Security
Application security
Application security feature allows you to define rules to control which applications and files the users can run. You can configure application security rules in the web console and provide a tool to retrieve information needed for rule configuration. Also, you can use this feature to create assignment groups with security rules. When the Process application rules and Process DLL rules are enabled, the Overwrite mode is turned on by default. In Overwrite mode, the rules that are processed in the end overwrite rules that were processed earlier. We recommend that you apply this mode to only single-session machines. This feature also allows you to create the following rules:
- Executable rules
- Windows installer rules
- Script rules
- Packaged app rules
- DLL rules
Note:
Before creating rules, we recommend that you first add the default rules to ensure that important system files can run.
Create Windows installer rule
This includes two menu items, Basic information and Exceptions. To create a Windows installer rule, complete the following steps under Basic information and Exceptions:
- Selecting Create rule leads you to the Create Windows installer rule page.
- Enter the name and an optional description.
- Choose the desired Action.
- Select the Criteria type such as Path, Publisher, or File hash from the drop-down list.
- Selecting Open File info Viewer directs you to Citrix Environment Tool Hub. Use Citrix Environment Tool Hub** to quickly get the required information. For more information, see File Info Viewer.
- Optionally, you can add exceptions to include files that are normally included in the rule based on the primary criteria. To perform this task, select Add exception.
- Go to Citrix Environment Tool Hub to copy data from one of the specified criteria under File Info Viewer and then click Paste from File Info Viewer.
- Click Done.
- Select Continue to assignment to update the assignments as required in the Manage assignments page.
- Select Assignment targets (users and groups) to assign this item to. Use filters to contextualize the assignment. Filters you specify are effective only in the Overwrite mode and are supported only on agent versions 2406 or later.
- Enter an asterisk if you need a specific rule to be applied to all files.
Import AppLocker rules in WEM web console
You can directly import application security rules exported from an AppLocker xml file into the WEM web console. Doing this, you can quickly bring in multiple rules from existing AppLocker configurations, streamlining setup, and improving consistency across environments. When you import a rule, its assignment is also included.
To import AppLocker rules, navigate to the Administration Console > Security > Application Security tab and select Import AppLocker rules.
On the Import AppLocker rules page, you get two import mode options:
- Skip: The rules with the same GUID that exist in your environment are not created or updated. The existing rules are retained instead of using the ones from the XML file.
- Overwrite: The existing rules with matching GUIDs are updated using the rules from the XML file.
Note:
- The AppLocker rule XML file must not exceed 10 MB in size.
- The file must also be a valid XML format.
- The board displays an error message if the assignee can’t be found or a rule can’t be imported.
- The creation of the rule fails if the rule is invalid.
Privilege elevation
This feature defines rules to run certain programs with administrator privileges. You can elevate the privileges of non-administrative users to an administrator level necessary for some executables. As a result, the users can start those executables as if they are members of the administrators group.
Privilege elevation options
-
Process privilege elevation rules: When selected, enables agents to process privilege elevation settings and other options on the Privilege Elevation tab become available.
-
Apply to Windows Server Operating Systems: Controls whether to apply privilege elevation settings to Windows Server operating systems. If selected, rules assigned to users work on Windows Server machines. By default, this option is disabled.
-
Enforce RunAsInvoker: Controls whether to force all executables to run under the current Windows account. If selected, users are not prompted to run executables as administrators.
This pane also displays the complete list of rules that you have configured. Click Executable Rules, Windows Installer Rules, or Self-elevation to filter the rule list to a specific rule type. You can use Find to filter the list. The assigned column displays a check mark icon for assigned users or user groups.
Supported rules
You can configure privilege elevation using two types of rules: executable rules and Windows installer rules.
-
Executable Rules: Rules that include files with .exe and .com extensions associated with an application.
-
Windows Installer Rules: Rules that include installer files with
.msiand.mspextensions associated with an application. When you add Windows installer rules, consider the following scenario:- Privilege elevation applies only to Microsoft’s msiexec.exe. Make sure that the tool you use to deploy
.msiand.mspWindows installer files is msiexec.exe. - Suppose that a process matches a specified Windows installer rule and its parent process matches a specified executable rule. The process cannot get elevated privileges unless the Apply to Child Processes setting is enabled in the specified executable rule.
