-
Integration with Google Chrome Enterprise Premium
-
Apps configuration and management
-
Citrix Enterprise Browser to Chrome Enterprise Premium migration
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Use case: Configure an access policy to allow selective access to apps
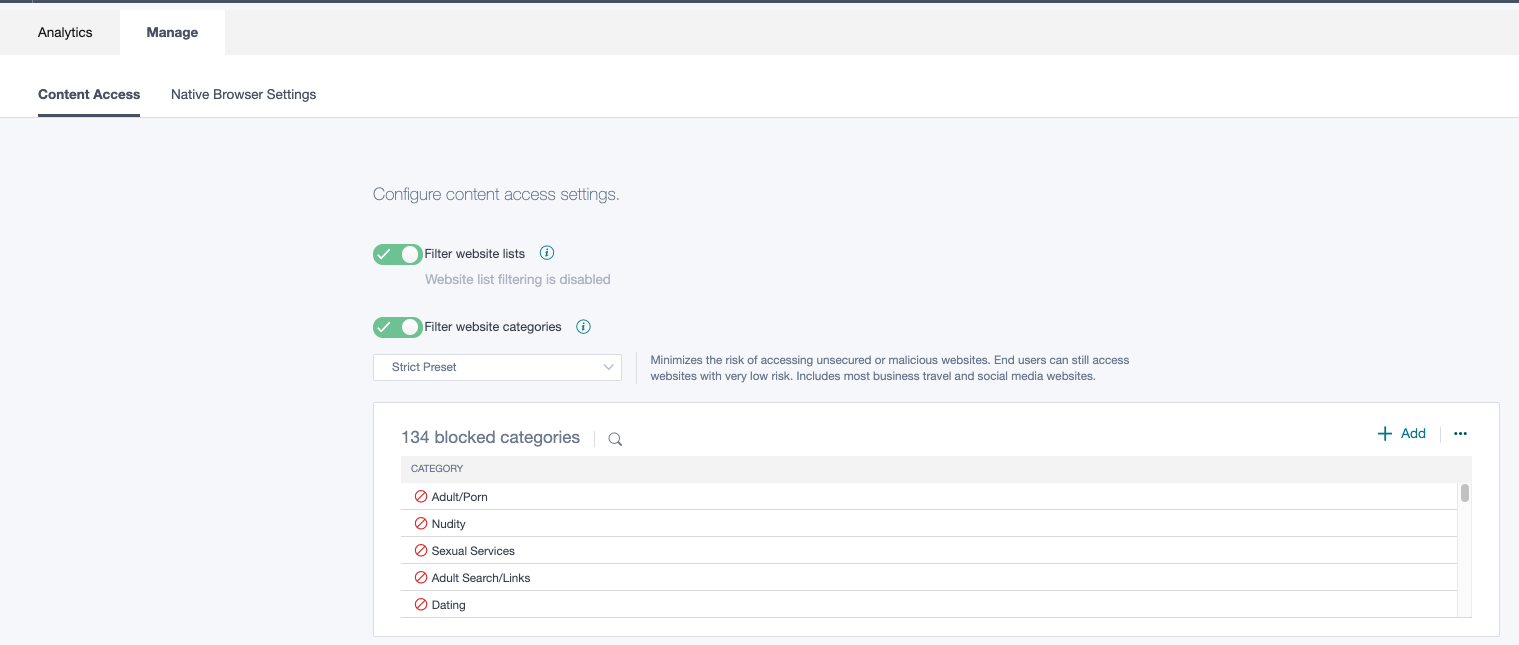
Some organizations want to restrict access to web based email or social networking sites, as a policy, for security or other reasons. To configure this, they can select strict preset in the website filter categories. Strict preset minimizes the risk of accessing unsecured or malicious websites. End users can still access websites with low risk.
If your organization policy mandates strict preset, but wants to allow selective access to apps that are not productivity related, but are required for social interaction, follow these steps to configure settings in the Citrix Secure Private Access™ service. In the following configuration, the strict preset is selected, but is customized so that access to Facebook groups is allowed, and access to the instagram is through a secure browser.
