This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Azure Active Directory as IdP
Configuring Azure Active Directory (AAD) as your identity provider (IdP) lets users enroll in XenMobile® using their Azure credentials.
iOS, Android, and Windows 10 and Windows 11 devices are supported. iOS and Android devices enroll through Secure Hub. This authentication method is available only to users enrolling in MDM through Citrix Secure Hub. Devices enrolling in MAM can’t authenticate using AAD credentials. To use Secure Hub with MDM+MAM, configure XenMobile to use Citrix Gateway for MAM enrollment. For more information, see Citrix Gateway and XenMobile.
You configure Azure as your IdP under Settings > Authentication > IDP. The IDP page is new to this version of XenMobile. In previous versions of XenMobile, you configured Azure under Settings > Microsoft Azure.
Requirements
-
Versions and licenses
- To enroll iOS or Android devices, you need Secure Hub 10.5.5.
- To enroll Windows 10 and Windows 11 devices, you need Microsoft Azure Premium licenses.
-
Directory services and authentication
- XenMobile Server must be configured for certificate-based authentication.
- If you are using Citrix ADC for authentication, Citrix ADC must be configured for certificate-based authentication.
- Secure Hub authentication uses Azure AD and honors the authentication mode defined on Azure AD.
- XenMobile Server must connect to Windows Active Directory (AD) using LDAP. Configure your local LDAP server to sync with Azure AD.
Authentication flow
When the device enrolls through Secure Hub and XenMobile is configured to use Azure as its IdP:
-
Users enter their Azure Active Directory user name and password, on their device, in the Azure AD login screen shown in Secure Hub.
-
Azure AD validates the user and sends an ID token.
-
Secure Hub shares the ID token with XenMobile Server.
-
XenMobile validates the ID token and the user information present in the ID token. XenMobile returns a session ID.
Azure account setup
To use Azure AD as your IdP, first log in to your Azure account and make these changes:
-
Register your custom domain and verify the domain. For details, see Add custom domain name to Azure Active Directory.
-
Extend your on-premises directory to Azure Active Directory using directory integration tools. For details, see Directory Integration.
To use Azure AD to enroll Windows 10 and Windows 11 devices, make the following changes to your Azure account:
-
Make the MDM a reliable party of Azure AD. To do so, click Azure Active Directory > Applications and then click Add.
-
Select Add an application from the gallery. Go to MOBILE DEVICE MANAGEMENT and then select on-premises MDM application. Save the settings.
You choose an on-premises application even if you signed up for Citrix XenMobile cloud. In Microsoft terminology, any non-multi-tenant application is an on-premises MDM application.
- In the application, configure XenMobile Server discovery, terms of use endpoints, and APP ID URI:
-
MDM Discovery URL:
https://<FQDN>:8443/<instanceName>/wpe -
MDM Terms of Use URL:
https://<FQDN>:8443/<instanceName>/wpe/tou -
APP ID URI:
https://<FQDN>:8443/
-
MDM Discovery URL:
-
Select the on-premises MDM application that you created in step 2. Enable the option Manage devices for these users to enable MDM management for all users or any specific user group.
For more information about using Azure AD with Windows 10 and Windows 11 devices, see the Microsoft article Azure Active Directory integration with MDM.
Configure Azure AD as your IdP
-
Locate or make note of the information you need from your Azure account:
- Tenant ID from the Azure application settings page.
- If you want to use Azure AD to enroll Windows 10 and Windows 11 devices, you also need:
- App ID URI: The URL for the server running XenMobile.
- Client ID: The unique identifier for your app from the Azure Configure page.
- Key: From the Azure application settings page.
