Restrictions device policy
The Restrictions device policy allows or restricts certain features or functionality on user devices, such as the camera. You can also set security restrictions, in addition to restrictions on media content and restrictions on the types of apps users can and can’t install. Most of the restriction settings default to On, or allows. The main exceptions are the iOS Security - Force feature and all Windows Tablet features, which default to Off, or restricts.
For Windows 10 RS2 Phone: After a Custom XML policy or Restrictions policy that disables Internet Explorer deploys to the phone, the browser remains enabled. To work around this issue, restart the phone. This issue is a third-party issue.
Tip:
Any option for which you select On means that the user can do the operation or use the feature. For example:
Camera. If On, the user can use the camera on their device. If Off, the user can’t use the camera on their device.
Screen shots. If On, the user can take screenshots on their device. If Off, the user can’t take screenshots on their device.
To add or configure this policy, go to Configure > Device Policies. For more information, see Device policies.
iOS settings
Some iOS restrictions policy settings apply only to specific versions of iOS, as noted here and in the XenMobile® console Restrictions policy page.
iOS restrictions policy settings can apply when the device is enrolled in user enrollment mode, unsupervised (full MDM) mode, or supervised mode. The following table shows the enrollment modes that are available for each restrictions policy setting for iOS 13 and later.
As noted the table, some settings that were previously available in unsupervised and supervised mode are available only in supervised mode starting with iOS 13. The following rules apply:
- If a supervised iOS 13+ device enrolls in XenMobile, the settings apply to the device.
- If an unsupervised iOS 13+ device enrolls in XenMobile, the settings don’t apply to the device.
- If an iOS 12 (or lower) device already enrolled in XenMobile and then upgrades to iOS 13, there are no changes. The settings apply to the device as they did before the upgrade.
For information on setting an iOS device to supervised mode, see To place an iOS device in Supervised mode by using the Apple Configurator.
| Setting | User Enrollment | Unsupervised | Supervised |
|---|---|---|---|
| Allow hardware controls | |||
| Camera | No | Yes | Yes |
| FaceTime | No | No (new in iOS 13) | Yes |
| Allow FaceTime Remote Control | No | No | Yes |
| Screenshots | Yes | No | Yes |
| Allow the Classroom app to remotely observe student screens | No | No | Yes |
| Allow the Classroom app to perform AirPlay and View Screen without prompting | No | No | Yes |
| Photo streams | No | Yes | Yes |
| Shared photo streams | No | Yes | Yes |
| Allow shared iPad temporary session | No | Yes | Yes |
| Voice dialing | No | Yes | Yes |
| Siri | Yes | Yes | Yes |
| Allow while device is locked | Yes | Yes | Yes |
| Siri profanity filter | No | No | Yes |
| Installing apps | No | No (new in iOS 13) | Yes |
| Alternative App Marketplace | No | No | Yes |
| Web Distribution apps | No | No | Yes |
| Allow global background fetch while roaming | No | Yes | Yes |
| Allow apps | |||
| iTunes Store | No | No (new in iOS 13) | Yes |
| In-app purchases | No | Yes | Yes |
| Require iTunes password for purchases | No | Yes | Yes |
| Safari | No | No (new in iOS 13) | Yes |
| Autofill | No | No (new in iOS 13) | Yes |
| Force fraud warning | Yes | Yes | Yes |
| Enable JavaScript | No | Yes | Yes |
| Block pop-ups | No | Yes | Yes |
| Accept cookies | No | Yes | Yes |
| Network - Allow iCloud actions | |||
| iCloud documents and data | No | No (new in iOS 13) | Yes |
| iCloud backup | No | Yes | Yes |
| iCloud photo keychain | No | Yes | Yes |
| iCloud photo library | No | Yes | Yes |
| Security - Force | |||
| Encrypted backups | Yes | Yes | Yes |
| Limited ad tracking | No | Yes | Yes |
| Passcode on first AirPlay pairing | Yes | Yes | Yes |
| Paired Apple Watch to use Wrist Detection | Yes | Yes | Yes |
| Sharing managed documents using AirDrop | Yes | Yes | Yes |
| Security - Allow | |||
| Accepting untrusted SSL certificates | No | Yes | Yes |
| Automatic update to certificate trust settings | No | Yes | Yes |
| Require managed pasteboard | Yes | Yes | Yes |
| Documents from managed apps in unmanaged apps | Yes | Yes | Yes |
| Unmanaged apps read managed contacts | No | No | Yes |
| Managed apps write unmanaged contacts | No | No | Yes |
| Documents from unmanaged apps in managed apps | Yes | Yes | Yes |
| Diagnostic submission to Apple | Yes | Yes | Yes |
| Touch ID to unlock device | No | Yes | Yes |
| Auto unlock | No | Yes | Yes |
| Passbook notifications when locked | No | Yes | Yes |
| Handoff | No | Yes | Yes |
| iCloud sync for managed apps | Yes | Yes | Yes |
| Backup for enterprise books | Yes | Yes | Yes |
| Notes and highlights sync for enterprise books | Yes | Yes | Yes |
| Internet results in Spotlight | No | Yes | Yes |
| Enterprise app trust | No | Yes | Yes |
| Allow Apple personalized advertising | No | Yes | Yes |
| Supervised only settings - Allow | |||
| Allow eSIM modification | No | No | Yes |
| Preserve eSIM on erase | No | No | Yes |
| Erase all content and settings | No | No | Yes |
| Configuring restrictions | No | No | Yes |
| Podcasts | No | No | Yes |
| Installing configuration profiles | No | No | Yes |
| Fingerprint modification | No | No | Yes |
| Installing apps from device | No | No | Yes |
| Keyboard shortcuts | No | No | Yes |
| Paired Apple watch | No | No | Yes |
| Passcode modification | No | No | Yes |
| Device name modification | No | No | Yes |
| Wallpaper modification | No | No | Yes |
| Automatically downloading apps | No | No | Yes |
| AirDrop | No | No | Yes |
| iMessage | No | No | Yes |
| Siri user-generated content | No | No | Yes |
| iBooks | No | No | Yes |
| Removing apps | No | Yes | Yes |
| Game Center | No | No (new in iOS 13) | Yes |
| Add friends | No | No | Yes |
| Multiplayer gaming | No | No (new in iOS 13) | Yes |
| Modifying account settings | No | No | Yes |
| Modifying app cellular data settings | No | No | Yes |
| Allow network drive connections | No | No | Yes |
| Allow USB device connections | No | No | Yes |
| Allow Find My Device | No | No | Yes |
| Allow Find My Friends | No | No | Yes |
| Modifying Find My Friends settings | No | No | Yes |
| Pairing with non-Configurator hosts | No | No | Yes |
| Predictive keyboards | No | No | Yes |
| Keyboard auto-corrections | No | No | Yes |
| Keyboard spell-check | No | No | Yes |
| Allow QuickPath Keyboard | No | No | Yes |
| Definition lookup | No | No | Yes |
| Single App bundle ID | No | No | Yes |
| News | No | No | Yes |
| Apple Music service | No | No | Yes |
| iTunes Radio | No | No | Yes |
| Notifications modification | No | No | Yes |
| Restricted App usage | No | No | Yes |
| Diagnostic submission modification | No | No | Yes |
| Bluetooth modification | No | No | Yes |
| Allow dictation | No | No | Yes |
| Force Wi-Fi on | No | No | Yes |
| Join only Wi-Fi networks installed by a Wi-Fi policy | No | No | Yes |
| Allow the Classroom app to perform AirPlay and View Screen without prompting | No | No | Yes |
| Allow the Classroom app to lock to an app and lock the device without prompting | No | No | Yes |
| Automatically join the Classroom app classes without prompting | No | No | Yes |
| Allow AirPrint | No | No | Yes |
| Allow storage of AirPrint credentials in Keychain | No | No | Yes |
| Allow discovery of AirPrint printers by using iBeacons | No | No | Yes |
| Allow AirPrint only to destinations with trusted certificates | No | No | Yes |
| Adding VPN configurations | No | No | Yes |
| Modifying cellular plan settings | No | No | Yes |
| Removing system apps | No | No | Yes |
| Setting up new nearby devices | No | No | Yes |
| Allow USB restricted mode | No | No | Yes |
| Force delayed software updates | No | No | Yes |
| Enforced software update delay | No | No | Yes |
| Force classroom request permission to leave classes | No | No | Yes |
| Force authentication before autofill | No | No | Yes |
| Force automatic date and time | No | No | Yes |
| Password AutoFill | No | No | Yes |
| Password proximity requests | No | No | Yes |
| Password Sharing | No | No | Yes |
| Modify personal Hotspot settings | No | No | Yes |
| Allow boot to recovery by an unpaired device | No | No | Yes |
| Install rapid security response | No | No | Yes |
| Remove rapid security response | No | No | Yes |
| Allow mail privacy protection | No | No | Yes |
| NFC | No | No | Yes |
| Allow App clips | No | No | Yes |
| Genmoji | No | No | Yes |
| Image Playground | No | No | Yes |
| Image Wand | No | No | Yes |
| iPhone Mirroring | No | No | Yes |
| Personalized Handwriting Results | No | No | Yes |
| Writing Tools | No | No | Yes |
| Call Recording | No | No | Yes |
| Apps To Be Hidden | No | No | Yes |
| Apps To Be Locked | No | No | Yes |
| Mail Summary | No | No | Yes |
| RCS Messaging | No | No | Yes |
| Allow external intelligence integrations | No | No | Yes |
| Allow signing in to external intelligence integrations | No | No | Yes |
| Allow Mail Smart Replies | No | No | Yes |
| Allow Notes Transcription | No | No | Yes |
| Allow Safari Summary | No | No | Yes |
| Allow visual intelligence summary | No | No | Yes |
| Allow Notes transcription Summary | No | No | Yes |
| Allow Apple Intelligence Report | No | No | Yes |
| Allow Default Calling App Modification | No | No | Yes |
| Allow Default Messaging App Modification | No | No | Yes |
| Allow External Intelligence Workspace IDs | No | No | Yes |
| Default Browser Modification | No | No | Yes |
| Allow Live Voicemail | No | No | Yes |
| Security - Show in lock screen | |||
| Control Center | Yes | Yes | Yes |
| Notification | Yes | Yes | Yes |
| Today view | Yes | Yes | Yes |
| Media content - Allow | |||
| Explicit music, podcasts, and iTunes U material | No | No (new in iOS 13) | Yes |
| Explicit sexual content in iBooks | No | Yes | Yes |
| Ratings region | No | Yes | Yes |
| Movies | No | Yes | Yes |
| TV Shows | No | Yes | Yes |
| Apps | No | Yes | Yes |
-
Allow hardware controls
-
Camera: Allow users to use the camera on their devices.
