Support for Enterprise web apps
Web app delivery using the Secure Private Access service enables enterprise specific applications to be delivered remotely as a web-based service. Commonly used web apps include SharePoint, Confluence, OneBug, and so on.
Web apps can be accessed using Citrix Workspace using the Secure Private Access service. The Secure Private Access service coupled with Citrix Workspace provides a unified user experience for the configured Web apps, SaaS apps, configured virtual apps, or any other workspace resources.
SSO and remote access to web apps are available as part of the following service packages:
- Secure Private Access Standard
- Secure Private Access Advanced
System requirements
Connector Appliance - Use the Connector Appliance with the Citrix Secure Private Access service to support VPN-less access to the Enterprise Web apps in the customers’ data center. For details, see Secure Workspace Access with Connector Appliance.
How it works
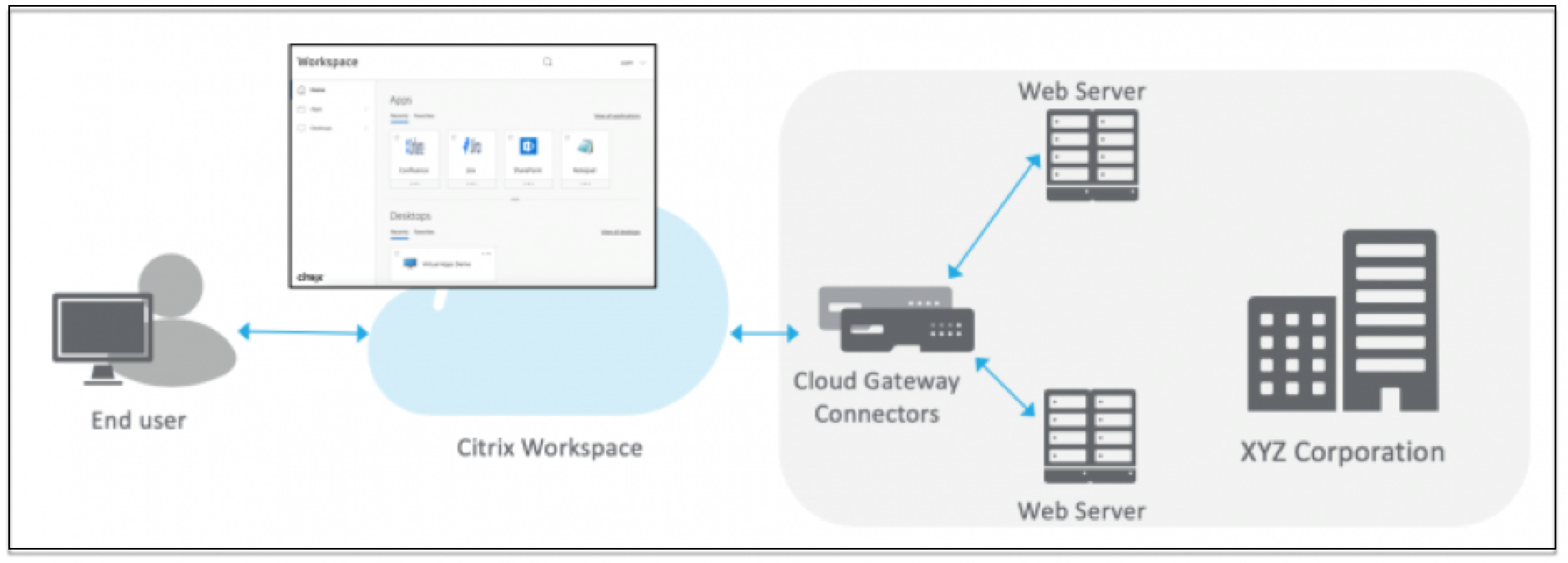
The Citrix Secure Private Access service securely connects to the on-premises data center using the connector, which is deployed on-premises. This connector acts as a bridge between Enterprise web apps deployed on-premises and the Citrix Secure Private Access service. These connectors can be deployed in an HA pair and require only an outbound connection.
A TLS connection between the Connector Appliance and the Citrix Secure Private Access service in the cloud secures the on-premises applications that are enumerated into the cloud service. Web applications are accessed and delivered through Workspace using a VPN-less connection.
The following figure illustrates accessing web applications using Citrix Workspace.
