Resource filtering using delivery group access policies
You can configure Access Policies for delivery groups based on Workspace URLs. You can control end users’ access to resources based on the Workspace URL that they’re using.
To configure an Access Policy for delivery groups based on Workspace URLs, you need to apply the following SmartAccess filters. The filter values are also sent as SmartAccess tags to the DaaS service. It is applicable in both the scenarios:
- while listing apps and desktops published by DaaS
- while launching an app or desktop
| Filter |
Value |
Description |
| Citrix.Workspace.UsingDomain |
example.cloud.com |
Allows filtering of delivery group resources by Workspace URL. The value is the fully qualified domain name of the cloud.com Workspace URL, even when users access Workspace using a custom domain. |
| Citrix-Via-Workspace |
True |
Indicates that the end user is using Citrix Workspace™, rather than an on-premises StoreFront™ deployment. |
Note:
The SmartAccess tags are sent automatically. If Adaptive Access is enabled then DaaS treats requests from Workspace as being through Citrix Gateway so you must add criteria to the Citrix Gateway Connections rule. If Adaptive Access is disabled then you must add criteria to the Non-Citrix Gateway Connections rule.
This allows filtering of apps and desktops within a delivery group, based on the following criteria:
- the workspace URL that is being used by the end users
- whether users have signed into Workspace or StoreFront
For more information on configuring an access policy for a delivery group, see Manage delivery groups.
Create an access policy rule for multiple URL workflows
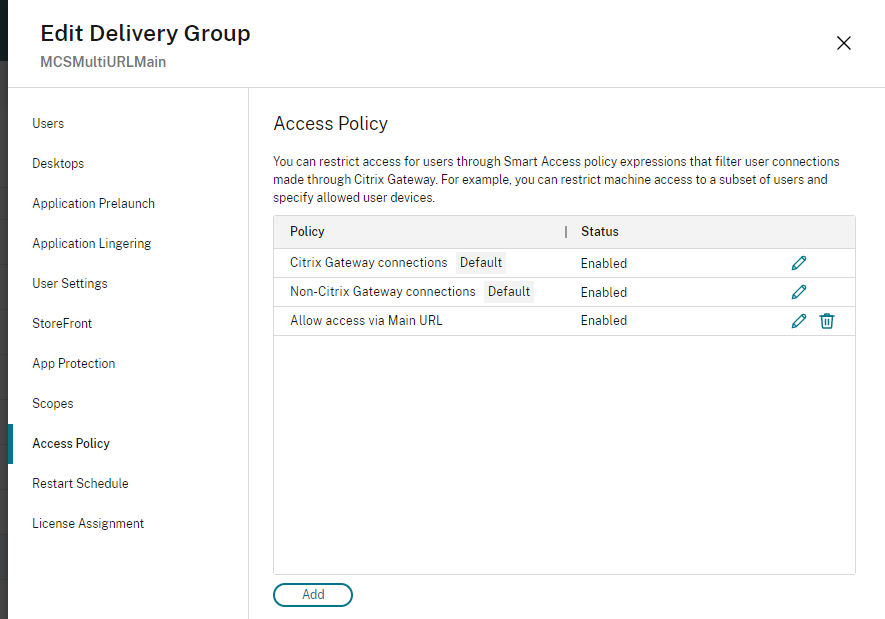
- To create an access policy rule, go to Edit Delivery Group > Access Policy, and click Add. Access policies can only be changed once a delivery group has been created.
- Add a descriptive policy name.
- Select one of the following criteria for your filters:
-
Match any: The access policy allows access if any of the given filter criteria matches the incoming request.
-
Match all: The access policy allows access only if all of the given filter criteria match the incoming request.
- Add values for the
Citrix.Workspace.UsingDomain and Citrix-Via-Workspace filters.
