Citrix Workspace app for ChromeOS - Preview
This documentation describes the features and configuration of Citrix Workspace app for ChromeOS 2511. This version is the preview for the latest version of Citrix Workspace app for ChromeOS.
Early Adopter Release (EAR) build for 2511 is available on:
EAR build is for the purpose of testing or validation with the intent to make organizations ready for the upcoming release and is NOT advised to be deployed in production environments.
For more information on how to install the EAR build, see To access the EAR build.
What’s new
In addition to new features, this release is compatible with ChromeOS versions 143 and 144. This release addresses areas that improve overall performance and stability. Following are the new features and enhancements:
- Integration of deviceTRUST with Citrix Workspace app for ChromeOS
- Always On Tracing (AOT)
- Default audio device selection
- Entra ID single sign-on support for VDA with Azure AD credentials
- Global App Configuration service v2 authenticated user group support
Integration of deviceTRUST with Citrix Workspace app for ChromeOS
Starting with version 2511, Citrix Workspace app for ChromeOS supports deviceTRUST integration, enhancing security through continuous device posture checks within sessions. This integration ensures only compliant ChromeOS devices can access Citrix Virtual Apps and Desktops.
About the feature
deviceTRUST provides continuous device posture monitoring and assessment capabilities for ChromeOS devices accessing Citrix environments. The integration uses Google Chrome Enterprise APIs to collect device information and enforce security policies based on device compliance status.
Note:
For more information about deviceTRUST, see deviceTRUST Platform.
Supported device properties
The following device properties (signals) are available for ChromeOS platform configuration in the deviceTRUST console:
ChromeOS properties
- Asset ID - Administrator-assigned asset identifier
- Directory Device ID - Unique identifier for the device
- Location - Administrator-annotated device location
Hardware properties
- BIOS Serial Number - Device BIOS serial number
- CPU - CPU model name
- CPU Count - Number of CPU cores
Device name
- Name - Device host name
Operating system properties
- Name - Operating system name (ChromeOS)
- Platform - OS architecture
- Type - Client device type
- Version - ChromeOS version
User properties
- Name - Email address of the user logged into the Chrome device
- SID - Unique identifier for the user account
Enterprise API requirements
deviceTRUST uses Google Chrome Enterprise APIs that are only available to managed, force-installed Citrix Workspace app instances. The following properties require force installation:
ChromeOS properties (force install required)
- Asset ID
- Directory Device ID
- Location
Hardware properties (force install required)
- BIOS Serial Number
Device name (force install required)
- Name
Configuration in Google Admin Console
To configure device properties in the Google Admin Console:
- Sign in to the Google Admin Console.
- Navigate to Chrome > Devices.
- Select the device whose properties you want to set or view.
- Edit the Asset ID or Location property in the Custom fields section.
- View the Directory Device ID and BIOS Serial Number properties in the Basic Info section.
- Click Save to apply changes.
Benefits
This integration provides:
- Continuous security monitoring - Real-time device posture assessment during active sessions
- Policy enforcement - Automated responses based on device compliance status
- Enhanced visibility - Comprehensive device information for security administrators
- Seamless user experience - Transparent security checks without user intervention
Limitations
The following properties are not available for ChromeOS devices due to API limitations:
- Hardware Model property
- Hardware Vendor property
Always On Tracing (AOT)
Citrix Workspace app for ChromeOS now supports Always On Tracing (AOT), a modern diagnostic framework from Citrix that continuously captures relevant log data across the Citrix Virtual Apps and Desktops environment. This feature simplifies troubleshooting for IT administrators and Citrix support teams by automatically capturing log data for user sessions and system events, eliminating the need to reproduce issues.
AOT makes logs easily accessible and readable without engineering-level expertise, enabling self-service diagnostics to reduce dependency on Citrix Support and improve mean-time-to-resolution.
Benefits
AOT provides significant value to customers by:
- Automatically capturing log data for user sessions and system events without manual intervention
- Eliminating the need to reproduce issues since logs are continuously collected during normal operations
- Making logs easily accessible and readable without requiring engineering-level expertise
- Enabling self-service diagnostics to reduce dependency on Citrix Support
- Improving mean-time-to-resolution for troubleshooting scenarios
Use cases
AOT fits into your overall experience in the following scenarios:
- Proactive monitoring: Continuously monitor user sessions and system events to identify potential issues before they impact users
- Rapid troubleshooting: Access comprehensive log data immediately when issues occur, without waiting for log reproduction
- Self-service support: Enable IT administrators to diagnose and resolve common issues independently using accessible log data
Upload AOT logs to Centralized AOT Log Server
The AOT Log Server acts as a centralized destination for collecting and storing Always On Tracing (AOT) logs from various Citrix® components. It is containerized using Docker technology and is preferably deployed on Linux, though it also supports Windows environments through Docker Desktop.