Configure a Web app
Configuring a Web app involves the following high-level steps.
Configure application details
-
On the Secure Private Access tile, click Manage.
-
On the Secure Private Access landing page, click Continue and then click Add an app.
Note:
The Continue button appears only for the first time that you use the wizard. In the subsequent usages, you can directly navigate to the Applications page and then click Add an app.
-
Select the app that you want to add and click Skip.
-
In Where is the application location?, select the location.
-
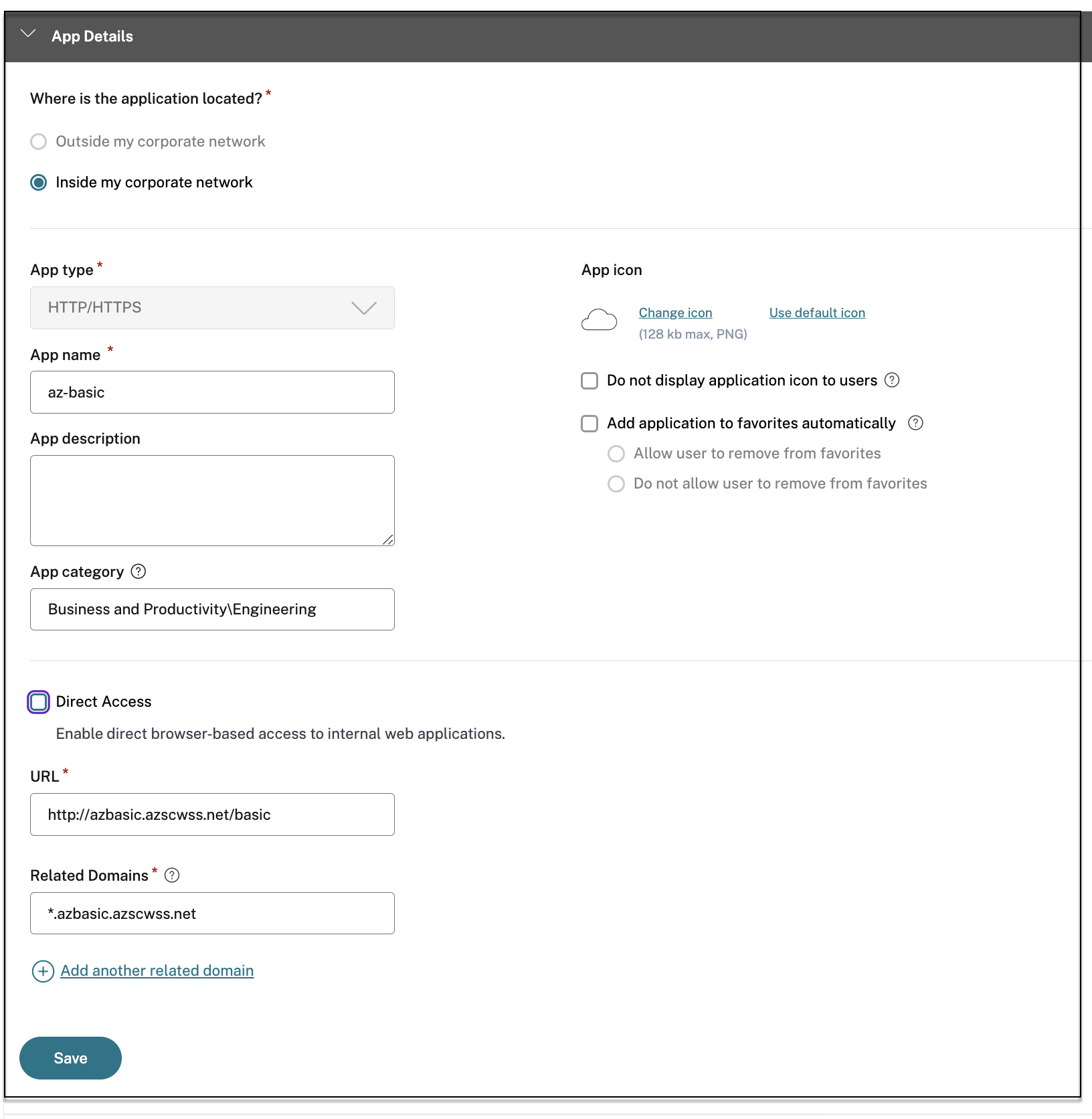
Enter the following details in the App Details section and click Next.
