Citrix Gateway and XenMobile®
When you configure Citrix Gateway using XenMobile, you establish the authentication mechanism for remote device access to the internal network. This functionality enables apps on a mobile device to access corporate servers in the intranet. XenMobile creates a micro VPN from the apps on the device to Citrix Gateway.
You configure Citrix Gateway for use with XenMobile by exporting a script from XenMobile that you run on Citrix Gateway.
Prerequisites for using the Citrix Gateway configuration script
Citrix ADC requirements:
- Citrix ADC (minimum version 11.0, Build 70.12).
- Citrix ADC IP address is configured and has connectivity to the LDAP server, unless LDAP is load balanced.
- Citrix ADC Subnet (SNIP) IP address is configured, has connectivity to the necessary back end servers, and has public network access over port 8443/TCP.
- DNS can resolve public domains.
- Citrix ADC is licensed with Platform/Universal or Trial licenses. For information, see https://support.citrix.com/article/CTX126049.
- A Citrix Gateway SSL certificate is uploaded and installed on the Citrix ADC. For information see, https://support.citrix.com/article/CTX136023.
XenMobile requirements:
- XenMobile Server (minimum version 10.6).
- LDAP server is configured.
Configure authentication for remote device access to the internal network
-
In the XenMobile console, click the gear icon in the upper-right corner of the console. The Settings page appears.
-
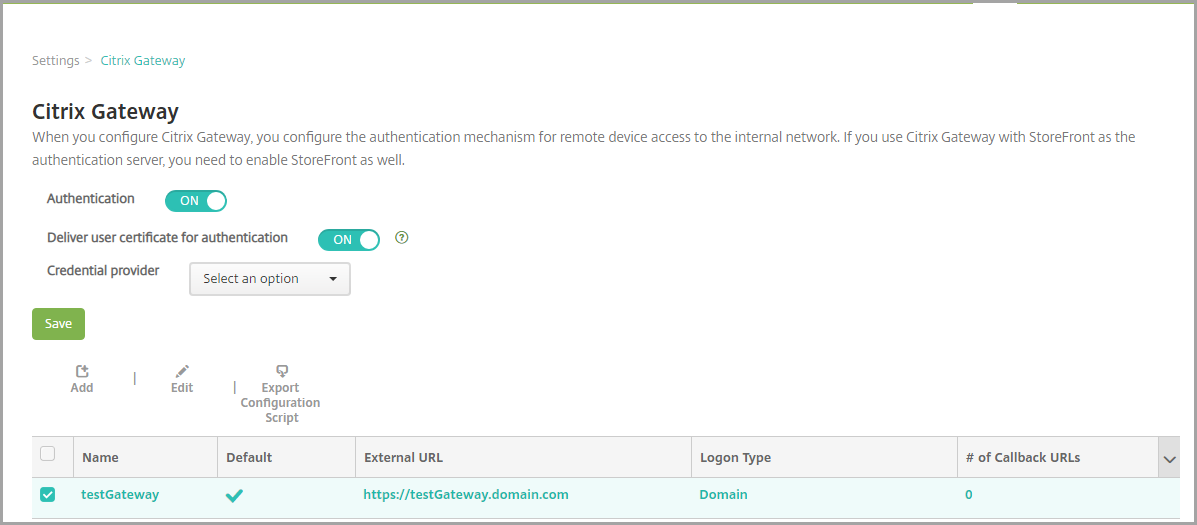
Under Server, click Citrix Gateway. The Citrix Gateway page appears. In the following example, a Citrix Gateway instance exists.
-
Configure these settings:
- Authentication: Select whether to enable authentication. The default is ON.
- Deliver user certificate for authentication: Select whether you want XenMobile to share the authentication certificate with Secure Hub, to enable the Citrix Gateway to handle client certificate authentication. The default is OFF.
- Credential Provider: In the list, click the credential provider to use. For more information, see Credential Providers.
-
Click Save.
Add a Citrix Gateway instance
After you save the authentication settings, you add a Citrix Gateway instance to XenMobile.
