Configure event response policies
Event response policies let you configure event-triggered actions so that you can:
- Send an email alert when a session start event is detected.
- Take action (any combination of the following actions) when events are detected in recorded sessions:
- Send email alerts
- Start screen recording immediately (with or without lossy screen recording enabled)
- Lock session
- Log off session
- Disconnect session
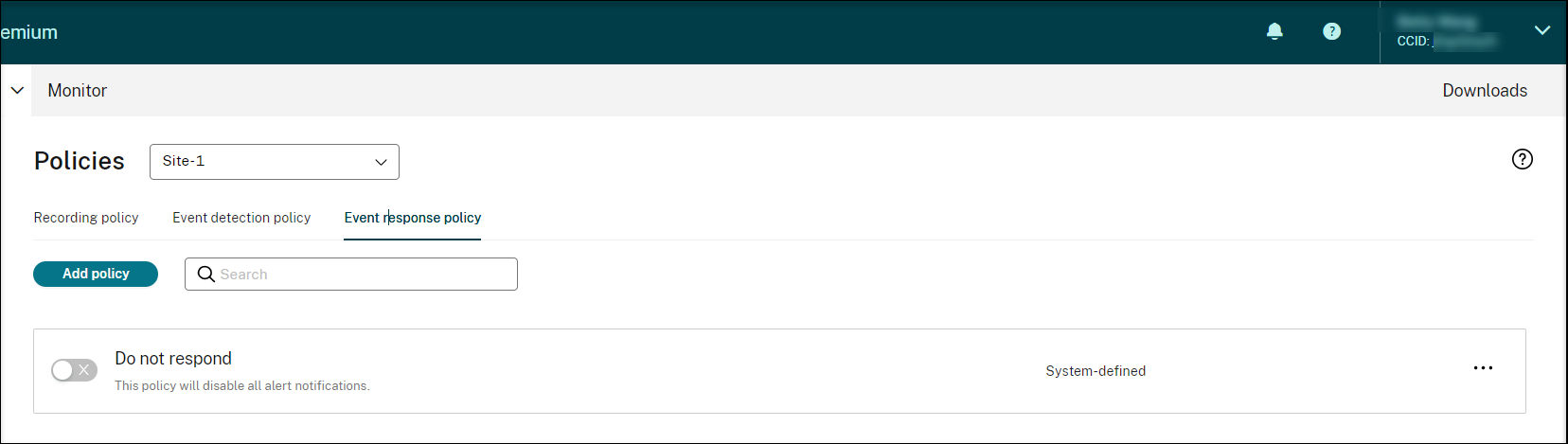
The only system-defined event response policy is Do not respond. You can create custom event response policies as needed. Only one event response policy can be active at a time. By default, there’s no active event response policy.
Note:
After you create or activate an event response policy, the policy applies to all Session Recording servers of the selected site. You can create and activate separate event response policies for different sites.
System-defined event response policy
Session Recording provides one system-defined event response policy:
- Do not respond. By default, no action is taken in response to logged events in your recordings.
Create a custom event response policy
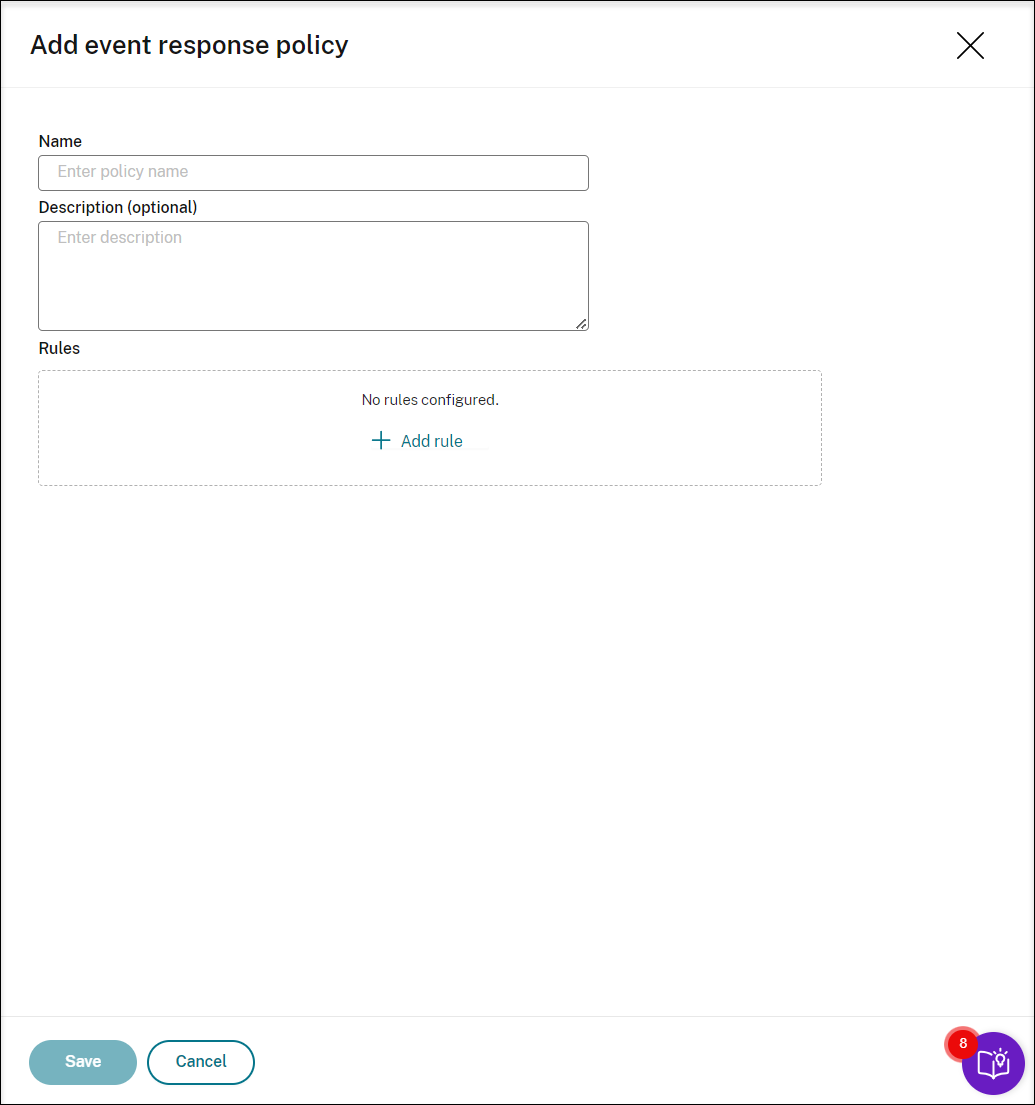
- Click Add policy.
