Authentication
You can configure various types of authentication for your Citrix Workspace app including domain pass-through (single sign-on or SSON), smart card, and Kerberos pass-through.
Starting with Citrix Workspace™ app for Windows version 2503, the system installs SSON by default in dormant mode. You can enable SSON post-installation using the Group Policy Object (GPO) policy. To enable, navigate to User Authentication > Local user name and password and select the Enable pass-through authentication checkbox.
Note:
You must reboot the system after updating the GPO policy for the SSON setting to take effect.
Authentication tokens
Authentication tokens are encrypted and stored on the local disk so that you don’t need to reenter your credentials when your system or session restarts. Citrix Workspace app provides an option to disable the storing of authentication tokens on the local disk.
For enhanced security, we now provide a Group Policy Object (GPO) policy to configure the authentication token storage.
You can download the Citrix ADMX/ADML templates for Group Policy Editor from the Download page of Citrix.
Note:
This configuration is applicable only in cloud deployments.
To disable storing of authentication tokens using the Group Policy Object (GPO) policy:
- Open the Citrix Workspace app Group Policy Object administrative template by running
gpedit.msc. - Under the Computer Configuration node, go to Administrative Templates > Citrix Components > SelfService.
-
In the Store authentication tokens policy, select one of the following:
- Enabled: Indicates that the authentication tokens are stored on the disk. By default, set to Enabled.
- Disabled: Indicates that the authentication tokens aren’t stored on the disk. Reenter your credentials when your system or session restarts.
- Click Apply and OK.
Starting with Version 2106, Citrix Workspace app provides another option to disable the storing of authentication tokens on the local disk. Along with the existing GPO configuration, you can also disable the storing of authentication tokens on the local disk using the Global App Configuration service.
In the Global App Configuration Service, set the Store Authentication Tokens attribute to False.
You can configure this setting using the Global App Configuration service in one of the following methods:
- Global App Configuration service User Interface (UI): To configure using UI, see Configure Citrix Workspace app
- API: To configure settings using APIs, see the Citrix Developer documentation.
Configuration Checker
Configuration Checker lets you run a test to check if the single sign-on is configured properly. The test runs on different checkpoints of the single sign-on configuration and displays the configuration results.
- Right-click the Citrix Workspace app icon in the notification area and click Advanced Preferences. The Advanced Preferences dialog appears.
-
Click Configuration Checker. The Citrix Configuration Checker window appears.
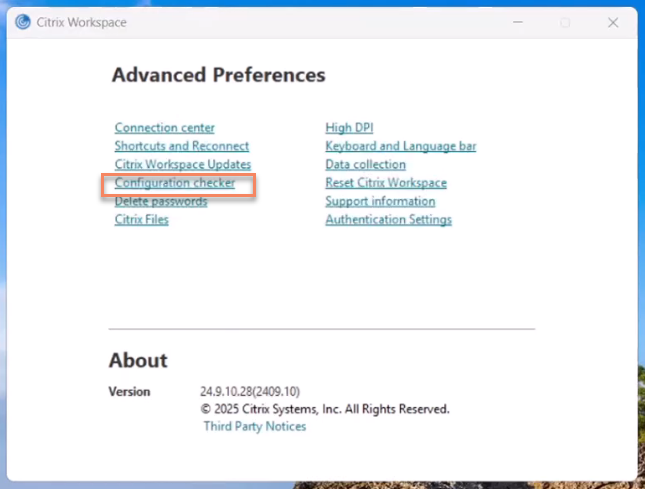
- Select SSONChecker from the Select pane.
- Click Run. A progress bar appears, displaying the status of the test.
The Configuration Checker window has the following columns:
-
Status: Displays the result of a test on a specific check point.
- A green check mark indicates that the specific checkpoint is configured properly.
- A blue I indicates information about the checkpoint.
- A Red X indicates that the specific checkpoint isn’t configured properly.
- Provider: Displays the name of the module on which the test is run. In this case, single sign-on.
- Suite: Indicates the category of the test. For example, Installation.
- Test: Indicates the name of the specific test that is run.
- Details: Provides additional information about the test, for both pass and fail.
The user gets more information about each checkpoint and the corresponding results.
The following tests are done:
- Installed with single sign-on.
- Logon credential capture.
- Network Provider registration: The test result against Network Provider registration displays a green check mark only when “Citrix Single Sign-on” is set to be first in the list of Network Providers. If Citrix Single Sign-on appears anywhere else in the list, the test result against Network Provider registration appears with a blue I and additional information.
- A single sign-on process is running.
- Group Policy: By default, this policy is configured on the client.
- Internet Settings for Security Zones: Make sure that you add the Store/XenApp Service URL to the list of Security Zones in the Internet Options. If the Security Zones are configured via Group policy, any change in the policy requires the Advanced Preferences window to be reopened for the changes to take effect and to display the correct status of the test.
- Authentication method for StoreFront.
Note:
- If you’re accessing workspace for web, the test results aren’t applicable.
- If Citrix Workspace app is configured with multiple stores, the authentication method test runs on all the configured stores.
- You can save the test results as reports. The default report format is .txt.
Hide the Configuration Checker option from the Advanced Preferences window
- Open the Citrix Workspace app GPO administrative template by running
gpedit.msc. - Go to Citrix Components > Citrix Workspace > Self Service > DisableConfigChecker.
- Click Enabled to hide the Configuration Checker option from the Advanced Preferences window.