-
In the XenMobile console, click the gear icon in the upper-right corner of the console. The Settings page opens.
-
Under Server, click Citrix Gateway. The Citrix Gateway page appears.
-
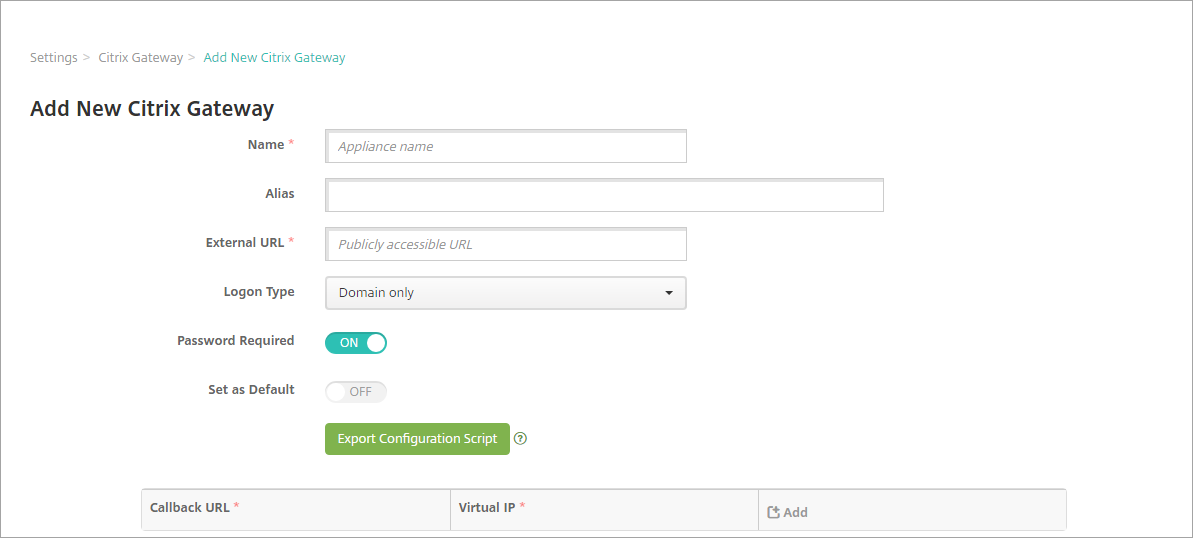
Click Add. The Add New Citrix Gateway page appears.
-
Configure these settings:
- Name: Type a name for the Citrix Gateway instance.
- Alias: Optionally include an alias name for the Citrix Gateway.
-
External URL: Type the publicly accessible URL for Citrix Gateway. For example,
https://receiver.com. - Logon Type: Choose a logon type. Types include Domain only, Security token only, Domain and security token, Certificate, Certificate and domain, and Certificate and security token. The default setting for the Password Required field changes based on the Logon Type you select. The default is Domain only.
If you have multiple domains, use Certificate and domain. For more information about configuring multiple-domain authentication with XenMobile and Citrix Gateway, see Configure authentication for multiple domains.
If you use Certificate and security token, some additional configuration is required on Citrix Gateway to support Secure Hub. For information, see Configuring XenMobile for Certificate and Security Token Authentication.
For more information, see Authentication in the Deployment Handbook.
- Password Required: Select whether you want to require password authentication. The default varies based on the Logon Type chosen.
- Set as Default: Select whether to use this Citrix Gateway as the default. The default is OFF.
- Export Configuration Script: Click the button to export a configuration bundle that you upload to Citrix Gateway to configure it with XenMobile settings. For information, see “Configure an on-premises Citrix Gateway for use with XenMobile Server” after these steps.
- Callback URL and Virtual IP: Save your settings before adding these fields. For information, see Add a callback URL and Citrix Gateway VPN virtual IP in this article.
-
Click Save.
The new Citrix Gateway is added and appears in the table. To edit or delete an instance, click the name in the list.