Note:
In this Citrix Workspace app for ChromeOS 2511 release, AOT logs are only captured for on-premises setups without gateway in the path.
Prerequisites
This feature is available only when you open a session using:
-
Citrix Virtual Apps and Desktops™ version 2507 CU1 or later
-
Citrix Virtual Apps and Desktops™ version 2511 or later
How to configure
To configure, you must first install and configure the log server. For detailed installation and configuration steps, see Install and configure log server.
After you install the log server, the system generates a StartLogServer script in the same location. The file name is StartLogServer.bat on Windows or StartLogServer.sh on Linux.
To enable communication between Citrix Workspace app for ChromeOS and the log server, you must configure the log server to accept the StoreFront FQDN URL by enabling Cross-Origin Resource Sharing (CORS) in the log server.
To enable CORS:
- If the log server is running, stop it using the following command:
docker stop logserver
<!--NeedCopy-->
- Add the following environment arguments to
StartLogServer.bat(orStartLogServer.shon Linux) by editing the CORS_ORIGINS parameter:
-e CORS_ORIGINS=""
<!--NeedCopy-->
Example for single URL:
-e CORS_ORIGINS="https://xyz.bvt.local;"
<!--NeedCopy-->
Example for multiple URLs:
-e CORS_ORIGINS="url1;url2;url3"
<!--NeedCopy-->
Use semicolons (;) to separate multiple URLs.
- Restart the log server using the command
StartLogServer.bat(orStartLogServer.shon Linux).
Default audio device selection
Starting with version 2511, Citrix Workspace app for ChromeOS lets users select and save their preferred audio speaker and microphone devices from the session toolbar for each VDA.
About this feature
This feature offers a more customized audio experience with the following key features when connected to a virtual desktop:
-
Device selection: Users can assign different input and output audio devices to different VDAs. For example, you can have two different VDAs, each using a separate default speaker (one built-in speaker and one headset). The exact audio device can be selected for each active VDA from the Preferences section. The selected device becomes the default device from the same session.
-
Configuration persistence: The system preserves the selected configuration for the next session, ensuring a seamless experience.
Prerequisites
Enable the Plug and play audio device support feature (enabled by default). If the feature is disabled, see Plug and play audio device support configuration to enable it.
How to select specific audio devices
To select the specific audio device, do the following:
- Navigate to the Preferences section on the session toolbar.
- Click More. The following image appears:
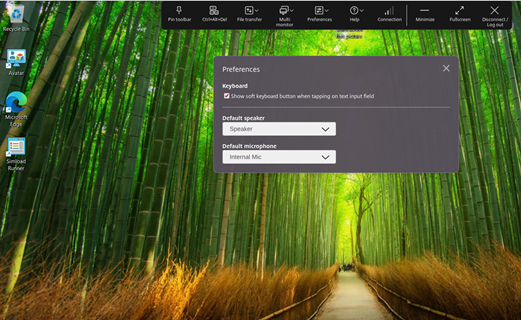
- Select the device that you want from the Default speaker drop-down list.
- Select the device that you want from the Default microphone drop-down list.
Note:
If the selected audio device for a VDA becomes unavailable or is unplugged, the session automatically switches to the client’s endpoint-assigned default audio device.
Known limitations in the feature
-
This feature does not apply to pooled desktop environments because users connect to different VDAs each time they sign in.
-
When you reinstalled Citrix Workspace app for ChromeOS, the default audio device settings isn’t retained.
Entra ID single sign-on support for VDA with Azure AD credentials
Previously, users were prompted for credentials when launching HDX sessions with Microsoft Entra ID joined VDAs because there was no SSO support for VDA with Entra ID credentials. This prompting creates challenges for users who migrate from traditional Active Directory to Azure AD as their primary identity provider.
Starting with version 2511, Citrix Workspace app for ChromeOS now provides a seamless single sign-on (SSO) experience for VDAs with Entra ID credentials. This feature eliminates the need for users to enter credentials when launching HDX sessions with Microsoft Entra ID joined VDAs, providing a streamlined authentication experience.
With this feature, users who have adopted Entra ID joined VDAs can now enjoy seamless authentication without manual credential entry for each VDA launch.
Note:
- This feature is enabled by default.
Applicability
This feature applies to app and desktop session launches with pure and hybrid Entra ID joined VDAs of version 2507 and above with the specified OS versions.