-
App type – Select the app type. You can select from HTTP/ HTTPS or UDP/TCP apps.
-
App name – Name of the application.
-
App description - A brief description of the app. This description that you enter here is displayed to your users in the workspace.
-
App category - Add the category and the subcategory name (if applicable) under which the app that you’re publishing must appear in the Citrix Workspace UI. You can add a new category for each app or use existing categories from the Citrix Workspace UI. Once you specify a category for a web or a SaaS app, the app shows up in the Workspace UI under the specific category.
- The category/subcategories are admin configurable and admins can add a new category for every app.
- The App category field is applicable for HTTP/HTTPS apps and is hidden for TCP/UDP apps.
-
The category/subcategories names must be separated by a backslash. For example, Business And Productivity\Engineering. Also, this field is case sensitive. Admins must ensure that they define the correct category. If there’s a mismatch between the name in Citrix Workspace UI and the category name entered in the App category field, the category gets listed as a new category.
For example, if you enter the Business and Productivity category incorrectly as Business And productivity in the App category field, then a new category named Business and productivity gets listed in the Citrix Workspace UI in addition to the Business And Productivity category.
-
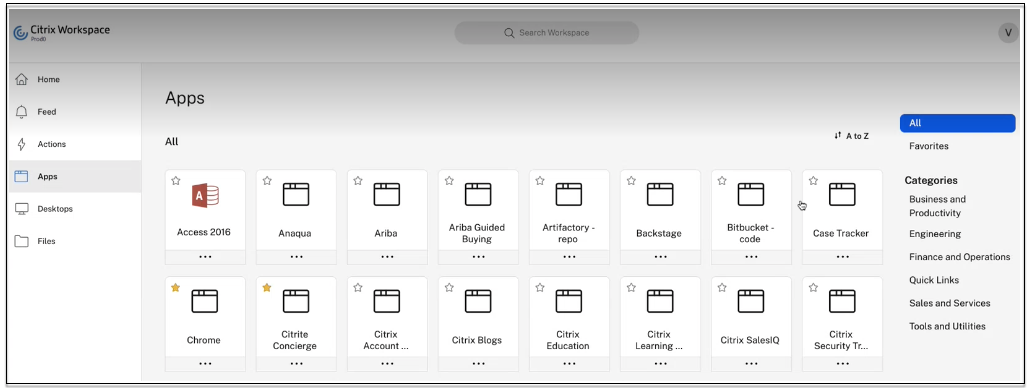
App icon – Click Change icon to change the app icon. The icon file size must be 128x128 pixels. If you do not change the icon, the default icon is displayed.
If you do not want to display the app icon, select Do not display application icon to users.
-
Select Direct Access to enable users access the app directly from a client browser. For details, see Direct access to Enterprise web apps.
-
URL – URL with your customer ID. The URL must contain your customer ID (Citrix Cloud customer ID). To get your customer ID, see Sign up for Citrix Cloud. In case SSO fails or you do not want to use SSO, the user is redirected to this URL.
Customer domain name and Customer domain ID - Customer domain name and ID are used to create the app URL and other subsequent URLs in the SAML SSO page.
For example, if you’re adding a Salesforce app, your domain name is
salesforceformyorgand ID is 123754, then the app URL ishttps://salesforceformyorg.my.salesforce.com/?so=123754.Customer domain name and Customer ID fields are specific to certain apps.
-
Related Domains – The related domain is auto-populated based on the URL that you’ve provided. Related domain helps the service to identify the URL as part of the app and route traffic accordingly. You can add more than one related domain.
-
Click Add application to favorites automatically to add this app as a favorite app in Citrix Workspace app.
- Click Allow user to remove from favorites to allow app subscribers to remove the app from the favorites apps list in Citrix Workspace app. When you select this option, a yellow star icon appears at the top left-hand corner of the app in Citrix Workspace app.
-
Click Do not allow user to remove from favorites to prevent subscribers from removing the app from the favorites apps list in Citrix Workspace app. When you select this option, a star icon with a padlock appears at the top left-hand corner of the app in Citrix Workspace app.
If you remove the apps marked as favorites from the Secure Private Access service console, then these apps must be removed manually from the favorites list in Citrix Workspace. The apps aren’t auto deleted from the Workspace app if removed from the Secure Private Access service console.