Configure Citrix Gateway for use with XenMobile Server
To configure an on-premises Citrix Gateway for use with XenMobile, you perform the following general steps, detailed in this article:
-
Download a script and related files from XenMobile Server. See the readme file provided with the script for the latest detailed instructions.
-
Verify that your environment meets the prerequisites.
-
Update the script for your environment.
-
Run the script on Citrix ADC.
-
Test the configuration.
The script configures these Citrix Gateway settings required by XenMobile:
- Citrix Gateway virtual servers needed for MDM and MAM
- Session policies for the Citrix Gateway virtual servers
- XenMobile Server details
- Authentication Policies and Actions for the Citrix Gateway virtual server. The script describes the LDAP configuration settings.
- Traffic actions and policies for the proxy server
- Clientless access profile
- Static local DNS record on Citrix ADC
- Other bindings: Service policy, CA certificate
The script doesn’t handle the following configuration:
- Exchange load balancing
- Citrix Files load balancing
- ICA® Proxy configuration
- SSL Offload
To download, update, and run the script
-
If you’re adding a Citrix Gateway, click Export Configuration Script on the Add New Citrix Gateway page.

Or, if you add a Citrix Gateway instance and click Save before you export the script: Return to Settings > Citrix Gateway, select the Citrix ADC, click Export Configuration Script, and then click Download.

After you click Export Configuration Script, XenMobile creates a .tar.gz script bundle. The script bundle includes:
- Readme file with detailed instructions
- Script that contains the Citrix ADC CLI commands used to configure the required components in Citrix ADC
- Public Root CA certificate and the Intermediate CA certificate of XenMobile Server (these certificates, for SSL offload, are not needed for the current release)
- Script that contains the Citrix ADC CLI commands used to remove the Citrix ADC configuration
-
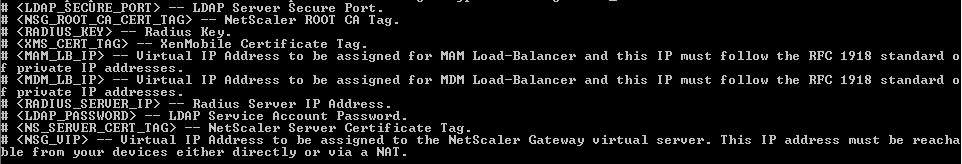
Edit the script (NSGConfigBundle_CREATESCRIPT.txt) to replace all placeholders with details from your environment.
-
Run your edited script in the Citrix ADC bash shell, as described in the readme file included in the script bundle. For example:
/netscaler/nscli -U :<NetScaler Management Username>:<NetScaler Management Password> batch -f "/var/NSGConfigBundle_CREATESCRIPT.txt"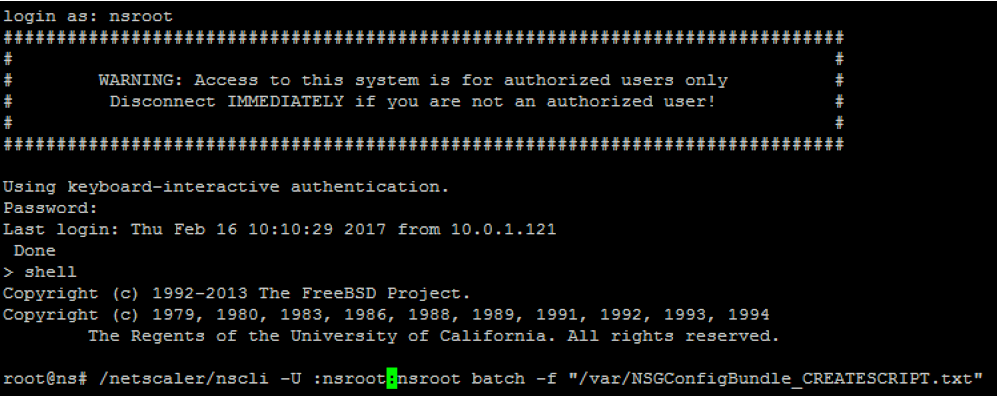
When the script completes, the following lines appear.
