Browser content redirection
Overview
Browser content redirection provides the ability of rendering webpages in the allow list on the client side. This feature uses Citrix Workspace™ app to instantiate a corresponding rendering engine on the client side, which fetches the HTTP and HTTPS content from the URL.
Note:
The Linux VDA supports browser content redirection in Google Chrome.
This overlay web layout engine runs on the client instead of on the VDA and uses the client CPU, GPU, RAM, and network.
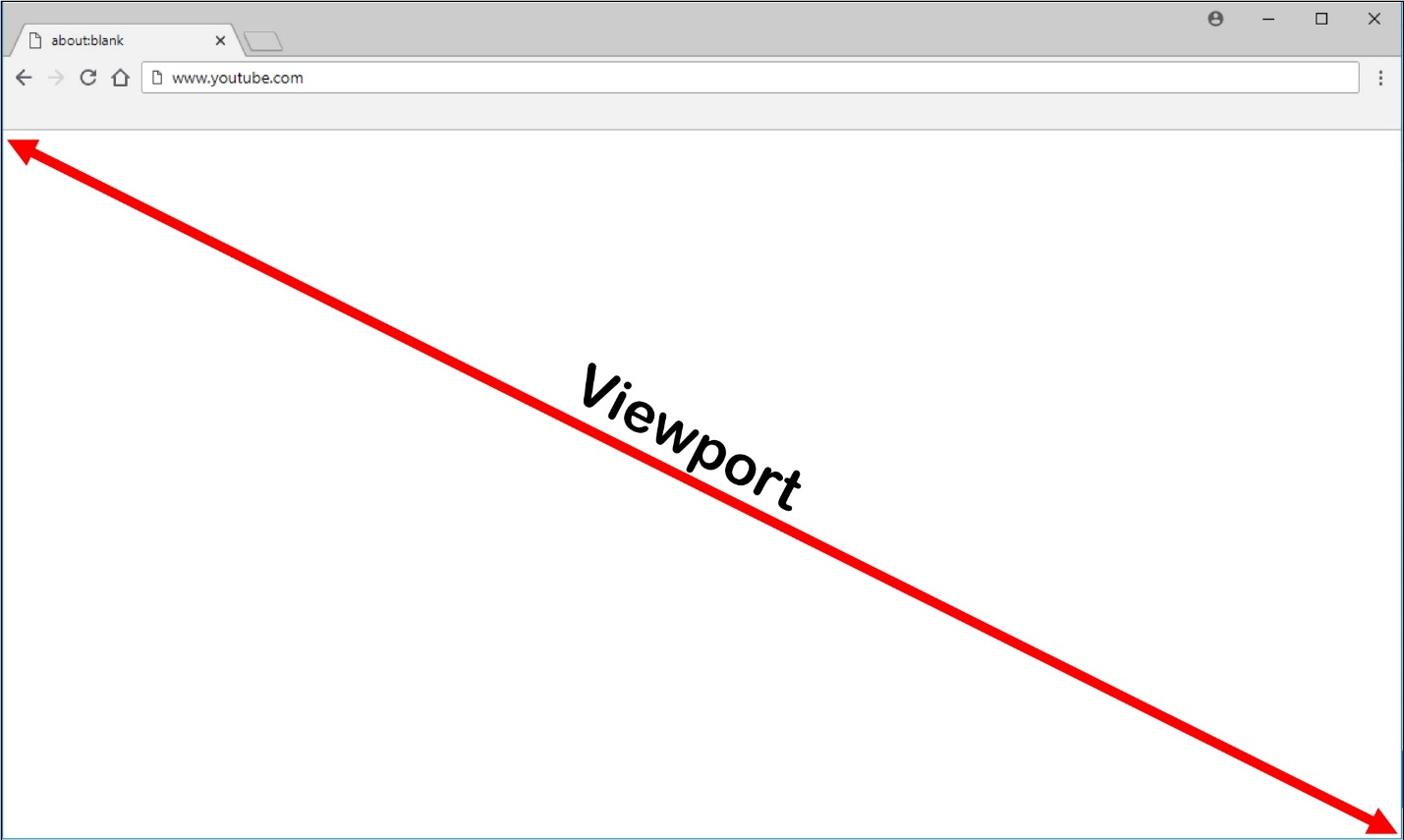
Only the browser viewport is redirected. The viewport is the rectangular area in your browser where content displays. The viewport does not include items such as the address bar, favorites bar, and status bar. Those items are still running in the browser on the VDA.