-
On the Add event response policy page, enter a name and description for your new policy.
-
Click Add Rule.
-
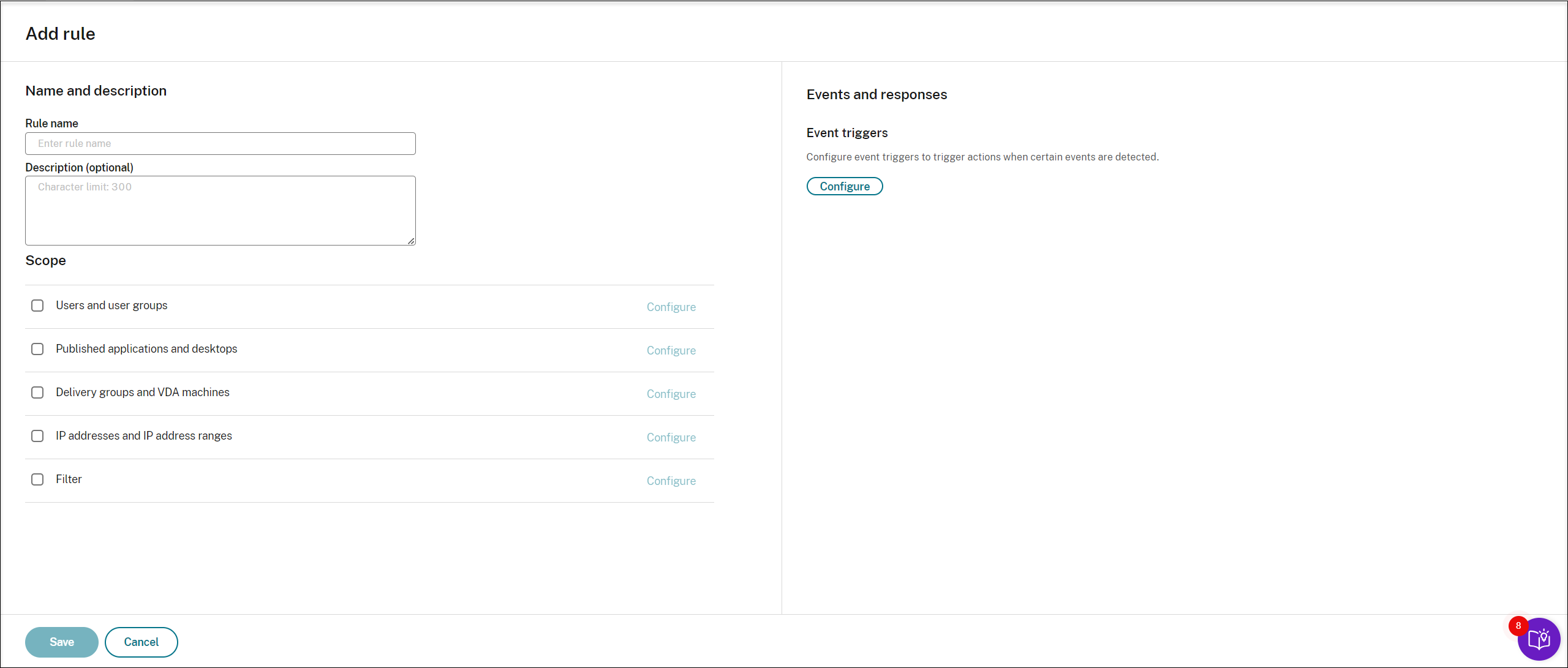
Enter the rule name and description.
-
In the Event triggers section, click Configure to configure event-triggered actions so that you can:
- Send an email alert when a session start event is detected.
- Take action (any combination of the following actions) when events are detected in recorded sessions
- Send email alert
- Start screen recording immediately (with or without lossy screen recording enabled)
- Lock session
- Log off session
- Disconnect session
Click Add event triggers to create event triggers from scratch. Or, click Browse templates to select existing event trigger templates to use directly or customize.