System requirements
Virtual Delivery Agent (VDA):
- Version: 2507
- Type: Single session or multi session
VDA machine identity:
- Microsoft Entra ID joined
- Microsoft Entra ID hybrid joined
Session host OS:
- Windows 11 24H2 with the 2025-08 Cumulative Update Preview for Windows 11 Version 24H2 - KB5068221 (OS Build 26100.6588 and above)
- Server OS - Preview Build 27924 and above
For more information on Entra ID SSO, see Microsoft Entra ID single sign-on in Citrix DaaS documentation.
Known limitations in the feature
Citrix Workspace app for ChromeOS does not support SSO for hybrid launches from browser because it lacks in-memory ICA support.
How to configure
Google Admin Policy
For managed devices and users, administrators can disable the feature using the Google Admin Policy as follows:
- Sign in to the Google Admin Policy.
- Go to Device management > Chrome Management > User Settings.
-
Add the following JSON strings to the
policy.txtfile under theengine_settingskey.Note:
You can apply this configuration to the following as well:
- Device > Chrome > Apps and extensions > Users and browsers > Search for the extension > Policy for extensions.
- Device > Chrome > Apps and extensions > Kiosks > Search for the extension > Policy for extensions.
- Device > Chrome > Apps and extensions > Managed guest sessions > Search for the extension > Policy for extensions.
-
Make sure that you set the attribute
enableAADSSOtofalse. The following is an example of JSON data:{ "settings": { "Value": { "settings_version": "1.0", "engine_settings": { "features": { "enableAADSSO”: false } } } } } <!--NeedCopy--> - Save the changes.
Troubleshoot
This article focuses on the logs that you need to collect when SSO fails and users receive unexpected credential prompts after their session launches.
Prerequisites
-
Cloud Broker - 126
-
VDA - 2507
-
Citrix Workspace app for ChromeOS - 2509
-
Citrix Workspace app for ChromeOS - set the attribute enableAADSSO to true from Citrix Workspace app for ChromeOS 2509 and later.
Collect logs for Citrix Workspace app for ChromeOS
-
Citrix Workspace app for ChromeOS log collection - perform the steps mentioned at Troubleshoot.
-
Network traces for MSAL token fetch status
- Open Chrome browser and navigate to chrome://net-export/.
-
Click Start Logging to Disk and select Include raw bytes (it includes cookies and credentials) as shown:
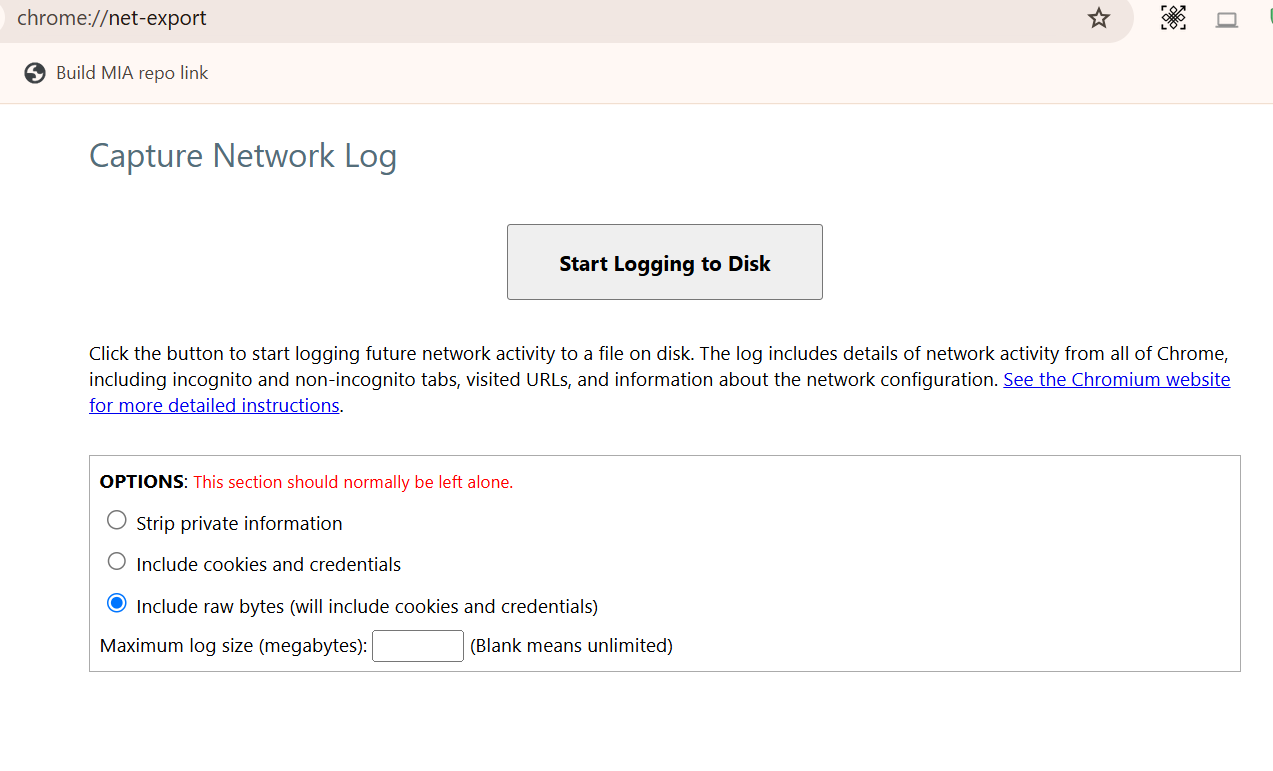
- Start a Citrix Workspace app for ChromeOS session to reproduce the issue and collect the traces. Click Stop logging in chrome://net-export/.
