Logging and troubleshooting
Use this topic to troubleshoot some of the app configuration, authentication and SSO, or app access-related issues. Copy the info code from the ‘Info Code’ column within the Secure Private Access diagnostic logs and then search for that code on this page to find the corresponding troubleshooting steps. The following are some FAQs to help you use this topic better.
FAQs?
What are Secure Private Access diagnostic logs?
Where do I find Secure Private Access logs?
Which widget displays the Secure Private Access diagnostic logs?
What details can I find in the Secure Private Access diagnostic logs?
What events are captured in the Secure Private Access diagnostic logs?
How do I filter the diagnostic logs?
What is an info code? Where do I find them?
What is a transaction ID? How do I use it?
What are all the Secure Private Access PoP locations?
What do I do if I am unable to resolve my failure using the info code and the error lookup table?
Info code lookup table
The following error lookup table provides a comprehensive overview of the various errors that users can possibly run into when using the Secure Private Access service.
| Info code | Description | Resolution |
|---|---|---|
| 0x180006, 0x1800B7 | App launch failed because App FQDN length exceeded | App launch failed because app FQDN length exceeded |
| 0x180022 | App launch failed as Authentication Service is down | App launch failed as authentication service is down |
| 0x180001, 0x18001A, 0x18001B, 0x18008A | Single sign-on errors, Connection establishment failure between Citrix Cloud and on-premises connectors, SAML SSO failure, Invalid app FQDN
|
App access is denied
|
| 0x1800A9, 0x1800AA, 0x1800AB, 0x1800AC | ||
| 0x1800AD, 0x1800AE, 0x1800AF, 0x1800B0 | ||
| 0x1800B1, 0x1800B2, 0x1800B3, 0x180048 | ||
| 0x1800EF | Problem connecting to Connector Appliance | Problem connecting to Connector Appliance |
| 0x18009D | DNS lookup/Connection failed | Secure Browser Service - DNS lookup/connection errors |
| 0x1800A0, 0x1800A2, 0x1800A3, 0x1800A5 | Web app launch failed as unable to connect to back end web app
|
Web app launch failed as unable to connect to back-end web app
|
| 0x1800A6, 0x1800A7 | ||
| 0x1800BC, 0x1800BF | User is not entitled to access the Web/SaaS app | User is not entitled to access the Web/SaaS app |
| 0x1800BD | User is not entitled to access the Web/SaaS app for DirectAccess | User is not entitled to access the Web/SaaS app for DirectAccess |
| 0x1800D0 | Citrix Secure Access agent Session launch has failed while fetching the application configuration | Citrix Secure Access agent Session launch has failed while fetching the application configuration |
| 0x1800CD, 0x1800CE, 0x1800D6, 0x1800EA | Citrix Secure Access agent Session launch has failed while fetching the application configuration, Citrix Secure Access agent App launch has failed during policy evaluation, Citrix Secure Access agent App launch has failed | Malformed client requests |
| 0x1800DE | Citrix Secure Access agent App launch has failed during Policy evaluation | Citrix Secure Access agent App launch has failed during Policy evaluation |
| 0x180055, 0x1800DF, 0x1800E3 | Apps restricted by contextual policy, Access denied due to policy configuration | One or more apps not listed in the user dashboard |
| 0x1800EB | Citrix Secure Access agent app launch has failed as IPv6 is not supported | Citrix Secure Access agent app launch has failed as IPv6 is not supported |
| 0x1800EC, 0x1800ED | Citrix Secure Access agent App launch has failed due to invalid IP address | Citrix Secure Access agent App launch has failed due to invalid IP address |
| 0x10000001, 0x10000002, 0x10000003, 0x10000004 | Citrix Secure Access client login failure due to network issue | Network connectivity reachability issue with Citrix Secure Access client |
| 0x10000006 | Citrix Secure Access client login failure due to proxy in the middle | Proxy server interfering client connectivity with service |
| 0x10000007 | Citrix Secure Access client login failure due to untrusted certificate authority | Untrusted server certificate issue is observed |
| 0x10000008 | Citrix Secure Access client login failure due to invalid certificate | Invalid server certificate issue is observed |
| 0x1000000A | Citrix Secure Access client login failure due to configuration issue | Login failed as configuration is empty for the user |
| 0x1000000B | Citrix Secure Access client login failure due to connection failure | Connection terminated by the network or end user |
| 0x10000010 | Citrix Secure Access client login failure due to expired session | Configuration download failed as session is expired |
| 0x10000013 | Citrix Secure Access client login failure due huge configuration list | Citrix Secure Access client failed to log in |
| 0x11000003 | Citrix Secure Access client login failure due to control channel creation failure | Control channel establishment failed as the session expired |
| 0x11000004 | Citrix Secure Access client login failure due control channel creation failure | Control channel establishment failed |
| 0x11000005 | Citrix Secure Access client login failure due control channel creation failure | Control channel establishment failed |
| 0x11000006 | Citrix Secure Access client login failure due control channel creation failure | Control channel establishment failed because of network issue |
| 0x12000001 | Citrix Secure Access client logout failure as session already expired | Unable to logoff as session is terminated |
| 0x12000002 | Citrix Secure Access client logout failure as session already timed out | Session is forcefully terminated |
| 0x13000001 | App access failed as the session expired | Application launch failed as session is expired |
| 0x13000002 | App access failed as inadequate license | Application Launch failed because of license issue |
| 0x13000003, 0x13000008, 0x001800DF | App access failed as access forbidden, TCP/UDP app launch is denied as per Policy | Application launch failed as access is denied by service |
| 0x13000004, 0x13000005 | App access failed as the server is unavailable | Application launch failed as the client is unable to reach the service |
| 0x13000007 | App access failed as the access policy is disabled or the user is not subscribed | Application launch failed as policy evaluation and config validation failed |
| 0x13000009 | App access failed as the routing entry is missing | Application launch failed because of issues in application domain table |
| 0x1300000B | The client closed the connection | Client closed the connection with Secure Private Access service |
| 0x1300000C | The FQDN resolution over ZTNA failed | Unable to resolve FQDN by the DNS server |
| 0x001800D3 | Applications configuration download failure while login | Failed to fetch configured application destinations list |
| 0x001800D9, 0x001800DA | TCP/UDP app launch has failed during parsing policy evaluation response, TCP/UDP app launch has failed with invalid result during policy evaluation | Application configuration issue |
| 0x001800DB | TCP/UDP app launch has failed with invalid resource location configuration | Issue with resource location |
| 0x13000006, 0x001800DC, 0x001800DD | TCP app launch has failed due to unsupported Enhanced Security policy configured for the app, TCP app launch has failed due to unsupported Secure Browser Service redirection configured for TCP App | Enhanced security policy is bound to the HTTP application |
| 0x001800DE | TCP/UDP app launch has failed as there is no application configuration found for the destination | Unable to locate the application |
| 0x001800EA | TCP app launch has failed due to destination FQDN is too long | Host name length exceeds 256 characters |
| 0x001800ED | TCP app launch has failed because of invalid destination IP | Invalid IP address |
| 0x001800EF | TCP app launch has failed during connection establishment to private TCP server | Unable to establish end-to-end connection |
| 0x001800F5 | UDP app launch failed because of IPV6 address | IPv6 received in the app request |
| 0x001800F9 | UDP Traffic failed to deliver as client connection is lost | UDP traffic failed to deliver |
| 0x001800FF | UDP Data traffic delivery failed | UDP data traffic delivery failed |
| 0x10000401 | Citrix rendezvous server dial failed | Application launch failed because of network connectivity issues |
| 0x10000402, 0x1000040C | Unable to register the Connector Appliance, UDP network connection initialization failure | Connector appliance failed to register to Secure Private Access service |
| 0x10000403, 0x10000404, 0x10000407, 0x1000040A | Connection error, Control packet transmission failure, Error on reading Gateway service, Control packet parsing failure, Error on writing gateway service
|
Connectivity issue with Connector Appliance
|
| 0x1000040B, 0x1000040F, 0x10000410 | ||
| 0x10000405, 0x10000408, 0x10000409, 0x1000040D | Back-end Unreachable, UDP packet transmission failure, UDP packet receiving failure, Error on writing back-end, back-end closed the connection
|
Connectivity issues with Connector Appliance and back-end private TCP/UDP servers
|
| 0x1000040E, 0x10000412 | ||
| 0x10000406 | DNS resolution failed | Connector appliance fails to resolve DNS for FQDNs |
| 0x10000411 | Gateway service closed the connection | Private server connection terminated |
| 0x10000413 | Error in determining connection teardown reason | Failed to connect or send data to the private service IP or FQDN |
| 0x100508 | User context does not match the access rule conditions | No matching policy condition |
