Implement machine-level redirections
With the App access control policy, you can use rules to implement machine-level redirections for files, folders, registry keys, and registry values. Typical use cases for this feature include:
- Implement data roaming. Redirect non-user-profile data to a file share, ensuring users can access the same data regardless of which machines they sign into.
- Enhance data protection. Redirect critical data to alternative locations or values, protecting it from unauthorized access.
- Customize the user experience. Tailor app experience based on specific requirements.
Note:
This feature applies to Active Directory (AD) and non-domain-joined (NDJ) environments.
Overview
A redirection rule specifies the following information:
- Data type. The type of data you want to redirect, such as a file, folder, registry key, or registry value.
- Source and destination paths. The source and destination paths for the specified data type.
- Assignments. Users, machines, and processes to which you want to apply this redirection. For more information, see Assignment types.
Assignment types
Assignments in redirection rules come in three categories: processes, users, and machines. The specific assignment types are listed as follows:
| Category | Type |
|---|---|
| Processes | Any processes |
| Users
|
|
| Machines
|
|
Note:
- In the context of the App access control policy, OUs are used as containers only for machines, but not for users.
- NDJ machines are limited to those machines that Citrix® creates and power manages.
When a rule has multiple assignments configured, be aware of the following considerations:
- If those assignments are of the same category (for example, user A and user group B), the rule applies to all objects specified in those assignments (user A and all users in user group B).
- If those assignments are of different categories (for example, user A and machine X), the rule applies when the conditions specified in all those assignments are met (when user A signs in to machine X).
Note:
If no assignments are configured for a rule, the redirection configured in this rule takes effect in any conditions.
Workflow
At a high level, the workflow of implementing machine-level redirections is as follows:
-
Create and generate redirection rules using either of these tools:
-
GUI-based tool – WEM Tool Hub > Rule Generator for App Access Control
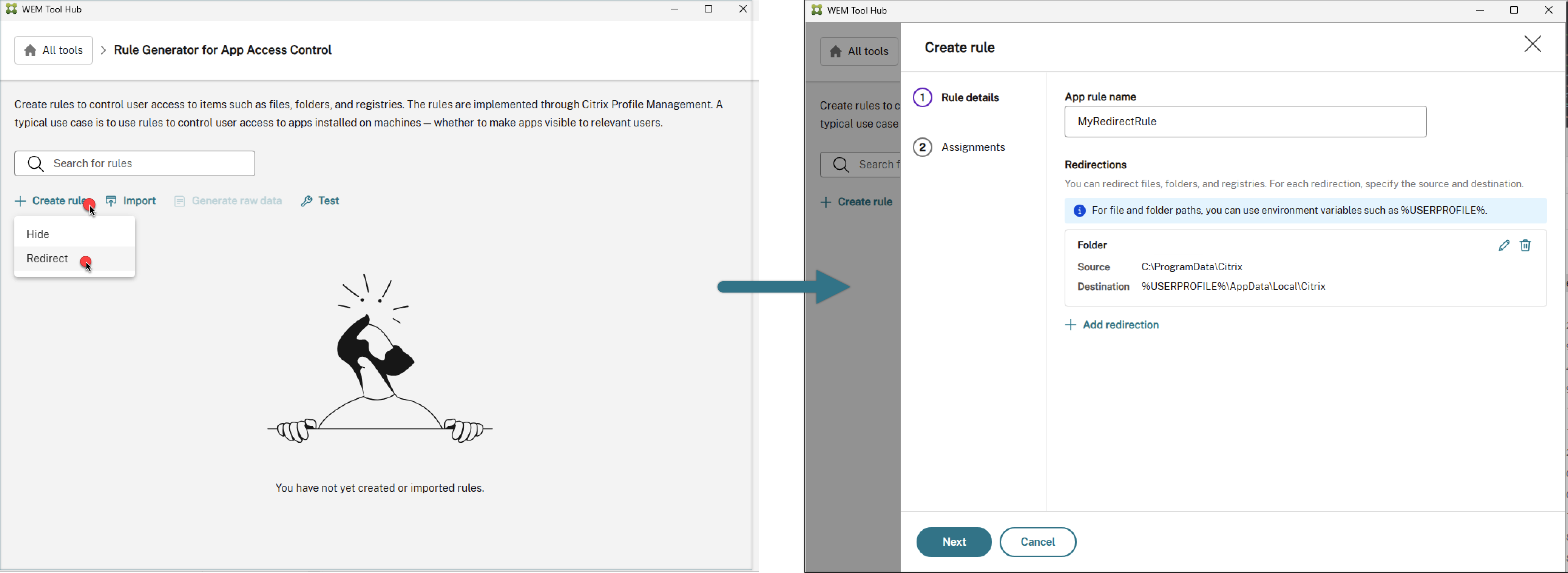
-
PowerShell tool – available with the Profile Management installation package. For more information, see Create, manage, and deploy rules using Rule Generator.
Note:
For a better user experience, we recommend using the GUI-based tool to create, manage, and generate app access control rules. Get the tool in WEM Tool Hub, downloadable in Citrix Cloud™ > WEM service > Utilities.
-
-
Deploy redirection rules to machines using the App access control Policy. For more information, see Deploy redirection rules to machines
Create, manage, and deploy rules using Rule Generator
This section guides you through using the PowerShell-based Rule Generator to create, manage, and deploy rules. Before you begin, make sure that the machine where you run the tool meets these requirements:
- Runs on Windows 10 or 11, or Windows Server 2016, 2019, or 2022.
- (For AD environments only) Is in the same domain as your users and machines.
The general procedure is as follows:
- Run Windows PowerShell as an administrator.
