Domain pass-through (single sign-on) authentication
Domain pass-through (single sign-on or SSON) also known as legacy domain pass-through (SSON)lets you authenticate to a domain and use Citrix Virtual Apps and Desktops™ and Citrix DaaS (formerly Citrix Virtual Apps and Desktops service) without having to reauthenticate again.
Note:
The Enable MPR notifications for the System policy in the Group Policy Object template must be enabled to support the domain pass-through (single sign-on) authentication feature on Windows 11. By default, this policy is disabled on Windows 11 24H2. So, if upgraded to Windows 11 24H2, you must enable the Enable MPR notifications for the System policy.
This feature is available from Citrix Workspace app for Windows version 2012 and later.
You can’t use legacy domain pass-through (SSON) authentication and enhanced domain pass-through together for authentication.
When enabled, domain pass-through (single sign-on) caches your credentials, so that you can connect to other Citrix® applications without having to sign in each time. Ensure that only software that is in accordance with your corporate policies runs on your device to mitigate the risk of credential compromise.
When you log on to Citrix Workspace app, your credentials are passed through to StoreFront, along with the apps and desktops and Start menu settings. After configuring single sign-on, you can log on to Citrix Workspace app and launch virtual apps and desktops sessions without having to retype your credentials.
All web browsers require you to configure single sign-on using the Group Policy Object (GPO) administrative template. For more information about configuring single sign-on using the Group Policy Object (GPO) administrative template, see Configure single sign-on with Citrix Gateway.
You can configure single sign-on on both fresh installation or upgrade setup, using any of the following options:
- Command-line interface
- GUI
Note:
The terms domain pass-through, single sign-on, and SSON might be used interchangeably in this document.
Limitations:
Domain pass-through using user credentials has the following limitations:
- Doesn’t support passwordless authentication with modern authentication methods such as Windows Hello or FIDO2. An additional component called the Federated Authentication Service (FAS) is required for single sign-on (SSO).
- Installation or upgrade of Citrix Workspace app with SSON enabled requires a reboot of the device.
- Requires Multi Provider Router (MPR) notifications to be enabled on Windows 11 machines.
- Must be on the top of the list of network providers order.
To overcome the preceding limitations, use Enhanced domain pass-through for single sign-on (Enhanced SSO).
Configure single sign-on during fresh installation
To configure single sign-on during fresh installation, do the following steps:
- Configuration on StoreFront.
- Configure XML trust services on the Delivery Controller.
- Modify Internet Explorer settings.
- Install Citrix Workspace app with single sign-on.
Configure single sign-on on StoreFront
Single sign-on lets you authenticate to a domain and use Citrix Virtual Apps and Desktops and Citrix DaaS from the same domain without having to reauthenticate to each app or desktop.
When you add a store using the Storebrowse utility, your credentials pass through the Citrix Gateway server, along with the apps and desktops enumerated for you, including your Start menu settings. After configuring single sign-on, you can add the store, enumerate your apps and desktops, and launch the required resources without having to type your credentials multiple times.
Depending on the Citrix Virtual Apps and Desktops deployment, single sign-on authentication can be configured on StoreFront using the Management Console.
Use the following table for different use cases and its respective configuration:
| Use case | Configuration details | Additional information |
|---|---|---|
| Configured SSON on StoreFront | Launch Citrix Studio, go to Stores > Manage Authentication Methods - Store > enable Domain pass-through. | When Citrix Workspace app isn’t configured with single sign-on, it automatically switches the authentication method from Domain pass-through to User name and password, if available. |
| When workspace for web is required | Launch Stores > Workspace for Web Sites > Manage Authentication Methods - Store > enable Domain pass-through. | When Citrix Workspace app isn’t configured with single sign-on, it automatically switches the authentication method from Domain pass-through to User name and password, if available. |
Configure single sign-on with Citrix Gateway
You enable single sign-on with Citrix Gateway using the Group Policy Object administrative template. However, you must ensure that you have enabled basic authentication and single factor (nFactor with 1 Factor) authentication on the Citrix Gateway.
- Open the Citrix Workspace app GPO administrative template by running
gpedit.msc. - Under the Computer Configuration node, go to Administrative Template > Citrix Components > Citrix Workspace > User Authentication, and select Single Sign-on for Citrix Gateway policy.
- Select Enabled.
- Click Apply and OK.
- Restart Citrix Workspace app for the changes to take effect.
Configure XML trust services on the Delivery Controller
On Citrix Virtual Apps and Desktops and Citrix DaaS™, run the following PowerShell command as an administrator on the Delivery Controller:
asnp Citrix* ; Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $True
Modify the Internet Explorer settings
- Add the StoreFront server to the list of trusted sites using Internet Explorer. To add:
- Launch Internet Options from the Control panel.
-
Click Security > Local Intranet and click Sites.
The Local Intranet window appears.
- Select Advanced.
- Add the URL of the StoreFront FQDN with the appropriate HTTP or HTTPS protocols.