- Click Apply and OK.
- Run the
gpupdate /forcecommand.
Limitation:
Configuration Checker does not include the checkpoint for the configuration of trust requests sent to the XML service on Citrix Virtual Apps and Desktops™ servers.
Beacon test
Citrix Workspace app allows you to do a beacon test using the Beacon checker that is available as part of the Configuration Checker utility. The Beacon test helps to confirm if the beacon (ping.citrix.com) is reachable. Starting from Citrix Workspace app for Windows 2405 version onwards, beacon test works for all the beacons configured in the store added in Citrix Workspace app. This diagnostic test helps to eliminate one of the many possible causes for slow resource enumeration that is the beacon not being available. To run the test, right-click the Citrix Workspace app in the notification area and select Advanced Preferences > Configuration Checker. Select the Beacon checker option from the list of Tests and click Run.
The test results can be any of the following:
- Reachable – Citrix Workspace app is successfully able to contact the beacon.
- Not reachable - Citrix Workspace app is unable to contact the beacon.
- Partially reachable - Citrix Workspace app can contact the beacon intermittently.
Note:
- The test results aren’t applicable on workspace for web.
- The test results can be saved as reports. The default format for the report is .txt.
Support for Conditional Access with Azure Active Directory
Conditional Access is a tool used by Azure Active Directory to enforce organizational policies. Workspace administrators can configure and enforce Azure Active Directory conditional access policies for users authenticating to the Citrix Workspace app. The Windows machine running the Citrix Workspace app must have Microsoft Edge WebView2 Runtime version 131 or later installed.
For complete details and instructions about configuring conditional access policies with Azure Active Directory, see Azure AD Conditional Access documentation.
Note:
This feature is supported only on Workspace (Cloud) deployments.
Support for modern authentication methods for StoreFront stores
Starting with Citrix Workspace app 2303 for Windows, you can enable support for modern authentication methods for StoreFront stores using Group Policy Object (GPO) template. With Citrix Workspace app version 2305.1, you can enable this feature using Global App Configuration service.
You can authenticate to Citrix StoreFront stores using any of the following ways:
- Using Windows Hello and FIDO2 security keys. For more information, see Other ways to authenticate.
- Single sign-on to Citrix StoreFront stores from Azure Active Directory (AAD) joined machines with AAD as the identity provider. For more information, see Other ways to authenticate.
- Workspace administrators can configure and enforce Azure Active Directory conditional access policies for users authenticating to Citrix StoreFront stores. For more information, see Support for Conditional access with Azure AD.
To enable this feature, you must use Microsoft Edge WebView2 as the underlying browser for direct StoreFront and gateway authentication.
Note:
Ensure that the Microsoft Edge WebView2 Runtime version is 131 or later.
You can enable modern authentication methods for StoreFront stores using Global App Config service and Group Policy Object (GPO) template.
Using Global App Config service
To enable this feature:
- From the Citrix Cloud™ menu, select Workspace Configuration and then select App Configuration.
- Click Security & Authentication.
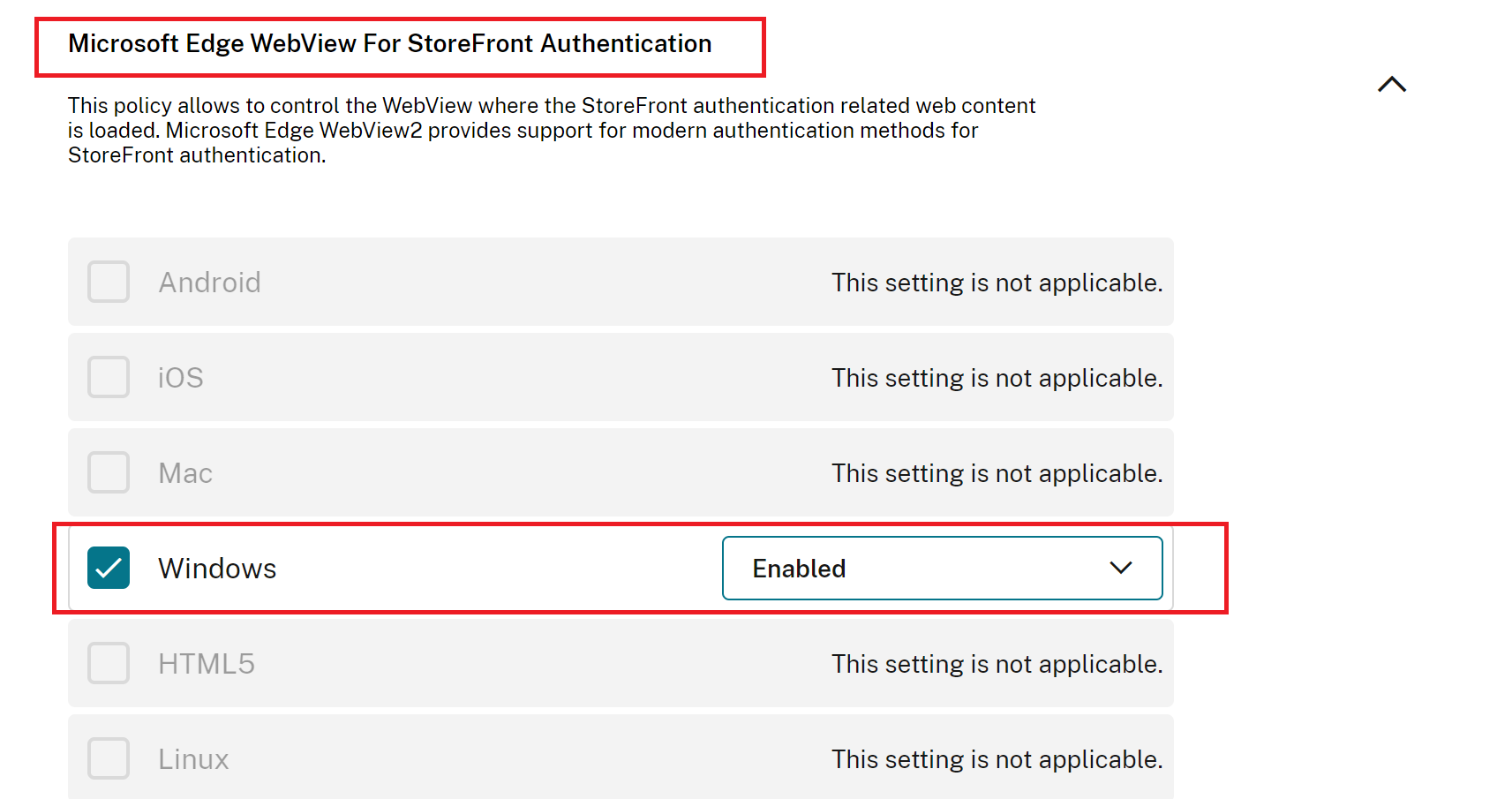
- Ensure the Windows check box is selected.