-
-
Click Next.
Important:
- To enable zero-trust-based access to the apps, apps are denied access by default. Access to the apps is enabled only if an access policy is associated with the application. For details, see Denied access to the apps, by default.
- If multiple apps are configured with the same FQDN or some variation of the wildcard FQDN, this might result in a conflicting configuration. For details, see Conflicting configuration that might result in app access issues.
Set the preferred sign-on method
-
In the Single Sign On section, select your preferred single sign-on type to be used for your application and click Save. The following single sign-on types are available.
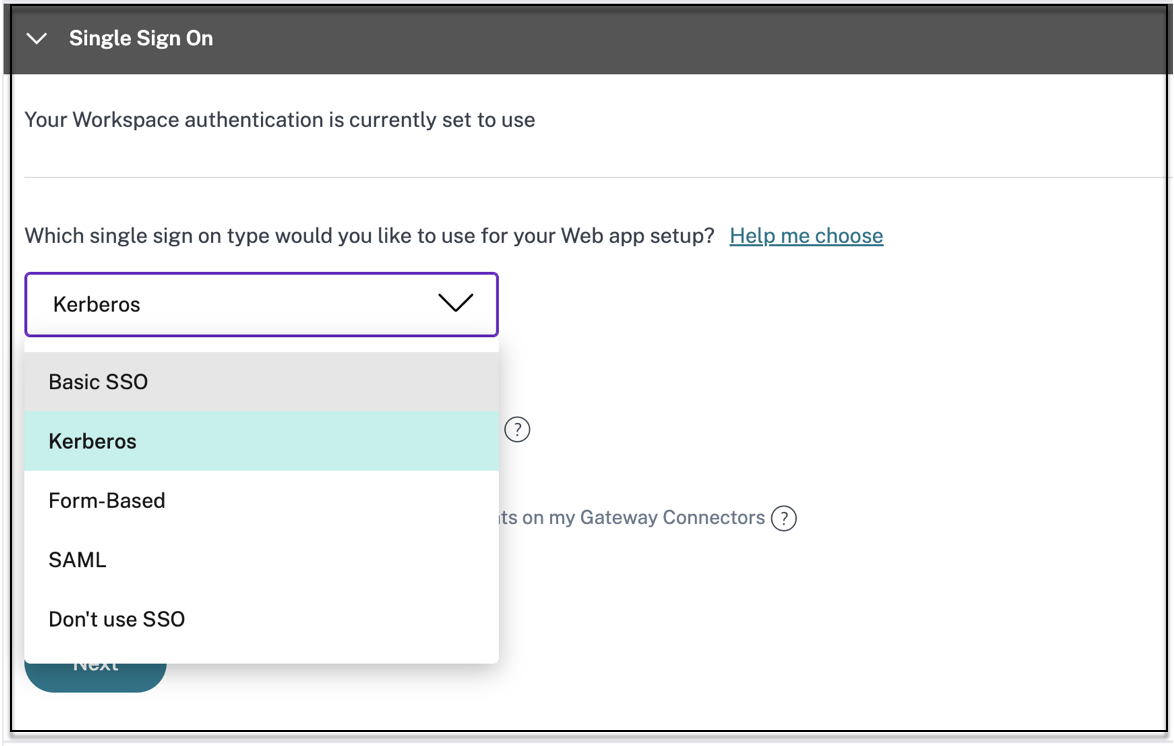
- Basic – If your back-end server presents you with a basic-401 challenge, choose Basic SSO. You do not need to provide any configuration details for the Basic SSO type.
- Kerberos – If your back-end server presents you with the negotiate-401 challenge, choose Kerberos. You do not need to provide any configuration details for the Kerberos SSO type.
- Form-Based – If your back-end server presents you with an HTML form for authentication, choose Form-Based. Enter the configuration details for the Form-Based SSO type.
- SAML - Choose SAML for SAML-based SSO into web applications. Enter the configuration details for SAML SSO type.
- Don’t use SSO – Use the Don’t use SSO option when you do not need to authenticate a user on the back end server. When the Don’t use SSO option is selected, the user is redirected to the URL configured under the App details section.
Form based details: Enter the following form-based configuration details in the Single Sign On section and click Save.