Configure a Studio policy that specifies an Access Control List containing the URLs in the allow list for redirection. Configure a block list that disables redirection for specific URLs.
If a match to a URL is found in an allow list but not in any block list, a virtual channel (CTXCSB) instructs the Citrix Workspace app that a redirection is required and relays the URL. Citrix Workspace app then instantiates a local rendering engine and displays the website.
Citrix Workspace app then blends back the website into the virtual desktop browser content area seamlessly.
-
Icon of the Citrix® browser content redirection extension
The color of the extension icon specifies the status of the Chrome extension. It is one of the three colors:
- Green: Active and connected
- Gray: Not active/idle on the current tab
- Red: Broken/Not working
- Viewport rendered on the client or blended back to the virtual desktop
- Linux VDA
- Windows client
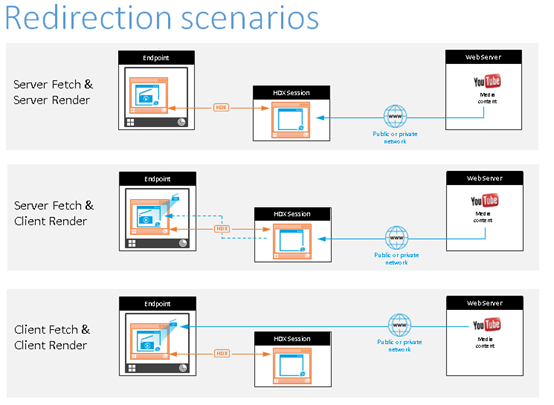
Here are scenarios of how the Citrix Workspace app fetches content:
-
Server fetch and server render: There is no redirection because you did not add the site to the allow list or the redirection failed. We fall back to rendering the webpage on the VDA and use Thinwire to remote the graphics. Use policies to control the fallback behavior. This scenario causes high CPU, RAM, and bandwidth consumption on the VDA.
-
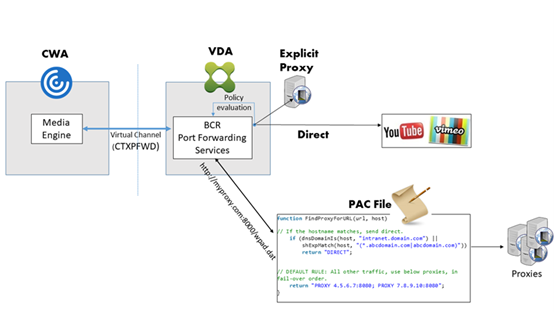
Server fetch and client render: Citrix Workspace app contacts and fetches content from the web server through the VDA using a virtual channel (CTXPFWD). This option is useful when the client doesn’t have access to the web server (for example, thin clients). It lowers CPU and RAM consumption on the VDA, but bandwidth is consumed on the ICA® virtual channel.
There are three modes of operation for this scenario. CTXPFWD forwards data to a proxy device that the VDA accesses to gain access to the web server.
Which policy option to choose:
- Explicit Proxy - If you have a single explicit proxy in your data center.
- Direct or Transparent - If you do not have proxies, or if you use transparent proxies.
- PAC files - If you rely on PAC files so browsers in the VDA can automatically choose the appropriate proxy server for fetching a specified URL.
For more information, see the Browser Content Redirection Proxy Configuration setting later in this article.
-
Client fetch and client render: Because the Citrix Workspace app contacts the web server directly, it requires Internet access. This scenario offloads all the network, CPU, and RAM usage from your Citrix Virtual Apps and Desktops™ site.