-
Select Enabled next to Windows from the Microsoft Edge WebView for StoreFront™ Authentication drop‑down list.
Note:
If you select Disabled next to Windows from the Microsoft Edge WebView for StoreFront Authentication drop‑down list, Internet Explorer WebView is used within the Citrix Workspace app. As a result, the modern authentication methods for Citrix StoreFront stores are not supported.
Using GPO
To enable this feature:
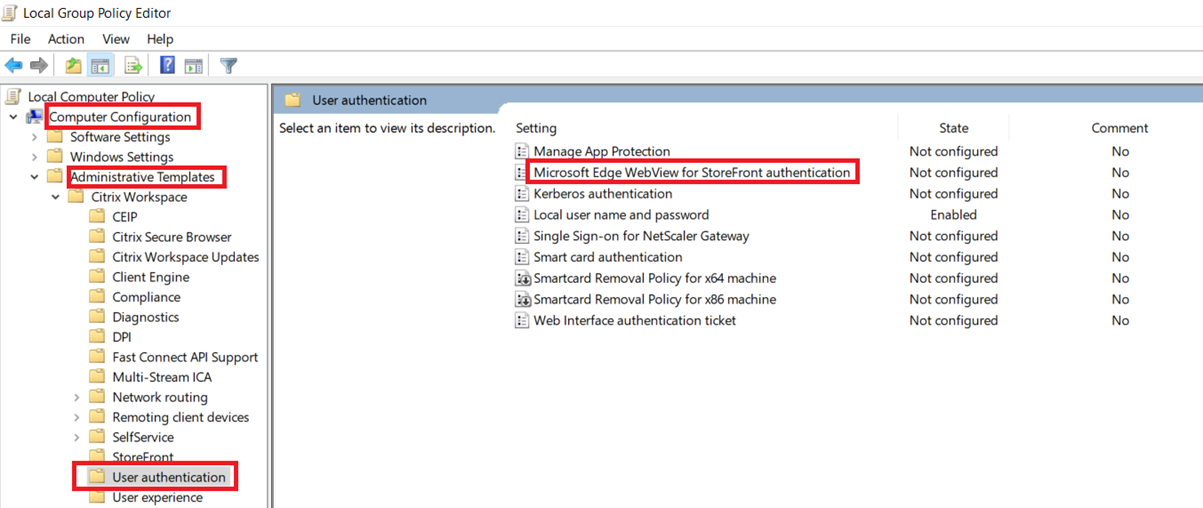
- Open the Citrix Workspace app Group Policy Object administrative template by running gpedit.msc.
- Under the Computer Configuration node, go to Administrative Templates > Citrix Workspace > User Authentication.
-
Click the Microsoft Edge WebView for StoreFront authentication policy and set it to Enabled.
- Click Apply and then OK.
When this policy is disabled, Citrix Workspace app uses Internet Explorer WebView. As a result, the modern authentication methods for Citrix StoreFront stores are not supported.
Single sign-on support for Edge WebView when using Microsoft Entra ID
Previously, when using Entra ID, authentication failed for Citrix Workspace app. Starting with 2409 version, Citrix Workspace app supports single sign-on (SSO) for Edge WebView when using Entra ID for authentication.
You can enable this feature using the UI or through Group Policy Object (GPO).