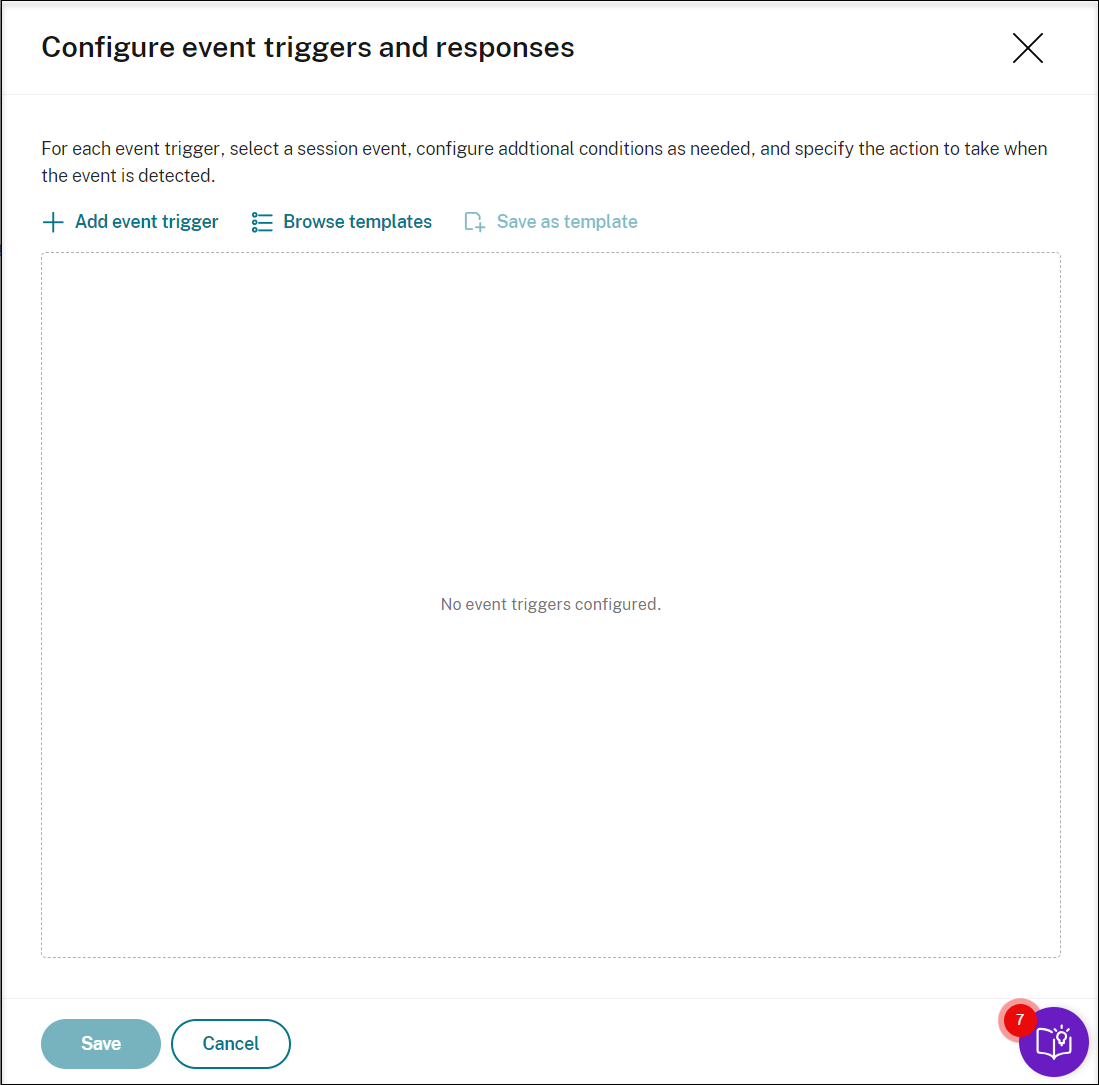
Each time you click Add event triggers, a new event trigger is created in the pane below. You can also click the Duplicate button to make duplicates of an existing event trigger.
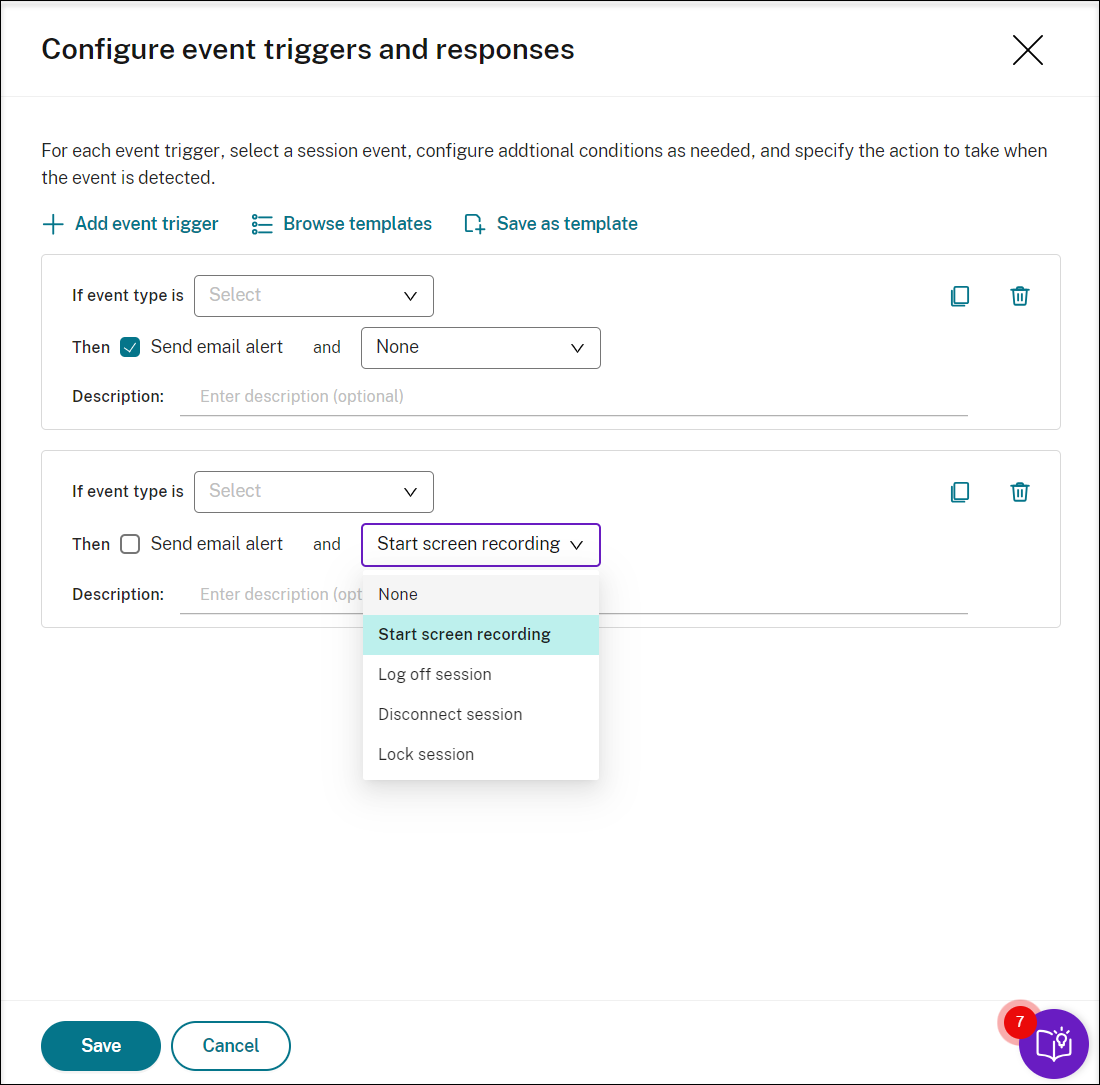
When you finish creating at least one event trigger, click Save as template to save your event triggers as a template. You can then find the new template on the My organization tab of the Event trigger templates page.
To access the Event trigger templates page, click Browse Template or click Resource Library from the left navigation pane of the Session Recording service page.