Benefits:
- Better end user experience (Adaptive Bit Rate (ABR))
- Reduced VDA resource usage (CPU/RAM/IO)
- Reduced bandwidth consumption
System requirements
Windows client:
- Citrix Workspace app 1809 for Windows or later
Linux VDA:
- Browser on the VDA: Google Chrome v66 or later with the Citrix browser content redirection extension added
Configure browser content redirection
To use browser content redirection, configure relevant policies and install the browser content redirection extension in Google Chrome. To do so, complete the following steps:
-
In Citrix Studio, set Browser Content Redirection to Allowed to enable browser content redirection.
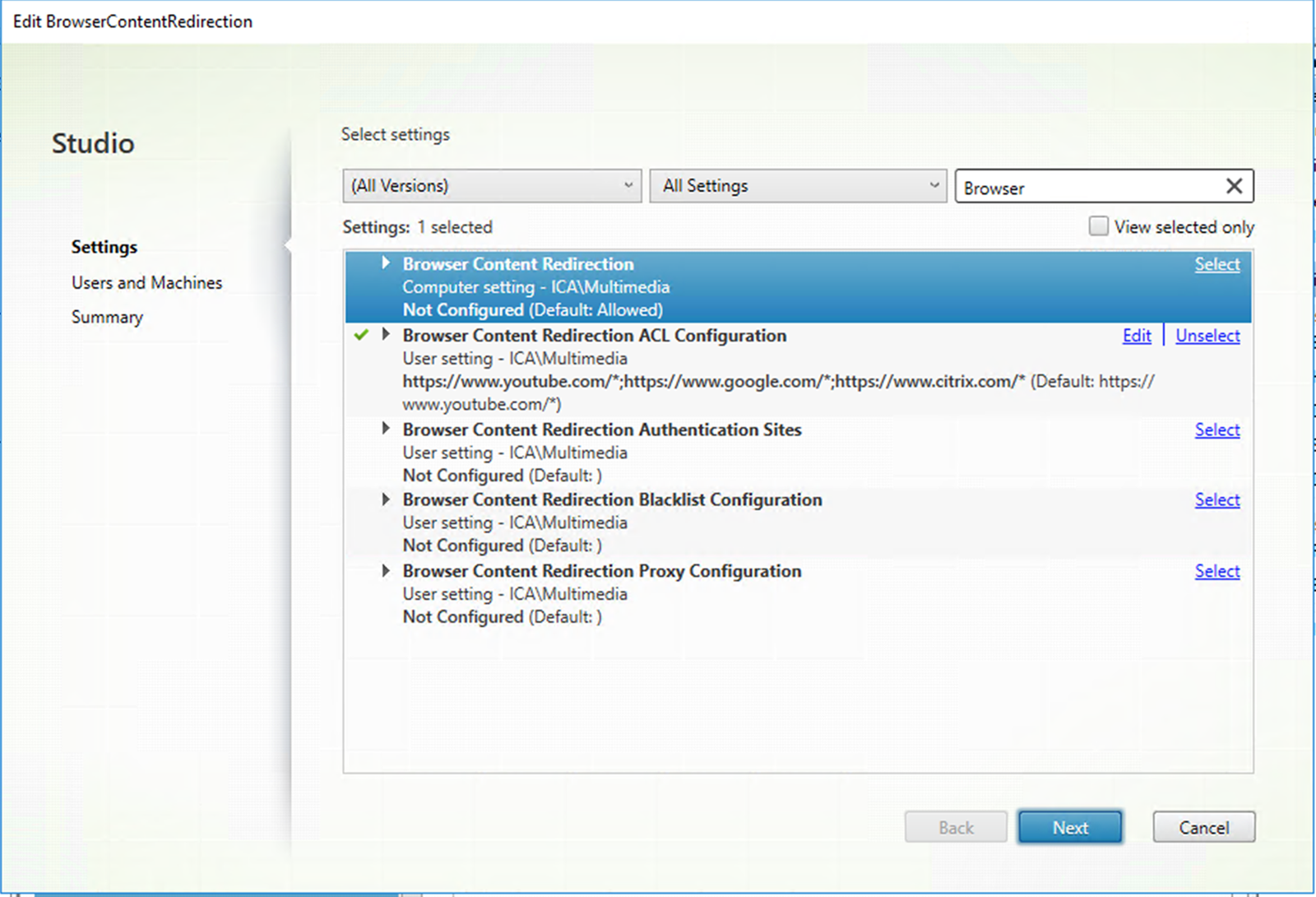
-
Specify an allow list of URLs whose content can be redirected to the client and a block list that disables redirection for specific URLs. Configuring a block list is optional.