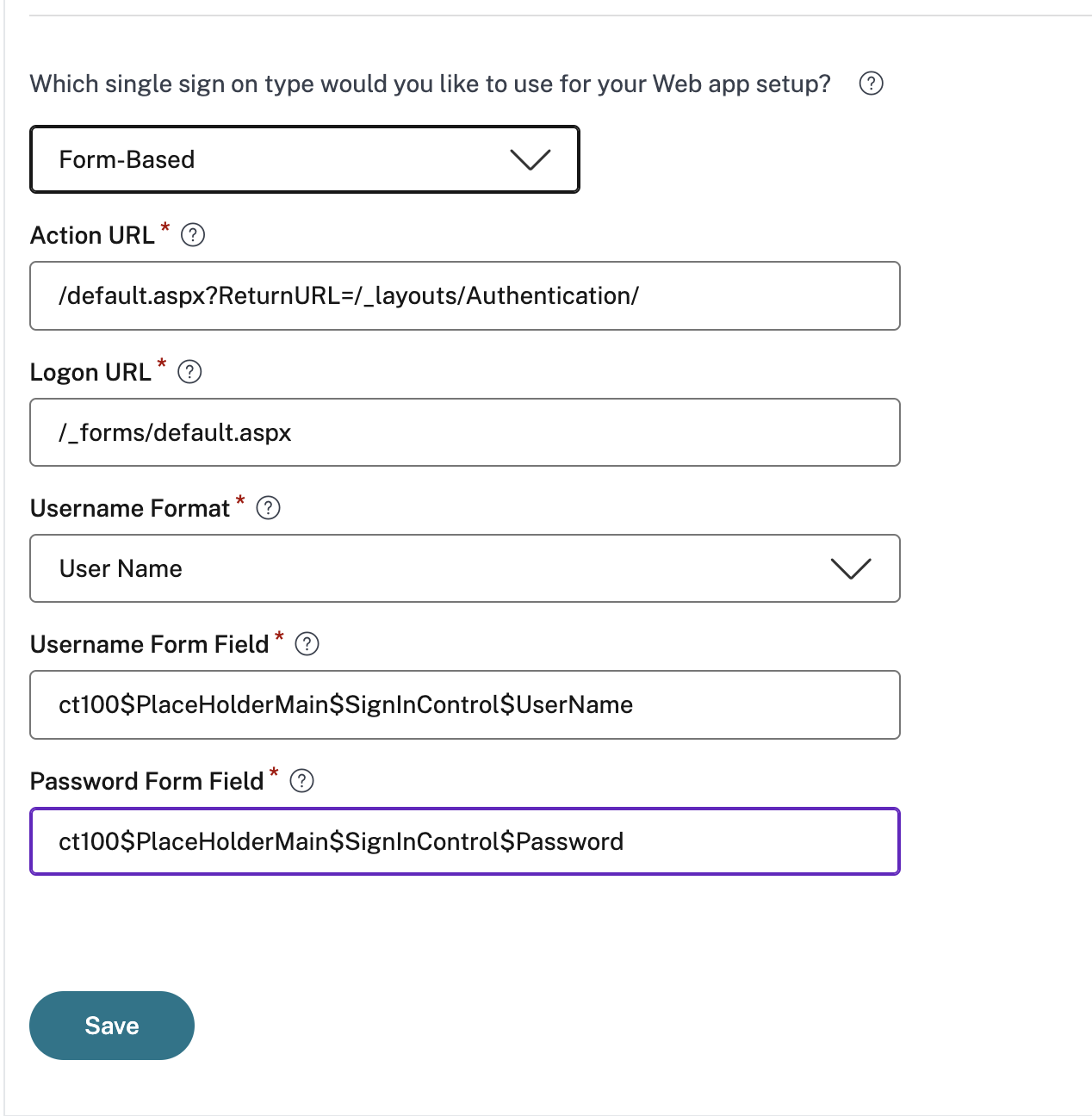
- Action URL - Type the URL to which the completed form is submitted.
- Logon form URL – Type the URL on which the logon form is presented.
- Username Format - Select a format for the user name.
- Username Form Field – Type a user name attribute.
- Password Form Field – Type a password attribute.
SAML: Enter the following details in the Sign sign on section and click Save.
