This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
XenMobile Server 10.15 Current Release
XenMobile Server is an on-premises enterprise mobility management solution that offers mobile device management (MDM) and mobile application management (MAM).
The mobile productivity apps are productivity and communication apps that are offered as a part of the XenMobile solution. For information about the mobile productivity apps, see mobile productivity apps.
The cloud service version of XenMobile Server is called Citrix Endpoint Management. For information specific to the XenMobile cloud offering, see Citrix Endpoint Management.
XenMobile Migration Service
If you’re using XenMobile Server on-premises, our Migration Services team can get you started with Endpoint Management. Citrix Endpoint Management provides secure and simplified device enrollment, configuration, and administration of endpoints using the Cloud environment. For information, see Simplicity with Citrix Endpoint Management Service.
To start migration, contact your local Citrix salesperson or Citrix partner.
Prerequisites
-
XenMobile Server:
- One of the latest three versions of the on-premises XenMobile Server deployment
- A local administrator account
- PKI passwords
- Valid XenMobile Server SSL Listener certificate. The certificate can’t be a wildcard and must not expire for at least six months.
-
Citrix Cloud:
- Citrix Cloud account
- Citrix Cloud Connectors installed on at least two dedicated machines running Windows Server 2012 R2 or later. For details, see Citrix Cloud Connector.
- Windows Server 2008 R2 or later to support forest and domain functional levels in Active Directory
-
XenMobile database requirements:
- Microsoft SQL Server 2014 SP3 or later: Endpoint Management requires that you provide the on-premises SQL service account password. For more information about the database requirements and compatibility, see System requirements.
- SQL Server Management Studio: Endpoint Management requires the latest version of SQL Server Management Studio to create a BACPAC file.
- Citrix ADC: To test MAM functionality, Endpoint Management requires a separate Citrix ADC appliance.
- Connection scheduling device policy: Prior to migration, configure the connection scheduling device policy to require a connection for 2 hours or more. We recommend that you use Firebase Cloud Messaging to control connections between Endpoint Management and Android, Android Enterprise, and Chrome OS devices. For more information, see Connection scheduling device policy and Firebase Cloud Messaging.
The following diagram shows the Endpoint Management migration flow:
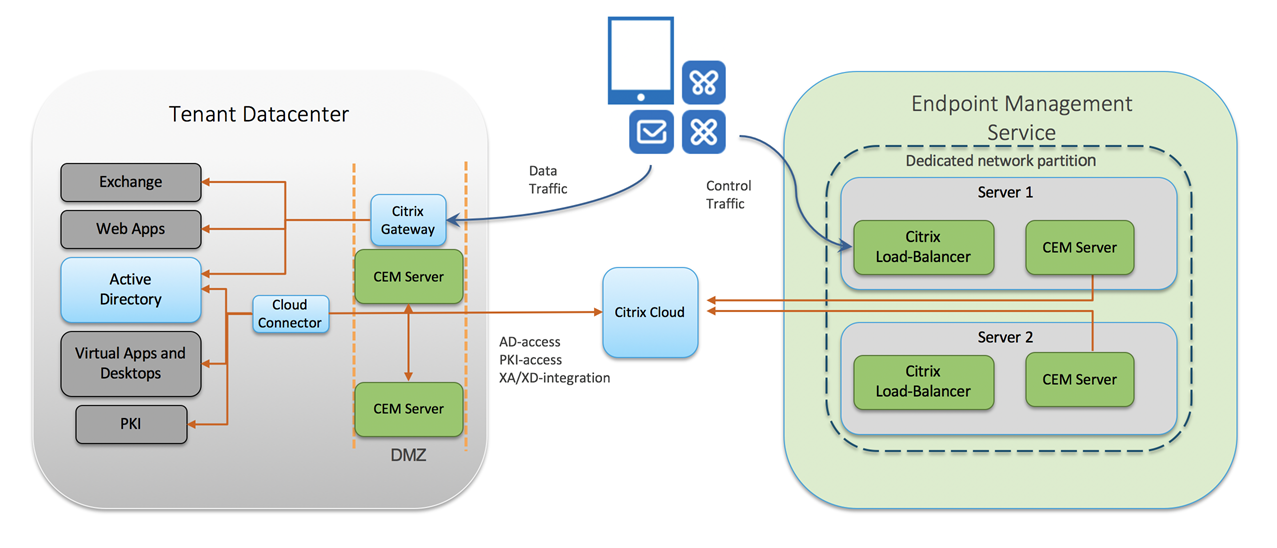
The migration process includes the following steps:
- Citrix assesses the customer’s on-premises environment to determine the best migration experience.
- The customer creates a BACPAC file that has data from the on-premises database.
- After the customer provides a BACPAC file, the Migration Services team assists the customer with the conversion of the database into a cloud-ready environment.
- To support single sign-on across all applications, the Migration Services team helps the customer configure Citrix Gateway.
- For the final stage of migration, the customer has two options:
- Test drive: Using a limited number of test devices, the customer points the devices to our cloud-hosted DNS to connect them with Endpoint Management. The migration from XenMobile Server to Citrix Endpoint Management doesn’t require the customer to re-enroll end user devices.
- Production switchover: The customer creates a CNAME record that acts as a subdomain for load balancing in the Cloud. The customer’s enrollment URL remains unchanged.
More information
These blogs discuss the XenMobile Migration service:
Current and prior version of XenMobile
For the XenMobile Server and apps, Citrix supports the current and prior versions of XenMobile, including Rolling Patches. The current version is 10.15, and the prior version is 10.14. For all security-related fixes, you must upgrade to the latest version of XenMobile Server. The latest software is available at the XenMobile Server 10 download page.
For a list of new features, known issues, and fixed issues in the current and prior versions of XenMobile Server, see:
- XenMobile Server 10.15: What’s new, Fixed issues, and Known issues
- What’s new in XenMobile Server 10.14
For PDFs of the documentation for all versions earlier than the most recent version, see the Archive List of Legacy Documents.
XenMobile 9. This version reached the End of Life (EOL) lifecycle status from June 30, 2017. When a product release reaches EOL, you can use the product within the terms of your product licensing agreement, but the available support options are limited. Historical information appears in the Knowledge Center or other online resources. The documentation is no longer updated and is provided on an as-is basis. For more information about product lifecycle milestones, see the Product Matrix.
For five years beyond the EOL date, you can download a PDF of the XenMobile 9 documentation from the Archive List of Legacy Documents.
For information about moving from XenMobile 9 to XenMobile Service via Citrix Cloud, see this Citrix.com blog.
Upgrades
For important information about upgrades, see What’s new.
To do the upgrade, download the latest binary available: Go to https://www.citrix.com/downloads. Navigate to Citrix Endpoint Management (and Citrix XenMobile Server) > XenMobile Server (on-premises) > Product Software > XenMobile Server 10. On the tile for the XenMobile Server software for your hypervisor, click Download File.
For more information about upgrading from XenMobile 10.14.x or 10.13.x, see Upgrade.
To install the latest version of XenMobile Server, see Install and configure.
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.