| 0x100509 | Access policy not associated with the application | No access policy associated with the application |
| 0x10050C | Policy evaluation results of multiple applications that the user might be entitled to | App enumeration information |
| 0x00180101 | TCP/UDP app launch failed as routing entry is missing in application domain table | TCP/UDP app launch failed as routing entry is missing in application domain table |
| 0x00180102 | TCP/UDP app launch failed as connectors are not healthy | TCP/UDP app launch failed as connectors are not healthy |
| 0x00180103 | UDP/DNS request failed, as Connector is unreachable | UDP/DNS request failed, as Connector is unreachable |
| 0x20580001 | Failed to load the page as NGS Cookie is expired | Failed to load the page as NGS Cookie is expired |
| 0x20580002 | Access policy fetch failed because of network failure | Access policy fetch failed because of network failure |
| 0x20580003 | Access policy fetch failed while parsing the JSON web token | Access policy fetch failed while parsing the JSON web token |
| 0x20580004 | Network failure to fetch Access Policy details | Network failure to fetch Access Policy details |
| 0x20580005 | Policy fetch failed while fetching public certificate | Policy fetch failed while fetching public certificate |
| 0x20580007 | Policy fetch failed while validating signature of JWT | Policy fetch failed while validating signature of JWT |
| 0x20580008 | Policy fetch failed while validating the public certificate | Policy fetch failed while validating the public certificate |
| 0x2058000A | Failed to determine store environment to form a policy URL | Failed to determine store environment to form a policy URL |
| 0x2058000B | Failed to get response of access policy fetch request | Failed to get response of access policy fetch request |
| 0x2058000C | Access policy fetch failed due to an expired secondary DS auth token | Access Policy fetch failed due to an expired secondary DS auth token |
| 0x10200002 | Connector appliance is not registered | Connector appliance is not registered |
| 0x10200003 | Unable to connect to connector appliance | Unable to connect to connector appliance |
| 0x10000301 | Connection to Citrix SPA service failed | Connection to Citrix Secure Private Access service failed |
| 0x10000303, 0x10000304 | The proxy server is not reachable | Proxy server is not reachable |
| 0x10000305 | Proxy server authentication failed | Proxy server authentication failed |
| 0x10000306 | Configured proxy servers are not reachable | Configured proxy servers are not reachable |
| 0x10000307 | Received error response from backend server | Received error response from backend server |
| 0x10000005 | Unable to send request to the target URL | Unable to send request to the target URL |
| 0x10000107 | Failed to process SSO | Failed to process SSO |
| 0x10000108, 0x1000010B | Failed to process SSO, unable to determine SSO settings | Failed to process SSO, unable to determine SSO settings |
| 0x10000101, 0x10000102, 0x10000103, 0x10000104 | FormFill SSO failed, incorrect form app configuration | FormFill SSO failed, incorrect form app configuration |
| 0x1000010A | FormFill SSO failed, incorrect form app configuration | FormFill SSO failed, incorrect form app configuration |
| 0x10000202 | Kerberos SSO failed | Kerberos SSO failed |
| 0x10000203 | Failed to process SSO for auth type | Failed to process SSO for auth type |
| 0x10000204 | Kerberos SSO failed but falling back to NTLM | Kerberos SSO failed but falling back to NTLM |
| 0x14000001 | Multiple ZTNA entitled accounts configured in the Citrix Workspace application | Multiple ZTNA entitled accounts configured in Citrix Workspace application |
Resolution steps
The following sections provide resolution steps for most of the info codes. For the codes that do not have the resolution steps captured, contact Citrix Support.
One or more apps not listed in the user dashboard
Info code: 0x180055, 0x1800DF, 0x1800E3
Due to the contextual policy settings, apps might not be seen for some users or devices. Parameters like trust factors (device posture or risk score) can affect the accessibility of the applications.
- Copy the transaction ID from the
reasonscolumn for error code0x18005Cin the Diagnostic Logs csv file. - Modify the
prodcolumn filter in the csv file to show events from the component calledSWA.PSEorSWA.PSE.EVENTS. This filter shows logs related to policy evaluation only. - Search for the evaluated policy payload in the
reasoncolumn. This payload shows the evaluated policy for the user’s context for all apps that the user is subscribed to. - If the policy evaluation indicates as app denied for the user, the possible reasons can be:
- Incorrect matching conditions in policy - check App policy configuration in Citrix Cloud
- Incorrect matching rules in policy - check App policy configuration in Citrix Cloud
- Incorrect matching default rule in policy - this is a fall-through case. Adjust the conditions accordingly.
User is not entitled to access the Web/SaaS app
Info code: 0x1800BC, 0x1800BF
The user might have clicked the app link for which the user might not have a subscription.
Ensure that the user has a subscription to the applications.
- Go to the application in the management portal.
- Edit the app and go to the Subscription tab.
- Ensure that the targeted user has an entry in the subscription list.
Slow back-end app performance
Info code:0x18000F
There are cases where the customer network is flaky due to the connectors in a resource location that can be down or the back-end server itself might not be responding.
- Ensure that the connector appliance is positioned geographically close to the back-end server to rule out network latencies.
- Check if the back-end server’s firewall is not blocking the connector appliance.
-
Check if the client is connecting to the nearest cloud POP.
For example,
nslookup nssvc.dnsdiag.neton the client, the canonical name in the answer indicates the geo-specific server such asaws-us-w.g.nssvc.net.
App launch failed because App FQDN length exceeded
Info code: 0x180006, 0x1800B7
App FQDNs must not exceed 512 characters in length. Check the application FQDN in the app configuration page. Ensure that the length does not exceed 512 bytes in size.
- Go to the Applications tab on the management console.
- Look for the application whose FQDN exceeds 512 characters.
- Edit the application and fix the app FQDN length.
App details length exceeded
Info code: 0x18000E
Check the policies if they are blocking the app access.
- Go to Access Policies.
- Look for the policies where the app has entitlement.
- Review the policy rules and conditions for the end user.
App access is denied
Info code: 0x180001, 0x18001A, 0x18001B, 0x18008A, 0x1800A9, 0x1800AB, 0x1800AC, 0x1800AD, 0x1800AE, 0x1800AF, 0x1800B0, 0x1800B1, 0x1800B2, 0x1800B3, 0x180048
This is related to contextual policies, where policies are denying the app for a given user.
Check the policies if they are blocking the app access
- Go to Access Policies.
- Look for the policies where the app has entitlement.
- Review the policy rules and conditions for the end user.
Applications not enumerated
Applications can be missing from the enumerated list because of policy denials or if the Secure Private Access integration is not enabled.
-
If access must be enabled for some of the apps but you see zero apps, try enabling the Secure Private Access integration.
- Sign into Citrix Cloud.
- Select Workspace Configuration from the hamburger menu, and then click Service Integrations.
- Click the ellipsis button in Secure Private Access, and then click Enable.
-
If the Secure Private Access integration is already enabled, disable it, and then enable it again to see if you have any apps.
Problem connecting to Connector Appliance
Info code: 0x1800EF
App routing fails because of non-availability of TCP connections with on-premises connectors.
Review events from the controller component
- Look up the
transaction IDfor error code0x1800EFin the diagnostic logs csv file. - Filter all events matching the transaction ID in the csv file.
-
Also, filter the
prodcolumn in the csv file that matchSWA.GOCTRL.If you see events with the
connectTypemessagemulticonnect::success? then;- This indicates that the tunnel establishment request was relayed to the controller successfully.
- Check if the
Resource Locationin the log message is correct. If it is incorrect, fix the resource location in the app configuration section on the Citrix management portal. - Check if the
VDA Ip and Portin the log message is correct. The VDA IP and port indicates the back-end application IP and port. If it is incorrect, fix the app FQDN or IP address in the app configuration section on the Citrix management portal. - Proceed to review the Connector events if you don’t find any earlier mentioned issues.
If you see events with the
connectTypemessageconnect::failureormulticonnect::success, then;- Check if the recommended fix for this log message states -
Check if connector is still connected to same pop. This indicates that the connector at the resource location might have gone down. Proceed to review the Connector events. - Contact Citrix Customer support if the earlier mentioned messages are not seen.
If you see events with the
connectTypemessageIntraAll::failure, then contact Citrix customer support.
Review events from the connector component
- Look up the
transaction IDfor error code0x1800EFin the Diagnostic Logs csv file. - Filter all events matching the transaction ID in the csv file.
