Secure Private Access service solution overview
Solution overview
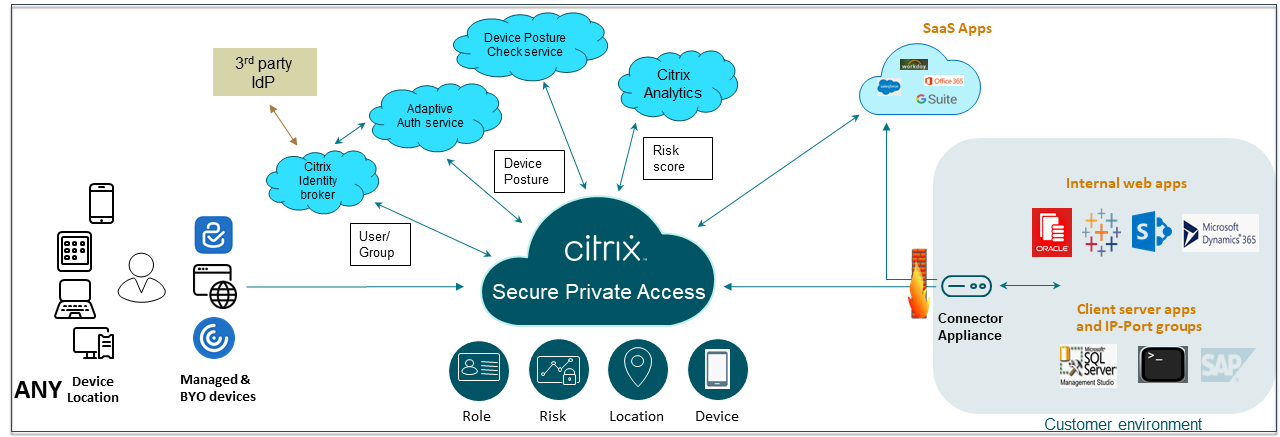
Traditional VPN solutions require end-user devices to be managed, provide access at the network level, and enforce static access control policies. Citrix Secure Private Access™ gives IT a set of security controls to protect against threats from BYO devices, giving users the choice to access their IT-sanctioned applications from any device, whether it’s managed or BYO.
Citrix Secure Private Access offers Adaptive Authentication, single sign-on support, enhanced security controls for the applications. Secure Private Access also provides the capabilities to scan the end user device before establishing a session by using the Device Posture service. Based on the Adaptive Authentication or Device Posture results, admins can define the authentication methods for the apps.
Adaptive security
Adaptive Authentication determines the right authentication flow for the current request. Adaptive Authentication can identify the device posture, geographical location, network segment, user organization/department membership. Based on the information obtained, an admin can define how they want to authenticate users to their IT sanctioned apps. This allows organizations to implement the same authentication policy framework across every resource including public SaaS apps, private web apps, private client-server apps, and Desktops as a Service (DaaS). For details, see Adaptive Security.
Application access
Secure Private Access can create a connection to the on-premises web apps without relying on a VPN. This VPN-less connection uses an on-premises deployed Connector Appliance. The Connector Appliance creates an outbound control channel to the organization’s Citrix Cloud subscription. From there, Secure Private Access can tunnel connections to the internal web apps without the need for a VPN. For details, see Application Access.
Single sign-on
With Adaptive Authentication, organizations can provide strong authentication policies to help reduce the risk of compromised user accounts. The single sign-on capabilities of Secure Private Access use the same Adaptive Authentication policies for all SaaS, private web, and client-server apps. For details, see Single Sign-On.
Browser security
Secure Private Access enables end users to safely browse the internet with a centrally managed and secured enterprise browser. When an end user launches a SaaS or private web app, several decisions are dynamically made to decide how best to serve this application. For details, see Browser Security.
Device posture
Device posture service allows an admin to define policies to check the posture of endpoint devices trying to access corporate resources remotely. Based on the compliance status of an endpoint, the device posture service can deny access or provide restricted/full access to corporate applications and desktops.
When an end user initiates a connection with Citrix Workspace™, the Device Posture client collects information about the endpoint parameters and shares this information with the Device Posture service to determine if the posture of the endpoint meets policy requirements.