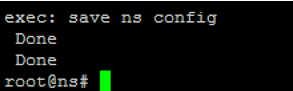
Test the configuration
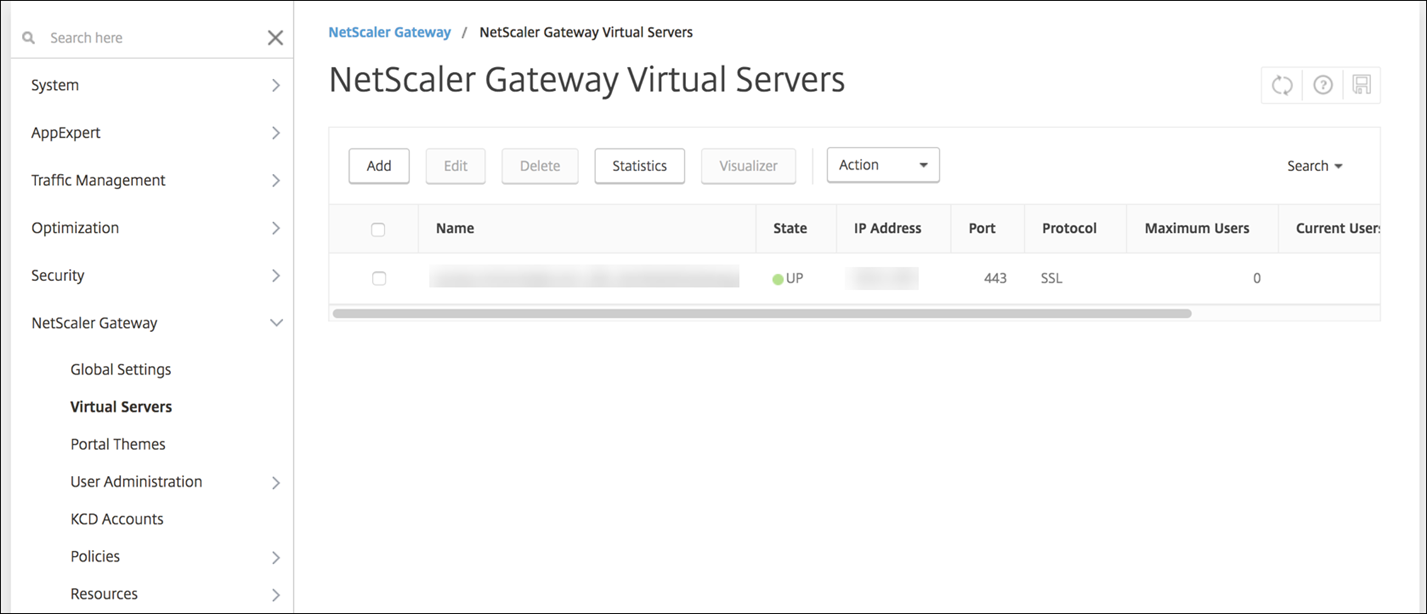
-
Validate that the Citrix Gateway Virtual Server shows a state of UP.