-
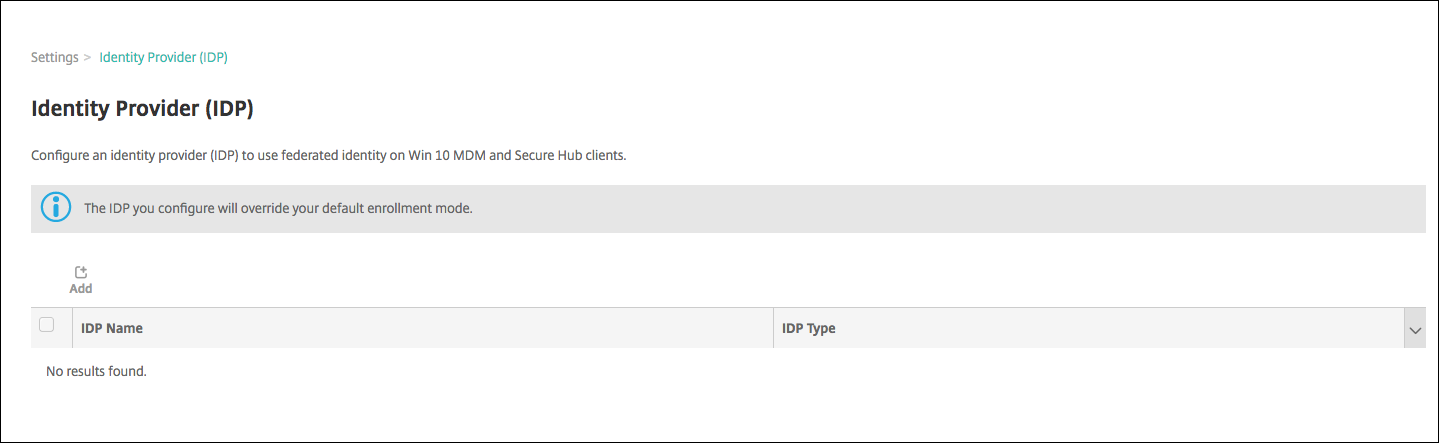
In the XenMobile console, click the gear icon in the upper-right corner. The Settings page appears.
-
Under Authentication, click Identity Provider (IDP). The Identity Provider page appears.
-
Click Add. The IDP configuration page appears.
-
Configure the following information about your IdP:
- IDP Name: Type a name for the IdP connection that you are creating.
- IDP Type: Choose Azure Active Directory as your IdP type.
- Tenant ID: Copy this value from the Azure application settings page. In the browser address bar, copy the section made up of numbers and letters.