The integration of the Device Posture service with Citrix Secure Private Access enables secure access to SaaS, Web, TCP and UDP apps from anywhere, delivered with the resiliency and scalability of Citrix Cloud. For details, see Device Posture.
Support for TCP and UDP applications
Sometimes remote users need access to private client-server apps that have their front-end on the endpoint and their back-end in a data center. Organizations can rightfully enforce strict security policies around these internal and private apps, making it difficult for remote users to access these applications without compromising security protocols.
Secure Private Access service addresses the TCP and UDP security vulnerabilities by enabling ZTNA to deliver secure access to these apps. Users can now access all private apps including TCP, UDP, and HTTPS apps either using a native browser or a native client application via the Citrix Secure Access™ client running on their machines.
Users must install the Citrix Secure Access client on their client devices.
- For Windows, the client version (22.3.1.5 and later) can be downloaded from https://www.citrix.com/downloads/citrix-secure-access/.
- For macOS, the client version (22.02.3 and later) can be downloaded from the App Store.
For details, see Support for client-server apps.
Set up Citrix Secure Private Access
Enable zero trust network access to SaaS apps, internal web apps, TCP, and UDP apps using the Secure Private Access admin console. This console includes configuration of Adaptive Authentication, applications including user subscription and adaptive access policies.
Set up identity and authentication
Select the authentication method for the subscribers to log in to Citrix Workspace. Adaptive Authentication is a Citrix Cloud™ service that enables advanced authentication for customers and users logging in to Citrix Workspace.
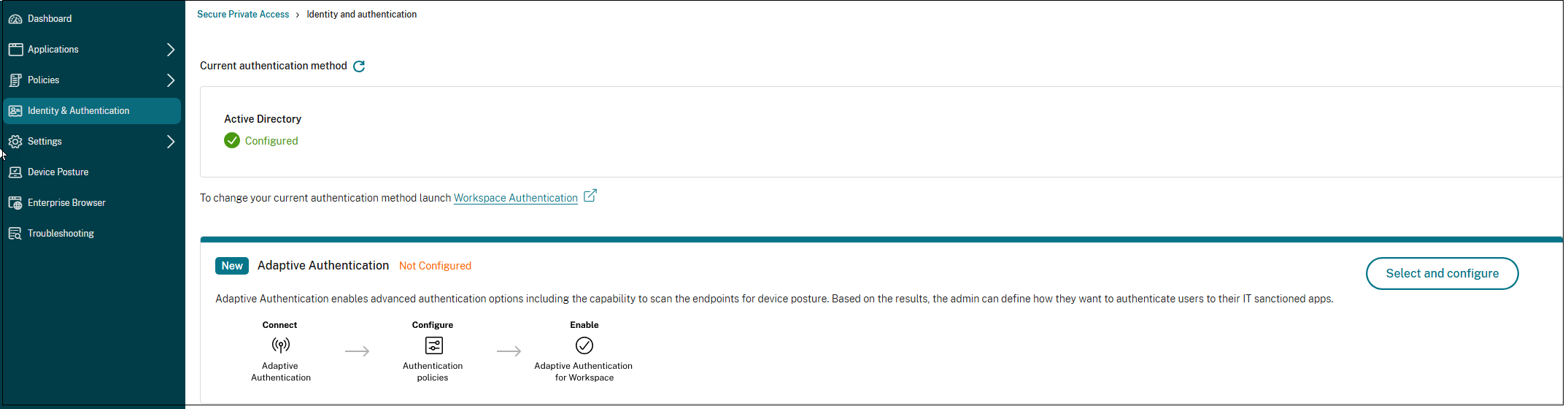
For details, see Set up identity and authentication.
Enumerate and publish apps
After you have selected the authentication method, configure the Web, SaaS, or the TCP and UDP apps using the admin console. For details, see Add and manage apps.
Enable enhanced security controls
To protect content, organizations incorporate enhanced security policies within the SaaS applications. Each policy enforces a restriction on the Citrix Enterprise Browser™ when using Workspace app for desktop or on Secure Browser when using Workspace app web or mobile.
- Restrict clipboard access: Disables cut/copy/paste operations between the app and the system clipboard.