- Also filter the
prodcolumn in the csv file that matchSWA.ConnectorAppliance.WebApps. - If you see events with
statusasfailure, then;- Review the
reasonmessage for each of these failure events. -
UnableToRegisterindicates that the connector wasn’t able to register to Citrix Cloud successfully. Contact Citrix Support. -
IsProxyRequiredCheckErrororProxyDialFailedorProxyConnectionFailedorProxyAuthenticationFailureorProxiesUnReachableindicates that the connector wasn’t able to resolve the back-end URL through the proxy configuration. Check the proxy configuration for correctness. - For further debugging see Connector SSO events.
- Review the
Single sign-on errors
For single sign-on, different SSO attributes from the app configuration are extracted and applied during app launch. If that particular user doesn’t have the attributes or if the attributes are incorrect, the single sign-on might fail. Ensure that the configuration looks correct.
- Go to Access Policies.
- Look for the policies where the app has entitlement.
- Review the policy rules and conditions for the end user.
SSO methods such as Form SSO, Kerberos, and NTLM are performed by the on-premises connector. Review the following diagnostic logs from the connector.
Review SSO events from the connector component
- Filter the
component namein the csv file that matchSWA.ConnectorAppliance.WebApps. - Do you see events with status as “failure”?
- Review the message for each of these failure events.
-
IsProxyRequiredCheckErrororProxyDialFailedorProxyConnectionFailedorProxyAuthenticationFailureorProxiesUnReachableindicates that the connector wasn’t able to resolve the back-end URL through the proxy configuration. Check the proxy configuration for correctness. -
FailedToReadRequestorRequestReceivedForNonSecureBrowseorUnableToRetrieveUserCredentialsorCCSPolicyIsNotLoadedorFailedToLoadBaseClientorProcessConnectionFailureorWebAppUnSupportedAuthTypeindicates tunneling failure. Contact Citrix Support. -
UnableToConnectTargetServerindicates that the back-end server is unreachable from the connector. Check the back-end configuration again. -
IncorrectFormAppConfigurationorNoLoginFormFoundorFailedToConstructForLoginActionURLorFailedToLoginViaFormBasedAuthindicates form-based authentication failure. Check the form SSO configuration section in App configuration in the Citrix management portal. -
NTLMAuthNotFoundindicates NTLM based authentication failure. Check the NTLM SSO configuration section in the app configuration in the Citrix management portal. - For further debugging, see Connector events.
App launch failed as authentication service is down
Info code: 0x180022
Secure Private Access allows admins to configure a third-party authentication service such as the traditional active directory, AAD, Okta, or SAML. Outages in these authentication services can this issue.
Check if the third-party servers are up and reachable.
SAML SSO failure
Info code: 0x18008A, 0x1800A9, 0x1800AA, 0x1800AB, 0x1800AC, 0x1800AD, 0x1800AE, 0x1800AF, 0x1800B0, 0x1800B1, 0x1800B2, 0x1800B3
Users face an authentication failure during app launch when it is IdP initiated or might see inaccessible links when it is SP initiated. Check the SAML app configuration at the Secure Private Access service side and service provider configuration as well.
Secure Private Access configuration:
- Go to the Applications tab.
- Look for the problematic SAML app.
- Edit the application and go to the Single Sign On tab.
- Check the following fields.
- Assertion URL
- Relay State
- Audience
- Name Id format, Name Id, and other attributes
Service provider configuration:
- Log in to the service provider.
- Go to SAML settings.
- Check the IdP certificate, audience, and IdP login URL.
If the configuration looks correct, contact Citrix support.
Invalid app FQDN
Info code: 0x180048
Customer admin might have provided an invalid FQDN or an FQDN where DNS resolve fails at the back-end server.
In this case, the end user sees an error on the webpage. Check the application settings.
SaaS App validation
Check if the app can be accessed from the network.
Web app validation
- Go to the Applications tab.
- Edit the problematic application.
- Go to App Details page.
- Check the URL. The URL must be accessible either in intranet or internet.
Secure Browser Service - DNS lookup/connection failed
Info code: 0x18009D
Broken browsing experience via Remote Browser Isolation service. Check the back-end server that the end user is trying to connect.
- Go to the back-end server and check if it is up and running, and is able to receive the requests.
- Check for proxy settings if it is stopping the connection to the back-end server.
Note:
The Citrix Remote Browser Isolation service was formerly known as the Secure Browser service.
CWA Web - DNS lookup/connection errors for Web apps
Info code: 0x1800A0, 0x1800A2, 0x1800A3, 0x1800A5, 0x1800A6, 0x1800A7
Broken browsing experience of web applications running inside a corporate network.
- Filter through the diagnostic logs for the FQDNs that are not resolvable.
- Check for reachability of the back-end server from inside the corporate network.
- Check the proxy settings to see if the connector is blocked from reaching the back-end server.
Direct Access - Misconfigured as Web app
Because Web app traffic is always routed via the connector, configuring direct access on them results in an app access error.
Check for the conflicting configuration between the routing domain table and the app configuration.
- Go to the application in the management portal.
- Edit the app and check if direct access is enabled.
- Check the app FQDN inside the routing domain table if it has been marked as internal.
User is not entitled to access the Web/SaaS app for DirectAccess
Info code: 0x1800BD
App configuration disables direct access for traffic that originates from browser-based clients.
Ensure that the user has a subscription to the applications.
- Go to the application in the management portal.
- Edit the app and check the agentless access configuration.
Enhanced security policies - Secure Browser Service misconfiguration
Info code: 0x1800C3
Incorrect behavior seen than what was intended by the policy rules. Check contextual access policies.
- Go to the Policies tab.
- Check the policies associated with the application.
- Check the rules for those policies.
Enhanced security policies - policy misconfiguration
Incorrect behavior seen than what was intended by the policy rules. Check the enhanced security settings.
- Go to the application.
- Click the Access Policies tab.
- Check the settings in the Available security restrictions: section.
Citrix Secure Access agent session launch has failed while fetching the application configuration
Info code: 0x1800D0
Citrix Secure Access app fails to successfully establish a full tunnel to Citrix Cloud.
- Review the routing domain configuration for the TCP/UDP apps.
- Ensure that the maximum number of entries is well within the 16k limit.
TCP/UDP apps - Malformed client requests
Info code: 0x1800CD, 0x1800CE, 0x1800D6, 0x1800EA
Either the VPN tunnel is not established or certain FQDNs might not be tunneled.
- Ensure that the requests are not being fabricated or reconstructed by proxies in the middle.
- Suspected man-in-middle attacks.
TCP/UDP Apps - Secure Browser Service redirect misconfiguration
Info code: 0x1800DD
Remote Browser Isolation service redirects can only be applied for Web apps and not TCP/UDP apps. Review the app configuration in the Secure Private Access service GUI.
Note:
The Citrix Remote Browser Isolation service was formerly known as the Secure Browser service.
Citrix Secure Access agent app launch has failed during the policy evaluation
Info code: 0x1800DE
Ensure that all the internal FQDNs that are to be tunneled by the Citrix Secure Access client have a corresponding entry in the routing domain table.
Citrix Secure Access agent app launch has failed as IPv6 is not supported
Info code: 0x1800EB
Review the routing domain entries. Ensure that there are no IPV6 entries in the table.
Citrix Secure Access agent app launch has failed due to invalid IP address
Info code:0x1800EC, 0x1800ED
Review the routing domain entries. Ensure that the IP addresses are valid and are pointing to the correct back end.
Network connectivity reachability issue with Citrix Secure Access client
Info code: 0x10000001, 0x10000002, 0x10000003, 0x10000004
- Check if the client machine network is reachable. If the network is reachable, contact Citrix Support with the client debug logs.
- Check if the proxy or firewall is blocking the network.
To collect client debug logs, see How to collect client logs.
Proxy server interfering client connectivity with service
Info code: 0x10000006
- Check if the client machine network is reachable.
- Check if the proxy is configured correctly in the client.
- If there are no issues with both, contact Citrix Support with the client debug logs.
To collect client debug logs, see How to collect client logs.
Untrusted server certificate issue is observed
Info code: 0x10000007
Contact Citrix Support to check whether the server certificate is correctly generated by a valid CA.
Invalid server certificate issue is observed
Info code: 0x10000008
Contact Citrix Support to check whether the server certificate is self-signed, expired, or from an untrusted source.
Login failed as configuration is empty for the user
Info code: 0x1000000A
- Ensure that at least one TCP/UDP/HTTP app is configured. For details, see Add and manage applications.
- Ensure that the Application Domain table (Secure Private Access > Settings > Application Domain) is not empty or all entries are not disabled. The destinations configured in the TCP/UDP/HTTP application are automatically added to this table.
It is recommended that you do not delete or disable an active TCP/UDP/HTTP application’s destinations or URL.