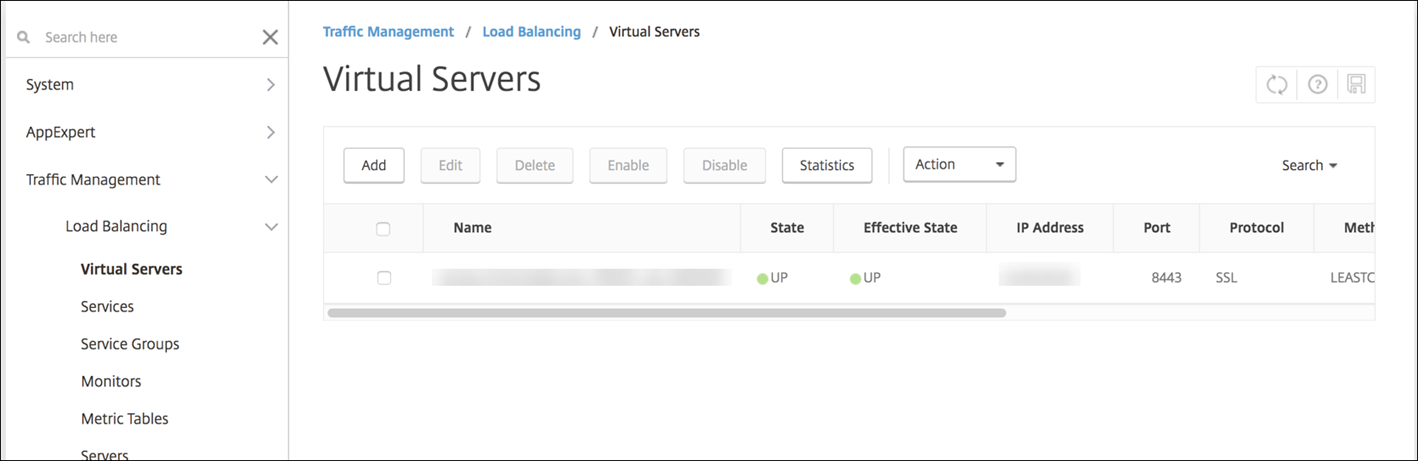
-
Validate that the Proxy Load Balancing Virtual Server shows a state of UP.
-
Open a web browser, connect to the Citrix Gateway URL, and attempt to authenticate. If the authentication fails, this message appears: HTTP Status 404 - Not Found
-
Enroll a device and ensure it gets both MDM and MAM enrollment.
Add a callback URL and Citrix Gateway VPN virtual IP
After adding the Citrix Gateway instance, you can add a callback URL and specify a Citrix Gateway virtual IP address. These settings are optional, but can be configured for extra security, especially when the XenMobile Server is in the DMZ.
-
In Settings > Citrix Gateway, select the Citrix Gateway and then click Edit.
-
In the table, click Add.
-
For Callback URL type the fully qualified domain name (FQDN). The callback URL verifies that a request originated from Citrix Gateway.
Ensure that the callback URL resolves to an IP address that is reachable from the XenMobile Server. The callback URL can be an external Citrix Gateway URL or some other URL.
-
Type the Citrix Gateway Virtual IP address and then click Save.
Configure authentication for multiple domains
If you have multiple XenMobile Server instances, such as for test, development, and production environments, you configure Citrix Gateway for the additional environments manually. (You can use the Citrix ADC for XenMobile wizard only one time.)
Citrix Gateway configuration
To configure Citrix Gateway authentication policies and a session policy for a multi-domain environment:
- In the Citrix Gateway configuration utility, on the Configuration tab, expand Citrix Gateway > Policies > Authentication.
- In the navigation pane, click LDAP.
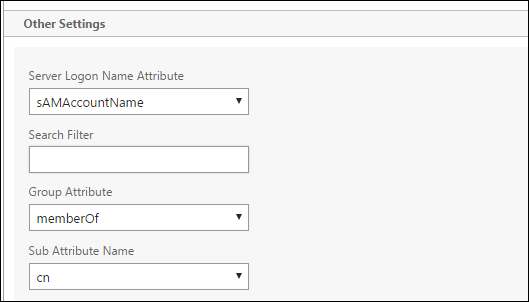
-
Click to edit the LDAP profile. Change the Server Logon Name Attribute to userPrincipalName or the attribute that you want to use for searches. Make a note of the attribute that you specify so you have it when configuring LDAP settings in the XenMobile console.
- Repeat those steps for each LDAP policy. A separate LDAP policy is required for each domain.
- In the session policy bound to the Citrix Gateway virtual server, navigate to Edit session profile > Published Applications. Make sure that Single Sign-On Domain is blank.
XenMobile Server configuration
To configure LDAP for a multi-domain XenMobile environment:
-
In the XenMobile console, go to Settings > LDAP and add or edit a directory.