-
CDF traces - Collect CDF traces from the VDA for all modules and startup tracing following the steps here - Collect a Citrix Diagnostic Facility (CDF) trace at system startup, as SSO can fail even when capability negotiation from CWA succeeds.
Known limitations in the feature
- Citrix Workspace app for ChromeOS does not support SSO for hybrid launches from browser because it lacks in-memory ICA support.
- When session launch takes longer than 30 seconds, AAD SSO login fails and prompts users for credentials.
Global App Configuration service v2 authenticated user group support
Starting with version 2511, Citrix Workspace app for ChromeOS now supports Global App Configuration Service v2 authenticated user group support, enabling administrators to configure settings for specific user groups through configuration profiles instead of applying settings store-wide.
About this feature
Previously, administrators could only apply settings store-wide to all users, which prevented targeted configuration for specific user groups.
With 2511, the Global App Configuration service now enables administrators to target specific user groups by pushing settings to configuration profiles rather than applying settings to entire stores.
With this feature, administrators can now:
- Target specific user groups: Configure settings for specific user groups rather than applying generic settings to all users.
- Use configuration profiles: Leverage configuration profiles to organize and manage settings for different user groups.
- Maintain granular control: Apply different settings based on user group requirements and organizational needs.
Benefits
This feature provides significant value by:
- Enabling targeted configuration: Administrators can push settings according to specific user group needs instead of using generic settings for all users
- Improving administrative efficiency: Streamlines the configuration process by allowing group-based policy management
- Enhancing user experience: Users receive configurations tailored to their specific roles and requirements
- Reducing configuration complexity: Simplifies management of diverse user environments within the same organization
- Enhancing user experience: Users receive configurations tailored to their specific roles and requirements.
Applicability
This feature applies to:
- All apps and desktops for cloud stores
- All user groups configured through configuration profiles
How to enable
This feature is enabled by default on Citrix Workspace app for ChromeOS. Administrators can immediately start using configuration profiles to target specific user groups.
For detailed information on managing settings using configuration profiles, see Manage settings using configuration profile.
To configure settings for cloud store, see Configure settings for cloud stores.
To configure settings for on-prem store, see Configure settings for on-premises stores.
Known limitations in the feature
Citrix Workspace app for ChromeOS is not supported on on-premises deployments.
Fixed issues
- When a store with Azure IdP is accessed with Citrix Workspace app for ChromeOS in kiosk mode or accessed after the store is left to idle state, the end user might see an error - “Request Header or Cookie too large”. [CCPHELP-13096]
- Website tabs display incorrect page titles when you open websites using BCR (Browser Content Redirection) in a Citrix Workspace app for ChromeOS session. [CVADHELP-30597]
Known issues
There are no new known issues in this release.
Citrix Workspace app for ChromeOS - Preview feedback
You can give the EAR feedback at: https://forms.office.com/r/WjD1ppYSjQ.
Important:
The Early Adopter Release (EAR) documentation is available for information purposes only. It isn’t a commitment, promise, or legal obligation to deliver any material, code, or functionality and must not be relied upon in making Citrix product purchase decisions. The development, release, and timing of any features or functionality described in the EAR documentation remain at our sole discretion and are subject to change without notice or consultation. Citrix does not accept support cases for EAR but welcomes feedback for improving them. Citrix might act on feedback based on its severity, criticality, and importance.