-
Log on to Citrix Cloud.
-
On the Citrix Secure Private Access tile, click Manage.
-
Click Configure Content Access.
-
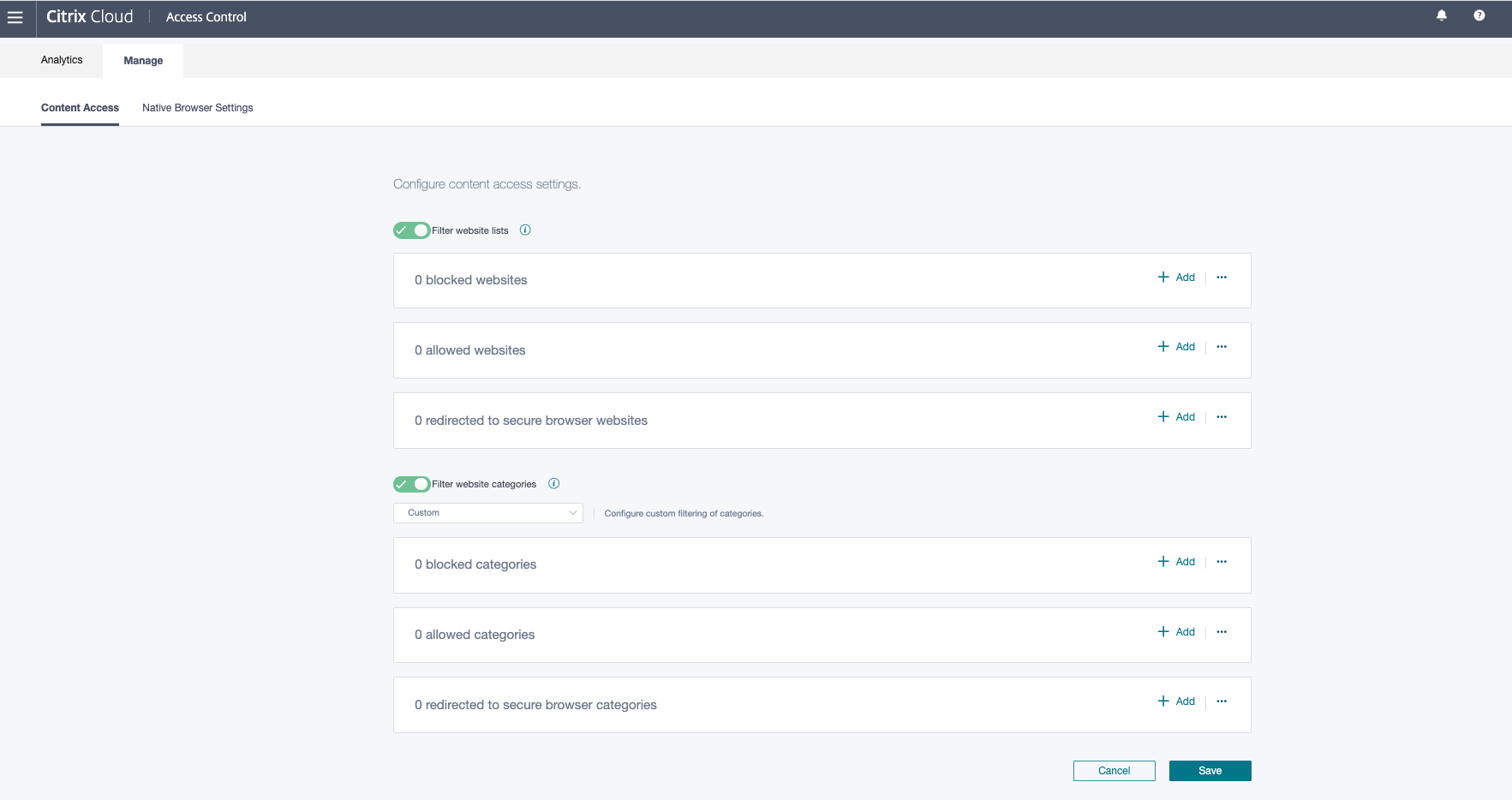
Enable Filter website categories.
