Configure Workspace URLs
Overview
When you first enable Workspace, the system creates a Workspace URL of the form customername.cloud.com that can be used to access the Workspace from web browsers or locally installed Citrix Workspace app.
You can add additional cloud.com URLs. If you have defined multiple Workspace URLs, you can use these URLs as policy inputs. For example, you might want different branding, authentication methods, and resources for different divisions within your organization.
You can also use your own custom domain as an alias for your default cloud.com domain. For more information, see configure custom domain.
Store name
Each Workspace URL has a Store name. This name is displayed in the Accounts list within Citrix Workspace™ app.
You configure whether the user can modify the store name within Citrix Workspace app. To allow users to edit their store name from the Citrix Workspace app, users must be on the following versions of the Citrix Workspace app clients:
- Citrix Workspace app for Windows version 2405 or later
- Citrix Workspace app for iOS version 24.2.0 or later
- Citrix Workspace app for Mac version 2402
Enable or Disable Workspace URL
You can disable all access to your Workspaces for cloud.com URLs. This affects both locally installed Citrix Workspace app and browsers. Users can continue to use a Custom Workspace URL to access the default Workspace. If you do not have a Custom Workspace URL then this blocks all access.
To disable access via cloud.com:
- Untick Workspace URL enabled. This brings up a confirmation screen.
- Select the checkboxes to confirm you understand.
- Press Disable.
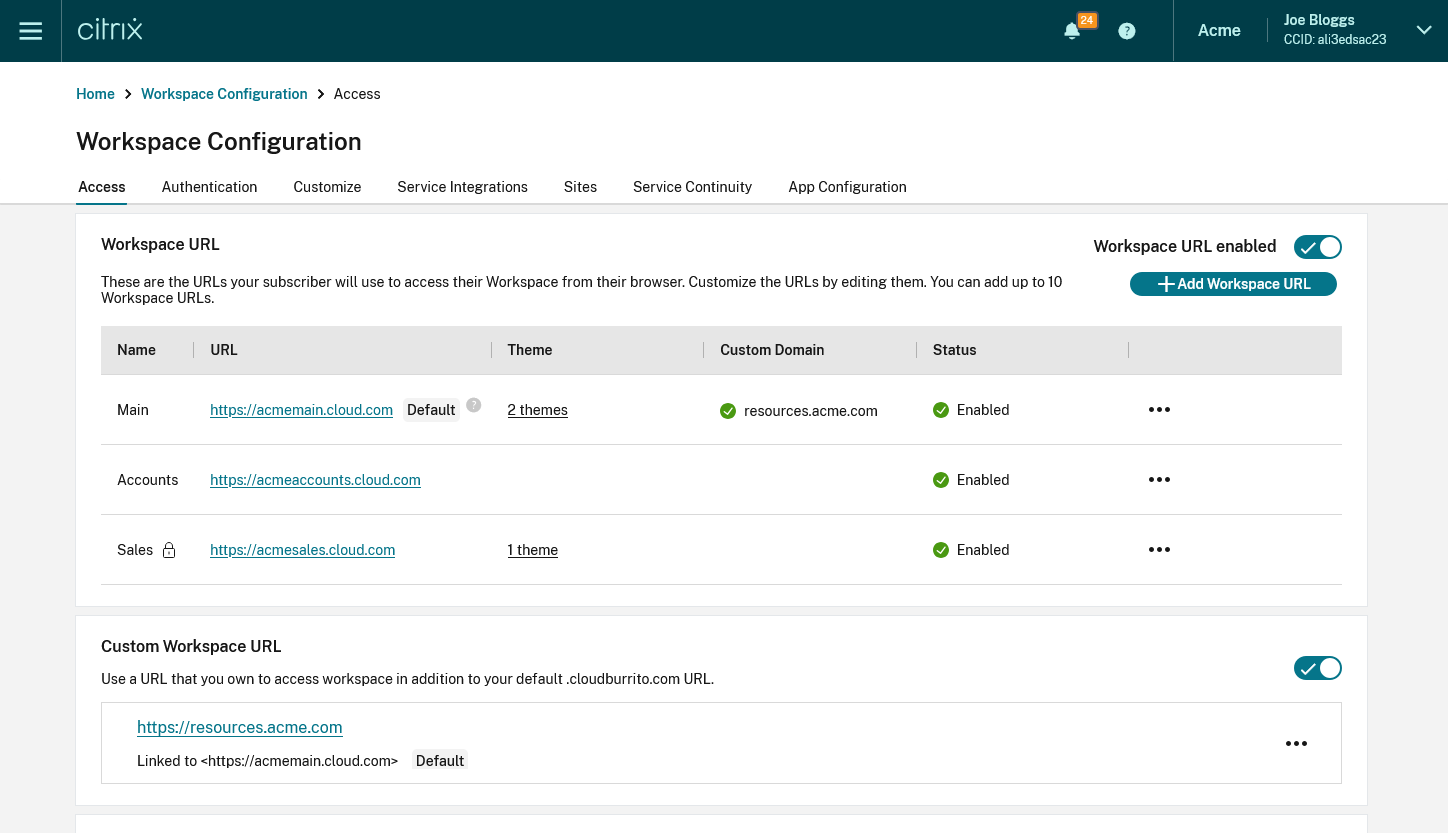
View URLs
- Go to Citrix Cloud™ and sign in with your credentials.