Using UI
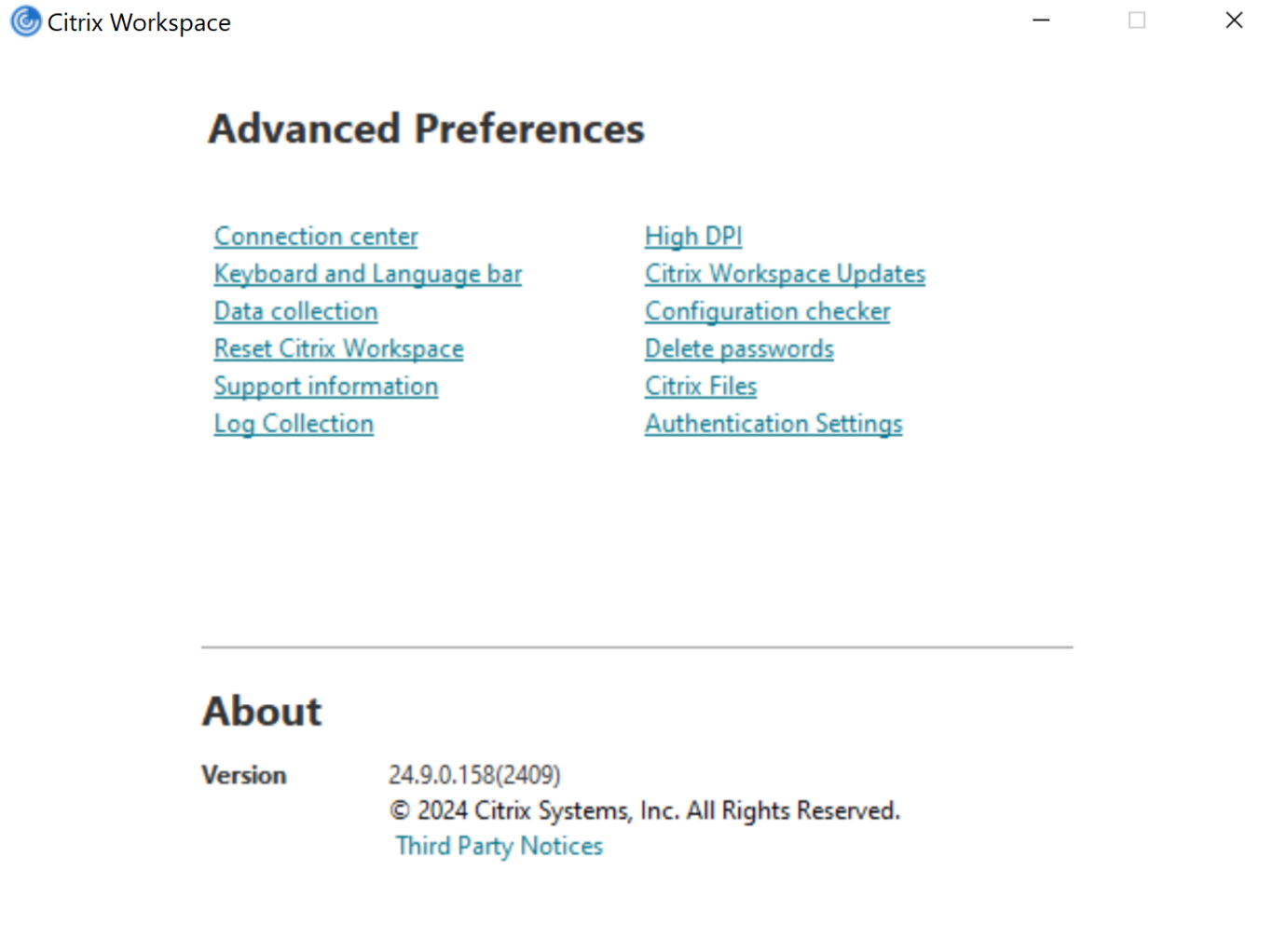
To enable the support for using single sign-on for Edge WebView, a new option called Authentication Settings is introduced in the Advanced Preferences section of the system tray in the UI.
Perform the following steps to enable the feature from the UI:
-
Click the Advanced Preferences section in the system tray. The following screen appears.
-
Click Authentication Settings. The following screen appears.
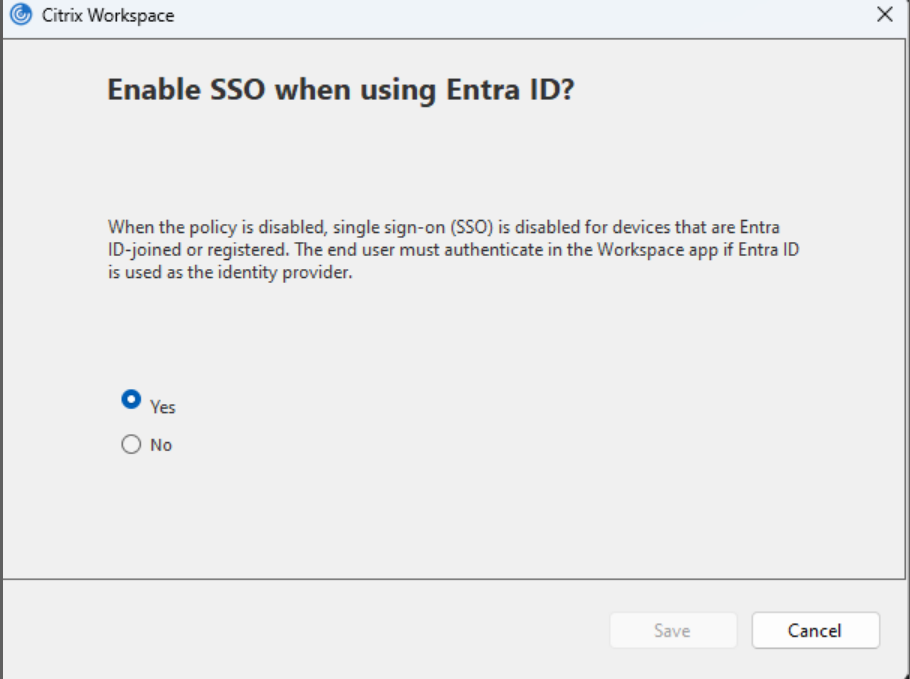
- Ensure that the option selected is Yes, which is the default option. If not, select Yes.
