This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Secure HDX™
Secure HDX is an Application Level Encryption (ALE) solution that prevents any network elements in the traffic path from being able to inspect the HDX traffic. It does this by providing true End-to-End Encryption (E2EE) at the application level between the Citrix Workspace™ app (client) and the VDA (session host) using AES-256-GCM encryption.
System requirements
The following list depicts the system requirements for using Secure HDX.
- Control plane
- Citrix DaaS™
- Citrix Virtual Apps and Desktops™ 2503 or later
- Session host
- Operating System
- Windows 10 22H2
- Windows 11 22H2 or later
- Windows Server 2019 or later
- Virtual Delivery Agent (VDA)
- Windows: version 2503 or later
- Linux: version 2407 or later
- Operating System
- Workspace app
- Windows: version 2503 or later
- Linux: version 2408 or later
- Mac: version 2409 or later
- Chrome OS: version 2409 or later
- HTML5: version 2408 or later
- Android: version 2503 or later
- iOS: version 2503 or later
- Access tier
- Citrix Workspace
- Citrix StoreFront™ 2402 or later
NOTE:
Support with Citrix Virtual Apps and Desktops™ 2402 LTSR is availabe with CU3 or later.
For details on configuring Secure HDX with Linux VDA, refer to the Linux VDA documentation.
Configuration
Secure HDX is disabled by default. You can configure this feature using the Secure HDX setting in Citrix policy:
Secure HDX: Defines whether to enable or disable the feature.
IMPORTANT:
If you have Secure ICA® enabled on the delivery groups that you want to enable Secure HDX on, you must first disable Secure ICA (Edit delivery group > User Settings).
Considerations
The following are considerations for using Secure HDX:
-
If a user tries to connect to a session host with Secure HDX enabled using a client that does not support the feature, the connection will be denied.
-
Only Service Continuity for connector-less workloads is supported with Secure HDX. If you are using the standard version of Service Continuity, you will not be able to connect to any session hosts that have Secure HDX enabled if there is a Cloud service outage.
-
If you use HDX Insight, note that using Secure HDX prevents HDX Insight data collection as the NetScaler® is not able to inspect the encrypted HDX traffic. If you must use HDX Insight, you can set Secure HDX to be enabled only for direct connections.
-
If you use SmartControl, note that using Secure HDX prevents SmartControl from working as the NetScaler is unable to inspect the encrypted HDX traffic. If you must use SmartControl, you can set Secure HDX to be enabled only for direct connections.
-
Multi-Stream ICA is not supported when Secure HDX is enabled.
-
If you use any third-party solutions that rely on inspecting HDX traffic, they would no longer work if you enable Secure HDX since HDX traffic is encrypted.
Troubleshooting
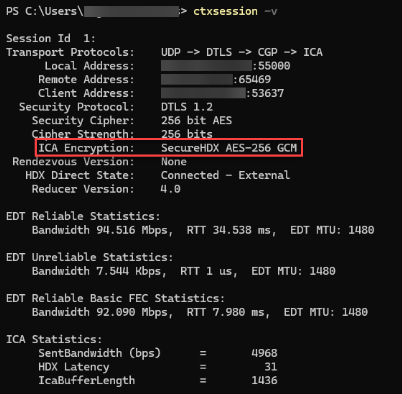
To confirm that Secure HDX is active, you can use the ctxsession.exe utility on the VDA machine.
To use the CtxSession.exe utility, open a Command Prompt or PowerShell within the session and run ctxsession.exe -v. If Secure HDX is in use, ICA Encryption displays SecureHDX AES-256 GCM.
When Secure HDX does not get enabled in the session
-
Ensure the VDA version in use supports the feature per the system requirements.
-
Confirm that you have a policy applied to the VDA that enables Secure HDX and that there are no other policies with higher priority disabling the feature.
-
If the session host was already running when you configured Secure HDX, restart the machine to ensure changes take effect.
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.