- FaceTime: Allow users to use FaceTime on their devices. For supervised iOS devices.
- Allow FaceTime Remote Control: Allow a remote FaceTime session to request control of the device. For supervised iOS devices. Available for iOS 18.4 and later.
-
Screenshots: Allow users to take screenshots on their devices.
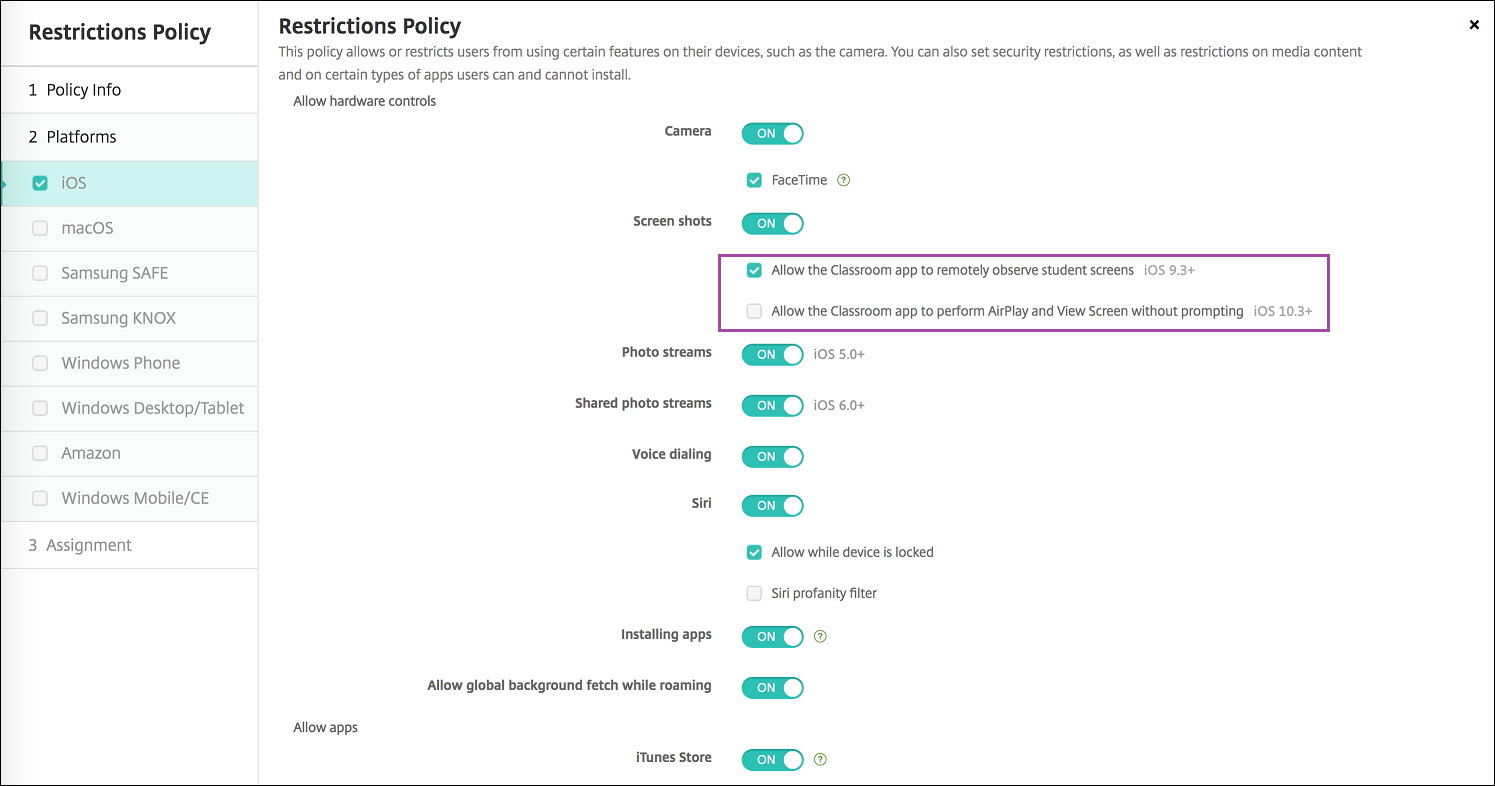
- Allow the Classroom app to remotely observe student screens: If this restriction is unselected, an instructor can’t use the Classroom app to remotely observe student screens. The default setting is selected, an instructor can use the Classroom app to observe student screens. The setting for Allow the Classroom app to perform AirPlay and View Screen without prompting determines whether students receive a prompt to give the instructor permission. For supervised iOS devices.
- Allow the Classroom app to perform AirPlay and View Screen without prompting: If this restriction is selected, the instructor can perform AirPlay and View Screen on a student device, without prompting for permission. The default setting is unselected. For supervised iOS devices.
- Photo streams: Allow users to use MyPhotoStream to share photos through iCloud to all their iOS devices.
- Shared photo streams: Allow users to use iCloud Photo Sharing to share photos with coworkers, friends, and family.
- Allow shared iPad temporary session: Prevents access to temporary sessions on shared iPads when the setting is Off. Default is On.
- Voice dialing: Enables voice dialing on user devices.
-
Siri: Allows users to use Siri.
- Allow while device is locked: Allow users to use Siri while their devices are locked.
-
Siri profanity filter: Enable the Siri profanity filter. The default is to restrict this feature, which means no profanity filtering is done.
For more information about Siri and security, see Siri and dictation policies.
- Installing apps: Allow users to install apps. For supervised iOS devices.
- Alternative App Marketplace: Prevents installation of alternative marketplace apps from the web and prevents any installed alternative marketplace apps from installing apps. This feature is available from iOS 17.4 and later versions. Default is On. For supervised iOS devices.
- Web Distribution apps: Enable customer admins to block the web distributed third party apps on iOS devices. This is applicable for iOS versions 17.5 and later. For more information, see Restrictions.
- Allow global background fetch while roaming: Allow devices to automatically sync mail accounts to iCloud while the device is roaming. When Off, disables global background fetch activity when an iOS phone is roaming. Defaults to On.
-
Camera: Allow users to use the camera on their devices.
-
Allow apps
- iTunes Store: Allow users to access the iTunes Store. For supervised iOS devices.
-
In-app purchases: Allow users to make in-app purchases.
- Require iTunes password for purchases: Require a password for in-app purchases. The default is to restrict this feature, which means no password is required for in-app purchases.
-
Safari: Allow users to access Safari. For supervised iOS devices.
- Autofill: Allow users to set up autofill for user names and passwords on Safari.
- Force fraud warning: If this setting is enabled and users visit a suspected phishing website, Safari alerts users. The default is to restrict this feature, which means no warnings are issued.
- Enable JavaScript: Allow JavaScript to run on Safari.
- Block pop-ups: Block pop-ups while viewing websites. The default is to restrict this feature, which means pop-ups aren’t blocked.
- Accept cookies: Set to what extent cookies are accepted. In the list, choose an option to allow or restrict cookies. The default option is Always, which allows all websites to save cookies in Safari. Other options are Current website only, Never, and From visited sites only.
-
Network - Allow iCloud actions
- iCloud documents and data: Allow users to sync documents and data to iCloud. For supervised iOS devices.
- iCloud backup: Allow users to back up their devices to iCloud.
- iCloud keychain: Allow users to store passwords, Wi-Fi network, credit card, and other information in the iCloud Keychain.
- Cloud photo library: Allow users to access their iCloud photo library.
-
Security - Force
The default is to restrict the following features, which means no security features are enabled.
- Encrypted backups: Force backups to iCloud to be encrypted.
- Limited ad tracking: Block targeted ad tracking.
- Passcode on first Airplay pairing: Require that AirPlay-enabled devices are verified with a one-time onscreen code before they can use AirPlay.
- Paired Apple Watch to use Wrist Detection: Require a paired Apple Watch to use Wrist Detection.
- Sharing managed documents using AirDrop: Setting this option to On makes AirDrop appear as an unmanaged drop target.
-
Security - Allow
- Accepting untrusted SSL certificates: Allow users to accept websites’ untrusted SSL certificates.
- Automatic update to certificate trust settings: Allow trusted certificates to be updated automatically.
-
Require managed pasteboard: If On, allow copy and paste functionality to follow the same restrictions that you apply to Documents from managed apps in unmanaged apps and Documents from unmanaged apps in managed apps. Default is Off. For example, you configure the following:
- Require managed pasteboard: On
- Documents from managed apps in unmanaged apps: Off
- Documents from unmanaged apps in managed apps: On
Note:
After you deploy the policy to iOS devices, users can’t copy and paste data from managed apps to unmanaged apps, but they can copy and paste data from unmanaged apps to managed apps.
- Documents from managed apps in unmanaged apps: Allow users to move data from managed (corporate) apps to unmanaged (personal) apps.
- Documents from unmanaged apps in managed apps: Allow users to move data from unmanaged (personal) apps to managed (corporate) apps.
- Diagnostic submission to Apple: Allow anonymous diagnostic data about users’ devices to be sent to Apple.
- Touch ID to unlock device: Allow users to use their fingerprints to unlock their devices.
- Auto unlock: If Off, the user can’t use the Apple watch to unlock a paired iPhone. Default is On. Available for iOS 14.5 or later.
- Passbook notifications when locked: Allow Passbook notifications to appear on the lock screen.
- Handoff: Allow users to transfer activities from one iOS device to another nearby iOS device.
- iCloud sync for managed apps: Allow users to sync managed apps to iCloud.
- Backup for enterprise books: Allow enterprise books to be backed up to iCloud.
- Notes and highlights sync for enterprise books: Allow notes and highlights users have added to enterprise books to be synced to iCloud.
- Enterprise app trust: Allow enterprise applications to be trusted. Enterprise apps are any apps that are custom-made for your organization. These can be made internally or they can be developed and bought from an external vendor. For additional information, see Install custom enterprise apps on iOS.
- Internet results in Spotlight: Allow Spotlight to show search results from the Internet in addition to the device.