For example, in
https://manage.windowszaure.com/acmew.onmicrosoft.com#workspaces/ActiveDirectoryExtensin/Directory/abc213-abc123-abc123/onprem..., the tenant ID is:abc123-abc123-abc123.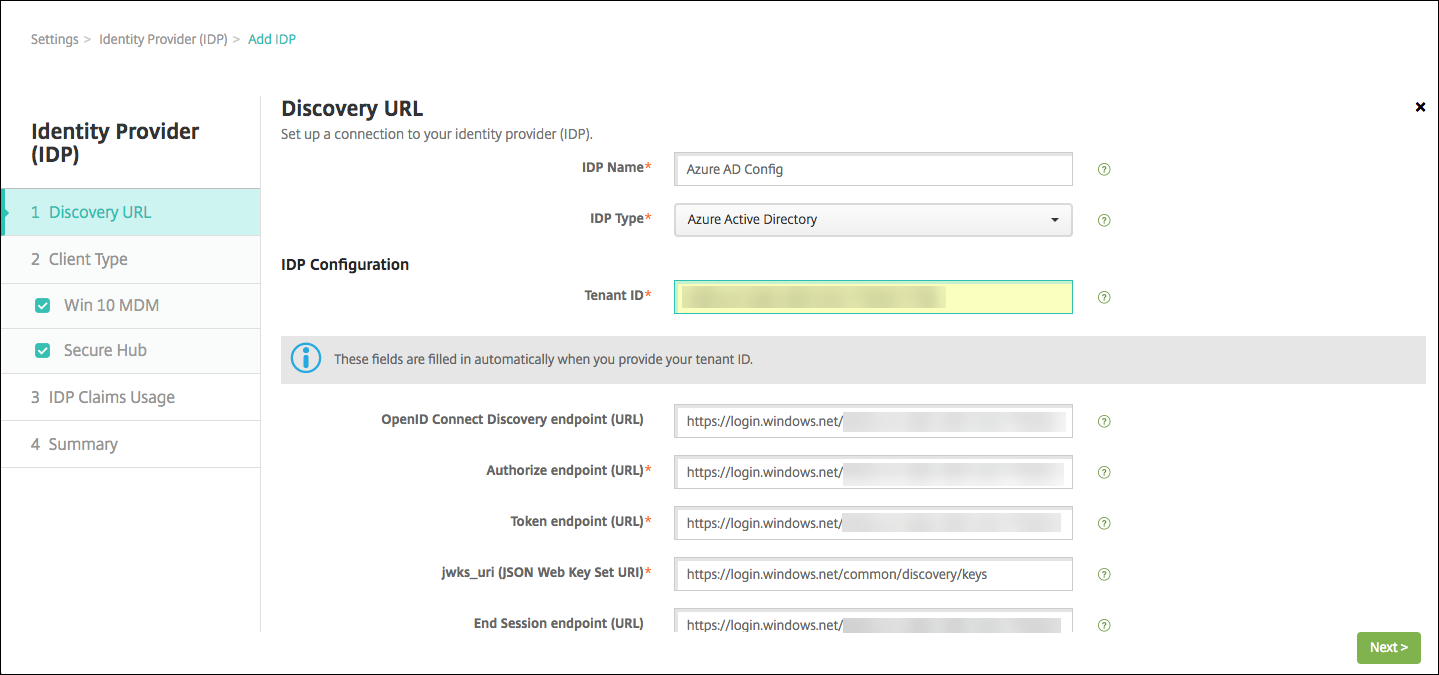
-
The rest of the fields automatically fill. When they are filled, click Next.
-
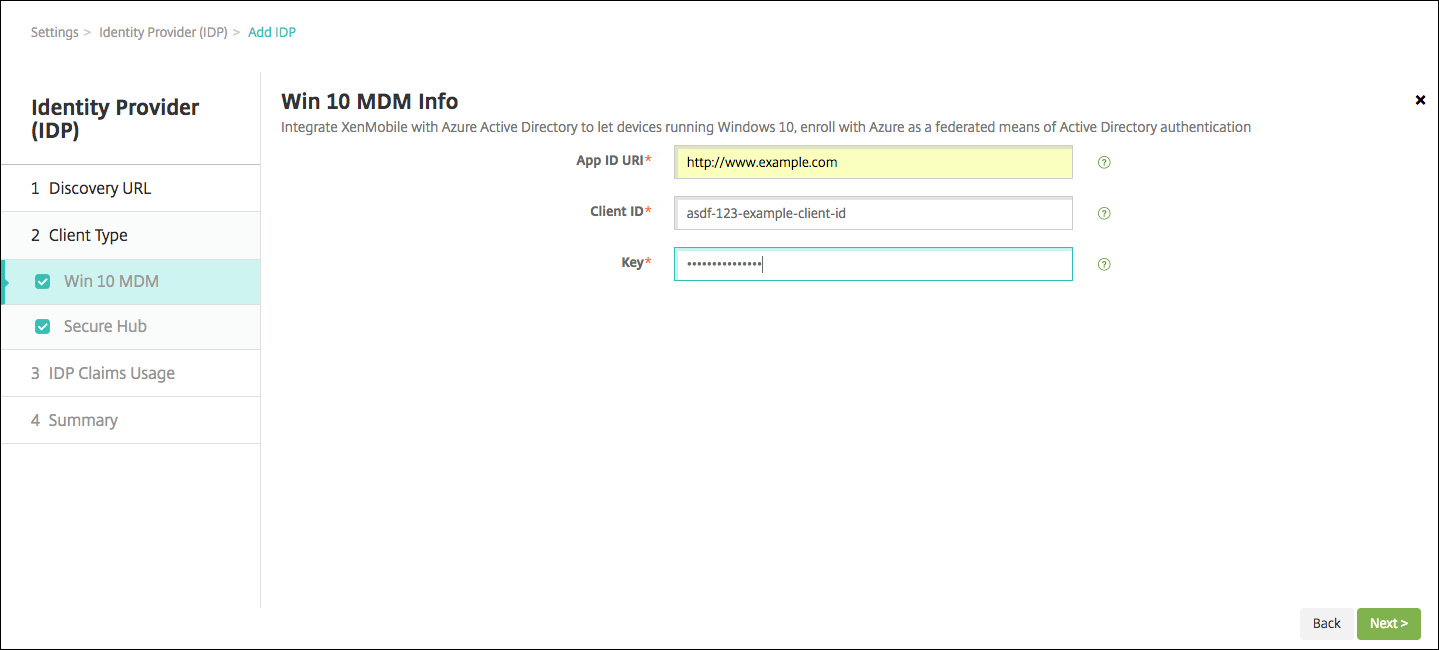
To configure XenMobile to enroll Windows 10 and Windows 11 devices using Azure AD for MDM enrollment, configure the following settings. To skip this optional step, clear Windows MDM.