- Restrict printing: Disables the ability to print from within the Citrix Enterprise Browser.
- Restrict downloads: Disables the user’s ability to download from within the app.
- Restrict uploads: Disables the user’s ability to upload within the app.
- Display watermark: Displays a watermark on the user’s screen displaying the user name and IP address of the user’s machine.
- Restrict key logging: Protects against key loggers. When a user tries to log on to the app using the user name and password, all the keys are encrypted on the key loggers. Also, all activities that the user performs on the app are protected against key logging. For example, if app protection policies are enabled for Office 365 and the user edit an Office 365 word document, all key strokes are encrypted on key loggers.
- Restrict screen capture: Disables the ability to capture the screens using any of the screen capture programs or apps. If a user tries to capture the screen, a blank screen is captured.
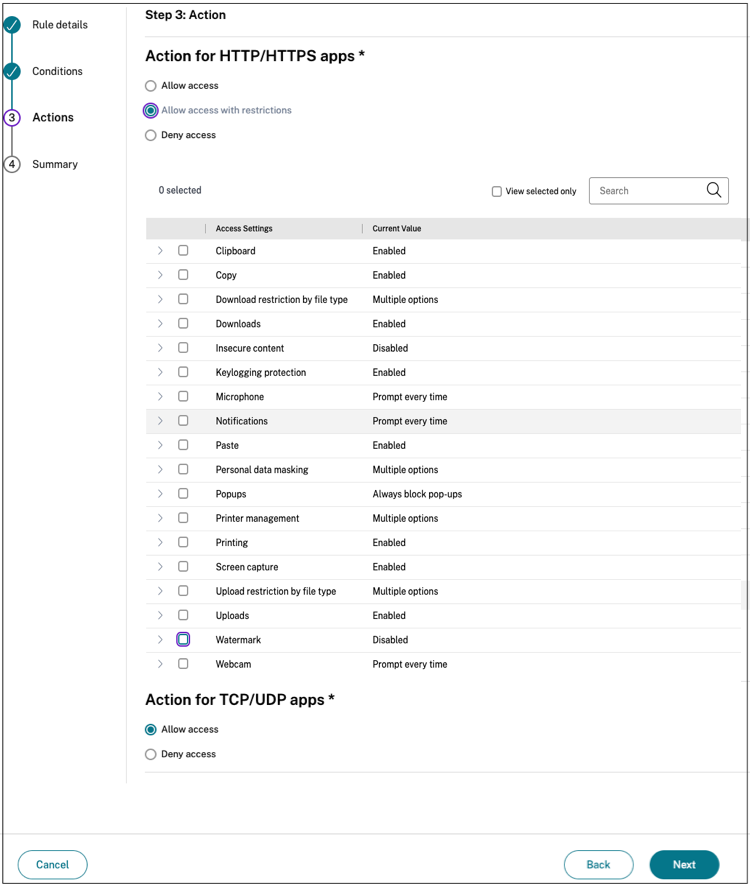
For details, see Configure an access policy.
Enable Citrix Enterprise Browser for application launches
Secure Private Access enables end users to launch their apps using the Citrix Enterprise Browser (CEB). CEB is a chromium-based browser integrated with the Citrix Workspace app that enables a seamless and secure access experience to access web and SaaS apps within Citrix Enterprise Browser.
CEB can be configured as preferred browser or as your work browser for all the internally hosted web apps or SaaS apps with security policies. CEB allows users to open all configured SaaS/web app domains inside a secure and controlled environment.
Enable Citrix Enterprise Browser
Administrators can use Global App Configuration service (GACS) to configure Citrix Enterprise Browser as the default browser to launch web and SaaS apps from the Citrix Workspace app.
Configuration through API:
To configure, here is an example JSON file to enable Citrix Enterprise Browser for all apps, by default:
"settings": [
{
"name": "open all apps in ceb",
"value": "true"
}
]
<!--NeedCopy-->
The default value is true.
Configuration through GUI:
Select the devices for which CEB must be made the default browser for the app launches.