-
Select Strict Preset.
-
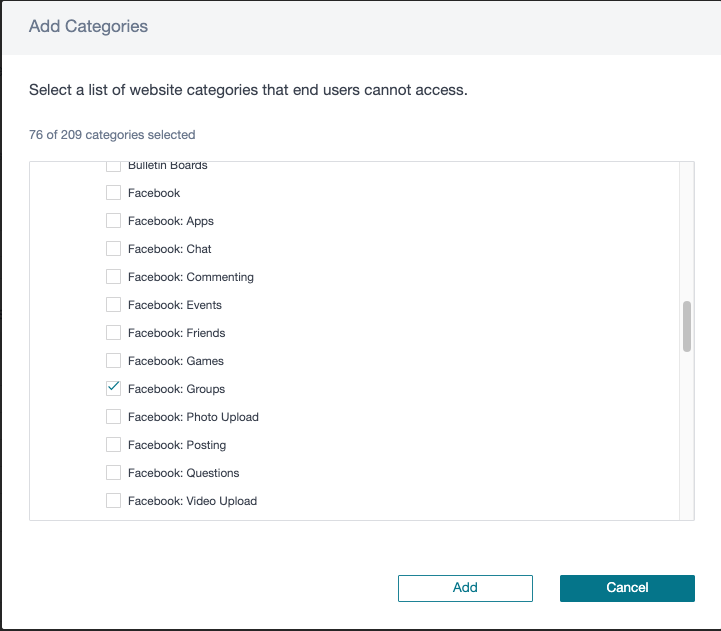
In the allowed categories section, click Add. In Add Categories, select Facebook Groups. Click Add.
-
In the redirected to secure browser categories section, click Add. In Add Categories, select Instagram. Click Add.
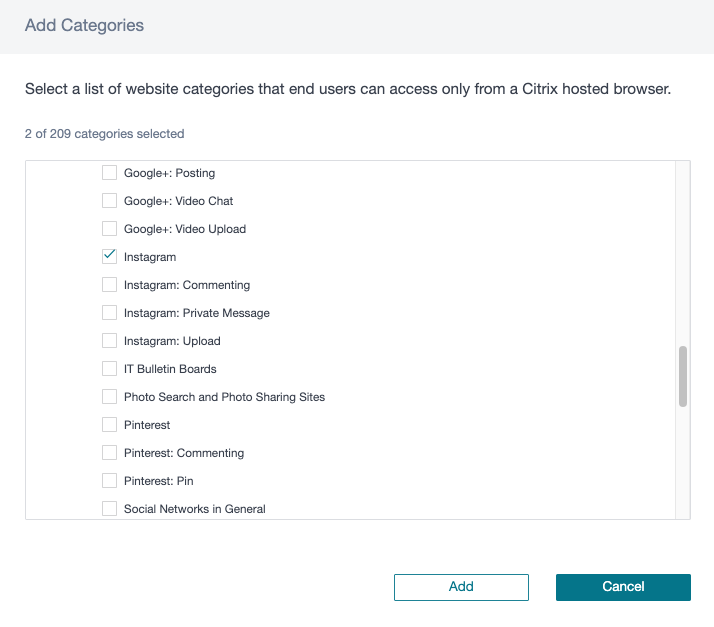
-
Your settings appear in the allowed and redirect categories. Click Save.