Connection terminated by the network and or end user
Info code: 0x1000000B
Check if the network is interrupted or if the end-user canceled the connection during the ZTNA session connection.
Configuration download failed as session is expired
Info code: 0x10000010
The VPN session might have expired during the ZTNA session config download request. Try to relogin to the Citrix Secure Access client.
Citrix Secure Access client failed to log in
Info code: 0x10000013
The Citrix Secure Access client failed to login as the configuration size exceeds the maximum configuration limit.
- Review the routing domain configuration for the TCP/UDP apps in Secure Private Access > Settings > Application Domain
-
Ensure that the number of entries are not huge. If the entries list is huge, disable or remove unused destinations.
If the destination list is expected to be more than 1000s, try increasing the max configuration download size by updating the ConfigSize registry key. For details, see Citrix Gateway VPN client registry keys.
Control channel establishment failed as the session expired
Info code: 0x11000003
The control channel for the DNS request establishment has failed as the session is expired.
The ZTNA session might have expired during the control channel setup.
Try to relogin to the Citrix Secure Access client.
Control channel establishment failed
Info code: 0x11000004
The control channel for DNS request establishment has failed.
- Maintain the resource location healthy:
- Log on to Citrix Cloud.
- Click Resource Location from the hamburger menu.
- Run a health check for the connector appliances on the respective resource location.
- If this does not fix the issue, try restarting the connector virtual machine.
- Maintain HA connector appliance:
- Log on to Citrix Cloud.
- Click Resource Location from the hamburger menu.
- Ensure that the expected resource location has at least two Connector Appliances.
Ensure the following:
- The resource location LAN is in working condition.
- No firewall or proxy is in the middle blocking Connector Appliance to the service or the back-end servers.
- The client network is healthy.
- The back-end private servers are up and running.
- The DNS servers are up and running.
- FQDNs are resolvable.
If you meet the preceding recommendations, then do the following.
- Fetch the transaction ID from the diagnostic log for this error.
- Filter all events matching the transaction ID in the Secure Private Access dashboard.
- Check if any error occurred in the client or Connector Appliance or Service diagnostic logs, matching to the transaction ID. Then take the appropriate actions accordingly.
-
Check if the resource location is chosen correctly for the destination in the application domain table (Secure Private Access > Settings > Application Domain).
- Check if the application is configured with the correct port, IP ranges, domains. For details, see Add and manage applications.
If you are still not able to resolve the issue, Contact Citrix Support with the error code respective to the transaction ID and client logs.
To collect client debug logs, see How to collect client logs.
Control channel establishment failed
Info code: 0x11000005
Control channel (for DNS request) establishment failed.
- Check the Secure Private Access service license entitlement.
- If not entitled, Contact Citrix Support to check the license.
For details, see https://www.citrix.com/buy/licensing/product.html.
Control channel establishment failed due to network issue
Info code: 0x11000006
Control channel (for DNS request) establishment failed due to network issue.
- Check if the Secure Private Access service is reachable.
- If not reachable, Contact Citrix Support with the error code and the client Logs.
To collect client debug logs, see How to collect client logs.
Control channel establishment failed due to insufficient IIPs
Info code: 0x11000007
Control channel (for DNS request) establishment failed due to insufficient IIPs.
Contact Citrix Support with the error code and the client Logs.
To collect client debug logs, see How to collect client logs.
Unable to logoff as session is terminated
This issue might have occurred because the client machine (keyboard or mouse) was idle for more than the configured timeout period.
Info code: 0x12000001
Try to relogin to the Citrix Secure Access client.
Session is forcefully terminated
The session is forcefully terminated as the configured force timeout is reached.
Info code: 0x12000002
Try to relogin to the Citrix Secure Access client.
Application Launch failed as session is expired
Info code: 0x13000001
- The ZTNA session has expired during the app launch.
- Try to relogin to the Citrix Secure Access client.
Application Launch failed because of license issue
Info code: 0x13000002
- Check for the Secure Private Access service license is entitlement.
- If not entitled, Contact Citrix Support to check the license.
For details, see https://www.citrix.com/buy/licensing/product.html.
Application launch failed as access is denied by service
Info code: 0x13000003, 0x13000008, 0x001800DF
Application launch is denied as per the policy configuration for the user and application.
Ensure the following.
- Same destinations are not used in multiple applications (HTTP, HTTPS, TCP, UDP)
- There are no overlapping destinations on multiple applications.
- Access policies are bound to the applications.
Also check the conditions and actions of the policies configured for the denied application. Then review the policy conditions and actions.
For details see, Access policies.
Application launch failed as the client is unable to reach the service
Info code: 0x13000004, 0x13000005
- Check if the Secure Private Access Service is reachable.
- Launch the app again.
- If the app is not reachable for a long time, Contact Citrix Support with the error code and client logs.
To collect client debug logs, see How to collect client logs.
Application launch failed as policy evaluation and config validation failed
Info code: 0x13000007
Application launch failed as policy evaluation and config validation is failed by the Secure Private Access service.
Unable to spot application for accessed destination.
Application launch failed as access is denied by service.
Application launch failed because of issues in application domain table
Info code: 0x13000009
Application launch failed as the Application domain table does not have an entry for the accessed destination.
Check that the route entry is correctly configured for the application in Secure Private Access > Settings > Application Domain.
Client closed the connection with Secure Private Access service
Info code: 0x1300000B
- Check if the end-user manually closed the connection.
- If not, contact Citrix Support with the error code and client logs.
To collect client debug logs, see How to collect client logs.
Unable to resolve FQDN by the DNS server
Info code: 0x1300000C
This issue occurs when the Connector Appliance fails to resolve DNS for FQDNs.
- Check the DNS entry for the respective app FQDN in the DNS server.
- Ensure that an appropriate DNS server is configured in the Connector Appliances. For details, see Configuring network settings on the Connector Appliance administration page.
Unable to locate the application
Info code: 0x001800DE
You might be unable to locate the application for the accessed destination for the user. This might occur if the destination to resource location mapping missing in the Application Domain table.
- Ensure that the TCP/UDP or HTTP application is configured for the accessed destination.
- Ensure that the user has a subscription to the application for the accessed destination.
- Go to the application in the management portal.
- Edit the app and go to the Subscription tab.
- Ensure that the targeted user has an entry in the subscription list.
- Ensure that the Application Domain table has the destination and the appropriate resource location.
Failed to fetch configured application destinations list
Info code: 0x001800D3
- Ensure that at least one TCP/UDP/HTTP app is configured. For details, see Add and manage applications.
- Ensure that the Application Domain table (Secure Private Access > Settings > Application Domain) page is not empty or not all entries are disabled. The destinations configured in the TCP/UDP/HTTP application are automatically added to this table. It is recommended not to delete or the disable the active TCP/UDP/HTTP application’s destinations or URLs in the Application Domain table.
Application configuration issue
The application configuration contains a special character or some policy configuration issue.
Info code: 0x001800D9, 0x001800DA
Ensure the following:
- The app configuration does not contain unsupported characters.
- The destination IP address or IP address range or the IP CIDR are valid.
- The application destination is enabled in the Application Domain table (Secure Private Access > Settings > Application Domain).
- The policies are configured and bound to the respective application.
- The access policy configuration is correct.
Issue with resource location
Info code: 0x001800DB
-
Ensure that a resource location is configured.
- In the Citrix Cloud hamburger menu, select Resource Location.
- Ensure that the expected resource location is configured and the resource location is in active status.
-
Ensure that a correct resource location is selected for the destination in the Application Domain table (Secure Private Access > Settings > Application Domain).
The destinations configured in the TCP/UDP/HTTP application are automatically added to this table. It is recommended not to delete or disable the active TCP/UDP/HTTP application’s destinations or URLs in the Application Domain table.
Enhanced security policy is bound to the HTTP application
Info code: 0x001800DC, 0x001800DD, 0x13000006
HTTP Application which has an enhanced security policy bound is accessed through the Citrix Secure Access client.
- Ensure that the same destination is not used for both TCP/UDP and HTTP applications.
- If enhanced security policy is enabled for HTTP/HTTPS application, it is recommended to access the app only through Citrix Workspace app or Citrix Remote Browser Isolation service.
-
Disable enhanced security control for HTTP/HTTPS applications to access the app through the Citrix Secure Access client.
- Go to the Secure Private Access admin portal.
- Click the Applications tab and search for the policy name for the accessed destination HTTP/HTTPS application.
- Click the Access Policies tab and search for the policy name identified earlier.
- Select the policy and click Edit.
- Change the action from Allow access with restriction to Allow access.
For details on configuration, see Add and manage applications.
Note:
The Citrix Remote Browser Isolation service was formerly known as the Secure Browser service.