- App ID URI: Type the URL for the XenMobile Server that you entered when you configured your Azure settings.
- Client ID: Copy and paste this value from the Azure Configure page. The client ID is the unique identifier for your app.
- Key: Copy this value from the Azure application settings page. Under keys, select a duration in the list and then save the setting. You can then copy the key and paste it into this field. A key is required when apps read or write data in Microsoft Azure AD.
-
Click Next.
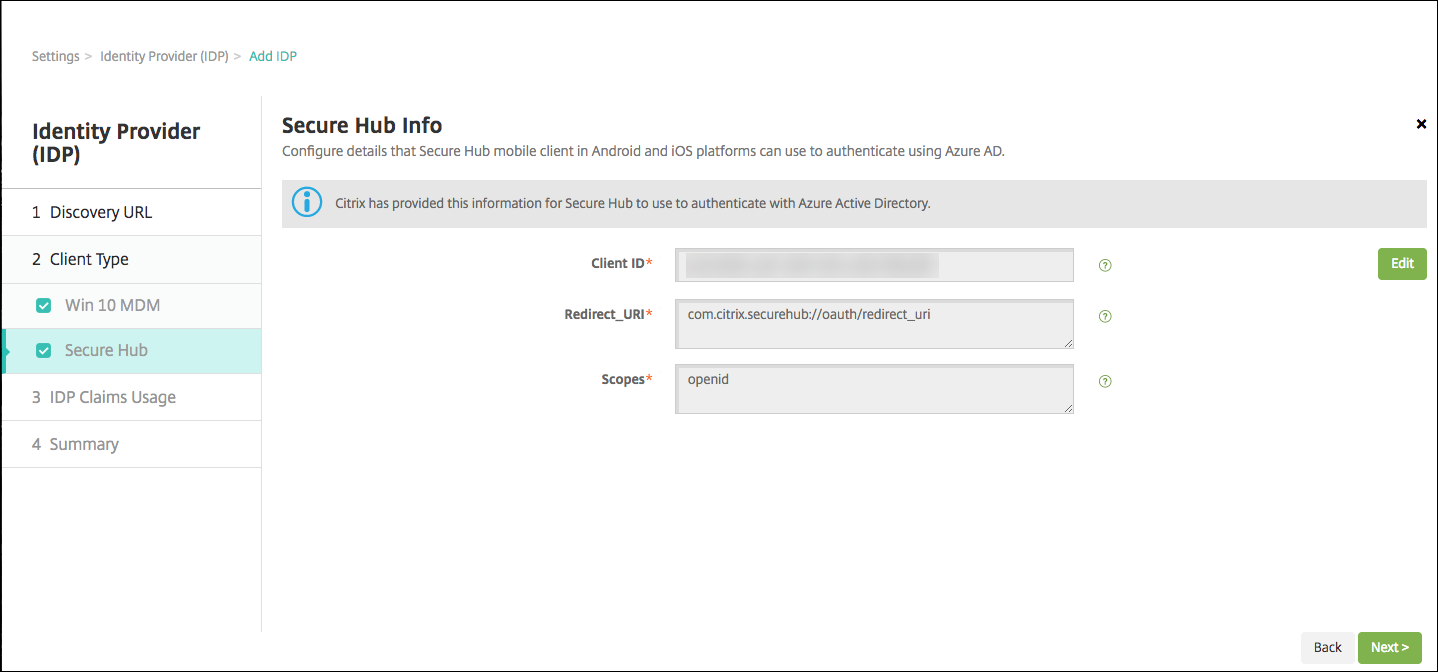
Citrix has registered Secure Hub with Microsoft Azure and maintains the information. This screen shows the details used by Secure Hub to communicate with Azure Active Directory. This page will be used in the future if any of this information needs a change. Edit this page only if Citrix advises you to.