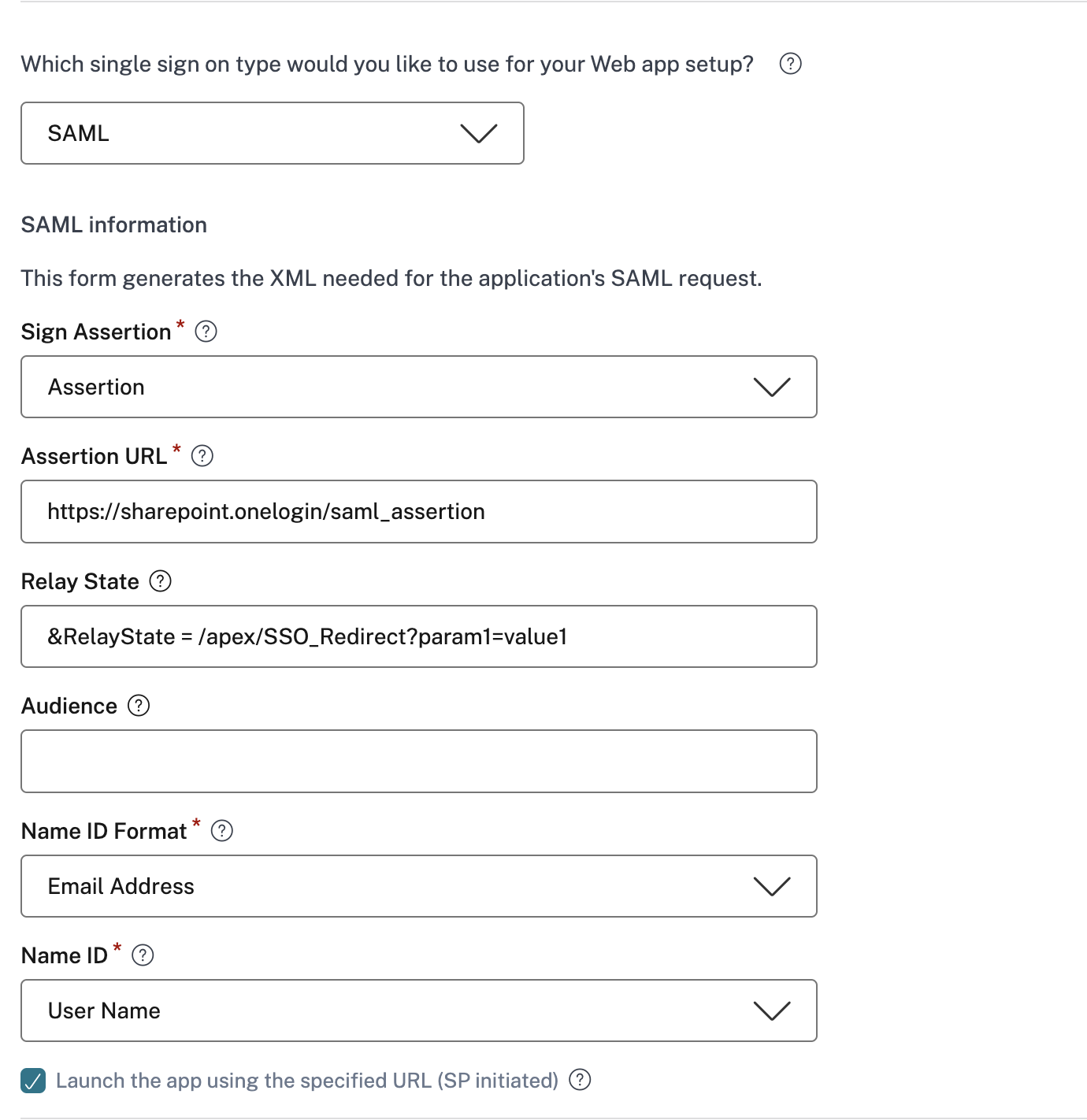
- Sign Assertion - Signing assertion or response ensures message integrity when the response or assertion is delivered to the relying party(SP). You can select Assertion, Response, Both, or None.
- Assertion URL – Assertion URL is provided by the application vendor. The SAML assertion is sent to this URL.
- Relay State – The Relay State parameter is used to identify the specific resource the users access after they’re signed in and directed to the relying party’s federation server. Relay State generates a single URL for the users. Users can click this URL to log on to the target application.
- Audience – Audience is provided by the application vendor. This value confirms that the SAML assertion is generated for the correct application.
