Domain pass-through to Citrix Workspace using Azure Active Directory as the identity provider
You can implement single sign-on (SSO) to Citrix Workspace using Azure Active Directory (AAD) as an identity provider with Domain joined, Hybrid, and Azure AD enrolled endpoints/VMs.
With this configuration, you can also use Windows Hello to SSO to Citrix Workspace using AAD enrolled endpoints.
- You can authenticate to Citrix Workspace app using Windows Hello.
- FIDO2 based Authentication with the Citrix Workspace app.
- Single sign-on to Citrix Workspace app from Microsoft AAD joined machines (AAD as IdP) and conditional access with AAD.
To achieve SSO to virtual apps and desktops, you can either deploy FAS or configure Citrix Workspace app as follows.
Note:
You can achieve SSO to the Citrix Workspace resources only when using Windows Hello. However, you’re prompted for user name and password when accessing your published virtual apps and desktops. To solve this prompt, you can deploy FAS and SSO to virtual apps and desktops.
Prerequisites:
- Connect Azure Active Directory to Citrix Cloud. For more information, see Connect Azure Active Directory to Citrix Cloud in the Citrix Cloud documentation.
- Enable Azure AD authentication to access workspace. For more information, see Enable Azure AD authentication for workspaces in the Citrix Cloud documentation.
To achieve single sign-on to Citrix Workspace:
- Configure Citrix Workspace app with includeSSON.
- Disable
prompt=loginattribute in Citrix Cloud. - Configure Azure Active Directory pass-through with Azure Active Directory Connect.
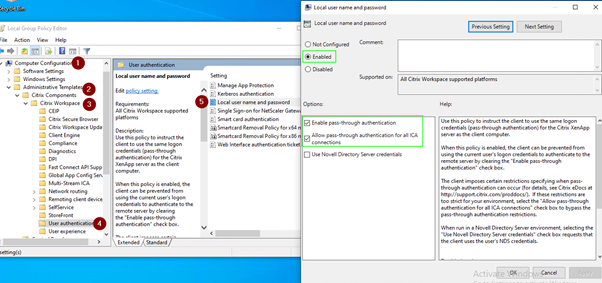
Starting with Citrix Workspace™ app for Windows version 2503, the system installs SSON by default in dormant mode. You can enable SSON post-installation using the Group Policy Object (GPO) policy. To enable, navigate to User Authentication > Local user name and password and select the Enable pass-through authentication checkbox.
Note:
You must reboot the system after updating the GPO policy for the SSON setting to take effect.
Configure Citrix Workspace app to support SSO
Prerequisites:
- Citrix Workspace version 2109 or higher.
Note:
If you’re using FAS for SSO, Citrix Workspace configuration isn’t needed.
-
Install Citrix Workspace app from administrative command line with option
includeSSON:CitrixWorkspaceApp.exe /includeSSON - Sign out from the Windows client and sign in to start the SSON server.
-
Click Computer configuration > Administrative templates > Citrix Components > Citrix Workspace > User Authentication to change Citrix Workspace GPO to allow Local username and password.
Note:
These policies can be pushed to the client device via Active Directory. This step is required only when accessing Citrix Workspace from the web browser.
-
Enable the setting as per the screenshot.
-
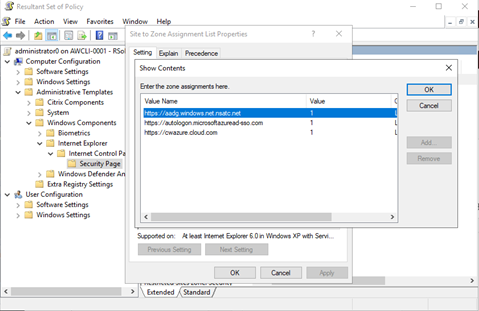
Add the following trusted sites via GPO:
https://aadg.windows.net.nsatc.nethttps://autologon.microsoftazuread-sso.com-
https://xxxtenantxxx.cloud.com: Workspace URL
Note:
Single sign-on for AAD is disabled when the AllowSSOForEdgeWebview registry in
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Citrix\Dazzleis set to false.
Disable prompt=login parameter in Citrix Cloud
By default prompt=login is enabled for Citrix Workspace that forces the authentication even if the user opted to stay signed in or if the device is Azure AD joined.
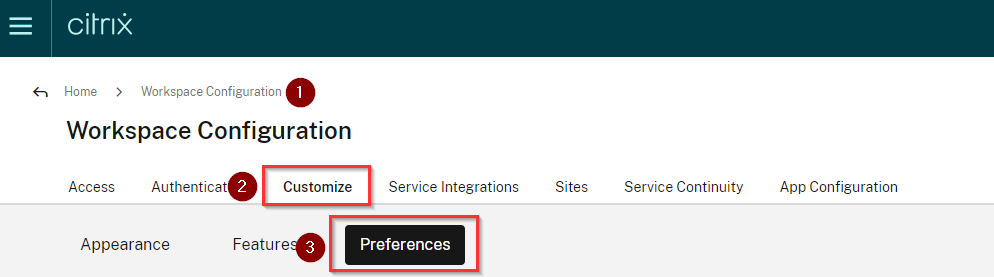
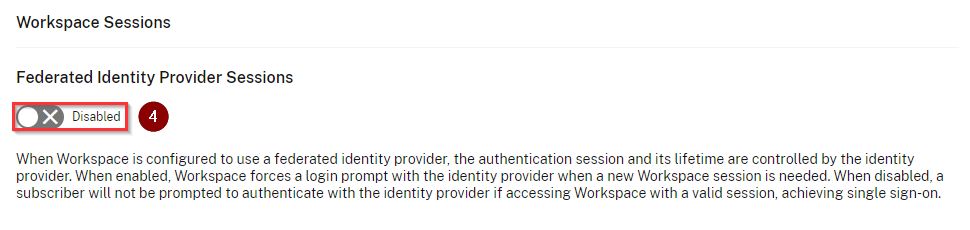
You can disable prompt=login in your citrix cloud account. Navigate to Workspace Configuration\Customize\Preferences-Federated Identity Provider Sessions and disable the toggle.
For more information, see Knowledge Center article CTX253779.
Note:
On AAD joined or hybrid AAD joined devices, if AAD is used as IdP for Workspace, then Citrix Workspace app doesn’t prompt for credentials. Users can automatically sign in using work or school account.
To allow users to sign in using different account, set the following registry to false.
Create and add a registry string REG_SZ with the AllowSSOForEdgeWebview name under
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Citrix\DazzleorComputer\HKEY_CURRENT_USER\SOFTWARE\Citrix\Dazzleand set its value as False. Alternatively, if users sign out from Citrix Workspace app, users can sign in with a different account on the next sign-in.
Configure Azure Active Directory pass-through with Azure Active Directory Connect
- If you’re installing Azure Active Directory Connect for the first time, on the User sign-in page, select Pass-through Authentication as the sign On method. For more information, see Azure Active Directory Pass-through Authentication: Quickstart in the Microsoft documentation.
-
If Microsoft Azure Active Directory Connect exists:
- Select the Change user sign-in task and click Next.
- Select Pass-through Authentication as the sign-in method.
Note:
You can skip this step if the client device is Azure AD joined, or hybrid joined. If the device is AD joined, domain pass-through authentication works using kerberos authentication.