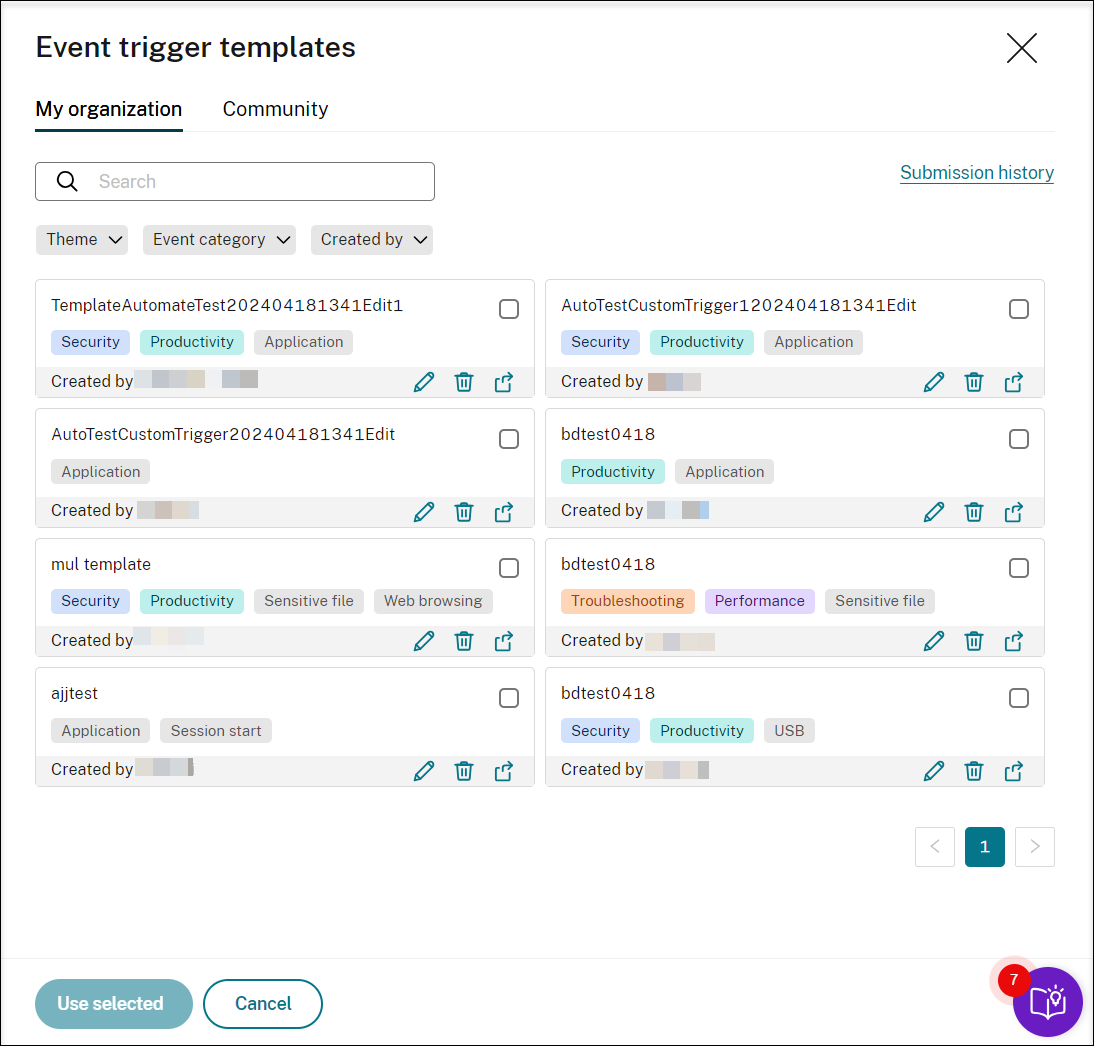
The Event trigger templates page accommodates all event trigger templates, both from your organization and from the other community members including Cloud Software Group itself.
On the My organization tab of the Event trigger templates page, you can publish your templates to the community for the other customers to access for free.
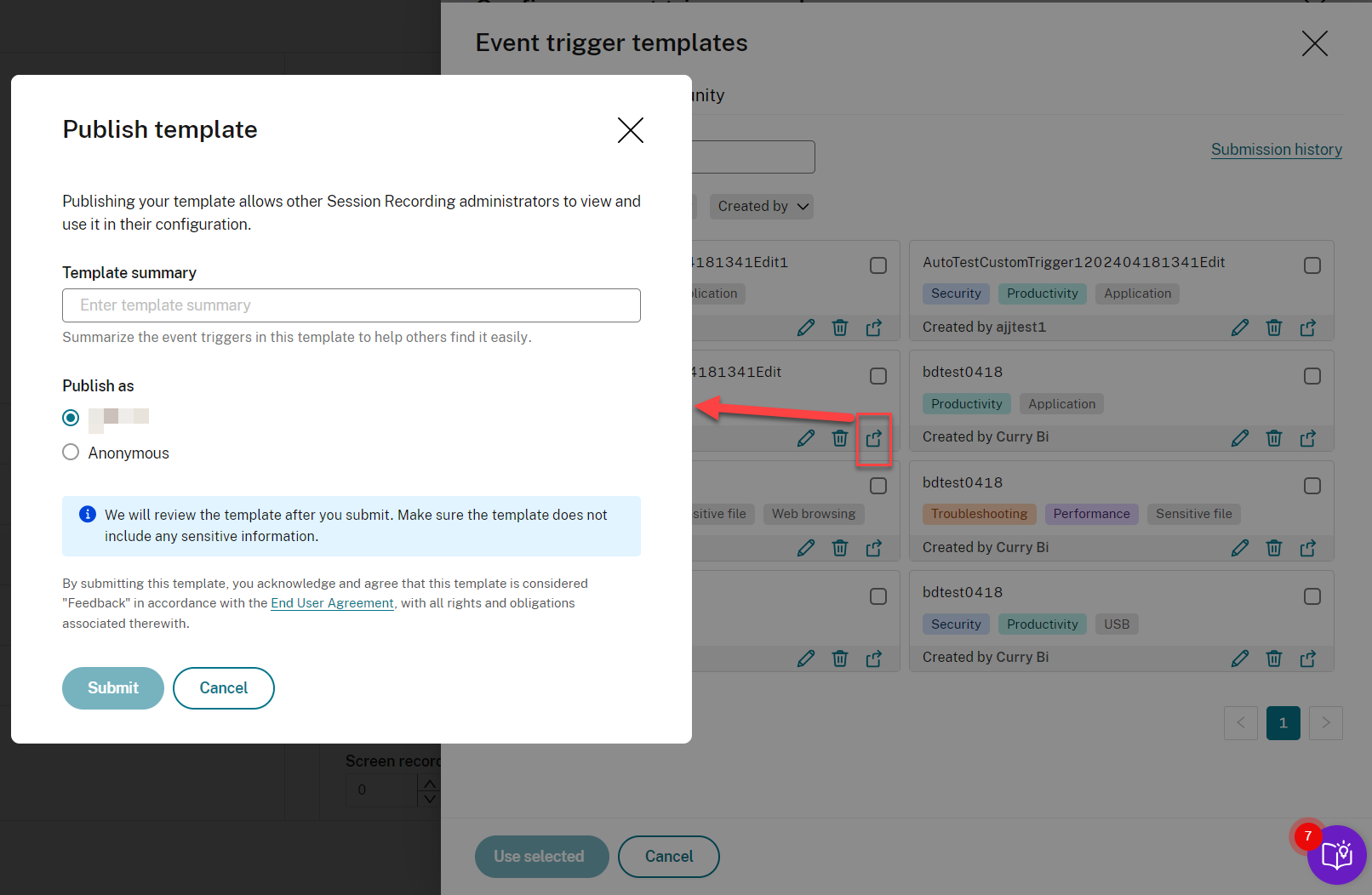
Note:
See the End User Agreement before submitting a template.