-
Name ID Format – Select the supported name identifier format.
- Name ID – Select the supported name ID.
-
In Advanced attributes (optional) add additional information about the user that is sent to the application for access control decisions.
-
Download the metadata file by clicking the link under SAML Metadata. Use the downloaded metadata file to configure SSO on the SaaS apps server.
Note:
- You can copy the SSO login URL under Login URL and use this URL when configuring SSO on the SaaS apps server.
- You can also download the certificate from the Certificate list and use the certificate when configuring SSO on the SaaS apps server.
-
Click Next.
Define application routing
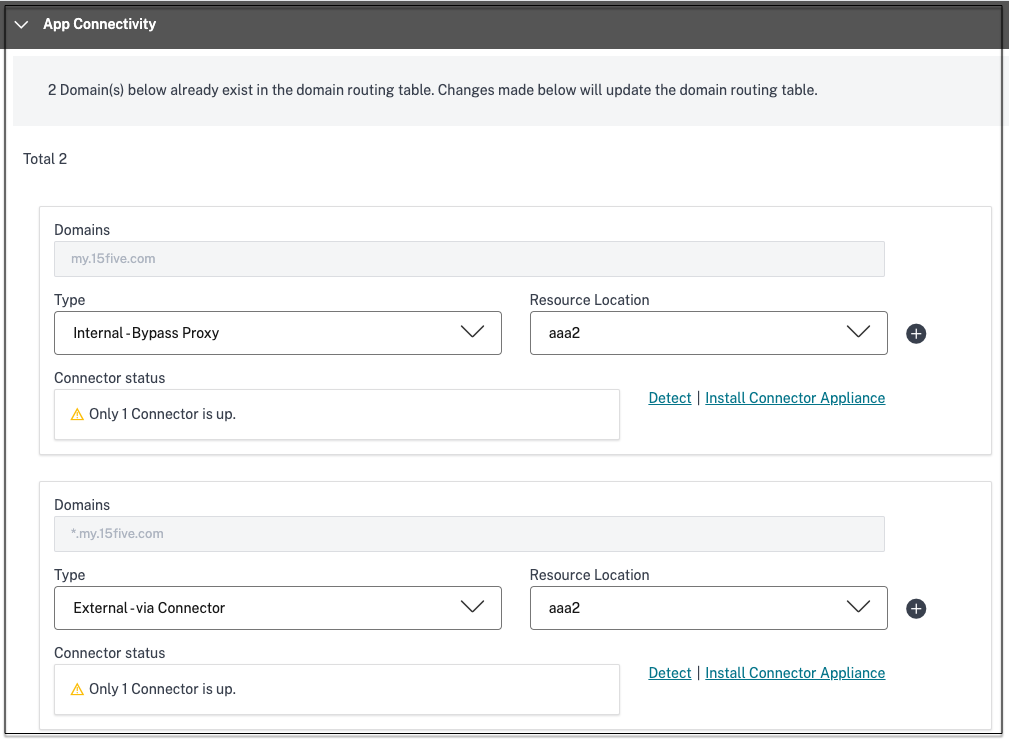
-
In the App Connectivity section, you define routing for the related domains of applications, if the domains must be routed externally or internally through Citrix Connector Appliance.
- Internal – bypass proxy - The domain traffic is routed through Citrix Cloud Connector, bypassing the customer’s web proxy configured on the Connector Appliance.
- Internal via Connector - The apps can be external but the traffic must flow through the Connector Appliance to the outside network.
- External – The traffic flows directly to the internet.
For details, see Route tables to resolve conflicts if the related domains in both SaaS and web apps are the same.
-
Click Finish.
After you click Finish, the app is added to the Applications page. You can edit or delete an app from the Applications page after you’ve configured the application. To do so, click the ellipsis button on an app and select the actions accordingly.
- Edit Application
- Delete
When you publish a Web or a SaaS app from the Secure Private Access service and if that app isn’t hidden, the Citrix Enterprise Browser app shows up automatically in the Citrix Workspace UI. In addition, the Citrix Enterprise Browser is also added as a favorite app, by default. End users can launch the workspace browser without a URL and access internal websites using the workspace browsers.
Important:
- To grant access to the apps for the users, admins are required to create access policies. In access policies, admins add app subscribers and configure security controls. For details, see Create access policies.