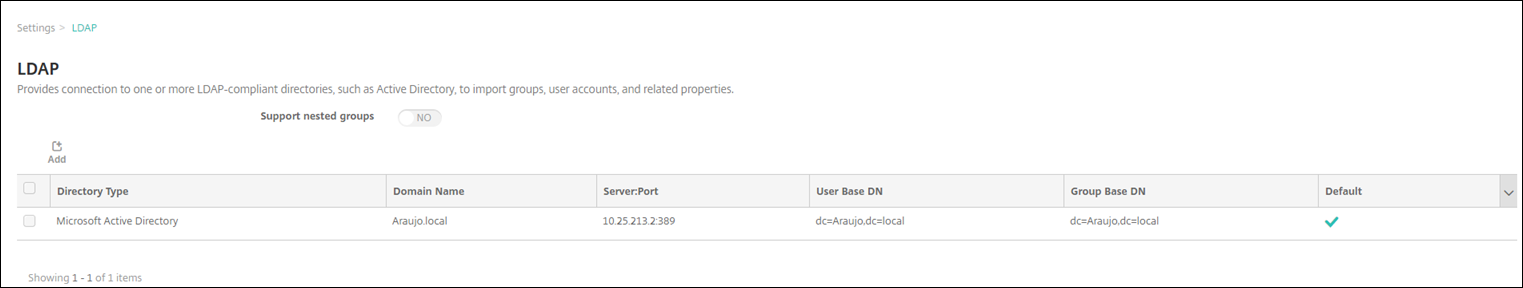
-
Provide the information.
-
In Domain Alias, specify each domain to use for user authentication. Separate the domains with a comma and don’t use spaces between the domains. For example:
domain1.com,domain2.com,domain3.com -
Ensure that the User search by field matches the Server Logon Name Attribute specified in the Citrix Gateway LDAP policy.
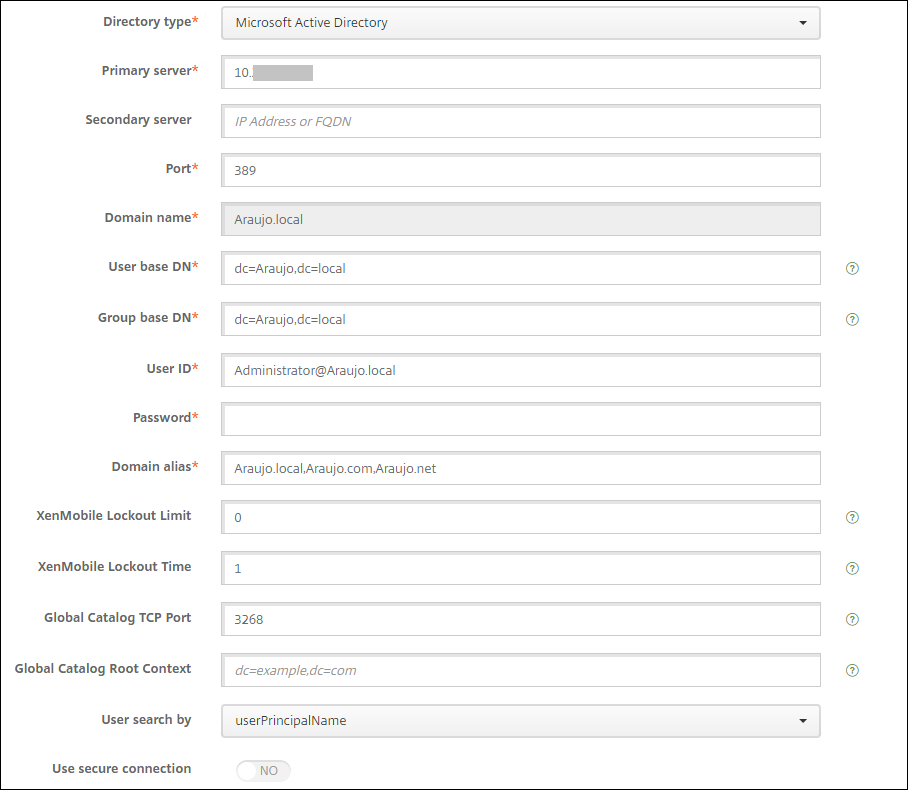
-
Drop inbound connection requests to specific URLs
If the Citrix Gateway in your environment is configured for SSL offload, you might prefer that the gateway drop inbound connection requests for specific URLs.