Host name length exceeds 256 characters
Info code: 0x001800EA
The host name received in the application launch request exceeds 256 characters.
It is recommended that the FDQN characters do not exceed 256 characters.
Invalid IP address
Info code: 0x001800ED
The IP address received in the application launch request is invalid.
It is recommended to access only a valid private IP address from the clients.
Unable to establish end-to-end connection
Info code: 0x001800EF
Unable to establish end-to-end connection between the client and the server configured in resource location.
- Ensure that the resource location is in active status.
- In the Citrix Cloud hamburger menu, select Resource Location.
- Run a health check for the Connector Appliances on the respective resource location.
- If this does not fix the issue, restart the connector virtual machine.
- Maintain a high availability Connector Appliance
- In the Citrix Cloud hamburger menu, select Resource Location.
- Ensure that the resource location has at least two Connector Appliances.
-
Ensure the following:
- Resource location LAN is in working condition.
- No firewalls or proxies in the middle blocking Connector Appliance to the service or back-end servers.
- Client Network is healthy.
- Back-end private servers are healthy.
- DNS servers are healthy.
- FQDNs are resolvable.
If there are no issues with these, then do the following:
- Fetch the transaction ID from the diagnostic logs for this error.
- Filter all events matching the transaction ID in the Secure Private Access service dashboard.
- Check the diagnostic logs corresponding to the transaction ID from the Secure Private Access service dashboard and then take appropriate actions accordingly.
- Check that a correct resource location is selected as the destination in the Application Domain table (Secure Private Access > Settings > Application Domain).
- Check if the application is configured (Secure Private Access > Applications) with the correct IP address, port, and FQDN.
If none of these steps resolve the issue, then contact Citrix Support with the error code respective to the transaction ID and collect client logs.
To collect client debug logs, see How to collect client logs.
IPv6 received in the app request
Info code: 0x001800F5
An IPv6 is received in the app request that is not supported. Currently, only IPv4 is supported.
Edit the application to fix the application IP address issue.
- Go to the Secure Private Access admin portal.
- Click the Applications tab.
- Search for the app and click Edit.
For details, see Add and manage apps.
UDP traffic failed to deliver
Info code: 0x001800F9
UDP traffic failed to deliver as the client connection is lost
- Check if the client session is active.
- Log out and then relogin.
UDP data traffic delivery failed
Info code: 0x001800FF
- Look up the transaction ID for the error code and filter all events matching to the transaction ID in the Secure Private Access service dashboard.
- Check if any error occurred in the other component matching the transaction ID. If an issue is found in other components, then take appropriate actions accordingly.
- If this does not solve the issue, contact Citrix Support with the error code along with the respective transaction ID.
Application launch failed due to network connectivity issues
Info code: 0x10000401
Application launch failure because of network connectivity issues between Connector Appliance and Secure Private Access service
- Check the public internet connectivity of the Connector Appliance.
- Check if any proxy or firewall rules are blocking the connection.
- If any proxy is causing the issue, bypass the proxy and try the app launch again.
- Check the health status of the Connector Appliance (Citrix Cloud > Resource Location).
For details on network settings, see Network settings for your Connector Appliance.
Connector Appliance failed to register to Secure Private Access service
Info code: 0x10000402, 0x1000040C
- Go to the Connector Appliances admin page and check the Connector Summary.
- If the connector status is not good, then go to the resource location in the management portal.
- Run a health check for the Connector Appliances on the respective resource location.
- If the health check fails, restart the connector virtual machine.
- Check the connector summary and run the health check again.
For details on network settings, see Network settings for your Connector Appliance.
Connectivity issue with Connector Appliance
Info code: 0x10000403, 0x10000404, 0x10000407, 0x1000040A, 0x1000040B, 0x1000040F, 0x10000410
- Look up the transaction ID for the error code.
- Filter all events matching the transaction ID in the Secure Private Access dashboard.
- Check if any error occurred in the other component matching the transaction ID if found do the respective workaround matching to that error code.
-
If no error is found in other components, then do the following:
- Go to the Connector Appliances admin page.
- Download the diagnostic report. For details, see Generating a diagnostic report.
- Capture the packet trace. For details, see Verify your network connection.
- Contact Citrix support with this diagnostic report and packet trace along with the error code and transaction ID.
Connectivity issues with Connector Appliance and back-end private TCP/UDP servers
Info code: 0x10000405, 0x10000408, 0x10000409, 0x1000040D, 0x1000040E, 0x10000412
Connector Appliance has connectivity issue with the back end Private TCP/UDP servers.
- Check if the back end server that the end user is trying to connect is up and running and is able to receive the requests.
- Check for the reachability of the back-end servers from inside the corporate network.
- Check the proxy settings to see if the connector is blocked from reaching the back-end server.
- If the request for an FQDN based app, check the DNS entry for the respective app in the DNS server.
Connector Appliance fails to resolve DNS for FQDNs
Info code: 0x10000406
- Check the DNS entry for the respective app FQDN in the DNS server.
- Ensure that an appropriate DNS server is configured in the Connector Appliances. For details, see Configuring network settings on the Connector Appliance administration page.
Private server connection terminated
Info code: 0x10000411
Connection to the private server is terminated by the client or Secure Private Access service.
- Check if the end user has closed the application.
- Check other diagnostic logs matching to this log’s transaction ID and take appropriate actions accordingly.
- Launch the app again.
- If this does not resolve the issue, contact Citrix Support with the error code and the transaction ID.
Failed to connect or send data to the private service IP or FQDN
Info code: 0x10000413
- Private server connection terminated
- Connectivity issues with Connector Appliance and backend private TCP/UDP servers. Review the routing domain entries. Make sure that the IP addresses are valid and are pointing to the correct back end.
No matching policy condition
Info code: 0x100508
The user context does not match the access rule conditions defined in the policies assigned to the app.
Update the policy configuration to match the user’s context.
No access policy associated with the application
Info code: 0x100509
- In the Citrix Secure Private Access service GUI, click Access Policies on left navigation.
- Ensure that an access policy is associated with the respective app.
-
If an access policy is not associated with the app, create an access policy for the app. For details, see Create access policies.
- If this does not resolve the issue, contact Citrix Support.
No application configuration found for the FQDN or the IP address
Info code: 0x10050A
No matching application was found for the incoming FQDN or the IP address request. Hence, the app is classified as an unpublished application. If this is not expected, do the following.
- Go to the Secure Private Access service admin portal.
- Click Applications on left navigation.
- Search for the app, and click Edit.
-
Add an FQDN or the IP address to the application. You can add the exact domain, IP address, or a wildcard domain.
Note: Adding an FQDN or an IP address in Secure Private Access > Settings > Application Domain does not solve this issue. It must be added as part of the application configuration.
App enumeration information
Info code: 0x10050C
This code captures the policy evaluation results of multiple applications that the user might be entitled to. App access might be denied for the following reasons:
- The user context does not match the access rule conditions defined in the policies assigned to the app – For details, see No matching policy condition.
- No access policy is associated with the application – For details, see No access policy associated with the application.
- A policy associated with the application is configured to deny access – In this case, no action required as this is intended.
- Unexpected Internal error in enforcing access policy. For details, contact Citrix Support.
TCP/UDP app launch failed as routing entry is missing in application domain table
Info code: 0x00180101
This issue can occur if the application configuration is present but the routing entry is missing or was previously deleted.
Add a routing entry (Secure Private Access > Settings > Application Domain) for the destination that is accessed.
TCP/UDP app launch failed as connectors are not healthy
Info code: 0x00180102
This issue can occur if none of the connectors is up/responding to the new connection.
Run a health check for the Connector Appliances on the respective resource location.
UDP/DNS request failed as connector is unreachable
Info code: 0x00180103
This issue can occur if the UDP/DNS traffic is unable to reach the connector.
Run a health check for the Connector Appliances on the respective resource location.
Failed to load the page as the NGS cookie is expired
Info code: 0x20580001
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Access policy fetch failed because of a network failure
Info code: 0x20580002
- Check the URL and the network connection.
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Access policy fetch failed while parsing the JSON web token
Info code:0x20580003
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Network failure to fetch access policy details
Info code:0x20580004
- Check if the access policy is enabled.
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Policy fetch failed while fetching the public certificate
Info code: 0x20580005
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Policy fetch failed while validating signature of the JSON web token
Info code: 0x20580007
- Check if the network time and user device time are in sync.
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Policy fetch failed while validating the public certificate
Info code: 0x20580008
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Failed to determine the store environment to form a policy URL
Info code: 0x2058000A
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Failed to get a response for access policy fetch request
Info code: 0x2058000B
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Access policy fetch failed due to an expired secondary DS auth token
Info code: 0x2058000C
- Restart the browser and try opening the app again.