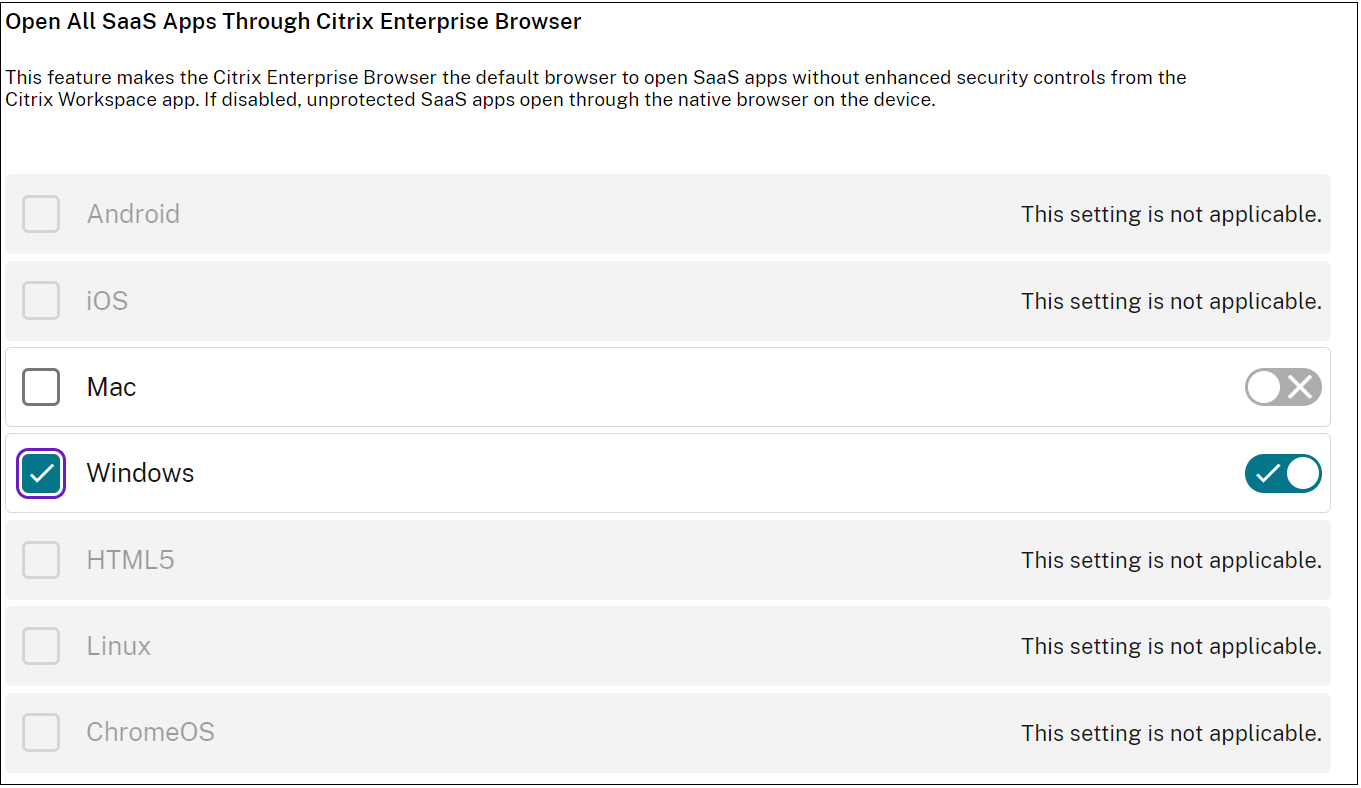
For details, see Manage Citrix Enterprise Browser through GACS.
Configure tags for contextual access using Device Posture
After the device posture verification, the device is allowed to log in and the device is classified as compliant or non-compliant. This classification is made available as tags to the Secure Private Access service and are used to provide contextual access based on device posture.
- Sign into Citrix Cloud.
- On the Secure Private Access tile, click Manage.
- Click Access Policies on the left navigation and then click Create policy.
- Enter the policy name and description of the policy.
- In Applications, select the app or set of apps on which this policy must be enforced.
- Click Create Rule to create rules for the policy.
- Enter the rule name and a brief description of the rule, and then click Next.
- Select the users’ conditions. The Users condition is a mandatory condition to be met to grant access to the applications for the users.