On the My organization or Community tab of the Event trigger templates page, you can search for target event trigger templates by keyword, theme, event category, and contributor. You can also bookmark or give likes to the templates of your interest.
You can select multiple event trigger templates at a time. The templates you select appear on the Add event triggers page where you can customize as needed.
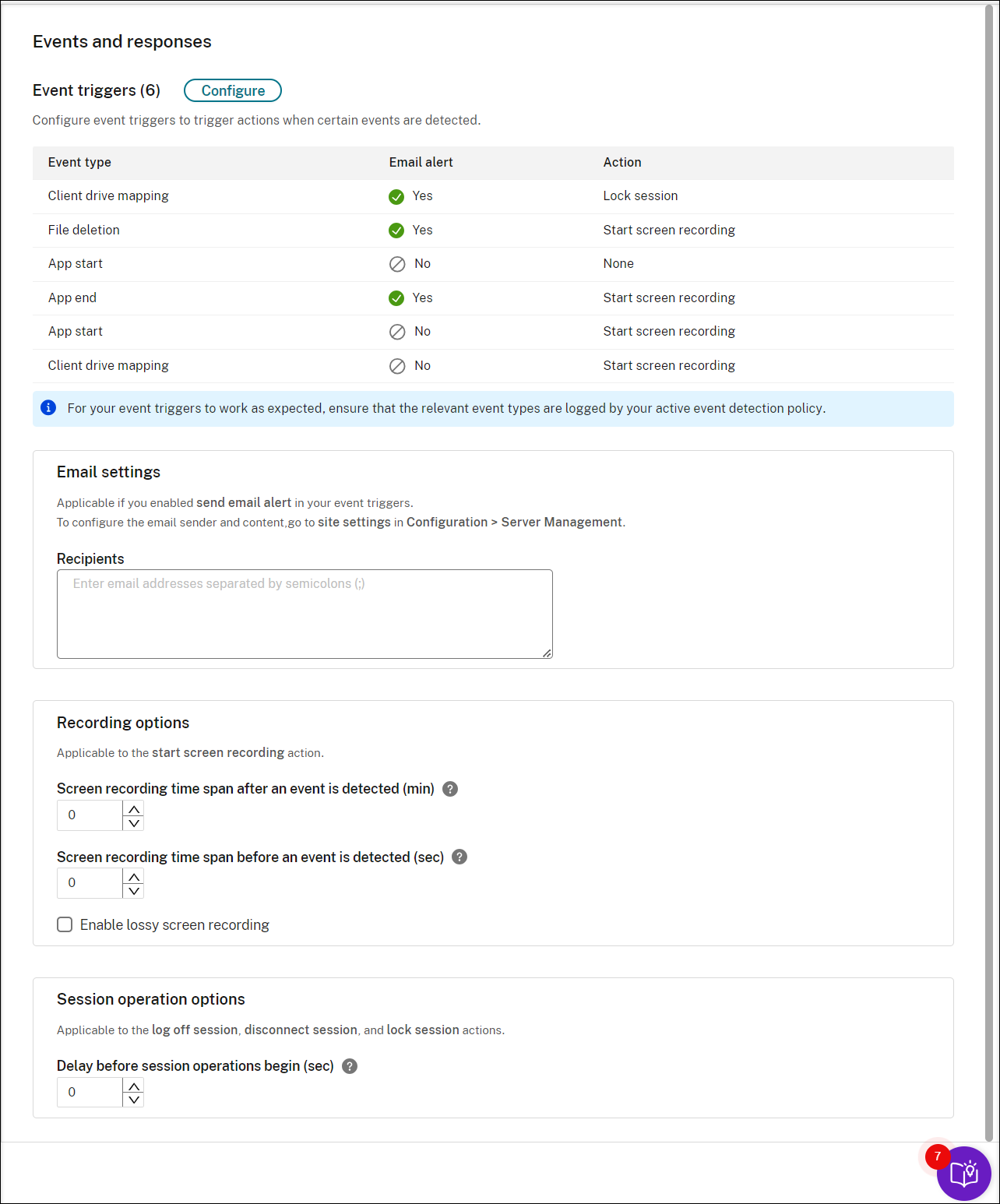
Click Save to save your settings. You are taken back to the Events and responses page where the event triggers you specify are listed. Click Configure to further adjust your event triggers. If you select the Send email alert or Start screen recording action for any of your event triggers, follow the GUI to configure email settings and recording options.
Note:
You must select the event types that the active event detection policy logs.