- Click Save if you have modified the option.
- Restart the Citrix Workspace app for the changes to take effect.
Note:
If you select No, the policy is disabled.
When the policy is disabled, single sign-on (SSO) is disabled for devices that are Microsoft Entra ID ID-joined or registered. The end user must authenticate in the Workspace app if Entra ID is used as the identity provider.
Using GPO
You can also enable the support for using single sign-on for Edge WebView using GPO.
Perform the following steps to enable the feature using GPO:
-
Open the Citrix Workspace app Group Policy Object administrative template by running
gpedit.mscand navigate to the Computer Configuration node.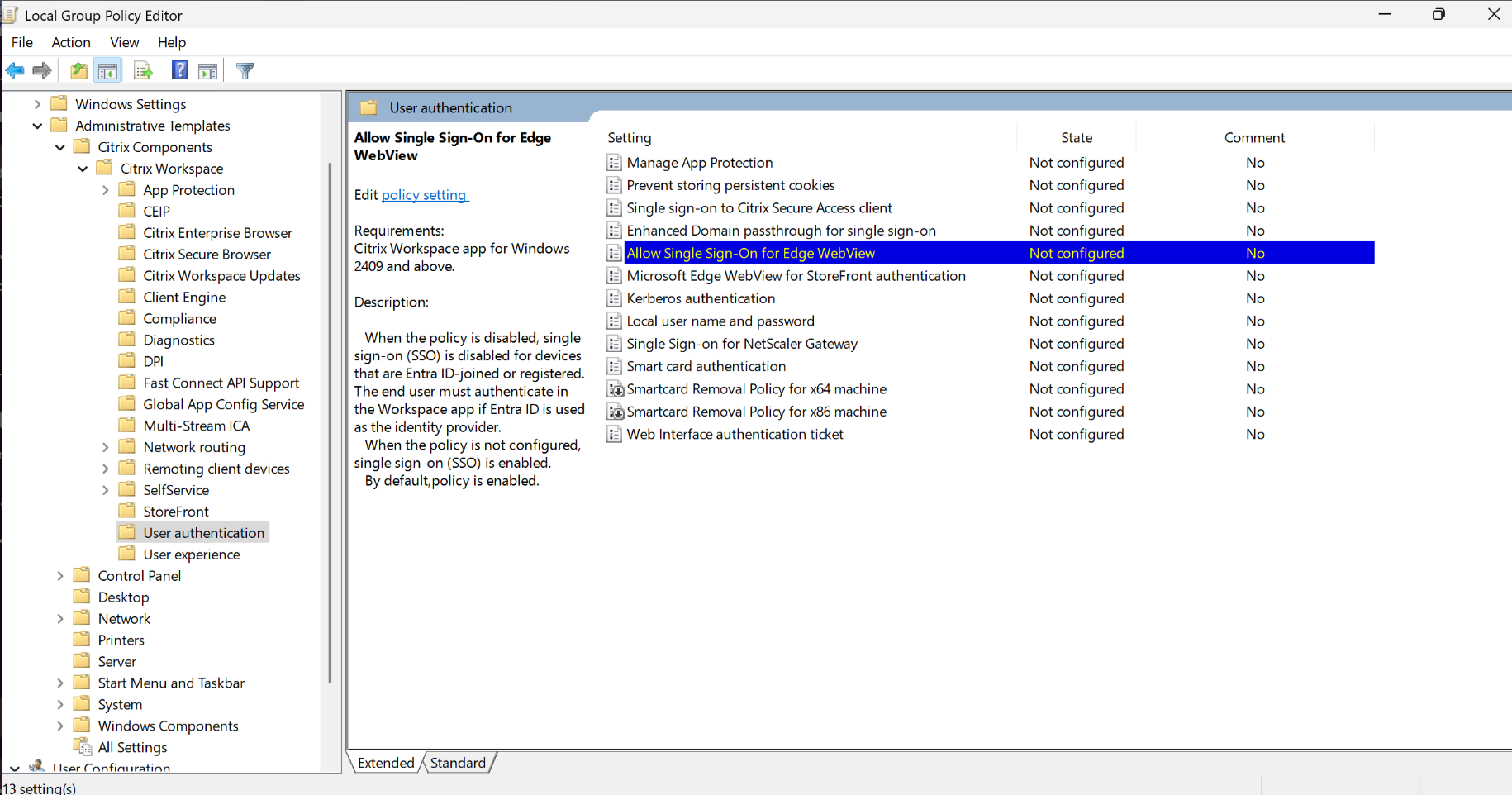
- Go to Administrative Templates > Citrix Components > Citrix Workspace > User Authentication.
- Select the Allow Single Sign-On for Edge WebView policy and set it to Enabled.
- Click Apply and OK.
Note:
If you select Disabled, the policy is disabled.
When the policy is disabled, single sign-on (SSO) is disabled for devices that are Microsoft Entra ID ID-joined or registered. The end user must authenticate in the Workspace app if Entra ID is used as the identity provider.