- If this does not resolve the issue, contact Citrix Support.
Connector Appliance is not registered
Info code: 0x10200002
Check the Connector Appliance registration.
For details, see Register your Connector Appliance with Citrix Cloud.
Unable to connect to the Connector Appliance
Info code: 0x10200003
The Connector Appliance is unable to communicate between Citrix Cloud and resource locations.
Check the connector registration.
For details, see Register your Connector Appliance with Citrix Cloud.
Connection to Citrix Secure Private Access service failed
Info code: 0x10000301
Check the Connector Appliance network settings. For details, see Network settings for your Connector Appliance.
Proxy server is not reachable
Info code: 0x10000303, 0x10000304
Check the proxy server settings and make sure that it is reachable to Connector Appliance. For details, see Register your Connector Appliance with Citrix Cloud.
Proxy server authentication failed
Info code: 0x10000305
Check proxy server credentials and make sure that they are configured correctly in Connector Appliance. For details, see After registering your Connector Appliance.
Configured proxy servers are not reachable
Info code: 0x10000306
Check the Connector Appliance network settings, firewall settings, or proxy server settings. For details see the following topics:
- Network settings for your Connector Appliance
- Register your Connector Appliance with Citrix Cloud
- Connector Appliance communication
Received error response from backend server
Info code: 0x10000307
Check the backend web server’s HTTP status code, if it is not an expected code.
Unable to send request to the target URL
Info code: 0x10000005
Check the target URL or check the Connector Appliance network settings. For details, see Network settings for your Connector Appliance.
Failed to process SSO
Info code: 0x10000107
Failure to retrieve app configuration data from Citrix Cloud.
Check the Connector Appliance network settings and make sure that the NTP server is configured and there are no time strip issues. For details, see Network settings for your Connector Appliance.
Connection to the Citrix Secure Private Access service failed
Info code: 0x10000108, 0x1000010B
Check the Connector Appliance network settings. For details, see Network settings for your Connector Appliance.
Failed to process SSO, unable to determine SSO settings
Info code: 0x1000010A
Check the SSO configuration and make sure that the server is reachable to Connector Appliance.
FormFill SSO failed, incorrect form app configuration
Info code: 0x10000101, 0x10000102, 0x10000103, 0x10000104
Check the SSO form app configuration and make sure that the user name, password, action, and login URL fields are correctly configured on the app settings.
Kerberos SSO failed
Info code: 0x10000202
Check the Kerberos SSO settings on the backend server and the domain controller. Also check the fallback NTLM authentication settings.
For Kerberos SSO settings, see Validating your Kerberos configuration.
Failed to process SSO for auth type
Info code: 0x10000203
Check the SSO settings in the Secure Private Access service and the backend server. For Secure Private Access service, see Set the preferred sign-on method.
Kerberos SSO failed but falling back to NTLM
Info code: 0x10000204
Retrieving the Kerberos ticket from the domain controller has failed. As a secondary authentication, Connector Appliance has tried the fallback NTLM authentication.
To enable successful Kerberos authentication, check the Kerberos SSO settings on the backend server and domain controller.
For details, see Validating your Kerberos configuration.
Multiple ZTNA entitled accounts configured in the Citrix Workspace application
Info code: 0x14000001
Configure only one ZTNA entitled account in the Citrix Workspace application.
How to collect client logs
-
Windows client:
- Open the app and ensure that logging is enabled.
- Now connect to the Secure Private Access service and duplicate the issue you are facing.
- In the app, go to Logging and click Collect Log Files. This generates the log file.
- Save the log file on the client machine’s desktop.
-
Mac client:
- Open the app and go to Logs > Verbose.
- Clear the logs and proceed to reproduce the issue.
- Go back to Logs > Export logs. This creates a zip file that contains log files.
Answers to FAQs
What are Secure Private Access diagnostic logs?
Secure Private Access diagnostic logs capture all events that occur when a user accesses any application (Web/SaaS/TCP/UDP). These logs capture device posture, app authentication, app enumeration, and app access logs. The details are presented in a tabular format. You can view the logs for the pre-set time or for a custom timeline. You can add columns to the chart by clicking the + sign depending on what information you want to see in the dashboard. You can export the user logs into CSV format.
Where do I find Secure Private Access logs?
- Log on to Citrix Cloud.
- On the Secure Private Access service tile, click Manage.
- Click Dashboard on the left navigation in the admin user interface.
- In the Diagnostic Logs chart, click the See more link.
Which widget displays the Secure Private Access diagnostic logs?
The Diagnostics Logs widgets in the Logging and Troubleshooting section displays a pie chart view of all Secure Private Access events related to authentication, application launch, app enumeration, and also logs related to device posture. The Secure Private Access diagnostic logs fetches events from multiple internal components, each sending an event when an end user accesses an application. These events are divided in categories; Login/Logoff, App Enumeration, and App Access. The pie chart displays the overall success/failures ratio of each category. Clicking the colored pie on any chart takes you to the diagnostic logs where you can find the appropriate events. There are also device posture logs if you have Device Posture service enabled. You can also click the See more link to view the complete diagnostic logs.
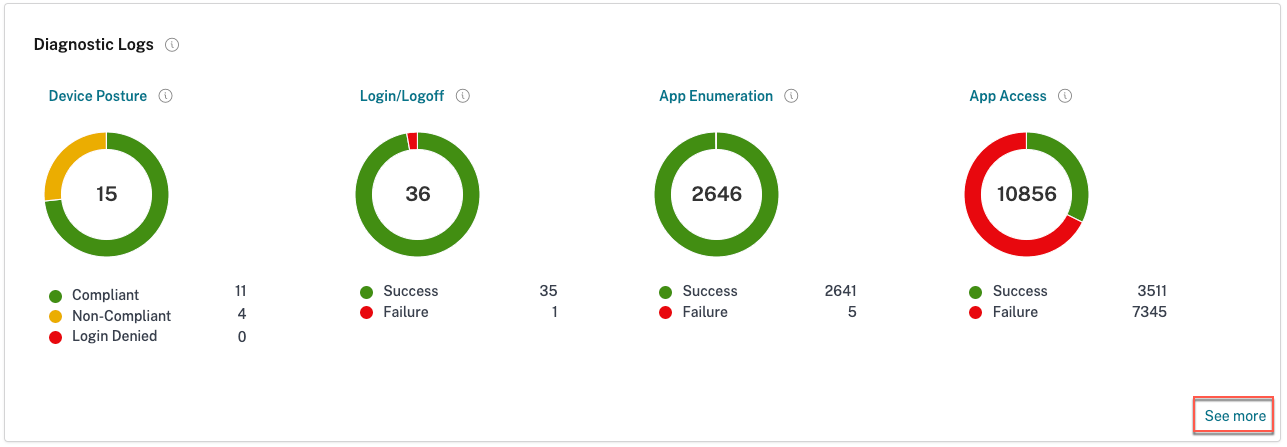
What details can I find in the Secure Private Access diagnostic logs?
The Secure Private Access user logs dashboard provides the following details, by default.
- Timestamp - Time of the event in UTC.
- Username - User name of the end-user accessing the app.
- App Name - Name of the app/apps that were accessed.
- Policy Info - Displays the name of the access policy or policies that were triggered during the event.
- Status - Displays the status of the event, success, or failure.
- Info Code - Every failure event within the Secure Private Access diagnostic logs dashboard has an associated info code. See more information on info code.
- Description - Displays the reason for the failure or more details about the event.
- APP FQDN: FQDN of the application accessed
- Event type - Displays the event type associated with the operation performed.
- Operation type - Displays the operation for which the log is generated.
- Category - Three categories are available depending on the type of event. That is app authentication, app enumeration, or app access. These options are also available as filter options. You can use these options to filter logs depending on the type of issue that you are facing.
- Transaction ID - Transaction ID correlates all Secure Private Access logs for an access request. Learn how to use a transaction ID. The following details can be fetched by clicking the + button on the rightmost side of the dashboard:
- SPA PoP Location - Displays the name/ID of the Secure Private Access service PoP location that was used during app access. See Secure Private Access PoP Locations.