You can define your event triggers on the Description row or leave the row empty. Your defined description of an event trigger is provided in the alert emails if you have Send email selected and events of the type are logged. If you have Start screen recording selected, set the relevant parameters as illustrated later in this article. After that, dynamic screen recording automatically starts when certain events occur during an event-only recording.
For a complete list of supported event types, see the following table.
Event type Dimension Option App Start App name Includes, Equals, Matches Full command line Includes, Equals, Matches App End App name Includes, Equals, Matches Top Most App name Includes, Equals, Matches Windows title Includes, Equals, Matches Web Browsing URL Includes, Equals, Matches Tab title Includes, Equals, Matches Browser name Includes, Equals, Matches File Create Path Includes, Equals, Matches File size (MB) Greater than, Between, Smaller than File Rename Path Includes, Equals, Matches Name Includes, Equals, Matches File Move Source path Includes, Equals, Matches Destination path Includes, Equals, Matches File size (MB) Greater than, Between, Smaller than File Delete Path Includes, Equals, Matches File size (MB) Greater than, Between, Smaller than CDM USB Drive letter Equals Generic USB Device name Includes, Equals, Matches Idle idle duration (Hrs) Greater than File Transfer File source Equals (“host” or “client”) File size (MB) Greater than File name Includes, Equals, Matches Registry Create Key name Includes, Equals, Matches Registry Delete Key name Includes, Equals, Matches Registry Set Value Key name Includes, Equals, Matches Value name Includes, Equals, Matches Registry Delete Value Key name Includes, Equals, Matches Value name Includes, Equals, Matches Registry Rename Key name Includes, Equals, Matches User Account Modification User name Includes, Equals, Matches Unexpected App Exit App name Includes, Equals, Matches App Not Responding App name Includes, Equals, Matches New App Installed App name Includes, Equals, Matches App Uninstalled App name Includes, Equals, Matches RDP Connection IP address Includes, Equals, Matches Popup Window Process name Includes, Matches Window content Includes, Equals, Matches Performance Data CPU usage (%) Greater than Memory usage (%) Greater than Net send (MB) Greater than Net receive (MB) Greater than RTT (ms) Greater than Clipboard Operation Data type Equals (Text, File, Bitmap) Process name Includes, Equals, Matches Content Includes, Equals, Matches -
(Optional) Email settings are available after you choose Send email alert in your event triggers. For an example email alert, see the following screen capture:
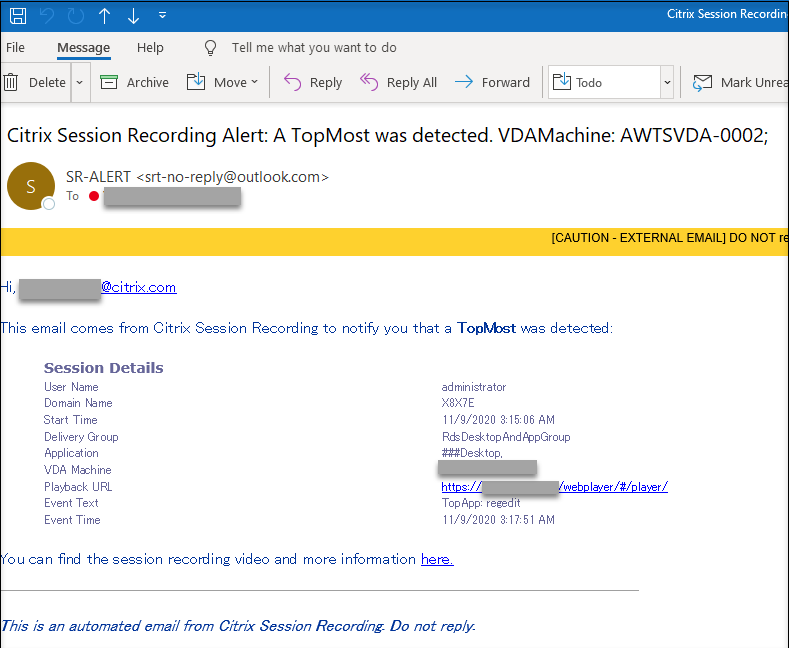
Tip:
Clicking the playback URL opens the playback page of the recorded session in the on-premises web player. Clicking here opens the All recordings page in the on-premises web player.
To send email alerts in response to detected events, complete the following settings:
-
In the Recipients section of the Events and responses page, enter email addresses for the target recipients.
-
On the Email alerts page of your Site settings, specify the email sender and content.