-
Access the \tool folder in the Profile Management installation package, and then run CPM_App_Access_Control_Config.ps1. The rule status information appears:
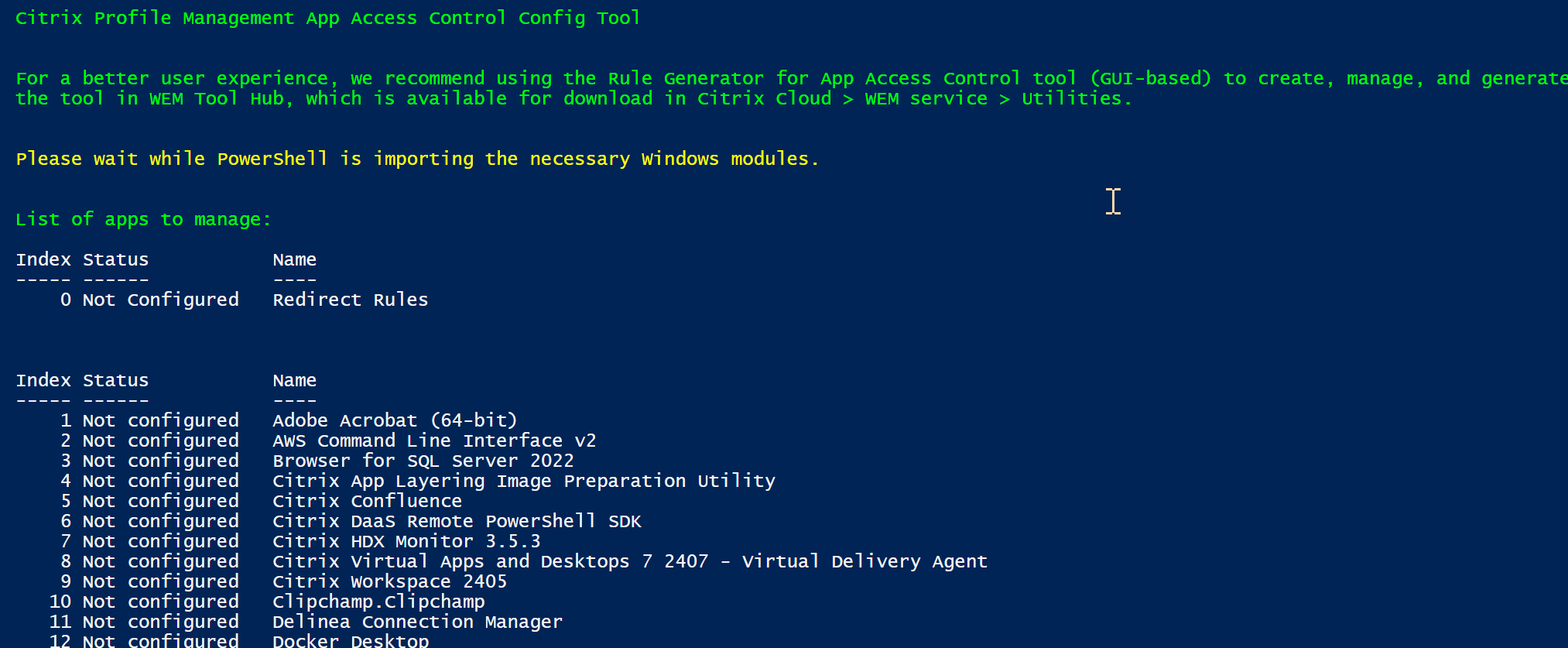
Field Description Index
- Shows 0 for redirection rules.
- Shows the index of an app hiding rule.
Status Shows the status of a rule, including Configured, Not configured, Configured & applied. Name
- Shows Redirection Rules for redirection rules.
- Shows the name of an application installed on the machine for app hiding rules.
- Shows 0 for redirection rules.
-
Enter 0 to choose to manage redirection rules. All configured redirect rules appear.
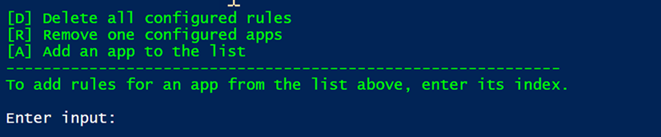
- To add a redirection rule, enter 1.
- Follow the onscreen prompts to configure the rule:
- Type of redirect object. Select a type from File, Folder, Registry key, or Registry value.
- Redirect source and destination. Specify the source and destination paths of the specified redirect object.
-
Assignments. Specify users, machines, and processes you want to apply this redirect to, separated by commas. For more information, see the following table.
Assignment type Description AD users, user groups, or OUs Enter their AD domain names, separated by commas. AD machines Enter their DNS host names, separated by commas. NDJ machine catalogs Enter catalog names, separated by commas. Example: Machine_catalog_name1,Machine_catalog_name2NDJ machines Collect machine names using the AAD/NDJ object selector in the WEM web console, and then enter those names, separated by commas. Example: Machine_name1,Machine_name2. To add all non-domain-joined machines, enter NDJ*. Wildcards*and?are supported for NDJ machine names.Note: To exclude specific users or machines, add EX>before their identifiers. To exclude specific processes, add a?before their identifiers. Separate an exclusion from the assigned group using a vertical bar (|).
- Repeat steps 4 and 5 to add more redirection rules.
- Follow the onscreen prompt to generate the raw data for the rules you configured, and then save it in a .txt file for future use.
- To test whether the rules work as expected, follow the onscreen prompt to deploy them to this machine or a group of machines.
Deploy redirection rules to machines
After you create and generate redirection rules, use GPOs, Studio, or WEM to deploy them to machines using the App access control policy. For more information, see Enable app access control using GPOs.