Other ways to authenticate
You can configure the following authentication mechanisms with the Citrix Workspace app. For the following authentication mechanisms to work as expected, the Windows machine running the Citrix Workspace app must have Microsoft Edge WebView2 Runtime version 131 or later installed.
-
Windows Hello based authentication – For instructions about configuring Windows Hello based authentication, see Configure Windows Hello for Business Policy settings - Certificate Trust.
Note:
Windows Hello based authentication with domain pass-through (single-sign-on or SSON) is not supported.
- FIDO2 Security Keys based authentication – FIDO2 security keys provide a seamless way for enterprise employees to authenticate without entering a user name or password. You can configure FIDO2 Security Keys based authentication to Citrix Workspace. If you would like your users to authenticate to Citrix Workspace with their Azure AD account using a FIDO2 security key, see Enable passwordless security key sign-in.
- You can also configure Single Sign-On (SSO) to Citrix Workspace app from Microsoft Azure Active Directory (AAD) joined machines with AAD as an identity provider. For more details about configuring Azure Active Directory Domain services, see Configuring Azure Active Directory Domain services. For information about how to connect Azure Active Directory to Citrix Cloud, see Connect Azure Active Directory to Citrix Cloud.
Smart card
Citrix Workspace app for Windows supports the following smart card authentication:
-
Pass-through authentication (single sign-on) - Pass-through authentication captures the smart card credentials when users log on to Citrix Workspace app. Citrix Workspace app uses the captured credentials as follows:
- Users of domain-joined devices who log on to Citrix Workspace app using the smart card can start virtual desktops and applications without needing to reauthenticate.
- Citrix Workspace app running on non-domain joined devices with the smart card credentials must type their credentials again to start a virtual desktop or application.
Pass-through authentication requires configuration both on StoreFront and Citrix Workspace app.
-
Bimodal authentication - Bimodal authentication offers users a choice between using a smart card and typing the user name and password. This feature is effective when you can’t use the smart card. For example, the logon certificate has expired. Dedicated stores must be set up per site to allow Bimodal authentication, using the DisableCtrlAltDel method set to False to allow smart cards. Bimodal authentication requires StoreFront configuration.
Using the Bimodal authentication, the StoreFront administrator can allow both user name and password and smart card authentication to the same store by selecting them in the StoreFront console. See StoreFront documentation.
Note:
Citrix Workspace app for Windows doesn’t support umlat character in the username and password fields.
-
Multiple certificates - Multiple certificates can be availed for a single smart card and if multiple smart cards are in use. When you insert a smart card in a card reader, the certificates are applicable to all applications running on the user device, including Citrix Workspace app.
-
Client certificate authentication - Client certificate authentication requires Citrix Gateway and StoreFront configuration.
- For access to StoreFront through Citrix Gateway, you must reauthenticate after removing the smart card.
- When the Citrix Gateway SSL configuration is set to Mandatory client certificate authentication, operation is more secure. However, mandatory client certificate authentication isn’t compatible with bimodal authentication.
-
Double hop sessions - If a double-hop is required, a connection is established between Citrix Workspace app and the user’s virtual desktop.
-
Smart card-enabled applications - Smart card-enabled applications, such as Microsoft Outlook and Microsoft Office, allow users to digitally sign or encrypt documents available in virtual apps and desktops sessions.
Limitations:
- Certificates must be stored on the smart card and not on the user device.
- Citrix Workspace app does not save the choice of the user certificate, but stores the PIN when configured. The PIN is cached in non-paged memory only during the user session and isn’t stored on the disk.
- Citrix Workspace app does not reconnect to a session when a smart card is inserted.
- When configured for smart card authentication, Citrix Workspace app does not support virtual private network (VPN) single-sign on or session pre-launch. To use VPN with smart card authentication, install the Citrix Gateway Plug-in. Log on through a webpage using their smart cards and PINs to authenticate at each step. Pass-through authentication to StoreFront with the Citrix Gateway Plug-in isn’t available for smart card users.
- Citrix Workspace app updater communications with citrix.com and the Merchandising Server aren’t compatible with smart card authentication on Citrix Gateway.
Warning
Some configuration requires registry edits. Using the Registry editor incorrectly might cause problems that can require you to reinstall the operating system. Citrix can’t guarantee that problems resulting from incorrect use of the Registry Editor can be solved. Make sure you back up the registry before you edit it.
To enable single sign-on for smart card authentication:
To configure Citrix Workspace app for Windows, include the following command-line option during installation:
-
ENABLE_SSON=YesSingle sign-on is another term for pass-through authentication. Enabling this setting prevents Citrix Workspace app from displaying a second prompt for a PIN.
-
In the Registry editor, navigate to the following path and set the
SSONCheckEnabledstring toFalseif you have not installed the single sign-on component.HKEY_CURRENT_USER\Software{Wow6432}\Citrix\AuthManager\protocols\integratedwindows\HKEY_LOCAL_MACHINE\Software{Wow6432}\Citrix\AuthManager\protocols\integratedwindows\The key prevents the Citrix Workspace app authentication manager from checking for the single sign-on component and allows Citrix Workspace app to authenticate to StoreFront.