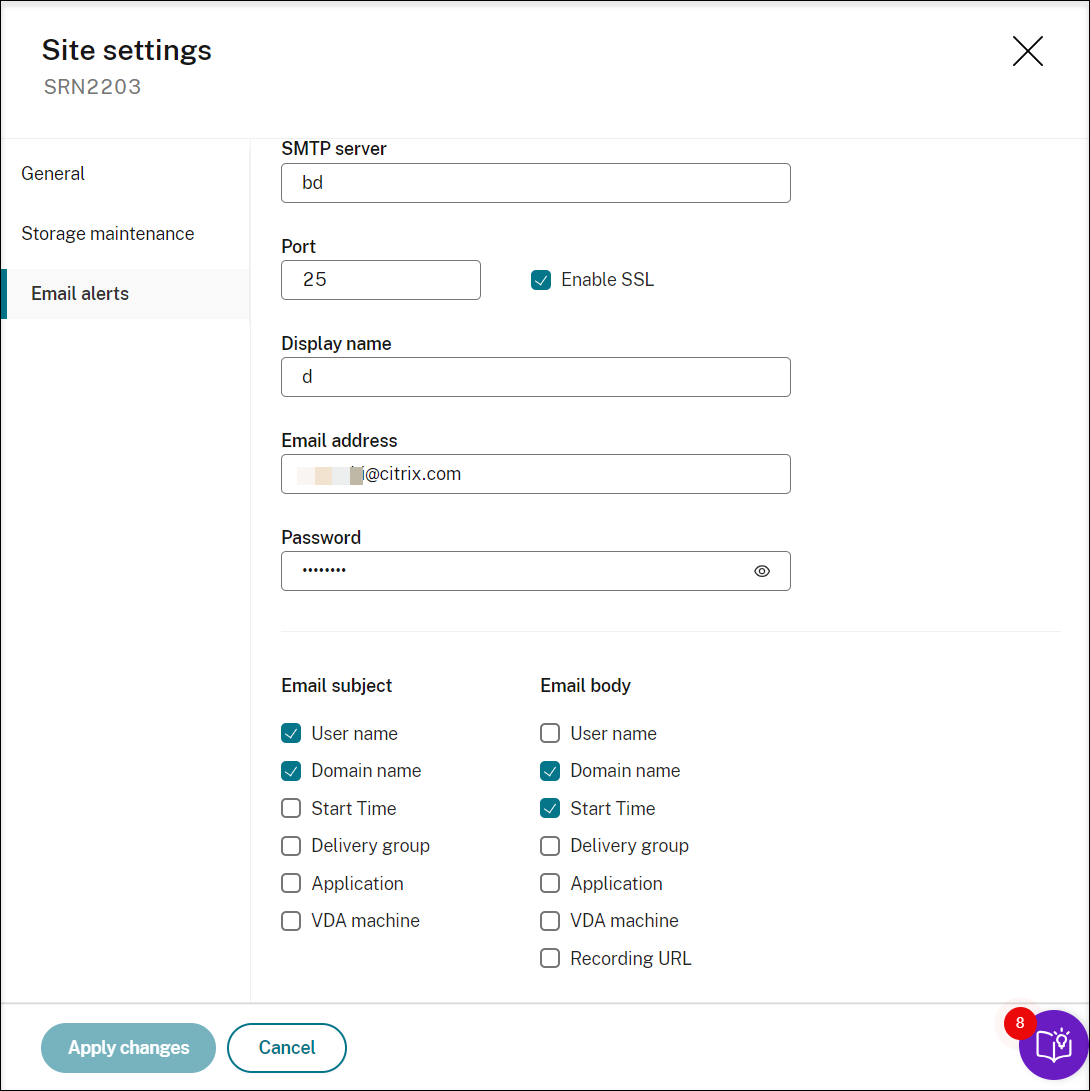
-
Edit registry for accessing the on-premises web player.
To make the playback URLs in your alert emails work as expected, browse to the registry key at
HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\SmartAuditor\Serverand do the following:-
Set the value data of LinkHost to the URL of the domain that you use to access the on-premises web player. For example, to access an on-premises web player at
https://example.com/webplayer/#/player/, set the value data of LinkHost tohttps://example.com. -
Add a value called EmailThreshold, and set its value data to a number in the range of 1 through 100. The value data determines the maximum number of alert emails that an email sending account sends within a second. This setting helps slow down the number of emails that are being sent and thus reduces the CPU usage. If you leave the value data unspecified or set it to a number out of range, the value data falls back to 25.
Note:
-
Your email server might treat an email sending account as a spam bot and thus prevent it from sending emails. Before an account is allowed to send emails, an email client such as Outlook might request you to verify that the account is used by a human user.
-
There’s a limit for sending emails within a given period. For example, when the daily limit is reached, you can’t send emails until the start of the next day. In this case, ensure that the limit is more than the number of sessions being recorded within the period.
-
-
-
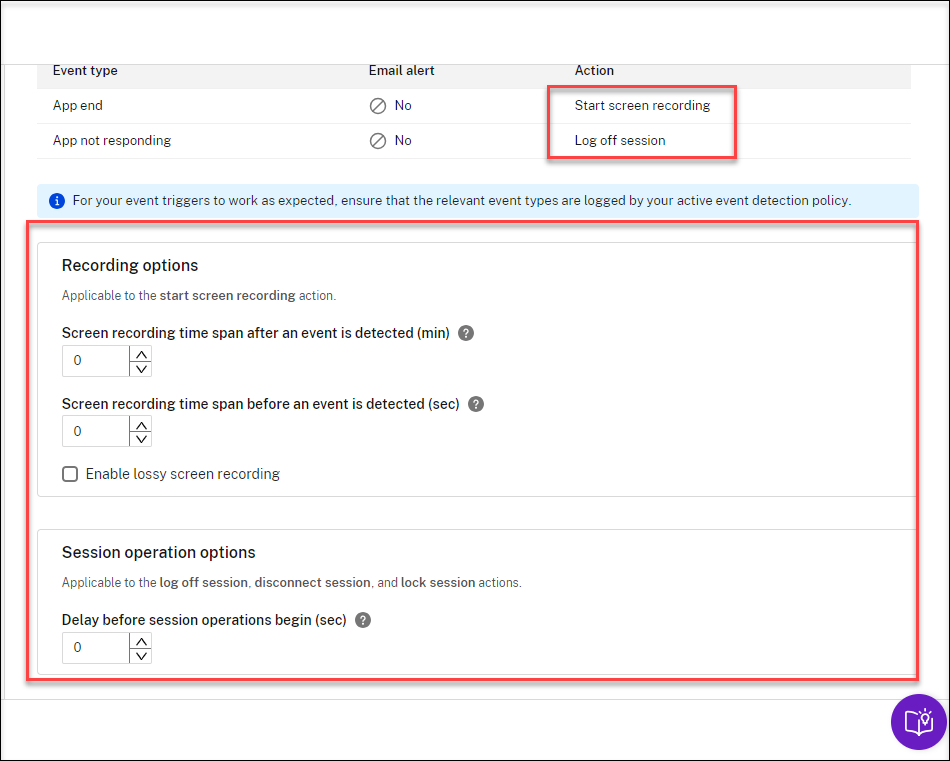
(Optional) To start screen recording immediately when certain events occur during an event-only recording, set the following options for dynamic screen recording in the Recording options section:
- Screen recording time span after an event is detected (min): You can configure the time duration (minutes) that you want to record the screen after events are detected. If you leave the value unspecified, screen recording continues until the recorded sessions end.
- Screen recording time span before an event is detected (sec): You can configure the time duration (seconds) of the screen recording you want to keep before events are detected. The value ranges from 1 to 120. Setting the value to any of 1 through 10 makes the value 10 effective. If you leave the value unspecified, the feature does not take effect. The actual length of the screen recording that Session Recording keeps might be a little longer than your configuration.
- Enable lossy screen recording: You can specify whether to enable lossy screen recording when a session event is detected. Lossy screen recording lets you adjust compression options to reduce the size of recording files and to accelerate navigating recorded sessions during playback. This feature is available with Session Recording 2308 and later. For more information, see Enable or disable lossy screen recording.