- Click Apply and OK.
- Modify the User Authentication settings in Internet Explorer. To modify:
- Launch Internet Options from the Control panel.
- Click Security tab > Local Intranet.
- Click Custom level. The Security Settings – Local Intranet Zone window appears.
-
In the User Authentication pane, select Automatic logon with current user name and password.
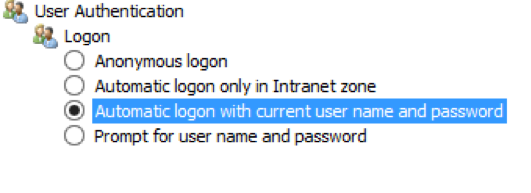
- Click Apply and OK.
Configure single sign-on using the command-line interface
Install Citrix Workspace app with the /includeSSON switch and restart Citrix Workspace app for the changes to take effect.
Configure single sign-on using the GUI
- Locate the Citrix Workspace app installation file (
CitrixWorkspaceApp.exe). - Double-click
CitrixWorkspaceApp.exeto launch the installer. - In the Enable Single Sign-on installation wizard, select the Enable Single Sign-on option.
- Click Next and follow the prompts to complete the installation.
You can now log on to an existing store (or configure a new store) using Citrix Workspace app without entering user credentials.
Configure single sign-on on workspace for web
You can configure single sign-on on workspace for web using the Group Policy Object administrative template.
- Open the workspace for web GPO administrative template by running gpedit.msc.
- Under the Computer Configuration node, go to Administrative Template > Citrix Component > Citrix Workspace > User Authentication.
- Select the Local user name and password policy and set it to Enabled.
- Click Enable pass-through authentication. This option allows the workspace for web to use your login credentials for authentication on the remote server.
- Click Allow pass-through authentication for all ICA® connections. This option bypasses any authentication restriction and allows credentials to pass-through on all the connections.
- Click Apply and OK.
- Restart the workspace for web for the changes to take effect.
Verify that the single sign-on is enabled by launching the Task Manager and check if the ssonsvr.exe process is running.
Configure single sign-on using Active Directory
Complete the following steps to configure Citrix Workspace app for pass-through authentication using Active Directory group policy. In this scenario, you can achieve the single sign-on authentication without using the enterprise software deployment tools, such as the Microsoft System Center Configuration Manager.
-
Download and place the Citrix Workspace app installation file (CitrixWorkspaceApp.exe) on a suitable network share. It must be accessible by the target machines you install Citrix Workspace app on.
-
Get the
CheckAndDeployCitrixReceiverPerMachineStartupScript.battemplate from the Citrix Workspace app for Windows Download page. -
Edit the content to reflect the location and the version of
CitrixWorkspaceApp.exe. -
In the Active Directory Group Policy Management console, type
CheckAndDeployCitrixReceiverPerMachineStartupScript.batas a startup script. For more information on deploying the startup scripts, see the Active Directory section. -
In the Computer Configuration node, go to Administrative Templates > Add/Remove Templates to add the
receiver.admlfile. -
After adding the
receiver.admltemplate, go to Computer Configuration > Administrative Templates > Citrix Components > Citrix Workspace > User authentication. For more information about adding the template files, see Group Policy Object administrative template. -
Select the Local user name and password policy and set it to Enabled.
-
Select Enable pass-through authentication and click Apply.
-
Restart the machine for the changes to take effect.
Configure single sign-on on StoreFront
StoreFront configuration
- Launch Citrix Studio on the StoreFront server and select Stores > Manage Authentication Methods - Store.
- Select Domain pass-through.
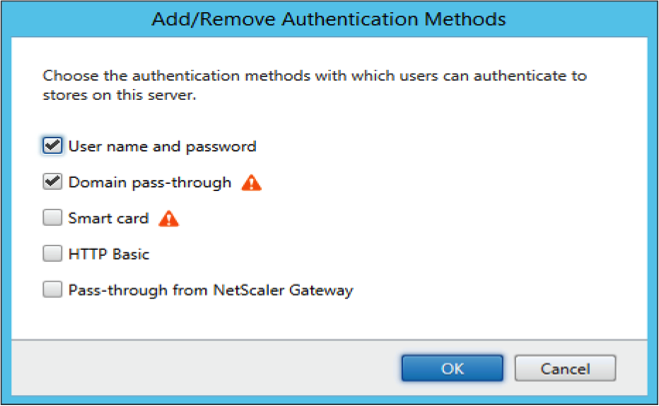
Domain pass-through (Single Sign-on) authentication with Kerberos
This topic applies only to connections between Citrix Workspace app for Windows and StoreFront, Citrix Virtual Apps and Desktops, and Citrix DaaS.
Citrix Workspace app supports Kerberos for domain pass-through (single sign-on or SSON) authentication for deployments that use smart cards. Kerberos is one of the authentication methods included in Integrated Windows Authentication (IWA).