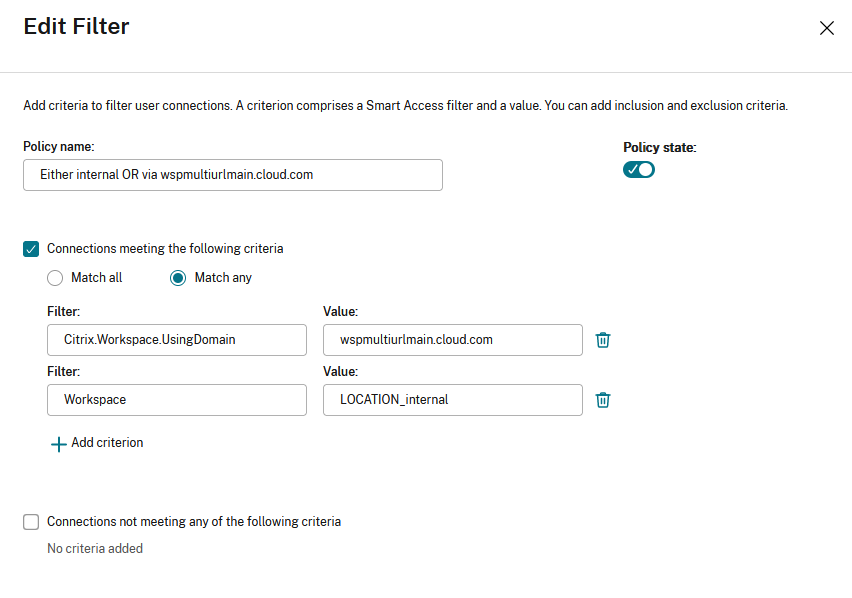
For example, in the following scenario the use of Match any filter means that this rule allows access from either a user using , or a user connecting from an internal network (as per the Network Location configuration). For more information, see [Adaptive access based on user’s network location](/en-us/citrix-daas/manage-deployment/adaptive-access/adaptive-access-based-on-users-network-location.html).

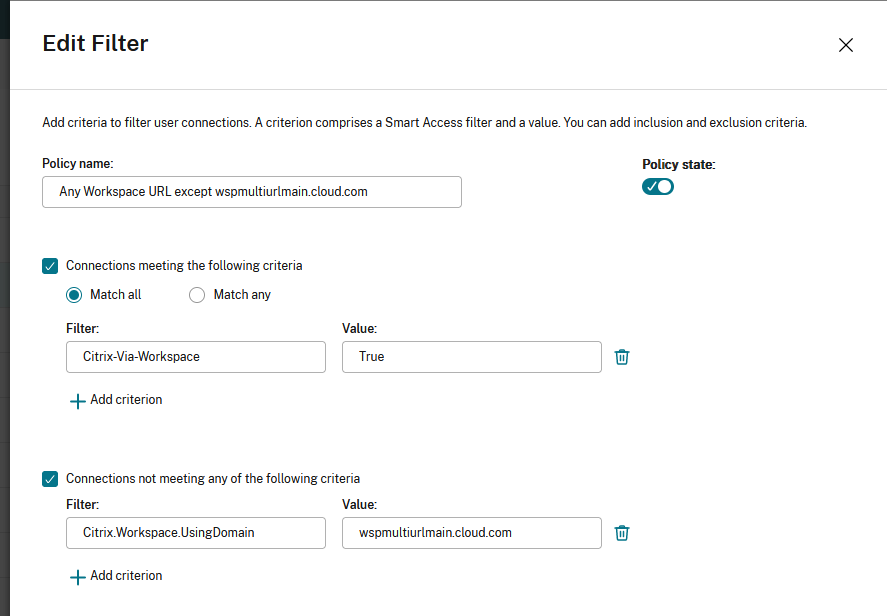
Changing the filter to Match all would mean that the rule only allows access to a user using <wspmultiurlmain.cloud.com> from an internal network.