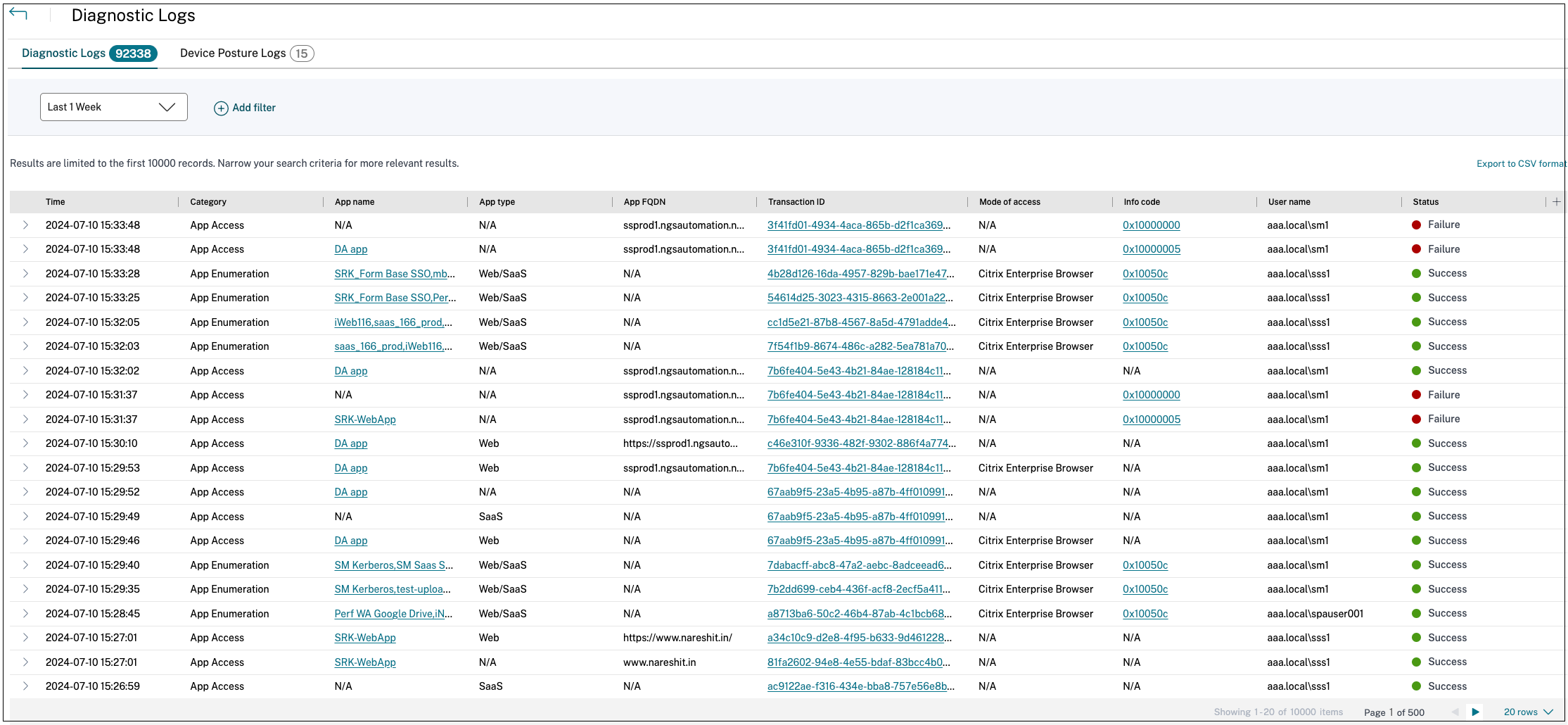
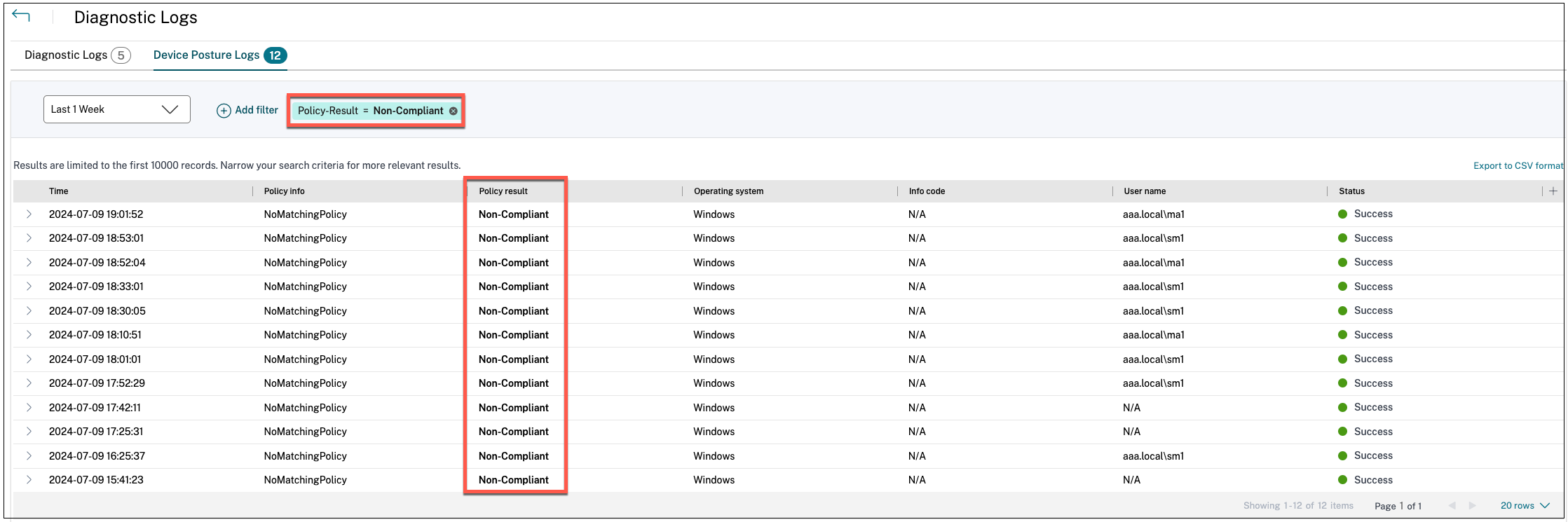
How do I filter the diagnostic logs?
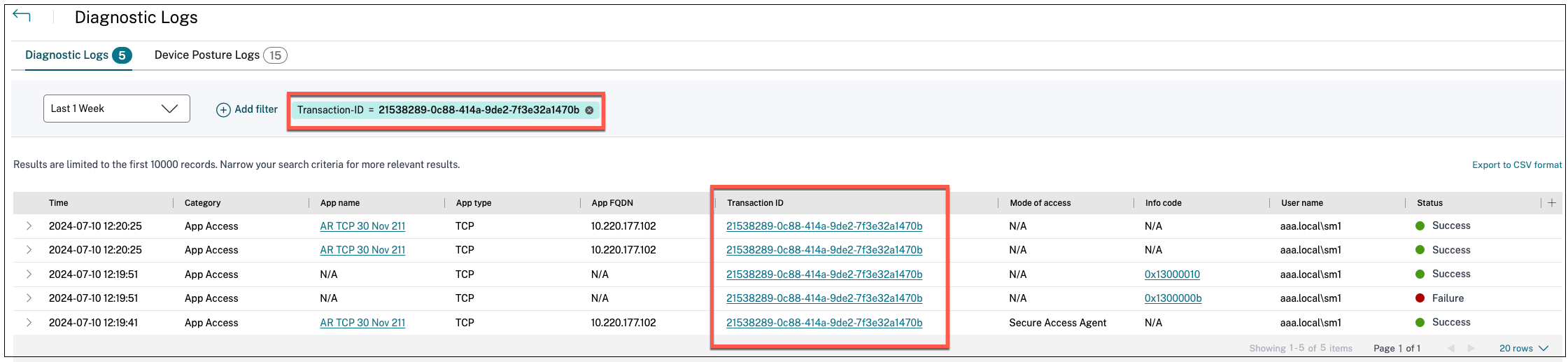
You can use the Add Filter option to refine you search based on the various criteria such as app type, category, description. For example, in the search field, you can click Transaction ID, = (equals to some value), and enter 21538289-0c88-414a-9de2-7f3e32a1470b, to search for all logs related to this transaction ID. For details on search operators that can be used with the filter option, see Search operators.