- Privilege elevation applies only to Microsoft’s msiexec.exe. Make sure that the tool you use to deploy
-
Self-elevation: When enabled, the Run with administrator privileges option is available in the context menu when you right-click a file. After selecting this option, you are prompted to provide a reason for the elevation. The elevation is then either allowed or denied, based on the criteria you specify. To configure the rule, you can use the Citrix Environment Tool Hub > File Info Viewer to quickly get the information required such as, path, publisher, and hash values. You can also specify the time period, choose the day of the week, and also optionally set the criteria to determine the machines on which the rule is effective. When the Self-elevation toggle is enabled for the first time in a configuration set, the self-elevation rule is created and can be found in the rule list when managing assignments for an assignment target. The rule is never removed after creation.
Important:
When configuring privilege elevation rules with folder-based path conditions, ensure that non-administrators do not have Write access to the specified paths. Allowing Write access can let standard users place files in those locations and potentially gain elevated privileges.
If you’ve already configured a folder-based path condition and standard users have Write access, either update the folder permissions to restrict Write access to administrators only, or change the rule to use a hash or publisher condition instead.
You can specify the time period during which the rule is effective. Also, you can optionally set the criteria to determine on which machines the rule applies. You can choose to match all or any of the following criteria:
- Machine catalog name
- Delivery group name
- Device name
- IP address
- OS platform type
- OS version
- Persistent machine status
After you select the Executable Rules, the Windows Installer Rules, or the Self-elevation rules, the Actions section displays the following actions available to you:
-
Edit. Lets you edit an existing executable rule.
-
Delete. Lets you delete an existing executable rule.
-
Create Rule. Lets you create an executable rule. To create an executable rule, follow the wizard instructions.
Process hierarchy control
The process hierarchy control feature controls whether certain child processes can be started from their parent processes in parent-child scenarios. You create a rule by defining parent processes and then designating an allow list or a block list for their child processes. Review this entire section before using the feature.
Note:
- This feature applies only to Citrix Virtual Apps.
To understand how the rule works, keep the following in mind:
-
A process is subject to only one rule. If you define multiple rules for the same process, only the rule with the highest priority is enforced.
-
The rule you defined is not restricted only to the original parent-child hierarchy but also applies to each level of that hierarchy. Rules applicable to a parent process prevail over rules applicable to its child processes regardless of the priority of the rules. For example, you define the following two rules:
- Rule 1: Word cannot open CMD.
- Rule 2: Notepad can open CMD.
With the two rules, you cannot open CMD from Notepad by first opening Word and then opening Notepad from Word, regardless of the priority of the rules.
This feature relies on certain process-based parent-child relationships to work. To visualize the parent-child relationships in a scenario, use the process tree feature of the Process Explorer tool. For more information about Process Explorer, see https://docs.microsoft.com/en-us/sysinternals/downloads/procmon.
To avoid any potential issues, we recommend that you add an executable file path that points to VUEMAppCmd.exe in the Full Configuration management interface. VUEMAppCmd.exe ensures that the WEM agent finishes processing settings before published applications start. Complete the following steps:
-
On the Application node, select the application, click Properties in the action bar, and then go to the Location page.
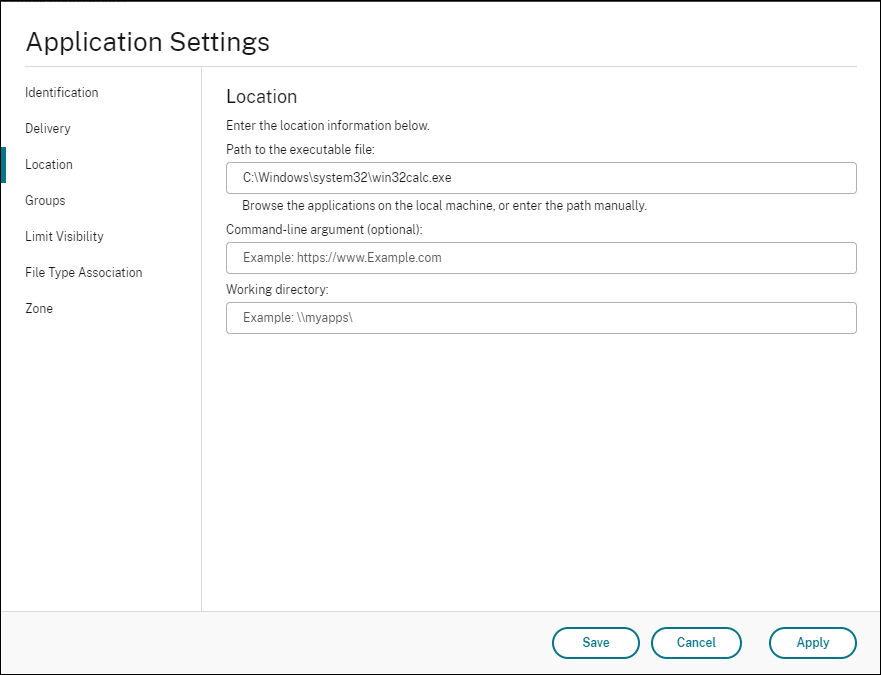
-
Type the path of the local application on the end-user operating system.