- Click + to add device posture condition.
- Select Device posture check and the logical expression from the drop-down menu.
-
Enter one of the following values in custom tags:
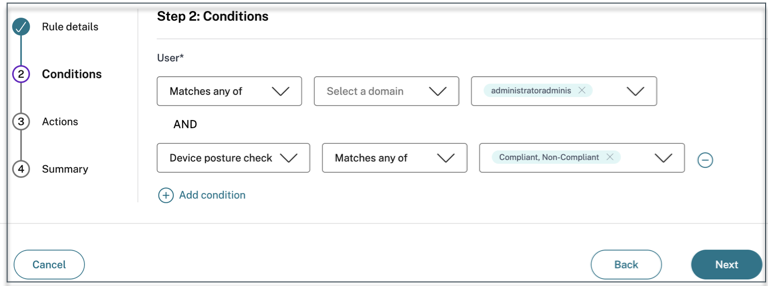
- Compliant - For compliant devices
- Non-Compliant - For non-compliant devices
- Click Next.
-
Select the actions that must be applied based on the condition evaluation, and then click Next.
The Summary page displays the policy details.
- Verify the details and click Finish.
Note:
Any Secure Private Access application which is not tagged as compliant or non-compliant in the access policy is treated as the default application and is accessible on all the endpoints regardless of device posture.
End-user experience
The Citrix administrator has the power to extend security control with the help of Citrix Secure Private Access. Citrix Workspace app is an entry point to access all resources securely. End users can access virtual apps, desktops, SaaS apps, and files through Citrix Workspace app. With Citrix Secure Private Access, administrators can control how a SaaS Application is accessed by the end user via Citrix Workspace Experience web UI or native Citrix Workspace app client.
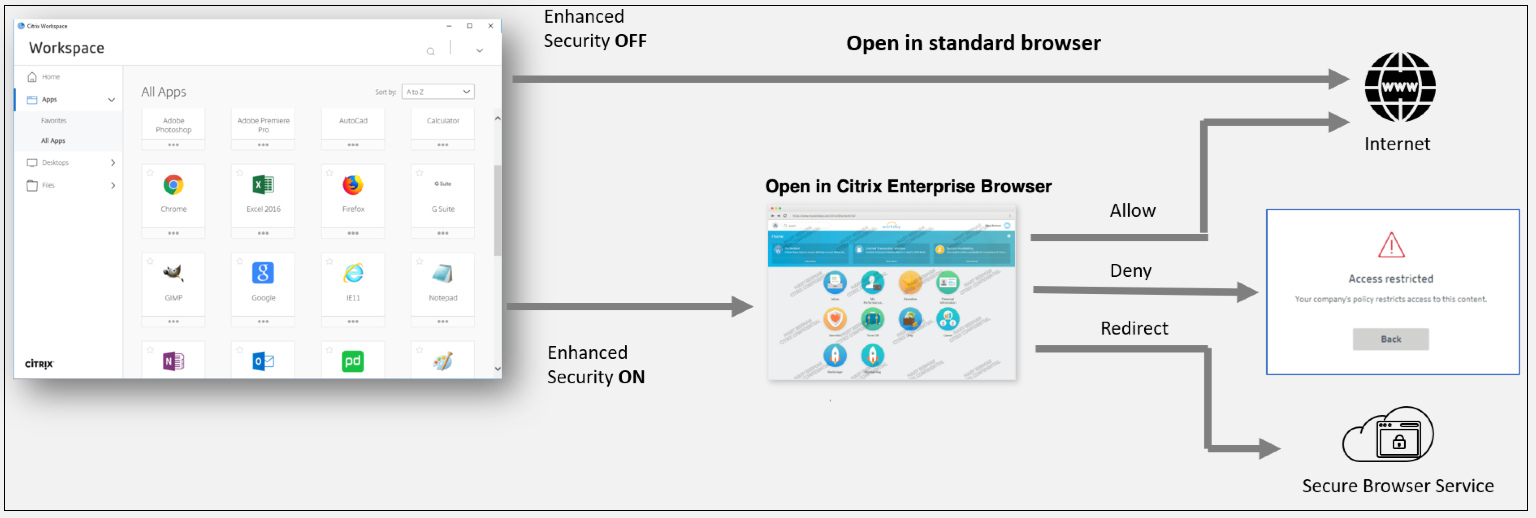
When the user launches the Workspace app on the endpoint, they see their applications, desktops, files, and SaaS apps. If a user clicks the SaaS application when enhanced security is disabled, the application opens in a standard browser which is locally installed. If the administrator has enabled enhanced security, then the SaaS apps open on the CEB within the Workspace app. Accessibility to hyperlinks within SaaS apps and web apps is controlled based on the unsanctioned websites policies. For details on Unsanctioned websites, see Unsanctioned websites.
