Migration of app security controls and access policies to the new access policy framework
Citrix has made changes to enabling application access in the product. Previously, applications needed to be subscribed to the users or user groups in the Applications > App subscribers section in the wizard to enable access. Going forward, at least one access policy is required to enable access to the applications. While creating the policies, the Users or groups condition is a mandatory condition to be met to grant access to the applications for the users. For details, see Create access policies.
Also, the Enhanced Security section in the application configuration is deprecated. You can now enforce granular security controls like clipboard restriction, download restriction, print restrictions in addition to advanced options like opening an app in the remote browser from Access Policies. With this change, customers can enforce adaptive security based on context like users, location, device, risk.
To migrate your apps’ security controls and access policies to the new access policy framework and to avoid any downtime in the application access, Citrix® has made the required changes. As a result, you might notice some changes in your policies list such as the following:
- New policies created
- A single policy split into multiple policies
- Policy names prefixed with
<System generated policy - App name>
Note:
If the apps do not have users or groups added, then new policies are not created.
The following table summarizes the changes.
| If you had configured an … | Then … |
|---|---|
| App without any enhanced security conditions | A new policy is created with users and groups as the mandatory condition. The users or groups is derived from the access policies. The action is set to Allow Access. |
| App with enhanced security conditions | A new policy is created with users and groups as the mandatory condition. The users or groups is derived from the access policies. The action is set is Allow with restriction. Based on the app level security condition configured earlier. The corresponding security restrictions are selected while creating the policy. The migrated policies are prefixed with <System generated policy - App name>. |
| Access policy with presets | If the policy already had a user group condition selected, then a new policy is created as-is and the corresponding security conditions are selected in the access policy based on the presets. |
| Access policy without user or group condition | As the users or groups is a mandatory condition to access the apps, a single policy that was configured for multiple apps is now split into multiple policies as each app might have different set of users or groups. The users or groups is derived from the access policies. For each policy, users or groups is set as a mandatory condition. |
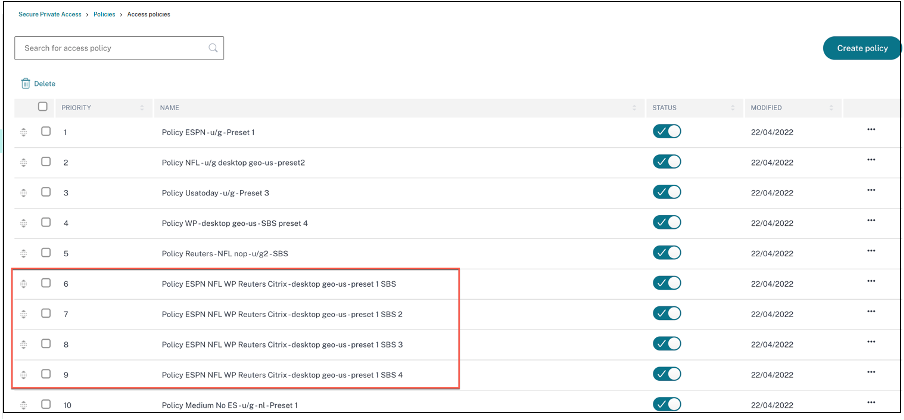
The following figure displays sample policy names prefixed with <System generated policy - App name>.
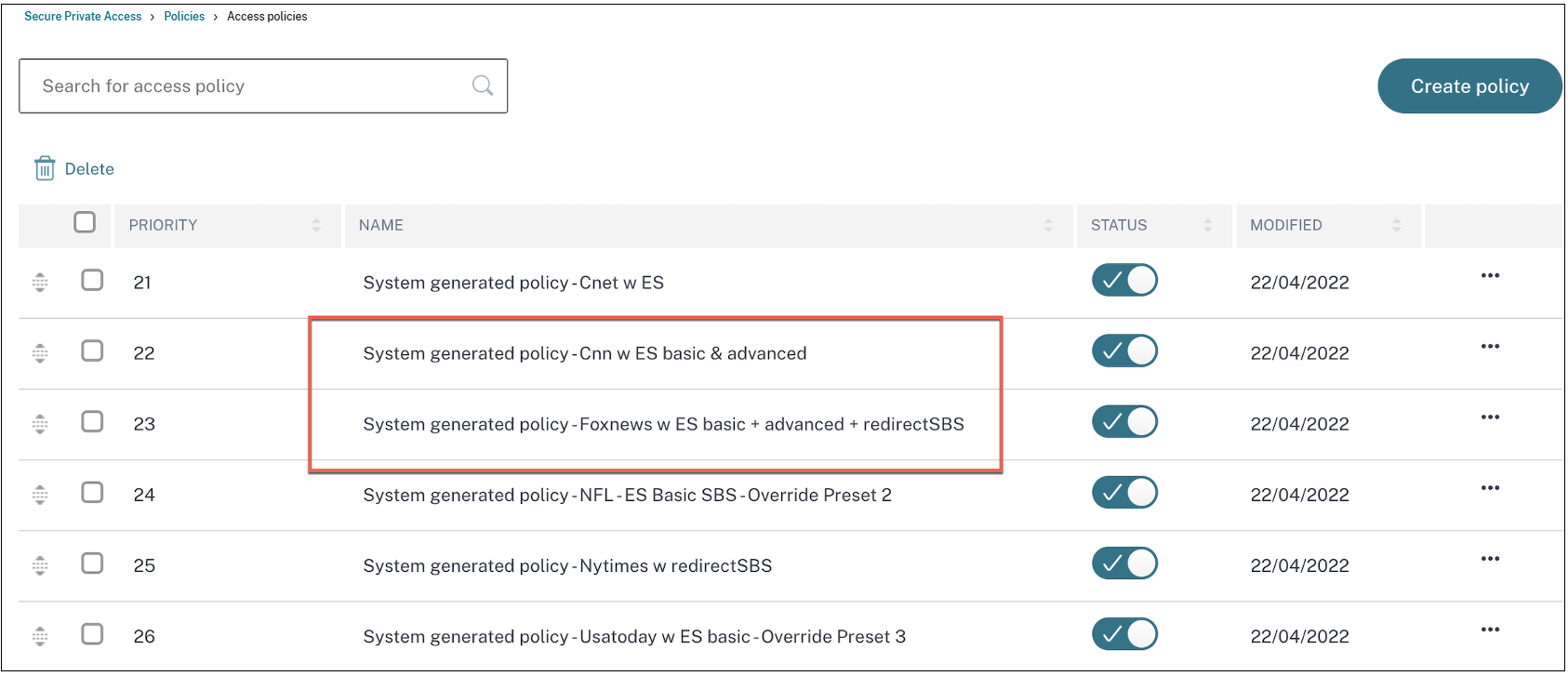
The following figure displays a sample of a single policy split into multiple policies.