-
Under the Path to the executable file field, type the following:
<%ProgramFiles%>\Citrix\Workspace Environment Management Agent\VUEMAppCmd.exe <!--NeedCopy-->
-
-
Type the command-line argument to specify an application to open.
- Under the Command-line argument field, type the full path to the application that you want to launch through VUEMAppCmd.exe. Make sure that you wrap the command line for the application in double quotes if the path contains blank spaces.
- For example, suppose you want to launch iexplore.exe through VUEMAppCmd.exe. You can do so by typing the following:
%ProgramFiles(x86)%\"Internet Explorer"\iexplore.exe.
Considerations
For the feature to work, you need to use the AppInfoViewer tool on each agent machine to enable the feature. Every time you use the tool to enable or disable the feature, a machine restart is required. With the feature enabled, be aware of the following considerations:
-
You must restart the agent machine after upgrading or uninstalling the agent.
-
The automatic agent upgrade feature does not work when the feature is enabled. To use the automatic agent upgrade feature, use the AppInfoViewer tool to first disable the process hierarchy control feature.
To verify that the process hierarchy control feature is enabled, open the Registry Editor on the agent machine. The feature is enabled if the following registry entry exists:
- 32-bit OS
HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\CtxHook\AppInit_Dlls\WEM Hook
- 64-bit OS
HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\CtxHook\AppInit_Dlls\WEM HookHKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Citrix\CtxHook\AppInit_Dlls\WEM Hook
Prerequisites
To use the feature, make sure that the following prerequisites are met:
- A Citrix Virtual Apps deployment.
- The agent is running on Windows 10 or Windows Server.
- The agent host has been restarted after an in-place upgrade or fresh install.
Process hierarchy control options
When you select Process Hierarchy Control in Security, the following options appear:
Enable Process Hierarchy Control: Controls whether to enable the process hierarchy control feature. When selected, other options on the Process Hierarchy Control tab become available and configured settings take effect. You can use this feature only in a Citrix Virtual Apps deployment.
Hide Open With from Context Menu: Controls whether to show or hide the Open With option from the Windows right-click context menu. When enabled, the menu option is hidden from the interface. When disabled, the option is visible and users can use it to start a process. The process hierarchy control feature does not apply to processes started through the Open With option. We recommend that you enable this setting to prevent applications from starting processes through system services that are unrelated to the current application hierarchy.
The Process Hierarchy Control tab also displays the complete list of rules that you have configured. You can use Find to filter the list. The assigned column displays a check mark icon for assigned users or user groups.
The Actions section displays the following actions:
- Edit. Lets you edit a rule.
- Delete. Lets you delete a rule.
- Create rule. Lets you add a rule.
Create rule
-
Navigate to Process Hierarchy Control and click Create rule. The Create rule page appears.
- In the Display section, type the following:
- Name. Type the display name of the rule. The name appears in the rule list.
- Description. Type additional information about the rule.
-
In the Priority section: set the priority for the rule. When configuring the priority, consider the following: The priority determines the order in which the rules you configured are processed. The greater the value, the higher the priority. Type an integer. If there is a conflict, the rule with the higher priority prevails.
- In the Criteria Type section, select an option to add Parent process.
- Path. The rule matches a file path.
- Publisher. The rule matches a selected publisher.
- Hash. The rule matches a specific hash code.
- In the Mode section, select either of the following options:
- Allow list. Set criteria for child processes that are allowed to open from the parent process. Everything else is denied.
- Deny list. Set criteria for child processes that are not allowed to open from the parent process. Everything else is allowed.
-
Criteria for child processes.
-
Specify the time period during which the rule is effective.
- Machine criteria: Set criteria to determine on which machines the rule is effective. You can optionally set the criteria to determine on which machines the rule applies. You can choose to match all or any of the following criteria:
- Machine catalog name
- Delivery group name
- Device name
- IP address
- OS platform type
- OS version
- Persistent machine status
To assign rules to users
Select one rule in the list and then click Manage assignments in the Actions section.
To delete rules
Select one or more rules in the list and then click Delete in the Actions section.