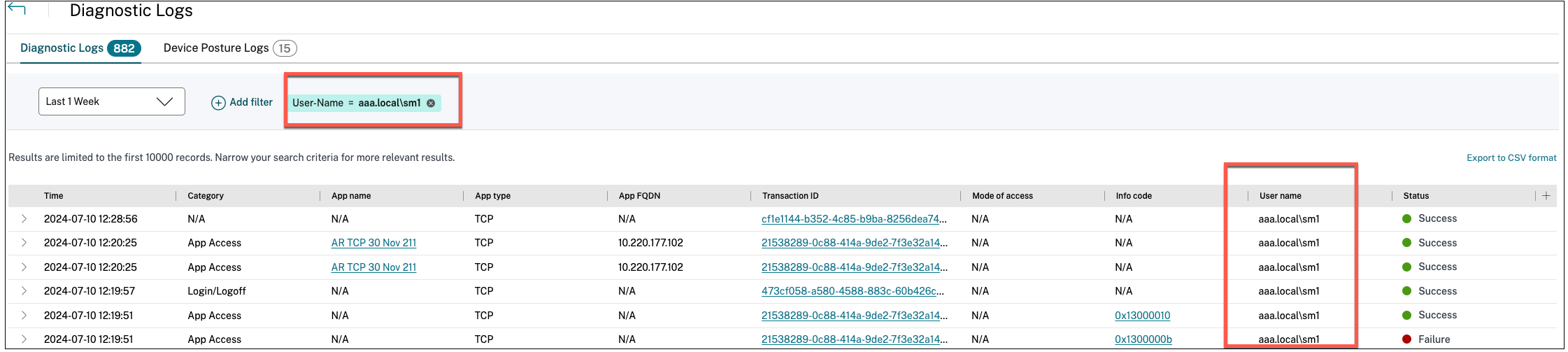
You can also use the various filter options to refine your search on the Device Posture logs.
What events are captured in the Secure Private Access diagnostic logs?
The Secure Private Access diagnostic logs capture the following events:
- Device Posture: End-user device status. These logs capture information about the device posture results. Whether the device was deemed compliant, non-compliant, or denied access based on your device posture policy.
- Login/Logoff: Events about end-user logon or logoff status to the Citrix Secure Access client and authentication to workspace (internal or external providers).
- App Enumeration: In the Secure Private Access service, access policies configured by admins decide which user gets to access which app. Denied applications are not visible (not enumerated) to end-users within Citrix Workspace App. These events help you know which applications were allowed or denied Access to a user based on the access policies configured within the Secure Private Access service.
- App Access: Events of end-user application/endpoint access, allow/deny status, single sign-on status, and connectivity status as per the configured access policies for the selected time interval.
How do I use the Secure Private Access troubleshooting topic to resolve a failure that I have encountered?
- Fetch the info code for the failure that you are trying to resolve.
- Find the info code in the Error lookup table.
- Follow the resolution steps provided for that info code.
What is an info code? Where do I find them?
Some log events such as failures have an associated info code. Search for this info code within the Error lookup table to find the resolution steps or more information about that event.
What is a transaction ID? How do I use it?
Access failures/issues via Citrix Enterprise Browser display a Transaction ID to the end user. Admins can fetch this transaction ID from the end users and use this transaction ID to filter the exact logs that caused the issue, enabling them to identify the exact problem. Once the admins filter events with the transaction ID, only the events pertaining to the issue in hand are displayed, providing all the details to the admins on why the failure or the issue happened. Admins can then use the error code on those logs to further resolve the issues.
What are all the Secure Private Access PoP locations?
The following is the list of Secure Private Access PoP locations.
| PoP name | Zone | Region |
|---|---|---|
| az-us-e | Azure eastus | Virginia |
| az-us-w | Azure westus | California |
| az-us-sc | Azure southcentralus | Texas |
| az-aus-e | Azure australiaeast | New South Wales |
| az-eu-n | Azure northeurope | Ireland |
| az-eu-w | Azure westeurope | Netherlands |
| az-jp-e | Azure japaneast | Tokyo, Saitama |
| az-bz-s | Azure brazilsouth | Sao Paulo State |
| az-asia-se | Azure southeastasia | Singapore |
| az-uae-n | Azure uaenorth | Dubai |
| az-in-s | Azure southindia | Chennai |
| az-asia-hk | Azure eastasia | Hong Kong |
What do I do if I am unable to resolve my failure using the info code and the error lookup table?
Contact Citrix Support.
References
- Add a Web app
- Add a SaaS app
- Configure client-server apps
- Create access policies
- Route tables
In this article
- FAQs?
- Info code lookup table
-
Resolution steps
- One or more apps not listed in the user dashboard
- User is not entitled to access the Web/SaaS app
- Slow back-end app performance
- App launch failed because App FQDN length exceeded
- App details length exceeded
- App access is denied
- Applications not enumerated
- Problem connecting to Connector Appliance
- Single sign-on errors
- App launch failed as authentication service is down
- SAML SSO failure
- Invalid app FQDN
- Secure Browser Service - DNS lookup/connection failed
- CWA Web - DNS lookup/connection errors for Web apps
- Direct Access - Misconfigured as Web app
- User is not entitled to access the Web/SaaS app for DirectAccess
- Enhanced security policies - Secure Browser Service misconfiguration
- Enhanced security policies - policy misconfiguration
- Citrix Secure Access agent session launch has failed while fetching the application configuration
- TCP/UDP apps - Malformed client requests
- TCP/UDP Apps - Secure Browser Service redirect misconfiguration
- Citrix Secure Access agent app launch has failed during the policy evaluation
- Citrix Secure Access agent app launch has failed as IPv6 is not supported
- Citrix Secure Access agent app launch has failed due to invalid IP address
- Network connectivity reachability issue with Citrix Secure Access client
- Proxy server interfering client connectivity with service
- Untrusted server certificate issue is observed
- Invalid server certificate issue is observed
- Login failed as configuration is empty for the user
- Connection terminated by the network and or end user
- Configuration download failed as session is expired
- Citrix Secure Access client failed to log in
- Control channel establishment failed as the session expired
- Control channel establishment failed
- Control channel establishment failed
- Control channel establishment failed due to network issue
- Control channel establishment failed due to insufficient IIPs
- Unable to logoff as session is terminated
- Session is forcefully terminated
- Application Launch failed as session is expired
- Application Launch failed because of license issue
- Application launch failed as access is denied by service
- Application launch failed as the client is unable to reach the service
- Application launch failed as policy evaluation and config validation failed
- Application launch failed because of issues in application domain table
- Client closed the connection with Secure Private Access service
- Unable to resolve FQDN by the DNS server
- Unable to locate the application
- Failed to fetch configured application destinations list
- Application configuration issue
- Issue with resource location
- Enhanced security policy is bound to the HTTP application
- Host name length exceeds 256 characters
- Invalid IP address
- Unable to establish end-to-end connection
- IPv6 received in the app request
- UDP traffic failed to deliver
- UDP data traffic delivery failed
- Application launch failed due to network connectivity issues
- Connector Appliance failed to register to Secure Private Access service
- Connectivity issue with Connector Appliance
- Connectivity issues with Connector Appliance and back-end private TCP/UDP servers
- Connector Appliance fails to resolve DNS for FQDNs
- Private server connection terminated
- Failed to connect or send data to the private service IP or FQDN
- No matching policy condition
- No access policy associated with the application
- No application configuration found for the FQDN or the IP address
- App enumeration information
- TCP/UDP app launch failed as routing entry is missing in application domain table
- TCP/UDP app launch failed as connectors are not healthy
- UDP/DNS request failed as connector is unreachable
- Failed to load the page as the NGS cookie is expired
- Access policy fetch failed because of a network failure
- Access policy fetch failed while parsing the JSON web token
- Network failure to fetch access policy details
- Policy fetch failed while fetching the public certificate
- Policy fetch failed while validating signature of the JSON web token
- Policy fetch failed while validating the public certificate
- Failed to determine the store environment to form a policy URL
- Failed to get a response for access policy fetch request
- Access policy fetch failed due to an expired secondary DS auth token
- Connector Appliance is not registered
- Unable to connect to the Connector Appliance
- Connection to Citrix Secure Private Access service failed
- Proxy server is not reachable
- Proxy server authentication failed
- Configured proxy servers are not reachable
- Received error response from backend server
- Unable to send request to the target URL
- Failed to process SSO
- Connection to the Citrix Secure Private Access service failed
- Failed to process SSO, unable to determine SSO settings
- FormFill SSO failed, incorrect form app configuration
- Kerberos SSO failed
- Failed to process SSO for auth type
- Kerberos SSO failed but falling back to NTLM
- Multiple ZTNA entitled accounts configured in the Citrix Workspace application
- How to collect client logs
-
Answers to FAQs
- What are Secure Private Access diagnostic logs?
- Where do I find Secure Private Access logs?
- Which widget displays the Secure Private Access diagnostic logs?
- What details can I find in the Secure Private Access diagnostic logs?
- How do I filter the diagnostic logs?
- What events are captured in the Secure Private Access diagnostic logs?
- How do I use the Secure Private Access troubleshooting topic to resolve a failure that I have encountered?
- What is an info code? Where do I find them?
- What is a transaction ID? How do I use it?
- What are all the Secure Private Access PoP locations?
- What do I do if I am unable to resolve my failure using the info code and the error lookup table?
- References