-
(Optional) Specify delay before session operations begin (sec). If you specify any of the following actions in response to logged events in recorded sessions, you can notify users of the actions in advance:
- Lock session
- Log off session
- Disconnect session
For example:
Note:
If you set the value to 0, it means that users aren’t notified when you lock, log off, or disconnect them from their virtual sessions. To notify users, set an appropriate value.
For an example notice, see the following screen capture:
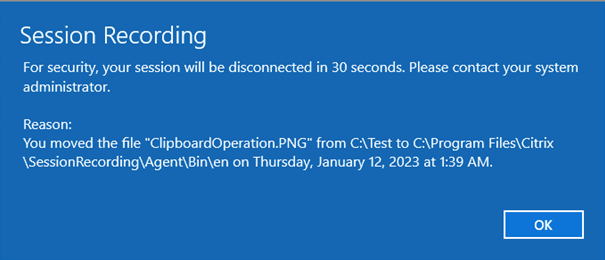
-
Select and edit the rule scope.
In a way similar to when you create a custom recording policy, you can choose at least one of the following items to create the rule scope:
- Users and user groups. Creates a list of users and groups to which the responses of the rule apply. Both Azure Active Directory (Azure AD) and Active Directory identity types are supported. Selecting Azure AD as the identity provider allows you to choose an instance from the drop-down list. The available instances depend on your settings on the Citrix Cloud™ Identity and Access Management > Authentication tab. For more information, see the instructions in the Create a custom recording policy section.
- Published applications and desktops. Creates a list of published applications and desktops to which the responses of the rule apply.
- Delivery groups and VDA machines. Creates a list of delivery groups and VDA machines to which the responses of the rule apply.
- IP addresses and IP address ranges. Creates a list of IP addresses and ranges of IP addresses to which the responses of the rule apply. The IP addresses mentioned here are the IP addresses of the Citrix Workspace™ apps.
-
Filter. Creates a list of smart access tags to which the rule applies. You can configure contextual access (smart access) using smart access policies on Citrix NetScaler, Citrix Device Posture service, and Adaptive access based on the user’s network location.
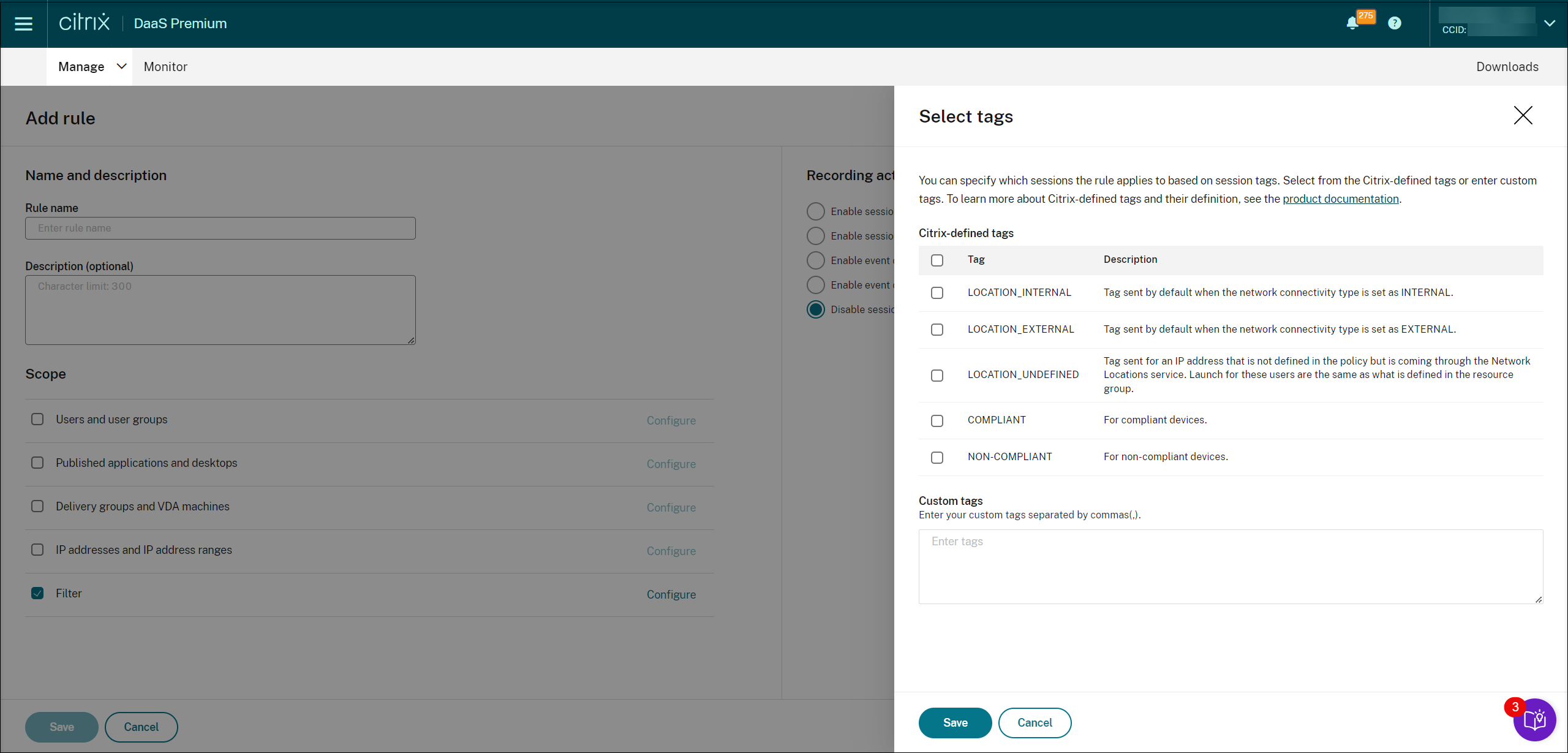
Contextual access (smart access) is available with Session Recording 2402 and later. It lets you apply policies based on the user access context including:
- The user’s location
- IP address range
- Delivery group
- Device type
- Installed applications
Note:
When a session or an event meets more than one rule in a single event response policy, the oldest rule takes effect.
- Follow the wizard to complete the configuration.
- Activate the new event response policy.
