getting started with PowerShell automation for Citrix Cloud.
-
Run the command
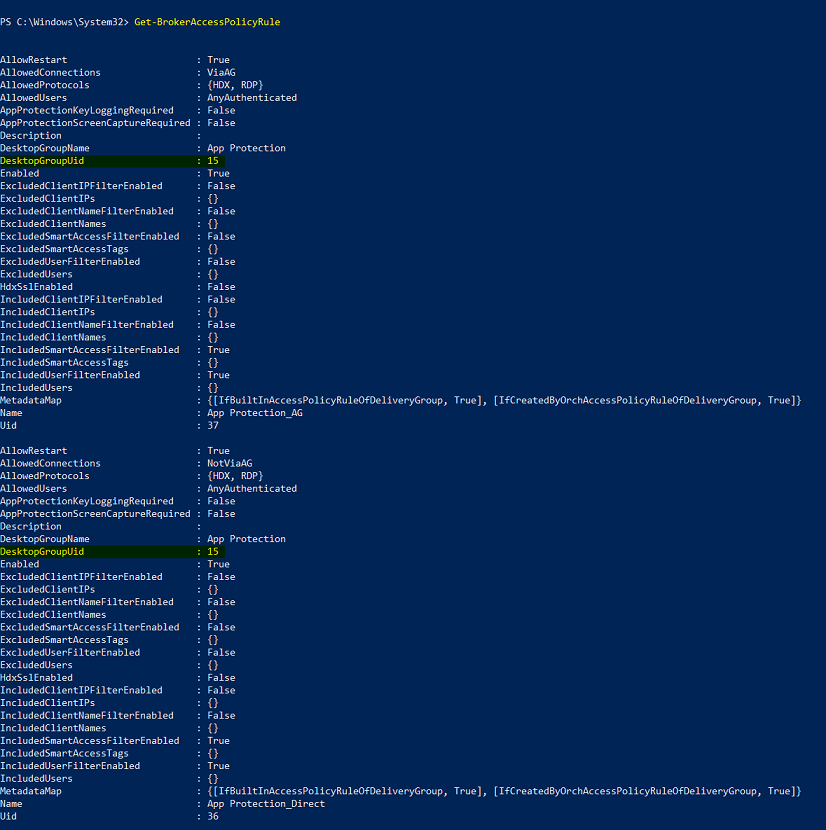
Get-BrokerAccessPolicyRule.A list of all the broker access policies for all the delivery groups that are present is displayed.
-
Find the DesktopGroupUid for the delivery group that you want to change.
-
Run the following command using the DesktopGroupUid to fetch policies applicable to the delivery group. There are at least two policies, one where AllowedConnections has ViaAG and another which has NotViaAG.
Get-BrokerAccessPolicyRule -DesktopGroupUid 15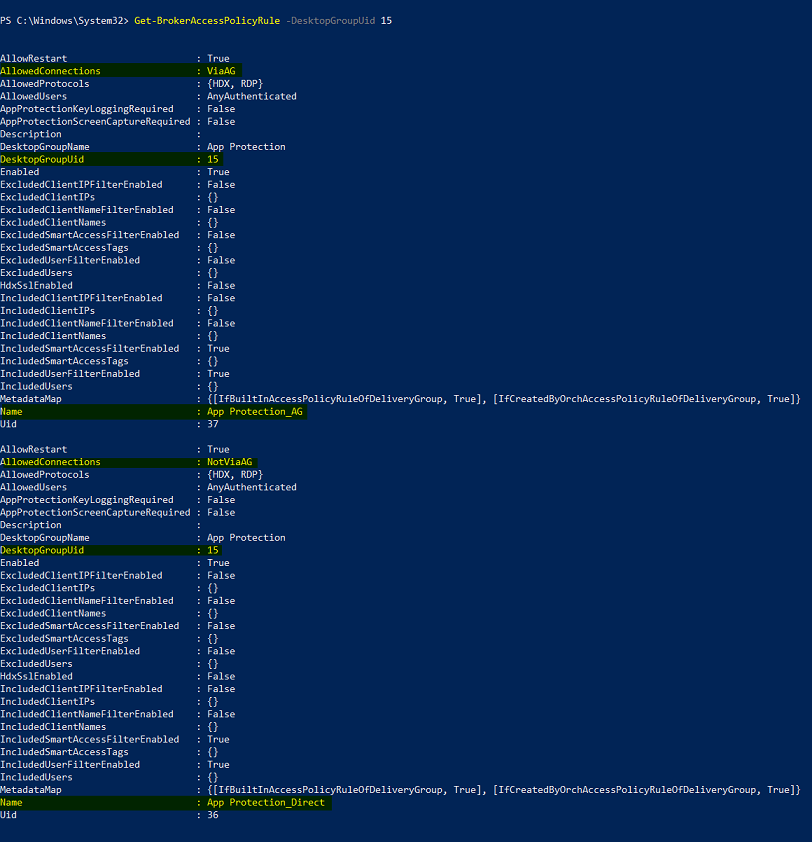
In the screenshot, you see two policies:
-
App Protection_AG - AllowedConnections with ViaAG, which is the policy for connections via the access gateway
-
App Protection_Direct – AllowedConnections with NotViaAG, which is the policy for connections not via the access gateway
-
-
-
Enable App Protection policies only for external connections and disable for internal connections using the following commands:
-
Set-BrokerAccessPolicyRule "App Protection_AG" -IncludedSmartAccessFilterEnabled $true -IncludedSmartAccessTags Workspace:LOCATION_internal -AppProtectionScreenCaptureRequired $false -AppProtectionKeyLoggingRequired $false -
New-BrokerAccessPolicyRule "App Protection_AG_Exclude" -ExcludedsmartAccessFilterEnabled $true -ExcludedSmartAccessTags Workspace:LOCATION_internal -AppProtectionScreenCaptureRequired $true -AppProtectionKeyLoggingRequired $true -DesktopGroupUid 15 -AllowedConnections ViaAG -AllowedProtocols HDX, RDP -
Remove-BrokerAccessPolicyRule "App Protection_Direct”
-
-
Verification:
Sign out of Citrix Workspace app and sign in again. Launch the protected resource from an external connection. You see that the App Protection policies are applied. Launch the same resource from an internal connection, a device from within the IP Address range configured in the first step. You see that the App Protection policies are disabled.