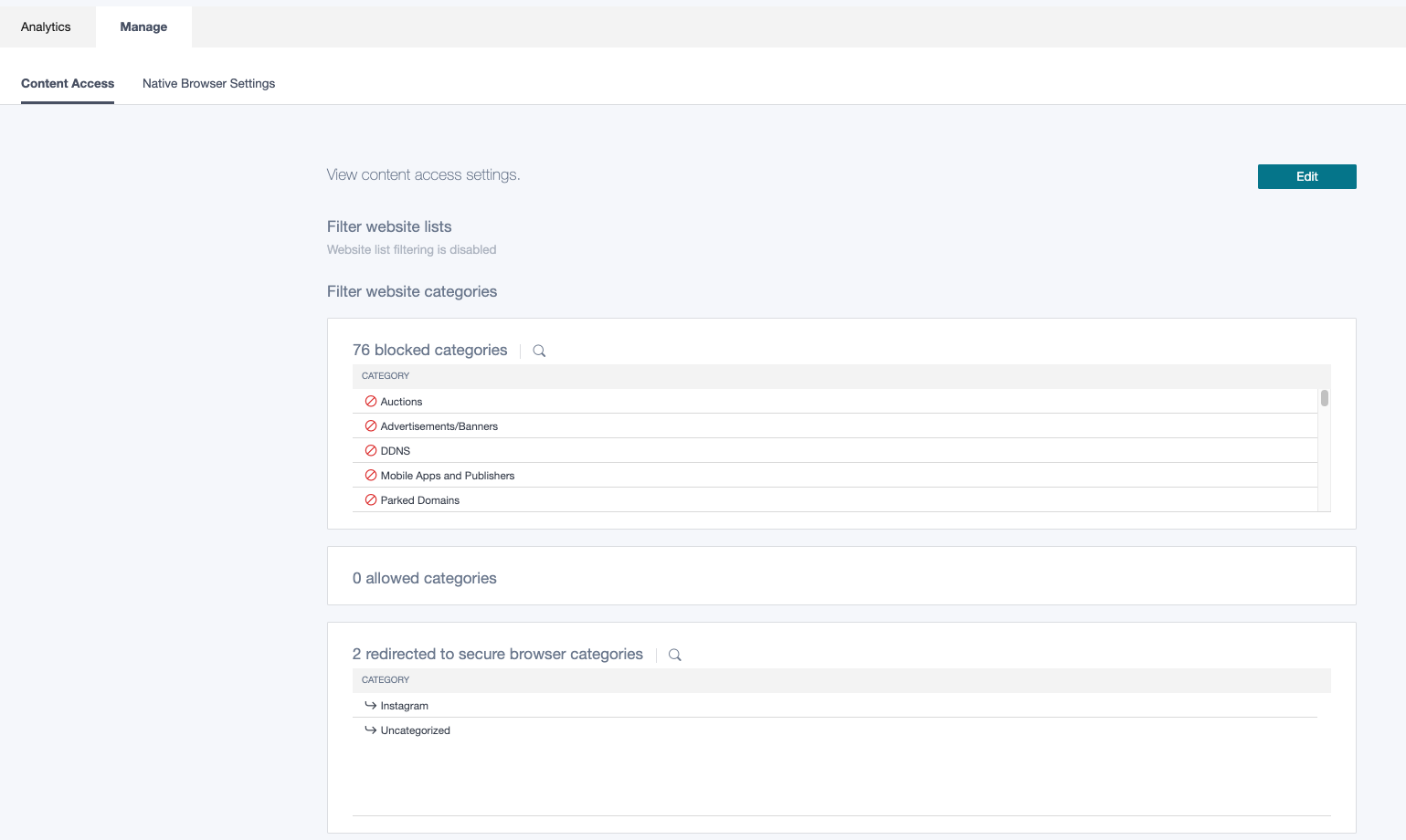
Validation
To validate your configuration, you can publish a SaaS app for https://www.google.com with single sign-on disabled and have some users subscribed to the app.
- Launch the SaaS app from Citrix Workspace™ app (or Citrix Workspace web).
- After the app opens, search for Facebook, and click the link returned in the search. You must see the app launch.
- Search for Instagram, and click the link returned in the search. You must see the app launch in a secure browser.
- Search for any URL in the blocked category, and click the link returned. You must get access denied.
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.