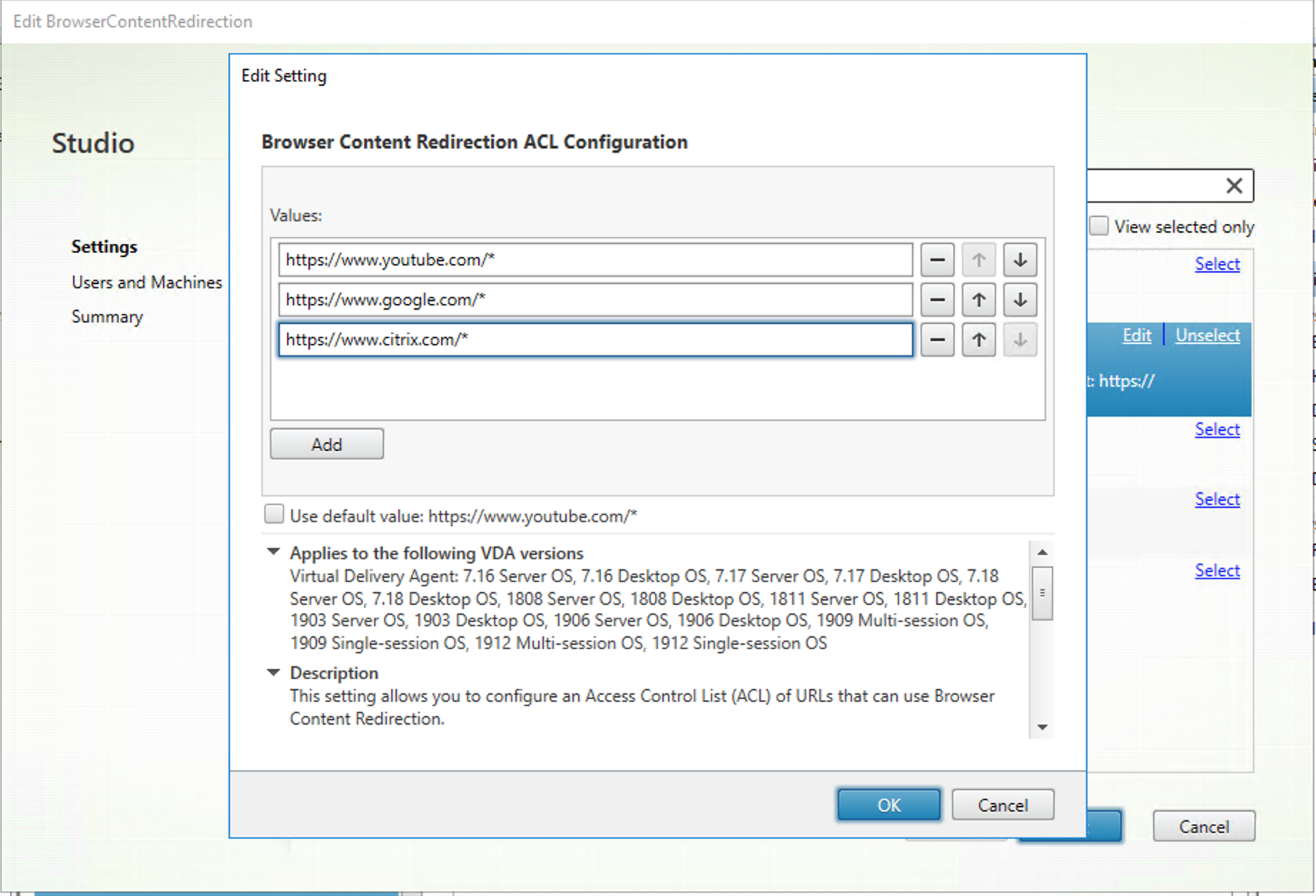
The Browser Content Redirection ACL Configuration setting specifies an allow list of URLs whose content can be redirected to the client. When specifying URLs, you can use the
*wildcard to represent all URL components except the protocol.