- Unmanaged apps read managed contacts: Optional. Only available if Documents from managed apps in unmanaged apps is disabled. If this policy is enabled, unmanaged apps can read data from managed accounts’ contacts. Default is Off. Available from iOS 12.
- Managed apps write unmanaged contacts: Optional. If enabled, allow managed apps to write contacts to unmanaged accounts’ contacts. If Documents from managed apps in unmanaged apps is enabled, this restriction has no effect. Default is Off. Available from iOS 12.
- Allow Apple personalized advertising: If Off, users’ data isn’t used by the Apple advertising platform to deliver personalized ads. Default is On. Available for iOS 14.0 or later.
-
Supervised only settings - Allow
These settings apply only to supervised devices. For the steps on setting an iOS device to supervised mode, see To place an iOS device in Supervised mode by using the Apple Configurator.
- Allow eSIM modification: Allow users to change the eSIM settings on their devices.
- Preserve eSIM on erase: If On, the system preserves eSIM when it erases the device due to too many failed password attempts or the Erase All Content and Settings option in Settings > General > Reset. Default is Off.
Note:
The system doesn’t preserve eSIM if Find My initiates erasing the device.
- Erase all content and settings: Allow users to erase all content and settings from their devices.
- Configuring restrictions: Allow users to configure parental controls on their devices.
- Podcasts: Allow users to download and sync podcasts.
- Installing configuration profiles: Allow users to install a configuration profile other than that the one deployed by you.
- Fingerprint modification: Allow users to change or delete their Touch ID fingerprint.
- Installing apps from device: Allow users to install apps. Disabling this setting stops end users from installing new apps. The App Store is disabled and its icon is removed from the Home Screen.
- Keyboard shortcuts: Allow users to create custom keyboard shortcuts for words or phrases that they use often.
- Paired Apple watch: Allow users to pair an Apple Watch to a supervised device.
- Passcode modification: Allow users to change the passcode on a supervised device.
- Device name modification: Allow users to change the name of their device.
- Wallpaper modification: Allow users to change the wallpaper on their devices.
- Automatically downloading apps: Allow apps to download.
- AirDrop: Allow users to share photos, videos, websites, locations, and more with nearby iOS devices.
- iMessage: Allow users to text over Wi-Fi with iMessage.
- Siri user-generated content: Allow Siri to query user-generated content from the web. Consumers, not traditional journalists; produce user-generated content. For example, content found on Twitter or Facebook is user-generated.
- iBooks: Allow users to use the iBooks app.
- Removing apps: Allow users to remove apps from their devices.
-
Game Center: Allow users to play online games through Game Center on their devices.
- Add friends: Allow users to send a notification to a friend to play a game.
- Multiplayer gaming: Allow users to start multiplayer game play on their devices.
- Modifying account settings: Allow users to modify their device account settings.
- Modifying app cellular data settings: Allow users to modify how apps use cellular data.
- Allow network drive connections: Prevents connecting to network drives in the Files app when the setting is Off. Default is On.
- Allow USB device connections: Prevents connecting to any connected USB devices in the Files app when the setting is Off. Default is On.
- Allow Find My Device: Disables the Find My Device option in the Find My app when the setting is Off. Default is On.
- Allow Find My Friends: Disables the Find My Friends option in the Find My app when the setting is Off. Default is On.
- Modifying Find My Friends settings: Allow users to change their Find My Friends settings.
- Pairing with non-Configurator hosts: Allow admin to control to which devices a user device can pair. Disabling this setting prevents pairing except with the supervising host running the Apple Configurator. If no supervising host certificate is configured, all pairing is disabled.
- Predictive keyboards: Allow user devices to use the predictive keyboard for suggesting words as they type. Disable this option in situations such as administering standardized tests where you do not want users to have access to suggested words.
- Keyboard auto-corrections: Allow user devices to use keyboard autocorrect. Disable this option in situations such as administering standardized tests where you do not want users to have access to autocorrect.
- Keyboard spell-check: Allow user devices to use spell checking while typing. Disable this option in situations such as administering standardized tests where you do not want users to have access to the spell-checker.
- Allow QuickPath Keyboard: Disables the QuickPath Keyboard when the setting is Off. Default is On.
- Definition lookup: Allow user devices to use definition look-up while typing. Disable this option in situations such as administering standardized tests where you do not want users to look up definitions as they type.
- Single App bundle ID: Create a list of apps that are allowed to retain control over the device and prevent interaction with other apps or functions. To add an app, click Add, type an App name, and click Save. Repeat that process for each app you want to add.
- News: Allow users to use the News app.
- Apple Music service: Allow users to use the Apple Music service. If you don’t allow Apple Music service, the Music app runs in classic mode.
- iTunes Radio: Allow users to use iTunes Radio.
- Notifications modification: Allow users to modify notification settings.
-
Restricted App usage: Allow users to use all apps or to use or not use apps, based on the bundle IDs you provide. Applies only to supervised devices. If you select Only allow some apps, add an app with the bundle ID
com.apple.webappto allow web clips.Note:
Beginning with iOS 11, Apple introduced changes to the policies that are available to app restrictions. Apple no longer lets you remove access to the Settings app and the Phone app by restricting the appropriate iOS application bundle.
After you configure the Restrictions device policy to block some apps and then deploy the policy: If you later want to allow some or all of those apps, changing and deploying the Restrictions device policy doesn’t change the restrictions. In this case, iOS doesn’t apply the changes to the iOS profile. To continue, use the Profile Removal policy to remove the iOS Profile and then deploy the updated Restrictions device policy.
If you change this setting to Only allow some apps: Before deploying this policy, advise users of devices enrolled using the Apple Deployment Program to sign in to their Apple accounts from the Setup Assistant. Otherwise, users might have to disable two-factor authentication on their devices to sign in to their Apple accounts and access-allowed apps.
- Diagnostic submission modification: Allow users to modify the diagnostic submission and app analytics settings in the Settings > Diagnostics & Usage pane.
- Bluetooth modification: Allow users to modify Bluetooth settings.
- Allow dictation: Supervised only. If this restriction is set to Off, dictation input isn’t allowed, including speech-to-text. The default setting is On.
- Force Wi-Fi on: Prevents Wi-Fi from being turned on or off in the Settings or Control Center. Activating airplane mode has no effect on this restriction, which does not prevent you from choosing which Wi-Fi network to connect to. Default is Off.
- Join only WiFi networks installed by a WiFi policy: Optional. Supervised only. If this restriction is set to On, the device can join Wi-Fi networks only when they were set up through a configuration profile. The default setting is Off.
- Allow the Classroom app to perform AirPlay and View Screen without prompting: If this restriction is selected, the instructor can perform AirPlay and View Screen on a student device, without prompting for permission. The default setting is unselected. For supervised iOS devices.
- Allow the Classroom app to lock to an app and lock the device without prompting: If this restriction is set to On, the Classroom app automatically locks user devices to an app and locks the device, without prompting the users. The default setting is Off. For supervised devices running iOS 11 (minimum version).
- Automatically join the Classroom app classes without prompting: If this restriction is set to On, the Classroom app automatically joins users to classes, without prompting the users. The default setting is Off. For supervised devices running iOS 11 (minimum version).
-
Allow AirPrint: If this restriction is set to Off, users can’t print with AirPrint. The default setting is On. When this restriction is On, these extra restrictions appear. For supervised devices running iOS 11 (minimum version).
- Allow storage of AirPrint credentials in Keychain: If this restriction is unselected, the AirPrint user name and password aren’t stored in the Keychain. The default setting is selected. For supervised devices running iOS 11 (minimum version).
- Allow discovery of AirPrint printers by using iBeacons: If this restriction is unselected, iBeacon discovery of AirPrint printers is disabled. This prevents spurious AirPrint Bluetooth beacons from phishing for network traffic. The default setting is selected. For supervised devices running iOS 11 (minimum version).
- Allow AirPrint only to destinations with trusted certificates: If this restriction is selected, users can use AirPrint to print only to destinations with trusted certificates. The default setting is unselected. For supervised devices running iOS 11 (minimum version).
- Adding VPN configurations: If this restriction is set to Off, users can’t create VPN configurations. The default setting is On. For supervised devices running iOS 11 (minimum version).
- Modifying cellular plan settings: If this restriction is set to Off, users can’t modify cellular plan settings. The default setting is On. For supervised devices running iOS 11 (minimum version).
- Removing system apps: If this restriction is set to Off, users can’t remove system apps from their device. The default setting is On. For supervised devices running iOS 11 (minimum version).
- Setting up new nearby devices: If this restriction is set to Off, users can’t set up new nearby devices. The default setting is On. For supervised devices running iOS 11 (minimum version).
- Allow USB restricted mode: If Off, the device can always connect to USB accessories while locked. Default is On. Available only for supervised iOS 11.3 and later devices.
- Force delayed software updates: If On, delays user visibility of Software Updates. With this restriction in place, the user doesn’t see a software update until the specified number of days after the software update release date. Default is Off. Available only for supervised iOS 11.3 and later devices.
- Enforced software update delay (days): Allows you to specify the number of days to delay a software update on the device. The maximum delay is 90 days. Default is 30 days. Available only for supervised iOS 11.3 and later devices.
- Force classroom request permission to leave classes: If On, a student enrolled in an unmanaged course with Classroom must request permission from the teacher when trying to leave the course. Default is Off. Available only for supervised iOS 11.3 and later devices.
- Force authentication before autofill: If On, the user needs to authenticate before the system can autofill passwords or credit card information in Safari and apps. Only supported on devices with Face ID or Touch ID. Default is Off.
- Force automatic date and time: Allows you to automatically set the date and time on supervised devices. If On, device users can’t turn off Set Automatically under General > Date & Time. The time zone on the device updates only when the device can determine its location. That is, when a device has a cellular connection or a Wi-Fi connection with location services enabled. Default is Off. Available only for supervised iOS 12 and later devices.
- Password AutoFill: Optional. If disabled, users can’t use the AutoFill Passwords or Automatic Strong Passwords features. Default is On. Available from iOS 12.
- Password proximity requests: Optional. If disabled, users’ devices don’t request passwords from nearby devices. Default is On. Available from iOS 12.
- Password Sharing: Optional. If disabled, users can’t share their passwords using the AirDrop Passwords feature. Default is On. Available from iOS 12.
- Modify personal Hotspot settings: Disables modifications to the personal hotspot setting when it is turned Off. Default is On.