-
Click Next.
-
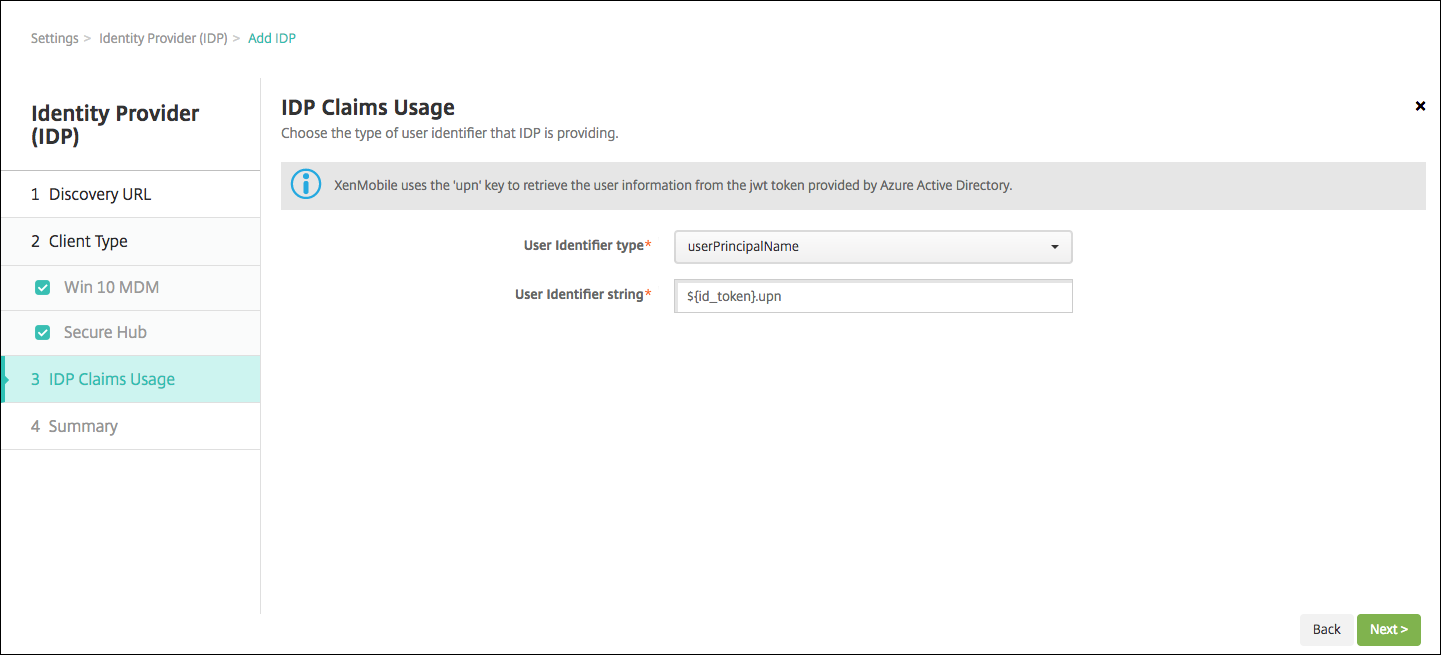
Configure the type of user identifier that your IdP provides:
- User Identifier type: Choose userPrincipalName from the list.