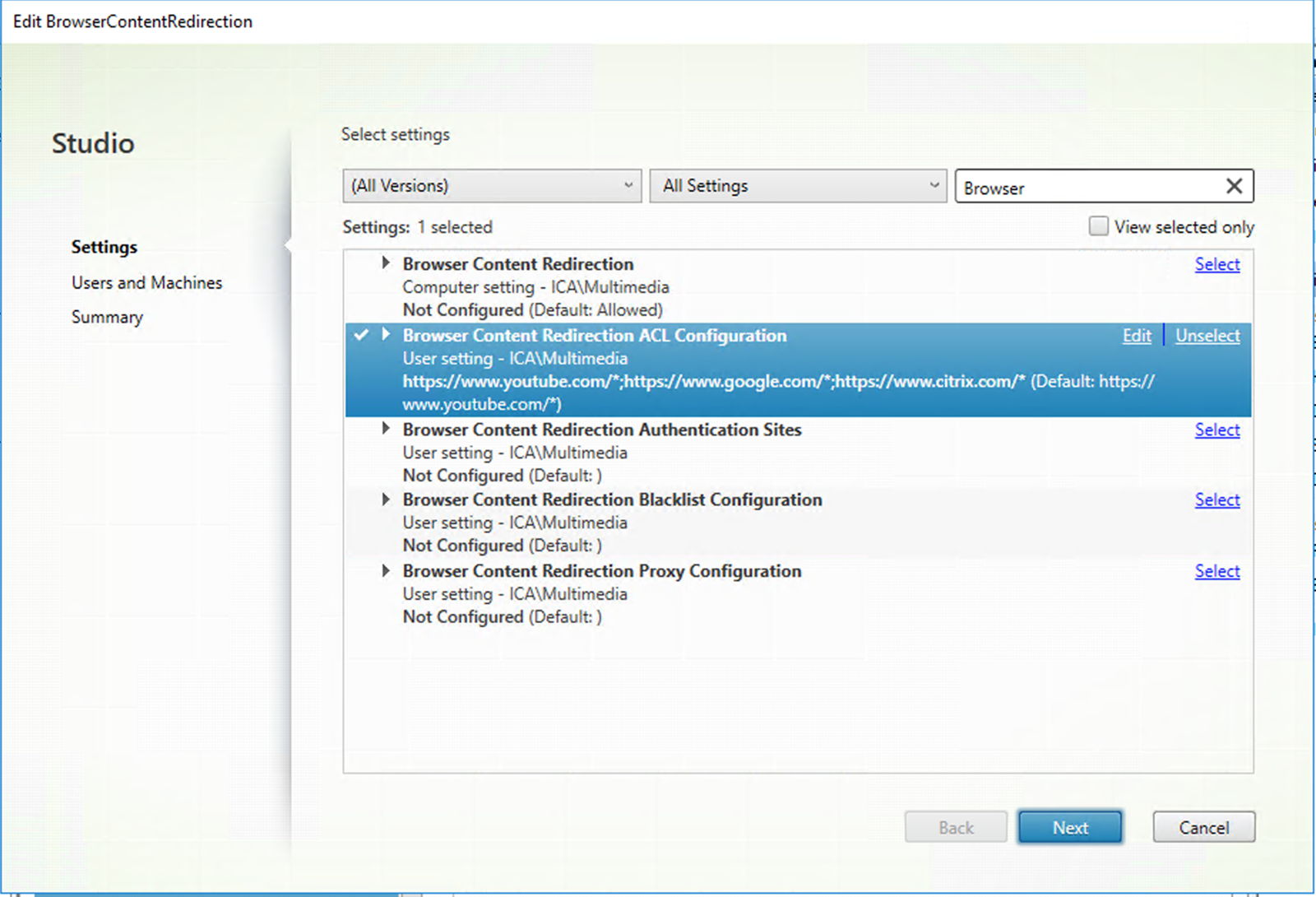
The following are allowed examples:
-
http://www.xyz.com/index.html(You can achieve better granularity by specifying paths in the URL. For example, if you specifyhttps://www.xyz.com/sports/index.html, only theindex.htmlpage