When enabled, Kerberos authenticates without passwords for Citrix Workspace app. As a result, prevents Trojan horse-style attacks on the user device that try to gain access to passwords. Users can log on using any authentication method and access published resources, for example, a biometric authenticator such as a fingerprint reader.
When you log on using a smart card to Citrix Workspace app, StoreFront, Citrix Virtual Apps and Desktops, and Citrix DaaS configured for smart card authentication- the Citrix Workspace app:
- Captures the smart card PIN during single sign-on.
-
Uses IWA (Kerberos) to authenticate the user to StoreFront. StoreFront then provides your Citrix Workspace app with information about the available Citrix Virtual Apps and Desktops and Citrix DaaS.
Note:
Enable Kerberos to avoid an extran PIN prompt. If Kerberos authentication isn’t used, Citrix Workspace app authenticates to StoreFront using the smart card credentials.
- The HDX engine (previously referred to as the ICA client) passes the smart card PIN to the VDA to log the user on to Citrix Workspace app session. Citrix Virtual Apps and Desktops and Citrix DaaS then delivers the requested resources.
To use Kerberos authentication with Citrix Workspace app, check if the Kerberos configuration conforms to the following.
- Kerberos works only between Citrix Workspace app and servers that belong to the same or to trusted Windows Server domains. Servers are trusted for delegation, an option you configure through the Active Directory Users and Computers management tool.
- Kerberos must be enabled both on the domain and Citrix Virtual Apps and Desktops and Citrix DaaS. For enhanced security and to make sure that Kerberos is used, disable any non-Kerberos IWA options on the domain.
- Kerberos logon isn’t available for Remote Desktop Services connections that’re configured to use either Basic authentication, always use specified logon information, or always prompt for a password.
Warning:
Using the Registry editor incorrectly might cause serious problems that can require you to reinstall the operating system. Citrix can’t guarantee that problems resulting from incorrect use of the Registry editor can be solved. Use the Registry Editor at your own risk. Make sure you back up the registry before you edit it.
Domain pass-through (Single Sign-on) authentication with Kerberos for use with smart cards
Before continuing, see Secure your deployment section in the Citrix Virtual Apps and Desktops document.
When you install Citrix Workspace app for Windows, include the following command-line option:
-
/includeSSONThis option installs the single sign-on component on the domain-joined computer, enabling your workspace to authenticate to StoreFront using IWA (Kerberos). The single sign-on component stores the smart card PIN, used by the HDX engine when it remotes the smart card hardware and credentials to Citrix Virtual Apps and Desktops and Citrix DaaS. Citrix Virtual Apps and Desktops and Citrix DaaS automatically selects a certificate from the smart card and gets the PIN from the HDX engine.
A related option,
ENABLE_SSON, is enabled by default.
If a security policy prevents you from enabling single sign-on on a device, configure Citrix Workspace app using Group Policy Object administrative template.
- Open the Citrix Workspace app Group Policy Object administrative template by running gpedit.msc.
- Choose Administrative Templates > Citrix Components > Citrix Workspace > User authentication > Local user name and password
- Select Enable pass-through authentication.
-
Restart Citrix Workspace app for the changes to take effect.
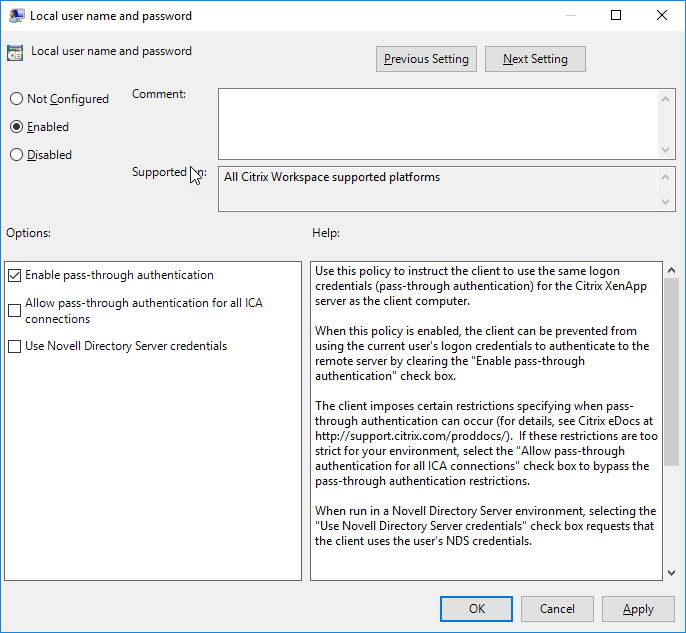
To configure StoreFront:
When you configure the authentication service on the StoreFront server, select the Domain pass-through option. That setting enables Integrated Windows Authentication. You do not need to select the Smart card option unless you also have non domain-joined clients connecting to StoreFront using smart cards.
For more information about using smart cards with StoreFront, see Configure the authentication service in the StoreFront documentation.