If you prefer that extra security, configure the two MDM load balancer virtual servers (one for port 443 and one for port 8443) on Citrix Gateway. Use the following information as a template for your settings.
Important:
The following updates are only for a Citrix Gateway configured for SSL offload.
-
Create a pattern set with the name
XMS_DropURLs.add policy patset XMS_DropURLs <!--NeedCopy--> -
Add the following URLs to the new pattern set. Customize this list as required.
bind policy patset XMS_DropURLs /zdm/shp/console -index 6 bind policy patset XMS_DropURLs /zdm/login_xdm_uc.jsp -index 5 bind policy patset XMS_DropURLs /zdm/helper.jsp -index 4 bind policy patset XMS_DropURLs /zdm/log.jsp -index 3 bind policy patset XMS_DropURLs /zdm/login.jsp -index 2 bind policy patset XMS_DropURLs /zdm/console -index 1 <!--NeedCopy--> -
Create a policy to drop all traffic to these URLs, unless the connection request originates from the specified subnet.
add responder policy XMS_DROP_pol “CLIENT.IP.SRC.IN_SUBNET(192.168.0.0/24).NOT && HTTP.REQ.URL.CONTAINS_ANY(”XMS_DropURLs”)” DROP -comment "Allow only subnet 192.168.0.0/24 to access these URLs. All other connections are DROPed" <!--NeedCopy--> -
Bind the new policy to both MDM load balancer virtual servers (ports 443 and 8443).
bind lb vserver _XM_LB_MDM_XenMobileMDM_443 -policyName XMS_DROP_pol -priority 100 -gotoPriorityExpression END -type REQUEST bind lb vserver _XM_LB_MDM_XenMobileMDM_8443 -policyName XMS_DROP_pol -priority 100 -gotoPriorityExpression END -type REQUEST <!--NeedCopy--> -
Block MAM URL access through the browser
Accessing the MAM URL directly through the browser prompts the users to enter their Active Directory credentials. While it acts as a tool for users to validate their credentials, some users might treat it as a security violation. The following section helps you restrict the browser access to the MAM URL (NetScaler® Gateway VIP), using the Responder Policy feature on NetScaler.
Create one of the following Responder Policy and bind it to your NetScaler Gateway Virtual Server:
-
add responder policy Resp_Brow_Pol "HTTP.REQ.HEADER(\"User-Agent\").CONTAINS(\"Mozilla\")&&HTTP.REQ.URL.PATH_AND_QUERY.EQ(\"/vpn/index.html\")" DROP -
add responder policy Resp_Brow_Pol_CR "!HTTP.REQ.HEADER(\"User-Agent\").CONTAINS(\"CitrixReceiver\")&&HTTP.REQ.URL.PATH_AND_QUERY.EQ(\"/vpn/index.html\")" DROP -
add responder policy Resp_Brow_Pol_CR "HTTP.REQ.HEADER(\"User-Agent\").CONTAINS(\"CitrixReceiver\").NOT&&HTTP.REQ.URL.PATH_AND_QUERY.EQ(\"/vpn/index.html\")" DROP
Bind to NetScaler Gateway Virtual Server using
bind vpn vserver _XM_XenMobileGateway -policy Resp_Brow_Pol_CR -priority 100 -gotoPriorityExpression END -type REQUESTNote:
_XM_XenMobileGatewayis an example name of a NetScaler Gateway Virtual Server. -
In this article
- Prerequisites for using the Citrix Gateway configuration script
- Configure authentication for remote device access to the internal network
- Add a Citrix Gateway instance
- Configure Citrix Gateway for use with XenMobile Server
- Add a callback URL and Citrix Gateway VPN virtual IP
- Configure authentication for multiple domains
- Drop inbound connection requests to specific URLs