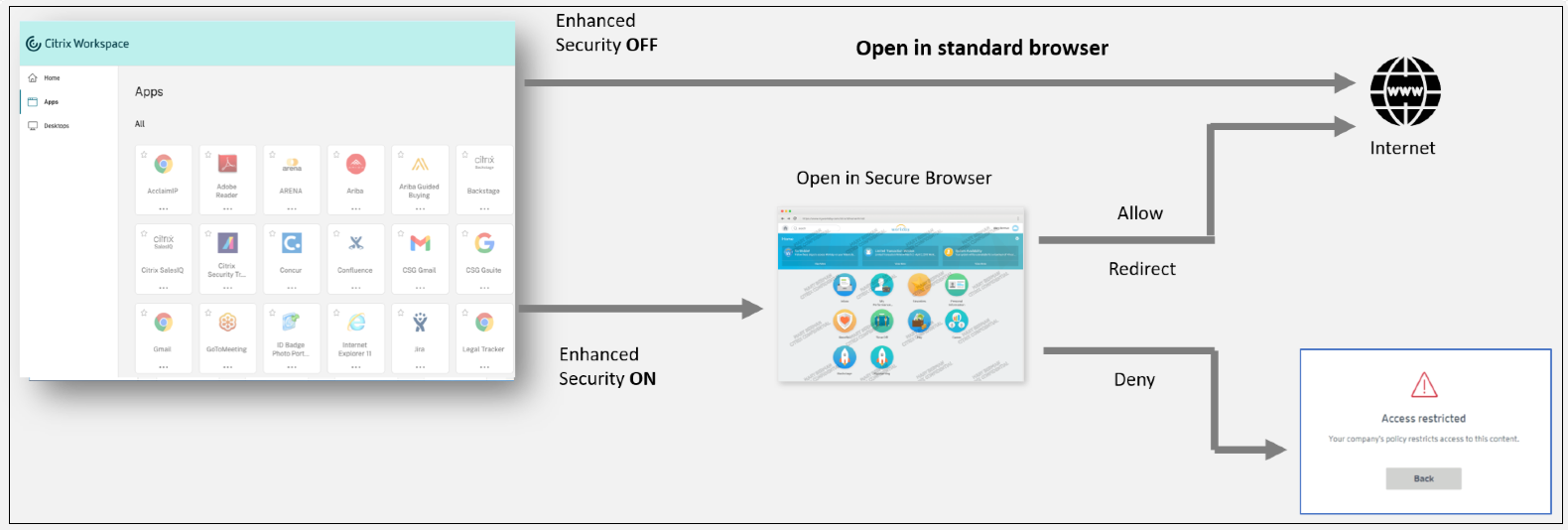
Similarly, with the Workspace Web portal, when enhanced security is disabled, SaaS applications are opened in a standard browser which is natively installed. When enhanced security is enabled, SaaS apps are opened in the secure Remote Browser. Users can access the websites within SaaS apps based on the unsanctioned websites policies. For details on Unsanctioned websites, see Unsanctioned websites.
Analytics dashboard
The Secure Private Access service dashboard displays the diagnostics and usage data of the SaaS, Web, TCP, and UDP apps. The dashboard provides admins full visibility into their apps, users, connectors health status, and bandwidth usage in a single place for consumption. This data is fetched from Citrix Analytics. The metrics are broadly classified into the following categories.
- Logging and troubleshooting
- Users
- Applications
- Access policies
For details, see Dashboard.