Once you confirm the changes, the new policy appears on the Access Policy page. For more information, see Manage Delivery Groups
The official version of this content is in English. Some of the Cloud Software Group documentation content is machine translated for your convenience only. Cloud Software Group has no control over machine-translated content, which may contain errors, inaccuracies or unsuitable language. No warranty of any kind, either expressed or implied, is made as to the accuracy, reliability, suitability, or correctness of any translations made from the English original into any other language, or that your Cloud Software Group product or service conforms to any machine translated content, and any warranty provided under the applicable end user license agreement or terms of service, or any other agreement with Cloud Software Group, that the product or service conforms with any documentation shall not apply to the extent that such documentation has been machine translated. Cloud Software Group will not be held responsible for any damage or issues that may arise from using machine-translated content.
DIESER DIENST KANN ÜBERSETZUNGEN ENTHALTEN, DIE VON GOOGLE BEREITGESTELLT WERDEN. GOOGLE LEHNT JEDE AUSDRÜCKLICHE ODER STILLSCHWEIGENDE GEWÄHRLEISTUNG IN BEZUG AUF DIE ÜBERSETZUNGEN AB, EINSCHLIESSLICH JEGLICHER GEWÄHRLEISTUNG DER GENAUIGKEIT, ZUVERLÄSSIGKEIT UND JEGLICHER STILLSCHWEIGENDEN GEWÄHRLEISTUNG DER MARKTGÄNGIGKEIT, DER EIGNUNG FÜR EINEN BESTIMMTEN ZWECK UND DER NICHTVERLETZUNG VON RECHTEN DRITTER.
CE SERVICE PEUT CONTENIR DES TRADUCTIONS FOURNIES PAR GOOGLE. GOOGLE EXCLUT TOUTE GARANTIE RELATIVE AUX TRADUCTIONS, EXPRESSE OU IMPLICITE, Y COMPRIS TOUTE GARANTIE D'EXACTITUDE, DE FIABILITÉ ET TOUTE GARANTIE IMPLICITE DE QUALITÉ MARCHANDE, D'ADÉQUATION À UN USAGE PARTICULIER ET D'ABSENCE DE CONTREFAÇON.
ESTE SERVICIO PUEDE CONTENER TRADUCCIONES CON TECNOLOGÍA DE GOOGLE. GOOGLE RENUNCIA A TODAS LAS GARANTÍAS RELACIONADAS CON LAS TRADUCCIONES, TANTO IMPLÍCITAS COMO EXPLÍCITAS, INCLUIDAS LAS GARANTÍAS DE EXACTITUD, FIABILIDAD Y OTRAS GARANTÍAS IMPLÍCITAS DE COMERCIABILIDAD, IDONEIDAD PARA UN FIN EN PARTICULAR Y AUSENCIA DE INFRACCIÓN DE DERECHOS.
本服务可能包含由 Google 提供技术支持的翻译。Google 对这些翻译内容不做任何明示或暗示的保证,包括对准确性、可靠性的任何保证以及对适销性、特定用途的适用性和非侵权性的任何暗示保证。
このサービスには、Google が提供する翻訳が含まれている可能性があります。Google は翻訳について、明示的か黙示的かを問わず、精度と信頼性に関するあらゆる保証、および商品性、特定目的への適合性、第三者の権利を侵害しないことに関するあらゆる黙示的保証を含め、一切保証しません。
ESTE SERVIÇO PODE CONTER TRADUÇÕES FORNECIDAS PELO GOOGLE. O GOOGLE SE EXIME DE TODAS AS GARANTIAS RELACIONADAS COM AS TRADUÇÕES, EXPRESSAS OU IMPLÍCITAS, INCLUINDO QUALQUER GARANTIA DE PRECISÃO, CONFIABILIDADE E QUALQUER GARANTIA IMPLÍCITA DE COMERCIALIZAÇÃO, ADEQUAÇÃO A UM PROPÓSITO ESPECÍFICO E NÃO INFRAÇÃO.