To enable smart card authentication to StoreFront instead of Kerberos, install Citrix Workspace app for Windows with the following command-line options:
-
/includeSSONinstalls single sign-on (pass-through) authentication. Enables credential caching and the use of pass-through domain-based authentication. -
If the user logs on to the endpoint with a different authentication method, for example, user name and password, the command line is:
/includeSSON LOGON_CREDENTIAL_CAPTURE_ENABLE=No
This type of authentication prevents capturing of the credentials at logon time and allows Citrix Workspace app to store the PIN during Citrix Workspace app login.
- Open the Citrix Workspace app Group Policy Object administrative template by running gpedit.msc.
- Go to Administrative Templates > Citrix Components > Citrix Workspace > User Authentication > Local user name and password.
- Select Enable pass-through authentication. Depending on the configuration and security settings, select Allow pass-through authentication for all ICA® option for pass-through authentication to work.
To configure StoreFront:
- When you configure the authentication service, select the Smart card check box.
For more information about using smart cards with StoreFront, see Configure the authentication service in the StoreFront documentation.
To enable user devices for smart card use:
- Import the certificate authority root certificate into the device’s keystore.
- Install your vendor’s cryptographic middleware.
- Install and configure Citrix Workspace app.
To change how certificates are selected:
By default, if multiple certificates are valid, Citrix Workspace app prompts the user to choose a certificate from the list. Instead, you can configure Citrix Workspace app to use the default certificate (per the smart card provider) or the certificate with the latest expiry date. If there are no valid logon certificates, the user is notified, and given the option to use an alternate logon method if available.
A valid certificate must have all of these characteristics:
- The current time of the clock on the local computer is within the certificate validity period.
- The Subject public key must use the RSA algorithm and have a key length of 1024 bits, 2048 bits, or 4096 bits.
- Key usage must include digital signature.
- Subject Alternative Name must include the User Principal Name (UPN).
- Enhanced key usage must include smart card logon and client authentication, or all key usages.
- One of the Certificate Authorities on the certificate’s issuer chain must match one of the allowed Distinguished Names (DN) sent by the server in the TLS handshake.
Change how certificates are selected by using either of the following methods:
-
On the Citrix Workspace app command line, specify the option
AM_CERTIFICATESELECTIONMODE={ Prompt | SmartCardDefault | LatestExpiry }.Prompt is the default. For
SmartCardDefaultorLatestExpiry, if multiple certificates meet the criteria, Citrix Workspace app prompts the user to choose a certificate. -
Add the following key value to the registry key HKEY_CURRENT_USER OR HKEY_LOCAL_MACHINE\Software\[Wow6432Node\Citrix\AuthManager: CertificateSelectionMode={ PromptSmartCardDefault LatestExpiry }.
Values defined in HKEY_CURRENT_USER take precedence over values in HKEY_LOCAL_MACHINE to best assist the user in selecting a certificate.
To use CSP PIN prompts:
By default, the PIN prompts presented to users are provided by Citrix Workspace app for Windows rather than the smart card Cryptographic Service Provider (CSP). Citrix Workspace app prompts users to enter a PIN when required and then passes the PIN to the smart card CSP. If your site or smart card has more stringent security requirements, such as to disallow caching the PIN per-process or per-session, you can configure Citrix Workspace app to use the CSP components to manage the PIN entry, including the prompt for a PIN.
Change how PIN entry is handled by using either of the following methods:
- On the Citrix Workspace app command line, specify the option
AM_SMARTCARDPINENTRY=CSP. - Add the following key value to the registry key
HKEY_LOCAL_MACHINE\Software\[Wow6432Node\Citrix\AuthManager: SmartCardPINEntry=CSP.
Smart card support and removal changes
A Citrix Virtual Apps session logs off when you remove the smart card. If Citrix Workspace app is configured with smart card as the authentication method, configure the corresponding policy on Citrix Workspace app for Windows to enforce the Citrix Virtual Apps session for logoff. The user is still logged into the Citrix Workspace app session.
Limitation:
When you log on to the Citrix Workspace app site using smart card authentication, the user name is displayed as Logged On.
Fast smart card
Fast smart card is an improvement over the existing HDX PC/SC-based smart card redirection. It improves performance when smart cards are used in high-latency WAN environments.
Fast smart cards are supported on Windows VDA only.
To enable fast smart card logon on Citrix Workspace app:
Fast smart card logon is enabled by default on the VDA and disabled by default on Citrix Workspace app. To enable fast smart card logon, include the following parameter in the default.ica file of the associated StoreFront site:
copy[WFClient]
SmartCardCryptographicRedirection=On
<!--NeedCopy-->
To disable fast smart card logon on Citrix Workspace app:
To disable fast smart card logon on Citrix Workspace app, remove the SmartCardCryptographicRedirection parameter from the default.ica file of the associated StoreFront site.
For more information, see smart-cards.
Silent authentication for Citrix Workspace
Citrix Workspace app introduces a Group Policy Object (GPO) policy to enable silent authentication for Citrix Workspace. This policy enables Citrix Workspace app to log in to Citrix Workspace automatically at system startup. Use this policy only when domain pass-through (single sign-on or SSON) is configured for Citrix Workspace on domain-joined devices. This feature is available from Citrix Workspace app for Windows version 2012 and later.
Starting with Citrix Workspace app for Windows version 2503, the system installs SSON by default in dormant mode. You can enable SSON post-installation using the Group Policy Object (GPO) policy. To enable, navigate to User Authentication > Local user name and password and select the Enable pass-through authentication checkbox.