- Allow boot to recovery by an unpaired device: If On, allows devices to be booted into recovery by an unpaired device. The default is Off. Available for iOS 14.5 or later.
- Install rapid security response: If Off, prohibits installation of rapid security responses. The default is On.
- Remove rapid security response: If Off, prohibits removal of rapid security responses. The default is On.
- Allow mail privacy protection: If Off, disables Mail Privacy Protection on the device. The default is On. Available for iOS 15.2 or later.
- NFC: If Off, disables NFC. The default is On. Available for iOS 14.2 or later.
- Allow App clips: If Off, prevents a user from adding any App Clips and removes any existing App Clips on the device. The default is On. Available for iOS 14.0 or later.
- Genmoji: If Off, prohibits creating new Genmoji. Available for iOS 18 or later.
- Image Playground: If Off, prohibits the use of image generation. Available for iOS 18 or later.
- Image Wand: If Off, prohibits the use of Image Wand. Available for iOS 18 or later.
- iPhone Mirroring: If Off, prohibits the use of iPhone Mirroring. When used on iOS, this prevents the iPhone from mirroring to any Mac. Available for iOS 18 or later.
- Personalized Handwriting Results: If Off, prevents the system from generating text in the user’s handwriting. Available for iOS 18 or later.
- Writing Tools: If Off, disables Apple Intelligence writing tools. Available for iOS 18 or later.
- Call Recording: If Off, disables call recording. Requires a supervised device. Available for iOS 18.1 or later.
- Apps To Be Hidden: If Off, prohibits the ability for the user to hide apps. When used on iOS, this prevents the user from hiding apps but still allows them to leave apps in the App Library while removing them from the home screen. Requires a supervised device. Available for iOS 18 or later.
- Apps To Be Locked: If Off, prohibits the ability for the user to lock apps. When used on iOS, this prevents the user from locking apps and, as a result, also prevents hiding apps. Requires a supervised device. Available for iOS 18 or later.
- Mail Summary: If Off, prohibits the ability to manually create summaries of email messages. When used on iOS, this does not affect automatic summary generation. Requires a supervised device. Available for iOS 18.1 or later.
- RCS Messaging: If Off, prevents the use of RCS messaging. Requires a supervised device. Available for iOS 18.1 or later.
- Allow external intelligence integrations: If Off, disables the use of external, cloud-based intelligence services with Siri. The default is On. Available for iOS 18.2 and later.
- Allow signing in to external intelligence integrations: If Off, forces external intelligence providers into anonymous mode. If a user is already signed in to an external intelligence provider, applying this restriction will cause them to be signed out when the next request is attempted. The default is On. Available for iOS 18.2 and later.
- Allow Mail Smart Replies: If Off, disables smart replies in Mail. The default is On. Available for iOS 18.2 and later.
- Allow Notes Transcription: If Off, disables transcription in Notes. The default is On. Available for iOS 18.2 and later.
- Allow Safari Summary: If Off, the system disables the ability to summarize content in Safari. The default is On. Available for iOS 18.4 and later.
- Allow visual intelligence summary: If Off, the system disables visual intelligence summarization. The default is On. Available for iOS 18.3 and later.
- Allow Notes transcription Summary: If Off, disables transcription summarization in Notes. The default is On. Available for iOS 18.3 and later.
- Allow Apple Intelligence Report: If Off, the system disables Apple Intelligence reports. The default is On. Available for iOS 18.4 and later.
- Allow Default Calling App Modification: If Off, disables default calling app preference modification. The MDM Settings command to set the default calling app preference still works when this is applied. The default is On. Available for iOS 18.4 and later.
- Allow Default Messaging App Modification: If Off, disables default messaging app preference modification. The MDM Settings command to set the default messaging app preference still works when this is applied. The default is On. Available for iOS 18.4 and later.
-
Allow External Intelligence Workspace IDs: An array of strings, but currently restricted to a single element. If present, Apple Intelligence only allows the given external integration workspace ID to be used, and requires a sign-in to make requests; the user will be required to sign in to integrations that support signing in. Multiple payloads combine using an intersect operation. This means the allowed set of workspace IDs can become the empty set if conflicting values are specified in multiple payloads. Available for iOS 18.3 and later.
- External Intelligence Workspace ID: To add an external intelligence workspace ID, click Add, type an External Intelligence Workspace ID, and click Save. Repeat that process for each workspace ID you want to add.
- Default Browser Modification: If Off, prohibits the modification of the default browser preference. When used on iOS, this still allows the MDM Settings command to set the default browser preference. Requires a supervised device. Available for iOS 18.2 or later.
- Allow Live Voicemail: If Off, the system disables live voicemail on the device. The default is On. Available for iOS 17.2 and later.
-
Security - Show in lock screen
- Control Center: Allow access to the Control Center on the lock screen. The Control Center lets users easily modify Airplane Mode, Wi-Fi, Bluetooth, Do Not Disturb Mode, and Lock Rotation settings.
- Notification: Allow notifications on the lock screen.
- Today view: Allow Today View, which aggregates information such as the weather and the current day’s calendar items, on the lock screen.
-
Media content - Allow
- Explicit music, podcasts, and iTunes U material: Allow explicit material on users’ devices.
- Explicit sexual content in iBooks: Allow explicit material to be downloaded from iBooks.
- Ratings region: Set the region from which parental control ratings are got. In the list, click a country to set the ratings region. The default is United States.
- Movies: Set whether movies are allowed on users’ devices. If movies are allowed, optionally set the ratings level for movies. In the list, click an option to allow or restrict movies on the device. The default is Allow all movies.
- TV Shows: Set whether TV shows are allowed on users’ devices. If TV shows are allowed, optionally set the ratings level for TV shows. In the list, click an option to allow or restrict TV shows on the device. The default is Allow all TV Shows.
- Apps: Set whether apps are allowed on users’ devices. If apps are allowed, optionally set the ratings level for apps. In the list, click an option to allow or restrict apps on the device. The default is Allow all apps.
-
Policy settings
-
Remove policy: Choose a method for scheduling policy removal. Available options are Select date and Duration until removal (in hours)
- Select date: Click the calendar to select the specific date for removal.
- Duration until removal (in hours): Type a number, in hours, until policy removal occurs. Only available for iOS 6.0 and later.
- Profile scope: Select whether this policy applies to a User or an entire System. The default is User. This option is available only on iOS 9.3 and later.
-
Remove policy: Choose a method for scheduling policy removal. Available options are Select date and Duration until removal (in hours)
macOS settings
-
Preferences
-
Restrict items in System Preferences: Allow or restrict user access to System Preferences. The default is Off, which allows users full access to System Preferences. If enabled, configure the following settings.
-
System Preference Pane: Select whether the settings you select are enabled or disabled. The default is to enable all settings, which are On by default.
- Users & Groups
- General
- Accessibility
- App Store
- Software Update
- Bluetooth
- CDs & DVDs
- Date & Time
- Desktop & Screen Saver
- Displays
- Dock
- Energy Saver
- Extensions
- FibreChannel
- iCloud
- Ink
- Internet Accounts
- Keyboard
- Language & Text
- Mission Control
- Mouse
- Network
- Notifications
- Parental Controls
- Printers & Scanners
- Profiles
- Security & Privacy
- Sharing
- Sound
- Diction & Speech
- Spotlight
- Startup Disk
- Time Machine
- Trackpad
- Xsan
-
System Preference Pane: Select whether the settings you select are enabled or disabled. The default is to enable all settings, which are On by default.
-
Restrict items in System Preferences: Allow or restrict user access to System Preferences. The default is Off, which allows users full access to System Preferences. If enabled, configure the following settings.
-
Apps
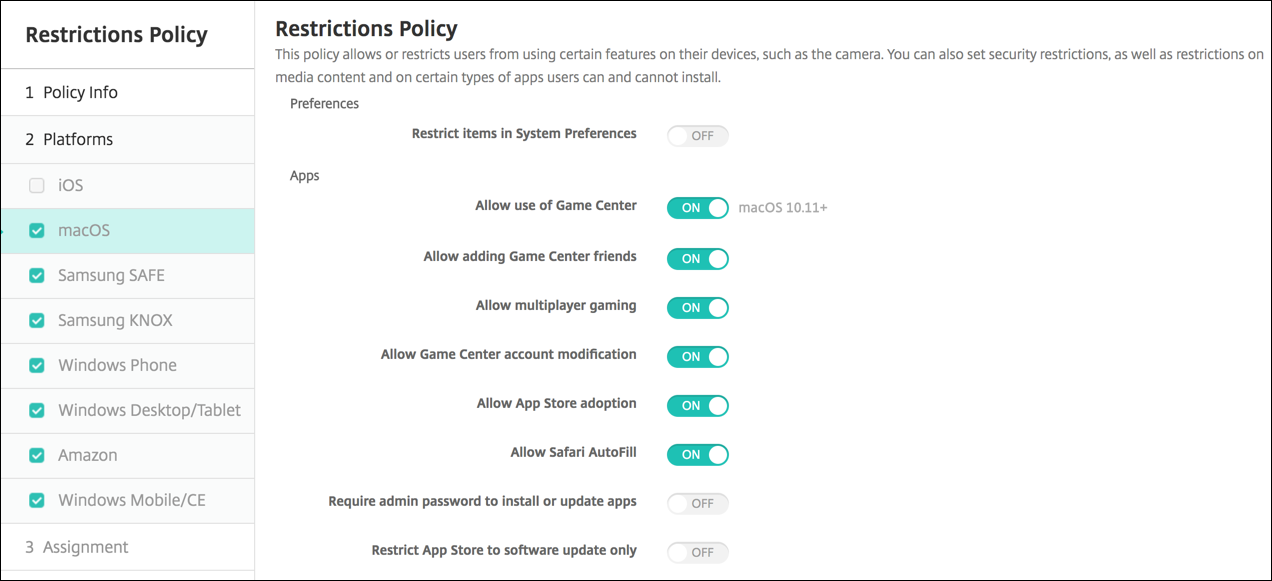
- Allow use of Game Center: Allow users to play online games through Game Center. The default is On.
- Allow adding Game Center friends: Allow users to send a notification to a friend to play a game. The default is On.
- Allow multiplayer gaming: Allow users to start multiplayer game play. The default is On.
- Allow Game Center account modification: Allow users to modify their Game Center account settings. The default is On.