- User Identifier string: This field is automatically filled.
-
Click Next.
-
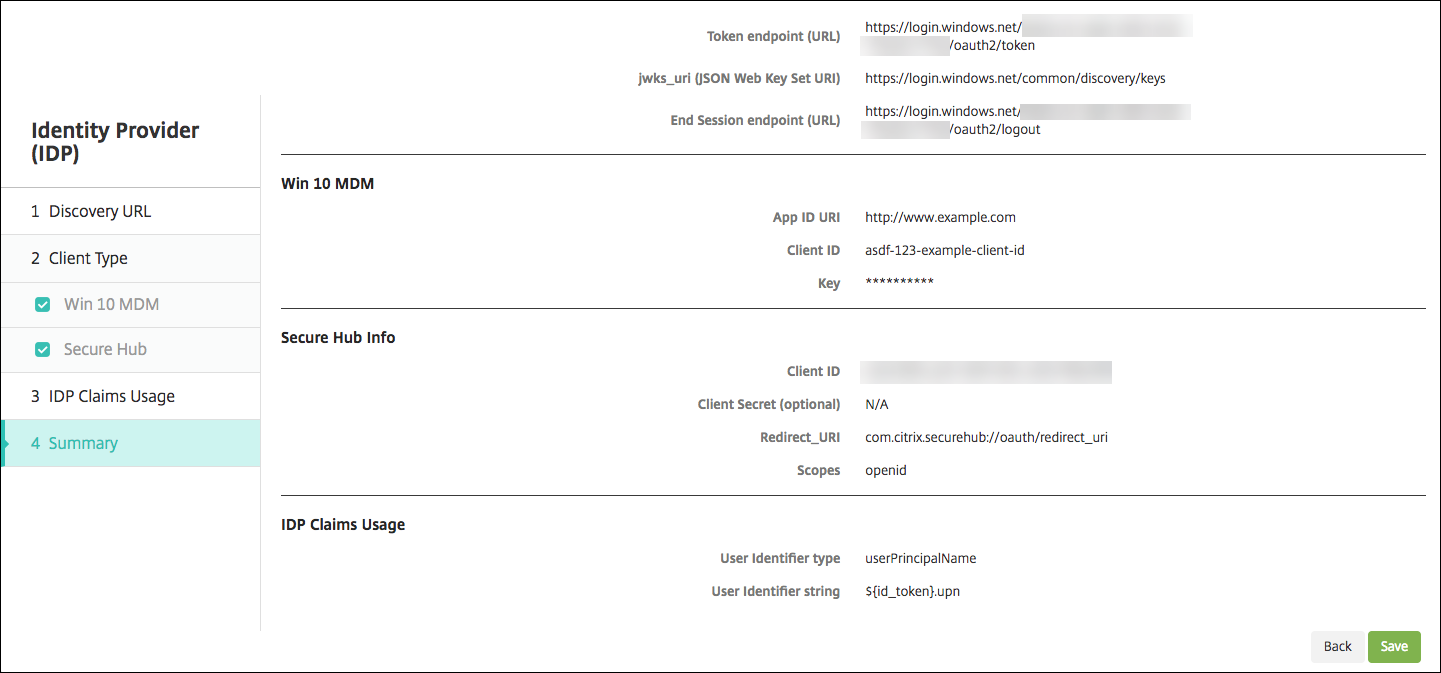
Review the Summary page and click Save.
What users experience
-
Users start Secure Hub. Users then enter the XenMobile Server Fully Qualified Domain Name (FQDN), a User Principle Name (UPN), or email address.
-
Users then click Yes, Enroll.
-
Users log on by using their Azure AD credentials.
-
Users complete the enrollment steps in the same way as any other enrollment through Secure Hub.
Note:
XenMobile doesn’t support authentication through Azure AD for enrollment invitations. If you send users an enrollment invitation that has an enrollment URL, users authenticate through LDAP instead of Azure AD.
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.