is redirected.) https://www.xyz.com/*http://www.xyz.com/*videos*http://*.xyz.com/http://*.*.com/
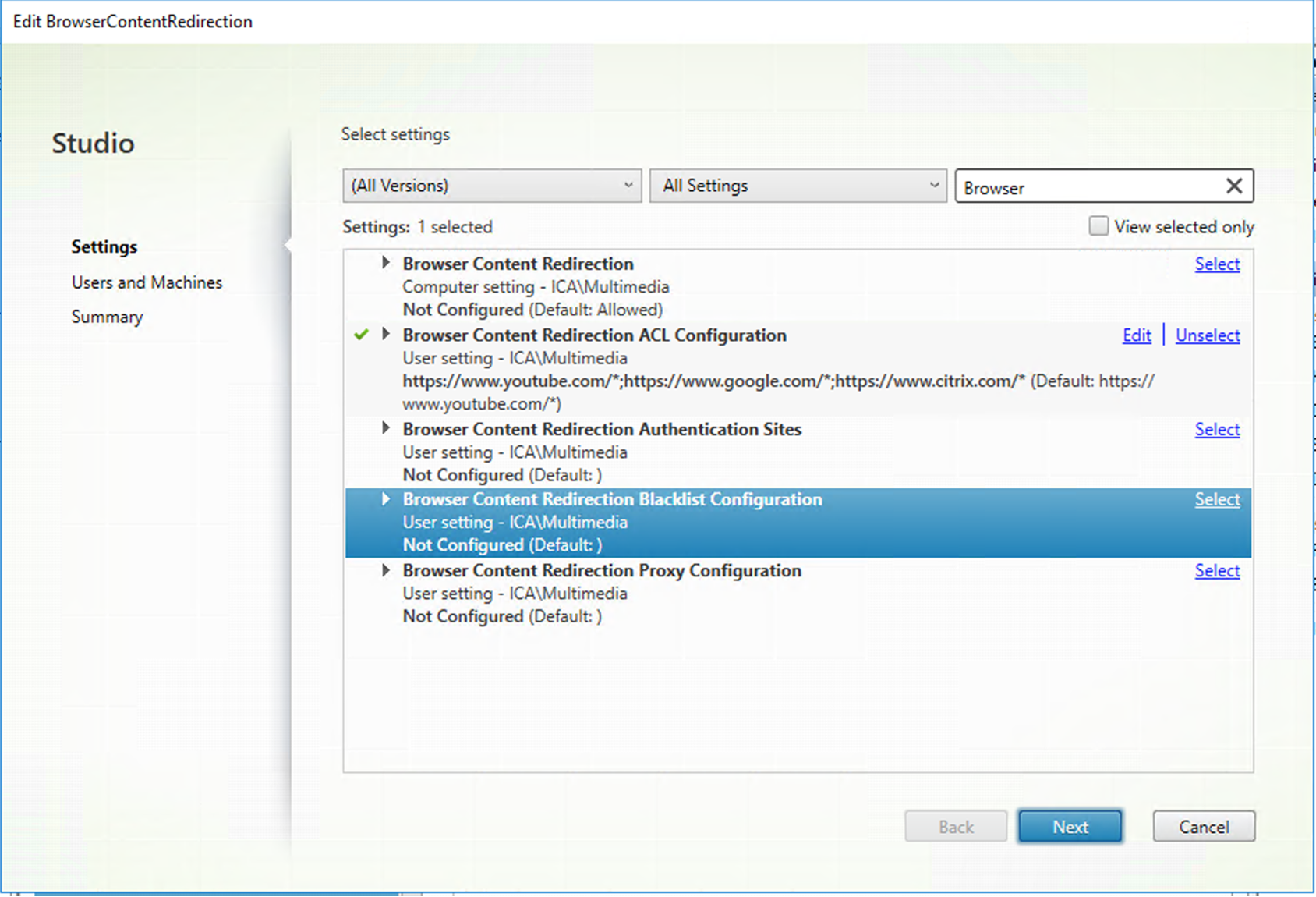
The Browser Content Redirection Blacklist Configuration setting specifies a block list that disables redirection for specific URLs.