- Allow App Store adoption: Allow or restrict the App Store to adopt apps that preexist in OS X. The default is On.
- Allow Safari Autofill: Allow Safari to automatically populate fields on websites with passwords, addresses, and other basic information that it has stored. The default is On.
- Require admin password to install or update apps: Require an administrator password to install or update apps. The default is Off, which means no administrator password is required.
- Restrict App Store to software update only: Restrict the App Store to updates only, which disables all tabs in the App Store except Updates. The default is Off, which allows full App Store access.
-
Restrict which apps are allowed to open: Restrict or allow apps users can use. The default is OFF, which allows all apps to be used. If enabled, configure the following settings:
- Allowed Apps: Click Add, enter the name and bundle ID for an app allowed to launch, and then click Save. Repeat this step for each app allowed to launch.
- Disallowed Folders: Click Add, type the file path to a folder to which you want to restrict user access (for example, /Applications/Utilities), and then click Save. Repeat this step for all folders that you don’t want users to access.
- Allowed folders: Click Add, type the file path to a folder to which you want to grant user access, and then click Save. Repeat this step for all folders that you want users to access.
-
Widgets
-
Allow only the following Dashboard widgets to run: Allow or restrict which Dashboard widgets, such as World Clock or Calculator, users are allowed to run. The default is Off, which allows users to run all widgets. If enabled, configure the following setting:
- Allowed Widgets: Click Add, type the name and ID of a widget that is allowed to run, and then click Save. Repeat this step for each widget that you want to run on the Dashboard.
-
Allow only the following Dashboard widgets to run: Allow or restrict which Dashboard widgets, such as World Clock or Calculator, users are allowed to run. The default is Off, which allows users to run all widgets. If enabled, configure the following setting:
-
Media
- Allow AirDrop: Allow users to share photos, videos, websites, locations, and more with nearby iOS devices.
-
Sharing
- Automatically enable new sharing services: Select whether to automatically enable sharing services.
- Mail: Select whether to allow a shared mailbox.
- Facebook: Select whether to allow a shared Facebook account.
- Video Services - Flickr, Vimeo, Tudou, and Youku: Select whether to allow shared video services.
- Add to Aperture: Select whether to allow shared ability to add to Aperture.
- Sina Weibo: Select whether to allow a shared Sina Weibo microblogging account.
- Twitter: Select whether to allow a shared Twitter account.
- Messages: Select whether to allow shared access to messages.
- Add to iPhoto: Select whether to allow shared ability to add to iPhoto.
- Add to Reading List: Select whether to allow shared ability to add to Reading List.
- AirDrop: Select whether to allow a shared AirDrop account.
-
Functionality
- Lock desktop picture: Select whether users can change the desktop picture. The default is Off, which means users can change the desktop picture.
- Allow use of camera: Select whether users can use the camera on their Macs. The default is Off, which means users can’t use the camera.
- Allow Apple Music: Allow users to use the Apple Music service (macOS 10.12 and later). If you don’t allow Apple Music service, the Music app runs in classic mode. Applies only to supervised devices. Defaults to On.
- Allow Spotlight Suggestions: Select whether users can use Spotlight Suggestions to search their Mac and to provide Spotlight Suggestions from the Internet, iTunes, and the App Store. The default is Off, which prevents users from using Spotlight Suggestions.
- Allow Look Up: Select whether users can look up the definitions of words with the context menu or the Spotlight search menu. The default is OFF, which prevents users from using Look Up on their Macs.
- Allow use of iCloud password for local accounts: Select whether users can use their Apple ID and iCloud password to sign on to their Macs. Enabling this policy means that users use only one ID and password for all login screens on their Macs. The default is On, which allows users to use their Apple ID and iCloud password to access their Macs.
-
Allow iCloud documents & data: Select whether to allow users to access documents and data stored on iCloud on their Macs. The default is Off, which prevents users from using iCloud documents and data on their Macs.
- Allow iCloud Desktop and Documents: (macOS 10.12.4 and later) The default is selected.
- Allow iCloud Keychain Sync: Allow iCloud Keychain sync (macOS 10.12 and later). The default is On.
- Allow iCloud Mail: Allow users to use iCloud Mail (macOS 10.12 and later). The default is On.
- Allow iCloud Contacts: Allow users to use iCloud Contacts (macOS 10.12 and later). The default is On.
- Allow iCloud Calendars: Allow users to use iCloud Calendars (macOS 10.12 and later). The default is On.
- Allow iCloud Reminders: Allow users to use iCloud Reminders (macOS 10.12 and later). The default is On.
- Allow iCloud Bookmarks: Allow users to sync with iCloud Bookmarks (macOS 10.12 and later). The default is On.
- Allow iCloud Notes: Allow users to use Cloud Notes (macOS 10.12 and later). The default is On.
- Allow iCloud Photos: If you change this setting to Off, any photos not fully downloaded from the iCloud Photo Library are removed from local device storage (macOS 10.12 and later). The default is On.
- Allow Auto Unlock: For information about this option and Apple Watch, see https://www.imore.com/auto-unlock (macOS 10.12 and later). The default is On.
- Allow Touch ID To Unlock Mac: (macOS 10.12.4 and later). The default is On.
- Force delayed software updates: If On, this setting delays user visibility of Software Updates. Users don’t see a software update until the specified number of days after the software update release date. Default is Off. Available only for supervised devices running macOS 10.13.4 and later.
- Enforced software update delay (days): Specifies how many days to delay a software update on the device. The maximum is 90 days. Default is 30. Available only for supervised devices running macOS 10.13.4 and later.
- Password AutoFill: Optional. If disabled, users can’t use the AutoFill Passwords or Automatic Strong Passwords features. Default is On. Available from macOS 10.14.
- Password proximity requests: Optional. If disabled, users’ devices don’t request passwords from nearby devices. Default is On. Available from macOS 10.14.
- Password Sharing: Optional. If disabled, users can’t share their passwords using the AirDrop Passwords feature. Default is On. Available from macOS 10.14.
- Image Playground: If Off, prohibits the use of image generation. Default is On. Available only for supervised devices running macOS 15 and later.
- iPhone Mirroring: If Off, prohibits the use of iPhone Mirroring. When used on macOS, this prevents the Mac from mirroring any iPhone. Default is On. Available only for supervised devices running macOS 15 and later.
- Writing Tools: If Off, disables Apple Intelligence writing tools. Default is On. Available only for supervised devices running macOS 15 and later.
- Allow Media Sharing Modification: If Off, prevents modification of Media Sharing settings. Default is On. Available for macOS 15.1 and later.
- Force Bypass Screen Capture Alert: If On, bypasses the presentation of a screen capture alert. Default is Off. Available for macOS 15.1 and later.
- Mail Summary: If Off, disables the ability to create summaries of email messages manually. This does not affect automatic summary generation. Default is On. Available for macOS 15.1 or later.
Android settings
- Camera: Allow users to use the camera on their devices. If Off, the camera is disabled. Defaults to On.
Android Enterprise settings
When a new or factory reset Android device enrolls in work profile mode, devices running Android 9.0-10.x enroll as fully managed devices with a work profile. Devices running Android 11+ enroll as work profile on corporate-owned devices. The restriction policy can apply to either the work profile on the device or the managed device.
On devices enrolled in the work profile on corporate-owned devices mode, the following restrictions are only available for the work profile:
- Allow backup service
- Enable system apps
- Keep the keyguard from locking the device
- Allow use of the status bar
- Keep the device screen on
- Allow user control of application settings
- Allow user to configure user credentials
- Allow VPN configuration
- Allow USB mass storage
- Allow factory reset
- Allow app uninstall
- Access email app from work and personal profiles
- Allow non-Google Play apps
- Allow cross profile copy and paste
- Enable app verification
- Allow account management
- Allow printing
- Allow NFC
- Allow adding users
By default, the USB Debugging and Unknown Sources settings are disabled on a device when it is enrolled in Android Enterprise in work profile mode.
For devices running Android 9.0-10.x and Samsung Knox 3.0 and later, configure the settings for Samsung Knox and Samsung SAFE on the Android Enterprise page. For devices running earlier versions of Android or Samsung Knox, use the Samsung Knox and Samsung SAFE pages.
Samsung restrictions don’t apply to devices enrolled in the work profile on corporate-owned devices mode. Use the Knox Service Plugin (KSP) to apply Samsung restrictions to these devices. For more information, see the Samsung documentation.
We recommend that you use Samsung Knox 3.4 or higher for the latest Samsung Knox management features.
-
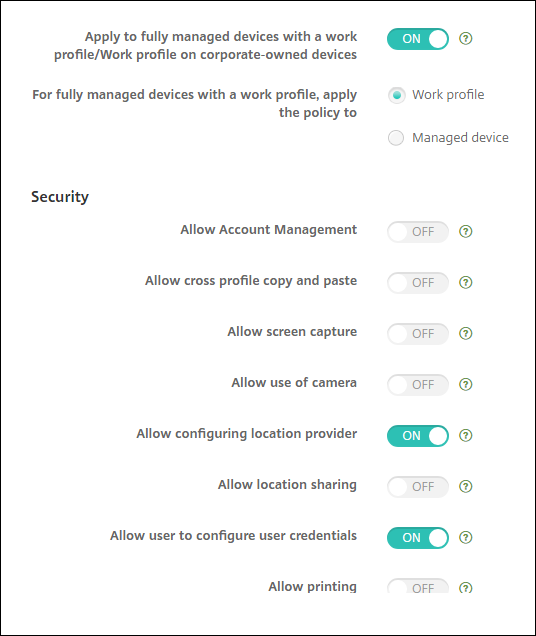
Apply to fully managed devices with a work profile/Work profile on corporate-owned devices: Allows restrictions policy settings to be configured for fully managed devices with work profiles. When this setting is On, select one of these settings:
- Work profile: The restrictions settings you configure apply only to the work profile on the device.
- Manage device: The restrictions settings you configure apply only to the device.
When this setting is Off, the credentials settings you configure apply to the device, except for settings that explicitly apply to the work profile. Default is Off.
When Apply to fully managed devices with a work profile/Work profile on corporate-owned devices is off, configure these settings:
-
Security
- Allow account management: Allows an account to be added in the work profile and managed devices. Default is Off.
- Allow cross profile copy and paste: If On, users can copy and paste between apps in the Android Enterprise profile and apps in the personal area. Default is Off.