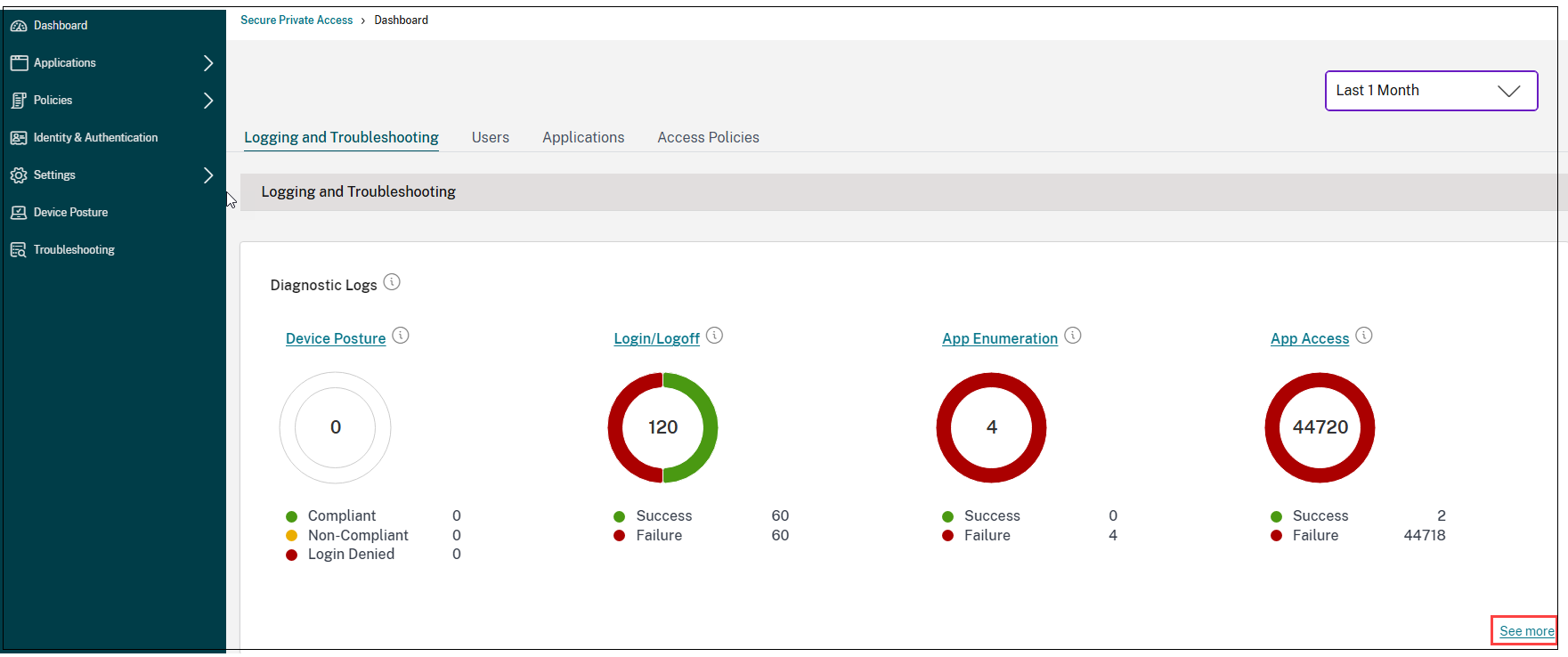
Troubleshoot app issues
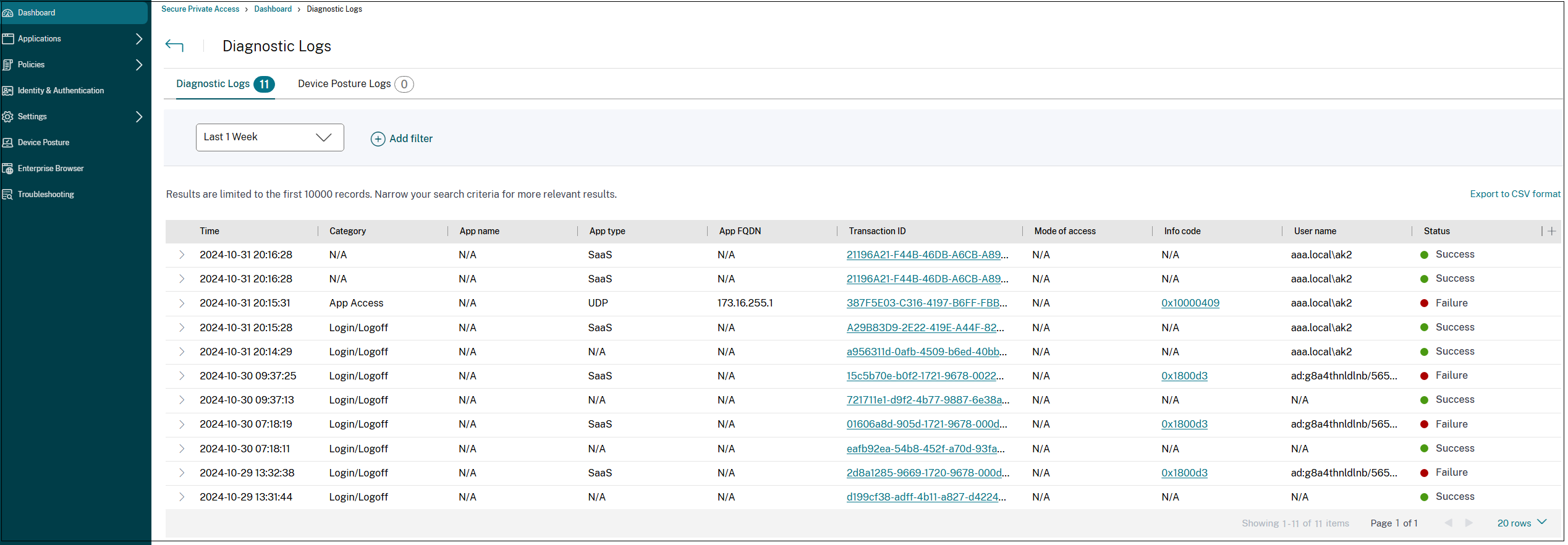
The Diagnostics Logs chart in the Secure Private Access dashboard provides visibility into the logs related to authentication, application launch, app enumeration, and device posture logs.
- Info code: Some log events such as failures have an associated info code. Clicking the info code redirects the users to the resolution steps or more information about that event.
- Transaction ID: The diagnostic logs also display a transaction ID that correlates all Secure Private Access logs for an access request. One app access request can have multiple logs generated, starting from authentication, then app enumeration within the workspace app, and then app access itself. All these events generate their own logs. Transaction ID is used to correlate all of these logs. You can filter the diagnostic logs using the transaction ID to find all logs related to a particular app access request. For details, see Troubleshoot Secure Private Access issues.
Sample use cases
- Access internal applications (Web/TCP/UDP) using a Zero-Trust approach without opening incoming traffic on the firewall
- Move to a Zero-Trust approach by discovering applications accessed by users
- Restrict access to SaaS applications to Citrix Enterprise Browser
- Restrict access to SaaS applications to company-owned public IP addresses
- Enhanced Security to Azure-managed SaaS Apps
- Enhanced Security to Office 365
- Enhanced Security to Okta Apps
Reference articles
- Introduction to Secure Private Access
- Tech brief
- Reference Architecture
- Citrix Enterprise Browser
- Manage Citrix Enterprise Browser through GACS
- Admin-guided workflow for easy onboarding and set up
Reference videos
- Zero trust network access (ZTNA) to apps
- Private Web app access with Citrix Secure Private Access
- Public SaaS app access with Citrix Secure Private Access
- Private client-server app access with Citrix Secure Private Access
- Keylogger Protection with Citrix Secure Private Access
- Screen sharing protection with Citrix Secure Private Access
- End-user experience with Citrix Secure Private Access
- ZTNA versus VPN logon experience with Citrix Secure Private Access
- ZTNA versus VPN port scans with Citrix Secure Private Access
What’s new in related products
- Citrix Enterprise Browser: About this release
- Citrix Workspace: What’s new
- Citrix DaaS: What’s new
- Citrix Secure Access client NetScaler Gateway Clients