-
-
To enable server fetch and client render, configure the Browser Content Redirection Proxy Configuration setting.
This setting provides configuration options for proxy settings on the VDA for browser content redirection. If enabled with a valid proxy address and port number, PAC/WPAD URL, or Direct/Transparent setting, Citrix Workspace app always attempts server fetch and client render first. For more information, see the Fallback mechanism.
If disabled or not configured and using a default value, Citrix Workspace app attempts client fetch and client render.
By default, this setting is Prohibited.
Allowed pattern for an explicit proxy:
http://\<hostname/ip address\>:\<port\>Example:
http://proxy.example.citrix.com:80 http://10.10.10.10:8080Allowed patterns for PAC/WPAD files:
http://<hostname/ip address>:<port>/<path>/<Proxy.pac>Example:
http://wpad.myproxy.com:30/configuration/pac/Proxy.pachttps://<hostname/ip address>:<port>/<path>/<wpad.dat>Example:
http://10.10.10.10/configuration/pac/wpad.datAllowed patterns for direct or transparent proxies:
Type the word DIRECT in the policy text box.
Note:
You can also set a proxy by editing the registry value
HKLM\Software\Citrix\HdxMediastream\WebBrowserRedirectionProxyAddress.Besides, theHKLM\Software\Citrix\HdxMediastream\AllowNonTlsPacUriregistry value lets you decide whether to allow PAC file downloads through HTTP. The default value is 0, which means HTTP is not allowed.Registries override options for policy settings. For a list of the relevant registry keys, see Browser content redirection registry key overrides.
-
Click Add to Chrome on the VDA to add the Citrix browser content redirection extension from the Chrome Web Store. Doing so helps the browser on the VDA to detect whether a URL (being navigated to) matches an allow list or a block list.
Important:
The extension is not required on the client. Add it only on the VDA.
Chrome extensions are installed on a per-user basis. Updating a golden image to add or remove an extension is not required.
Fallback mechanism
If you enable the Browser Content Redirection Proxy Configuration policy, Citrix Workspace app attempts server fetch and client render. If server fetch and client render fails, it falls back to client fetch and client render. If the client machine doesn’t have access to the web server, the browser on the VDA can then reload and render the page on the server (server fetch and server render).
Browser content redirection registry key overrides
Warning:
Editing the registry incorrectly can cause serious problems that might require you to reinstall your operating system. Citrix can’t guarantee that problems resulting from the incorrect use of the Registry Editor can be solved. Use the Registry Editor at your own risk. Be sure to back up the registry before you edit it.
HKLM\Software\Citrix\HdxMediastream
| Name | Type | Value |
|---|---|---|
| WebBrowserRedirection | DWORD | 1=Allowed, 0=Prohibited |
| WebBrowserRedirectionAcl | REG_MULTI_SZ | / |
| WebBrowserRedirectionProxyAddress | REG_SZ | If you set it to any of the following modes, server fetch client render is enabled: Explicit Proxy - If you have a single explicit proxy in your data center. Direct or Transparent - If you do not have proxies, or if you use transparent proxies. PAC files - If you rely on PAC files so browsers in the VDA can automatically choose the appropriate proxy server for fetching a specified URL. |
| WebBrowserRedirectionBlacklist | REG_MULTI_SZ | / |
| AllowNonTlsPacUri | DWORD | Determines whether to allow PAC file downloads through HTTP. The default value is 0, which means HTTP is not allowed. If you set it to 1, HDXWebProxy.exe can download PAC files over HTTP (not strictly over HTTPS). |