- Allow screen capture: Allows users to record or take a screen capture of the device screen. Default is Off.
- Allow use of camera: Allows users to take pictures and make videos with the device camera. Default is Off.
- Allow VPN configuration: Allows users to create VPN configurations. For work profile devices running Android 6 and later and for fully managed devices. Default is On.
- Allow backup service: Allows users to back up application and system data on their devices. Default is On.
- Allow NFC: Allow users to send webpages, photos, videos, or other content from their devices to another device using Near Field Communication (NFC). For MDM 4.0 and later. Default is On.
- Allow configuring location provider: Allows users to turn on GPS on their devices. For Android API 28 and later. Default is On.
-
Allow location sharing: For managed profiles, the device owner can override this setting. Default is Off.
Tip:
You can create Location device policies in XenMobile to enforce geographic boundaries. See Location device policy.
- Allow user to configure user credentials: Specify whether users can configure credentials in the managed keystore. Default is On.
- Allow printing: If On, the setting allows users to print to any printer accessible from the user device. The default is Off. Available for: Android 9 and later.
- Allow USB debugging: Default is Off.
-
Apps
-
Enable system apps: Allows users to run pre-installed device apps. Default is Off. To enable specific apps, click Add in the System apps list table.
-
System apps list: A list of the system apps you want to enable on the device. Set Enable system apps to On and add the app package name. To look up the package name for a system app, you can use the Android Debug Bridge (
adb) to call the Android package manager (pm) command. For example,adb shell "pm list packages -f name", where “name” is part of the package name. For more information, see https://developer.android.com/studio/command-line/adb. For Android Enterprise devices, you can restrict app permissions using the Android Enterprise app permissions policy.
-
System apps list: A list of the system apps you want to enable on the device. Set Enable system apps to On and add the app package name. To look up the package name for a system app, you can use the Android Debug Bridge (
-
Disable applications: Blocks a specified list of apps from running on devices. Default is Off. To disable an installed app, change the setting to On and then click Add in the Application list table.
- Application list: A list of the apps you want to block. Set Disable applications to On and add the app. Type the app package name. Changing and deploying an app list overwrites the prior app list. For example: If you disable com.example1 and com.example2, and then later change the list to com.example1 and com.example3, XenMobile enables com.example.2.
- Enable app verification: Enables the OS to scan apps to detect malicious behavior. Default is On.
- Enable Google apps: Allows users to download apps from Google Mobile Services onto the device. Default is On.
- Allow non-Google Play apps: Allows the installation of apps from stores other than Google Play. Default is Off.
- Allow user control of application settings: Allows users to uninstall apps, disable apps, clear cache and data, force stop any app, and clear defaults. Users do these actions from the Settings app. Default is Off.
-
Allow app uninstall: Allows users to uninstall apps from within the Managed Google Play Store. Default is Off. To show this setting, enable the server property
afw.restriction.policy.v2. For more information about server properties, see Server properties. - Access email app from work and personal profiles: Allows users to access and use the work profile email app from your personal profile when the setting is On. Default is Off.
-
Enable system apps: Allows users to run pre-installed device apps. Default is Off. To enable specific apps, click Add in the System apps list table.
-
BYOD work profile
-
Allow work profile app widgets on home screen: If this setting is On, users can place work profile app widgets on the device home screen. If this setting is Off, users can’t place work profile app widgets on the device home screen. Default is Off.
- Apps with allowed widgets: A list of the apps you want to allow on the home screen. Set Allow work profile app widgets on home screen to On and add the app. Click Add and select an app whose widgets you want to allow on the home screen from the list. Click Save. Repeat that process to allow more app widgets.
- Allow work profile contacts in device contacts: Shows contacts from the managed Android Enterprise profile in the parent profile, for incoming calls (Android 7.0 and later). Default is Off.
-
Allow work profile app widgets on home screen: If this setting is On, users can place work profile app widgets on the device home screen. If this setting is Off, users can’t place work profile app widgets on the device home screen. Default is Off.
-
Fully managed device only
- Allow adding users: Allows users to add new users on a device. Default is On.
- Allow data roaming: Allows users to use cellular data while roaming. The default is Off, which disables roaming on users’ devices. Default is Off.
- Allow SMS: Allows users to send and receive SMS messages. Default is Off.
- Allow use of the status bar: If On, this setting enables the status bar on managed devices and dedicated devices (also known as COSU devices). This setting disables notifications, quick settings, and other screen overlays that allow escape from full-screen mode. Users can go to system settings and see notifications. For Android 6.0 and later. Default is Off.
-
Allow Bluetooth: Allows users to use Bluetooth. Default is On.
-
Allow Bluetooth sharing: If unselected, users can’t establish outgoing Bluetooth sharing on their device. The default is selected. To show this setting, enable the server property
afw.restriction.policy.v2. For more information about server properties, see Server properties.
-
Allow Bluetooth sharing: If unselected, users can’t establish outgoing Bluetooth sharing on their device. The default is selected. To show this setting, enable the server property
- Allow configuring date and time: Allows users to change the date and time on their devices. Default is On.
- Allow factory reset: Allows users to do a factory reset on their devices. Default is On.
- Keep the device screen on: If this setting is set to On, the device screen remains on when the device is plugged in. Default is Off.
- Allow USB mass storage: Allows transfer of large data files between users’ devices and a computer over a USB connection. Default is On.
- Allow microphone: Allows users to use the microphone on their devices. Default is On.
- Allow tethering: Allows users to configure portable hotspots and tether data. Default is Off.
- Keep the keyguard from locking the device: If On, this setting disables the keyguard on the lock screen on managed devices and dedicated devices (also known as COSU devices). Default is Off.
- Allow Wi-Fi changes: If On, users can turn Wi-Fi on or off and connect to Wi-Fi networks. Default is On.
- Allow file transfer: Allows file transfers over USB. Default is Off.
-
Samsung
- Enable TIMA Keystore: The TIMA Keystore provides TrustZone-based secure key storage for the symmetric keys. RSA key pairs and certificates are routed to the default key store provider for storage. Default is Off.
- Allow share list: Allows users to share content between apps in the Share Via list. Default is On.
- Enable audit log: Enables creation of event audit logs for forensic analysis of a device. Default is Off.
-
Samsung: Fully managed device only
- Enable ODE Trusted Boot verification: Use ODE trusted boot verification to establish a chain of trust from the bootloader to the system image. Default is On.
- Allow emergency calls only: Allows users to enable Emergency Call Only mode on their devices. Default is Off.
- Allow firmware recovery: Allows users to recover the firmware on their devices. Default is On.
- Allow fast encryption: Allows encryption of only used memory space. This encryption contrasts full disk encryption, which encrypts all data. That data includes settings, application data, downloaded files and applications, media, and other files. Default is On.
- Enable Common Criteria mode: Places a device into Common Criteria Mode. The Common Criteria configuration enforces stringent security processes. Default is On.
- Enable reboot banner: Displays a DoD approved system use notification message or banner when users’ devices are restarted. Default is Off.
- Allow settings changes: Allows users to change settings on their fully managed devices. Default is On.
- Enable background data usage: Allows apps to sync data in the background. for fully managed devices. Default is On.
-
Allow clipboard: Allow users to copy data to the clipboard on their devices.
- Allow clipboard share: Allow users to share clipboard content between their devices and a computer (MDM 4.0 and later).
- Allow home key: Allows users to use the Home key on their fully managed devices. Default is On.
- Allow mock location: Allows users to fake their GPS location. For fully managed devices. Default is Off.
- NFC: Allows users to use NFC on their fully managed devices (MDM 3.0 and later). Default is On.
- Allow power off: Allows users to power off their fully managed devices (MDM 3.0 and later). Default is On.
- Allow Wi-Fi direct: Allows users to connect directly to another device through their Wi-Fi connection. Default is On. If On, you must enable the Allow Wi-Fi changes setting.
- Allow SD card: Allows users to use an SD card, if available, with their devices. Default is On.
- Allow USB host storage: Allows users’ devices to act as the USB host when a USB device connects to their devices. Users’ devices then supply power to the USB device. Default is On.
- Allow voice dialer: Allows users to use the voice dialer on their devices (MDM 4.0 and later). Default is On.
- Allow S beam: Allows users to share content with others using NFC and Wi-Fi Direct (MDM 4.0 and later). Default is On.
- Allow S voice: Allows users to use the intelligent personal assistant and knowledge navigator on their devices (MDM 4.0 and later). Default is On.
- Allow USB tethering: Allows users to share a mobile data connection with another device using their USB connection. The default is Off. If On the Allow tethering setting must be On as well.
-
Allow Bluetooth tethering: Allows users to share a mobile data connection with another device using their Bluetooth connection. The default is Off. If On the Allow tethering setting must be On as well.
-
Allow Bluetooth sharing: If unselected, users can’t establish outgoing Bluetooth sharing on their device. The default is selected. To show this setting, enable the server property
afw.restriction.policy.v2. For more information about server properties, see Server properties.
-
Allow Bluetooth sharing: If unselected, users can’t establish outgoing Bluetooth sharing on their device. The default is selected. To show this setting, enable the server property
- Allow Wi-Fi tethering: Allows users to share a mobile data connection with another device using their Wi-Fi connection. The default is Off. If On the Allow tethering setting must be On as well.
- Allow incoming MMS: Allows users to receive MMS messages. Default is Off. If On, you must turn on the Allow SMS setting.
- Allow outgoing MMS: Allows users to send MMS messages. Default is Off. If On, you must turn on the Allow SMS setting.
- Allow incoming SMS: Allows users to receive SMS messages. Default is Off. If On, you must turn on the Allow SMS setting.
- Allow outgoing SMS: Allows users to send SMS messages. Default is Off. If On, you must turn on the Allow SMS setting.
- Configure mobile networks: Allows users to use their cellular data connection. Default is Off.
- Limit by day (MB): Enter the number of MB of mobile data users can use each day. The default is 0, which disables this feature (MDM 4.0 and later).
- Limit by week (MB): Enter the number of MB of mobile data users can use each week. The default is 0, which disables this feature (MDM 4.0 and later).
- Limit by month (MB): Enter the number of MB of mobile data users can use each month. The default is 0, which disables this feature (MDM 4.0 and later).
- Allow only secure VPN connections: Allows users to only use secure connections (MDM 4.0 and later). Default is On.