Note:
You must reboot the system after updating the GPO policy for the SSON setting to take effect
For this policy to function, the following criteria must be met:
- Single sign-on must be enabled.
- The
SelfServiceModekey must be set toOffin the Registry editor.
Enabling silent authentication:
- Open the Citrix Workspace app Group Policy Object administrative template by running
gpedit.msc. - Under the Computer Configuration node, go to Administrative Templates > Citrix Workspace > Self Service.
- Click the Silent authentication for Citrix Workspace policy and set it to Enabled.
- Click Apply and OK.
Prevent Citrix Workspace app for Windows from caching passwords and usernames
By default, Citrix Workspace app for Windows automatically populates the last user name entered. To clear autofill of the user name field, edit the registry on the user device:
- Create a REG_SZ value HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\AuthManager\RememberUsername.
- Set its value false.
To disable the Remember my password check box and prevent an automatic sign-in, create following registry key on client machine where Citrix Workspace app for Windows is installed:
- Path: HKEY_LOCAL_MACHINE\Software\wow6432node\Citrix\AuthManager
- Type: REG_SZ
- Name: SavePasswordMode
- Value: Never
Note:
Using Registry Editor incorrectly can cause serious problems that can require you to reinstall the operating system. Citrix cannot guarantee that problems resulting from incorrect use of Registry Editor can be solved. Use Registry Editor at your own risk. Make sure you back up the registry before you edit it.
To prevent caching credentials for the StoreFront stores, see Prevent Citrix Workspace app for Windows from caching passwords and usernames in the StoreFront documentation.
Support for more than 200 groups in Azure AD
With this release, an Azure AD user who is part of more than 200 groups can view apps and desktops assigned to the user. Previously, the same user wasn’t able to view these apps and desktops.
Note:
Users must sign out from Citrix Workspace app and sign in back to enable this feature.
Proxy authentication support
Previously, on client machines configured with proxy authentication, if the proxy credentials don’t exist in the Windows Credential Manager, you aren’t allowed to authenticate to Citrix Workspace app.
From Citrix Workspace app for Windows version 2102 and later, on client machines configured for proxy authentication, if the proxy credentials aren’t stored in the Windows Credential Manager, an authentication prompt appears, asking you to enter the proxy credentials. Citrix Workspace app then saves the proxy server credentials in Windows Credential Manager. This results in a seamless login experience because you don’t need to manually save your credentials in Windows Credential Manager before accessing Citrix Workspace app.
Force login prompt for Federated identity provider
Starting from 2212 version, Citrix Workspace app honors the Federated Identity Provider Sessions setting. For more information, see Knowledge Center article CTX253779.
You no longer need to use the Store authentication tokens policy to force the login prompt
User-Agent
Citrix Workspace app sends a user agent in network requests that can be used to configure authentication policies including redirection of authentication to other Identity Providers (IdPs).
Note:
The version numbers mentioned as part of the User-Agent in the following table are examples and it is automatically updated based on the versions that you are using.
The following table describes the scenario, description, and the corresponding User-Agent for each scenario:
| Scenario | Description | User-Agent |
|---|---|---|
| Regular HTTP requests | In general, a network request made by Citrix Workspace app contains a User-Agent. For example, network requests like: GET /Citrix/Roaming/Accounts and GET / AGServices/discover
|
CitrixReceiver/23.5.0.63 Windows/10.0 (22H2 Build 19045.2965) SelfService/23.5.0.63 (Release) X1Class CWACapable |
| Cloud store | When a user authenticates to a cloud store in Citrix Workspace app, network requests are made with a specific User-Agent. For example, network requests with path /core/connect/authorize. |
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36 Edg/113.0.1774.50 CWA/23.5.0.63 Windows/10.0 (22H2 Build 19045.2965) |
| On-premises store with Gateway Advanced Auth using Edge WebView | When a user authenticates to the Gateway configured with Advanced Auth on Citrix Workspace app using Edge WebView, network requests are made with a specific User-Agent. For example, network requests that include: GET /nf/auth/doWebview.do and GET /logon/LogonPoint/tmindex.html. |
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36 Edg/108.0.1462.54 CWAWEBVIEW/23.2.0.2111 Windows/10.0 (22H2 Build 19045.2364) |
| On-premises store with Gateway Advanced Auth using IE WebView | When a user authenticates to the Gateway configured with Advanced Auth on Citrix Workspace app using Internet Explorer WebView, network requests are made with a specific User-Agent. For example, network requests that include: GET /nf/auth/doWebview.do and GET /logon/LogonPoint/tmindex.html. |
Mozilla/5.0 (Windows NT 10.0; WOW64; Trident/7.0; rv:11.0) like Gecko, CWAWEBVIEW/23.5.0.43 |
| Custom web store | When a user adds a custom web store to Citrix Workspace app, the app sends a User-Agent. | Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36 Edg/113.0.1774.50 CWA/23.5.0.63 Windows/10.0 (22H2 Build 19045.2965) |
In this article
- Authentication tokens
- Support for Conditional Access with Azure Active Directory
- Support for modern authentication methods for StoreFront stores
- Single sign-on support for Edge WebView when using Microsoft Entra ID
- Other ways to authenticate
- Smart card
- Silent authentication for Citrix Workspace
- Prevent Citrix Workspace app for Windows from caching passwords and usernames
- Support for more than 200 groups in Azure AD
- Proxy authentication support
- Force login prompt for Federated identity provider
- User-Agent