- Allow audio recording: Allows users to record audio with their devices (MDM 4.0 and later). Default is On. If On you must turn on the Allow microphone setting.
- Allow video recording: Allows users to record video with their devices (MDM 4.0 and later). Default is Off. If On you must turn on the Allow use of camera setting.
- Allow push messages when roaming: Allow users to use cellular data for pushing. Default is Off. If On, you must enable the Allow data roaming setting.
- Allow automatic synchronization when roaming: Allow users to use cellular data for syncing. Default is Off. If On, you must enable the Allow data roaming setting.
- Allow voice calls when roaming: Allow users to use cellular data for voice calls. Default is Off. If On, you must enable the Allow data roaming setting.
-
Samsung: Knox container/Fully managed device
- Enable revocation check: Enables checking for revoked certificates. Default is Off.
-
Samsung: Knox container only
- Move apps to container: Allows users to move apps between the Knox container and the personal area on their devices. Default is On.
- Enforce multi-factor authentication: Users must use a fingerprint and one other authentication method, such as password or PIN, to open their devices. Default is On.
- Enforce authentication for container: Use a different authentication method from the method used to unlock the device to open the KNOX container. Default is On.
- Enable secure keypad: Forces users to use a secure keyboard inside the Knox container. Default is On.
-
Samsung: DeX
-
Enable Samsung DeX: Enables supported Knox-enabled devices to run in Samsung DeX mode. Requires Samsung Knox 3.1 (minimum version). Default is On. For information about Samsung DeX device requirements and setting up Samsung DeX, see the Samsung Developers documentation.
- Allow Ethernet in DeX mode only: Enables use of Ethernet in Samsung DeX mode. Cellular data, Wi-Fi, and tethering (Wi-Fi, Bluetooth, and USB) are restricted in DeX mode. Default is unselected.
- Upload DeX logo image: Select this setting to specify a .png image to use as an icon for Samsung DeX.
- DeX screen timeout (seconds): Specify the amount of idle time, in seconds, after which the DeX screen turns off. To disable the timeout, type 0. The default is 1200 seconds (20 minutes).
-
Add app shortcut in Samsung DeX: Specify an app package name to add a shortcut for the app to DeX. To look up an app package name, go to Google Play and select the app. The URL includes the package name:
https://play.google.com/store/apps/details?id=<package.name><!--NeedCopy-->. - Remove app shortcut in Samsung DeX: Specify an app package name to remove a shortcut from DeX. Go to Google Play to look up app package names.
-
App packages to disable in Samsung DeX: Specify a comma-separated list of the app packages that you want to block from Samsung DeX mode. For example:
"com.android.chrome", "com.google.android.gm"<!--NeedCopy-->.
-
Enable Samsung DeX: Enables supported Knox-enabled devices to run in Samsung DeX mode. Requires Samsung Knox 3.1 (minimum version). Default is On. For information about Samsung DeX device requirements and setting up Samsung DeX, see the Samsung Developers documentation.
When Apply to fully managed devices with a work profile is on and For fully managed devices with a work profile, apply the policy to is set to Work profile, configure these settings:
-
Security
- Allow account management: Allows an account to be added in the work profile and managed devices. Default is Off.
- Allow cross profile copy and paste: If On, users can copy and paste between apps in the Android Enterprise profile and apps in the personal area. Default is Off.
- Allow screen capture: Allows users to record or take a screen capture of the device screen. Default is Off.
- Allow use of camera: Allows users to take pictures and make videos with the device camera. Default is Off.
- Allow configuring location provider: Allows users to turn on GPS on their devices. For Android API 28 and later. Default is On.
-
Allow location sharing: For managed profiles, the device owner can override this setting. Default is Off.
Tip:
You can create Location device policies in XenMobile to enforce geographic boundaries. See Location device policy.
- Allow user to configure user credentials: Specify whether users can configure credentials in the managed keystore. Default is On.
- Allow printing: If On, the setting allows users to print to any printer accessible from the user device. The default is Off. Available for: Android 9 and later.
-
Apps
-
Enable system apps: Allows users to run pre-installed device apps. Default is Off. To enable specific apps, click Add in the System apps list table.
-
System apps list: A list of the system apps you want to enable on the device. Set Enable system apps to On and add the app package name. To look up the package name for a system app, you can use the Android Debug Bridge (
adb) to call the Android package manager (pm) command. For example,adb shell "pm list packages -f name", where “name” is part of the package name. For more information, see https://developer.android.com/studio/command-line/adb. For Android Enterprise devices, you can restrict app permissions using the Android Enterprise app permissions policy.
-
System apps list: A list of the system apps you want to enable on the device. Set Enable system apps to On and add the app package name. To look up the package name for a system app, you can use the Android Debug Bridge (
-
Disable applications: Blocks a specified list of apps from running on devices. Default is Off. To disable an installed app, change the setting to On and then click Add in the Application list table.
- Application list: A list of the apps you want to block. Set Disable applications to On and add the app. Type the app package name. Changing and deploying an app list overwrites the prior app list. For example: If you disable com.example1 and com.example2, and then later change the list to com.example1 and com.example3, XenMobile enables com.example.2.
- Enable app verification: Enables the OS to scan apps to detect malicious behavior. Default is On.
- Enable Google apps: Allows users to download apps from Google Mobile Services onto the device. Default is On.
- Allow non-Google Play apps: Allows the installation of apps from stores other than Google Play. Default is Off.
- Allow user control of application settings: Allows users to uninstall apps, disable apps, clear cache and data, force stop any app, and clear defaults. Users perform these actions from the Settings app. Default is Off.
-
Allow app uninstall: Allows users to uninstall apps from within the Managed Google Play Store. Default is Off. To show this setting, enable the server property
afw.restriction.policy.v2. For more information about server properties, see Server properties. - Access email app from work and personal profiles: Allows users to access and use the work profile email app from your personal profile when the setting is On. Default is Off.
-
Enable system apps: Allows users to run pre-installed device apps. Default is Off. To enable specific apps, click Add in the System apps list table.
-
BYOD work profile
-
Allow work profile app widgets on home screen: If this setting is On, users can place work profile app widgets on the device home screen. If this setting is Off, users can’t place work profile app widgets on the device home screen. Default is Off.
- Apps with allowed widgets: A list of the apps you want to allow on the home screen. Set Allow work profile app widgets on home screen to On and add the app. Click Add and select an app whose widgets you want to allow on the home screen from the list. Click Save. Repeat that process to allow more app widgets.
- Allow work profile contacts in device contacts: Shows contacts from the managed Android Enterprise profile in the parent profile, for incoming calls (Android 7.0 and later). Default is Off.
-
Allow work profile app widgets on home screen: If this setting is On, users can place work profile app widgets on the device home screen. If this setting is Off, users can’t place work profile app widgets on the device home screen. Default is Off.
-
Samsung
- Enable TIMA Keystore: The TIMA Keystore provides TrustZone-based secure key storage for the symmetric keys. RSA key pairs and certificates are routed to the default key store provider for storage. Default is Off.
- Allow share list: Allows users to share content between apps in the Share Via list. Default is On.
- Enable audit log: Enables creation of event audit logs for forensic analysis of a device. Default is Off.
-
Samsung: Knox container/Fully managed device
- Enable revocation check: Enables checking for revoked certificates. Default is Off.
-
Samsung: Knox container only
- Move apps to container: Allows users to move apps between the Knox container and the personal area on their devices. Default is On.
- Enforce multi-factor authentication: Users must use a fingerprint and one other authentication method, such as password or PIN, to open their devices. Default is On.
- Enforce authentication for container: Use a different authentication method from the method used to unlock the device to open the KNOX container. Default is On.
- Enable secure keypad: Forces users to use a secure keyboard inside the Knox container. Default is On.
When Apply to fully managed devices with a work profile is on and For fully managed devices with a work profile, apply the policy to is set to Managed device, configure these settings:
-
Security
- Allow account management: Allows an account to be added in the work profile and managed devices. Default is Off.
- Allow cross profile copy and paste: If On, users can copy and paste between apps in the Android Enterprise profile and apps in the personal area. Default is Off.
- Allow screen capture: Allows users to record or take a screen capture of the device screen. Default is Off.
- Allow use of camera: Allows users to take pictures and make videos with the device camera. Default is Off.
- Allow VPN configuration: Allows users to create VPN configurations. For work profile devices running Android 6 and later and for fully managed devices. Default is On.
- Allow backup service: Allows users to back up application and system data on their devices. Default is On.
- Allow NFC: Allow users to send webpages, photos, videos, or other content from their devices to another device using Near Field Communication (NFC). For MDM 4.0 and later. Default is On.
- Allow configuring location provider: Allows users to turn on GPS on their devices. For Android API 28 and later. Default is On.
-
Allow location sharing: For managed profiles, the device owner can override this setting. Default is Off.
Tip:
You can create Location device policies in XenMobile to enforce geographic boundaries. See Location device policy.
- Allow user to configure user credentials: Specify whether users can configure credentials in the managed keystore. Default is On.
- Allow printing: If On, the setting allows users to print to any printer accessible from the user device. The default is Off. Available for: Android 9 and later.
- Allow USB debugging: Default is Off.
-
Apps
-
Enable system apps: Allows users to run pre-installed device apps. Default is Off. To enable specific apps, click Add in the System apps list table.
-
System apps list: A list of the system apps you want to enable on the device. Set Enable system apps to On and add the app package name. To look up the package name for a system app, you can use the Android Debug Bridge (
adb) to call the Android package manager (pm) command. For example,adb shell "pm list packages -f name", where “name” is part of the package name. For more information, see https://developer.android.com/studio/command-line/adb. For Android Enterprise devices, you can restrict app permissions using the Android Enterprise app permissions policy.
-
System apps list: A list of the system apps you want to enable on the device. Set Enable system apps to On and add the app package name. To look up the package name for a system app, you can use the Android Debug Bridge (
-
Disable applications: Blocks a specified list of apps from running on devices. Default is Off. To disable an installed app, change the setting to On and then click Add in the Application list table.
- Application list: A list of the apps you want to block. Set Disable applications to On and add the app. Type the app package name. Changing and deploying an app list overwrites the prior app list. For example: If you disable com.example1 and com.example2, and then later change the list to com.example1 and com.example3, XenMobile enables com.example.2.
- Enable app verification: Enables the OS to scan apps to detect malicious behavior. Default is On.
- Enable Google apps: Allows users to download apps from Google Mobile Services onto the device. Default is On.
- Allow non-Google Play apps: Allows the installation of apps from stores other than Google Play. Default is Off.
- Allow user control of application settings: Allows users to uninstall apps, disable apps, clear cache and data, force stop any app, and clear defaults. Users do these actions from the Settings app. Default is Off.
-
Allow app uninstall: Allows users to uninstall apps from within the Managed Google Play Store. Default is Off. To show this setting, enable the server property
afw.restriction.policy.v2. For more information about server properties, see Server properties.
-
Enable system apps: Allows users to run pre-installed device apps. Default is Off. To enable specific apps, click Add in the System apps list table.
-
Fully managed device only
- Allow adding users: Allows users to add new users on a device. Default is On.
- Allow data roaming: Allows users to use cellular data while roaming. The default is Off, which disables roaming on users’ devices. Default is Off.
- Allow SMS: Allows users to send and receive SMS messages. Default is Off.
- Allow use of the status bar: If On, this setting enables the status bar on managed devices and dedicated devices (also known as COSU devices). This setting disables notifications, quick settings, and other screen overlays that allow escape from full-screen mode. Users can go to system settings and see notifications. For Android 6.0 and later. Default is Off.
-
Allow Bluetooth: Allows users to use Bluetooth. Default is On.
-
Allow Bluetooth sharing: If unselected, users can’t establish outgoing Bluetooth sharing on their device. The default is selected. To show this setting, enable the server property
afw.restriction.policy.v2. For more information about server properties, see Server properties.
-
Allow Bluetooth sharing: If unselected, users can’t establish outgoing Bluetooth sharing on their device. The default is selected. To show this setting, enable the server property
- Allow configuring date and time: Allows users to change the date and time on their devices. Default is On.
- Allow factory reset: Allows users to do a factory reset on their devices. Default is On.
- Keep the device screen on: If this setting is set to On, the device screen remains on when the device is plugged in. Default is Off.
- Allow USB mass storage: Allows transfer of large data files between users’ devices and a computer over a USB connection. Default is On.
- Allow microphone: Allows users to use the microphone on their devices. Default is On.
- Allow tethering: Allows users to configure portable hotspots and tether data. Default is Off. When this setting is on, these settings are available for Samsung devices:
- Keep the keyguard from locking the device: If On, this setting disables the keyguard on the lock screen on managed devices and dedicated devices (also known as COSU devices). Default is Off.
- Allow Wi-Fi changes: If On, users can turn Wi-Fi on or off and connect to Wi-Fi networks. Default is On.
- Allow file transfer: Allows file transfers over USB. Default is Off.
-
Samsung
- Enable TIMA Keystore: The TIMA Keystore provides TrustZone-based secure key storage for the symmetric keys. RSA key pairs and certificates are routed to the default key store provider for storage. Default is Off.
- Allow share list: Allows users to share content between apps in the Share Via list. Default is On.
- Enable audit log: Enables creation of event audit logs for forensic analysis of a device. Default is Off.
-
Samsung: Fully managed device only
- Enable ODE Trusted Boot verification: Use ODE trusted boot verification to establish a chain of trust from the bootloader to the system image. Default is On.
- Allow emergency calls only: Allows users to enable Emergency Call Only mode on their devices. Default is Off.
- Allow firmware recovery: Allows users to recover the firmware on their devices. Default is On.
- Allow fast encryption: Allows encryption of only used memory space. This encryption contrasts full disk encryption, which encrypts all data. That data includes settings, application data, downloaded files and applications, media, and other files. Default is On.
- Enable Common Criteria mode: Places a device into Common Criteria Mode. The Common Criteria configuration enforces stringent security processes. Default is On.
- Enable reboot banner: Displays a DoD approved system use notification message or banner when users’ devices are restarted. Default is Off.
- Allow settings changes: Allows users to change settings on their fully managed devices. Default is On.
- Enable background data usage: Allows apps to sync data in the background. for fully managed devices. Default is On.
-
Allow clipboard: Allow users to copy data to the clipboard on their devices. Default is On.
- Allow clipboard share: Allow users to share clipboard content between their devices and a computer (MDM 4.0 and later).
- Allow home key: Allows users to use the Home key on their fully managed devices. Default is On.
- Allow mock location: Allows users to fake their GPS location. For fully managed devices. Default is Off.
- NFC: Allows users to use NFC on their fully managed devices (MDM 3.0 and later). Default is On.
- Allow power off: Allows users to power off their fully managed devices (MDM 3.0 and later). Default is On.
- Allow Wi-Fi direct: Allows users to connect directly to another device through their Wi-Fi connection. Default is On. If On, you must enable the Allow Wi-Fi changes setting.
- Allow SD card: Allows users to use an SD card, if available, with their devices. Default is On.
- Allow USB host storage: Allows users’ devices to act as the USB host when a USB device connects to their devices. Users’ devices then supply power to the USB device. Default is On.
- Allow voice dialer: Allows users to use the voice dialer on their devices (MDM 4.0 and later). Default is On.
- Allow S beam: Allows users to share content with others using NFC and Wi-Fi Direct (MDM 4.0 and later). Default is On.
- Allow S voice: Allows users to use the intelligent personal assistant and knowledge navigator on their devices (MDM 4.0 and later). Default is On.
- Allow USB tethering: Allows users to share a mobile data connection with another device using their USB connection. The default is Off. If On the Allow tethering setting must be On as well.
- Allow Bluetooth tethering: Allows users to share a mobile data connection with another device using their Bluetooth connection. The default is Off. If On the Allow tethering setting must be On as well.
- Allow Wi-Fi tethering: Allows users to share a mobile data connection with another device using their Wi-Fi connection. The default is Off. If On the Allow tethering setting must be On as well.
- Allow incoming MMS: Allows users to receive MMS messages. Default is Off. If On, you must turn on the Allow SMS setting.
- Allow outgoing MMS: Allows users to send MMS messages. Default is Off. If On, you must turn on the Allow SMS setting.
- Allow incoming SMS: Allows users to receive SMS messages. Default is Off. If On, you must turn on the Allow SMS setting.
- Allow outgoing SMS: Allows users to send SMS messages. Default is Off. If On, you must turn on the Allow SMS setting.
- Configure mobile networks: Allows users to use their cellular data connection. Default is Off.
- Limit by day (MB): Enter the number of MB of mobile data users can use each day. The default is 0, which disables this feature (MDM 4.0 and later).
- Limit by week (MB): Enter the number of MB of mobile data users can use each week. The default is 0, which disables this feature (MDM 4.0 and later).
- Limit by month (MB): Enter the number of MB of mobile data users can use each month. The default is 0, which disables this feature (MDM 4.0 and later).
- Allow only secure VPN connections: Allows users to only use secure connections (MDM 4.0 and later). Default is On.
- Allow audio recording: Allows users to record audio with their devices (MDM 4.0 and later). Default is On. If On you must turn on the Allow microphone setting.
- Allow video recording: Allows users to record video with their devices (MDM 4.0 and later). Default is Off. If On you must turn on the Allow use of camera setting.
- Allow push messages when roaming: Allow users to use cellular data for pushing. Default is Off. If On, you must enable the Allow data roaming setting.
- Allow automatic synchronization when roaming: Allow users to use cellular data for syncing. Default is Off. If On, you must enable the Allow data roaming setting.
- Allow voice calls when roaming: Allow users to use cellular data for voice calls. Default is Off. If On, you must enable the Allow data roaming setting.
-
Samsung: Knox container/Fully managed device
- Enable revocation check: Enables checking for revoked certificates. Default is Off.
-
Samsung: Knox container only
- Move apps to container: Allows users to move apps between the Knox container and the personal area on their devices. Default is On.
- Enforce multi-factor authentication: Users must use a fingerprint and one other authentication method, such as password or PIN, to open their devices. Default is On.
- Enforce authentication for container: Use a different authentication method from the method used to unlock the device to open the KNOX container. Default is On.
- Enable secure keypad: Forces users to use a secure keyboard inside the Knox container. Default is On.
Windows Desktop/Tablet settings
-
WiFi Settings
- Allow Internet sharing: Allow a device to share its internet connection with other devices by turning it into a Wi-Fi hotspot.
-
Connectivity
- Allow VPN over cellular: Allow the device to connect over VPN to a cellular network.
- Allow VPN over cellular while roaming: Allow the device to connect over VPN when the device roams over cellular networks.
- Allow cellular data roaming: Allow users to use cellular data while roaming.
-
Accounts
- Allow Microsoft account connection: Allow the device to use a Microsoft account for non-email related connection authentication and services.
- Allow non-Microsoft email: Allow user to add non-Microsoft email accounts.
-
System
- Allow storage card: Allow the device to use a storage card.
- Telemetry: Select an option in the drop-down list to allow or restrict the device from sending telemetry information. The default is Allowed. Other options are Not allowed and Allowed, except for secondary data request.
- Allow location services: Allow location services.
- Allow preview of internal builds: Allow users to preview Microsoft internal builds.
-
Camera:
- Allow use of camera: Allow users to use their device camera.
-
Bluetooth:
- Allow discoverable mode: Allow Bluetooth devices to find the local device.
- Local device name: A name for the local device.
-
Experience:
- Allow Cortana: Allow users access to Cortana, the intelligent personal assistant and knowledge navigator.
- Allow device discovery: Allow network discovery of the device.
- Allow manual MDM unenrollment: Allow users to manually unenroll their device from XenMobile MDM.
- Allow sync of device settings: Allow users to sync settings between Windows 10 and Windows 11 devices when roaming.
-
Above Lock:
- Allow toasts: Allow toast notifications on the lock screen.
-
Apps
- Allow appstore auto update: Allow apps from the app store to automatically update.
-
Privacy:
- Allow input personalization: Allows the input personalization service to run, to improve predictive inputs such as pen and touch keyboard, based on what a user types.
-
Settings:
- Allow auto play: Allows users to change Auto Play settings.
- Allow data sense: Allows users to change Data Sense settings.
- Allow date time: Allows users to change date and time settings.
- Allow language: Allows users to change language settings.
- Allow power sleep: Allows users to change power and sleep settings.
- Allow region: Allows users to change region settings.
- Allow sign-in options: Allows users to change sign-in settings.
- Allow workplace: Allows users to change workplace settings.
- Allow your account: Allows users to change account settings.