- Navigate to Workspace Configuration > Access. Under Workspace URL, you can find a list of existing URLs.
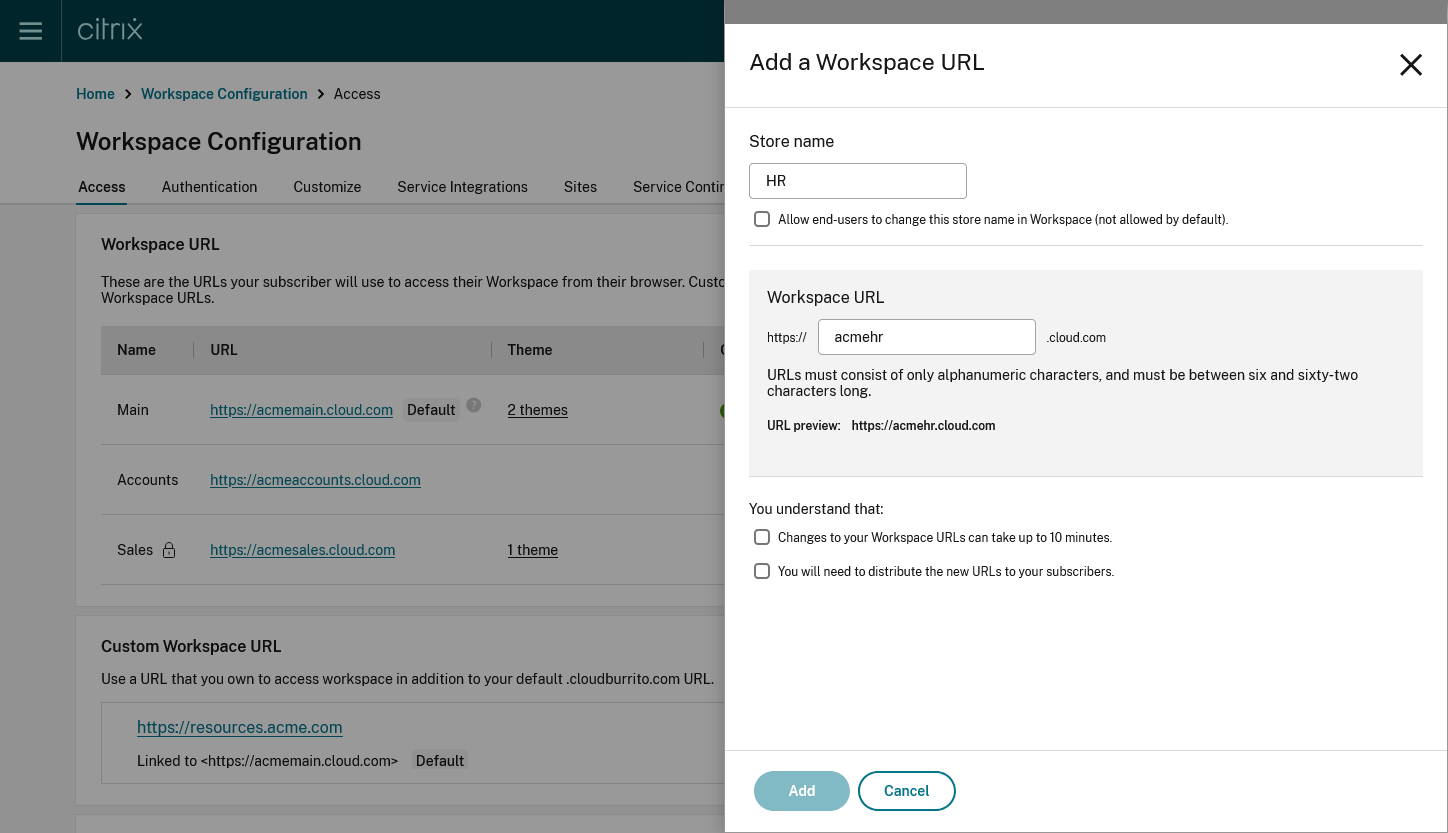
Add Workspace URLs
Select a unique workspace URL. Citrix Cloud rejects workspace URLs that other customers already use. Use a naming convention that contains a string unique to your organization. Avoid generic URLs such as workspace.cloud.com or mystore.cloud.com.
For example, you can create URLs using the following format:
YourOrgsales.cloud.comYourOrgengineering.cloud.comYourOrgmarketing.cloud.com
From the Access tab, to add a URL:
-
Click + Add Workspace URL
-
Enter a store name.
-
Choose whether you wish the user to be able to modify the store name within Citrix Workspace app.
-
Enter the subdomain.
-
Select the checkboxes as an acknowledgment that you must provide the new URLs to your end users post configuration.
-
Click Add to save the URL.
Note:
You can create up to 10 URLs by default. Contact your Citrix representative if you need more URLs.
Modify Workspace URL
Warning:
When you rename a URL, the old URL is immediately removed and is no longer available. Tell subscribers what the new URL is and manually update all local Citrix Workspace apps to use the new URL. The new URL will be unavailable for up to 10 minutes. If the URL is used in any policy then you must manually update that policy.
-
Click the … on the row of the Workspace URL you wish to edit.
-
Modify the Store name and Workspace URL as required.
-
If you modified the URL then you must tick several checkboxes to acknowledge that you understand the consequences.
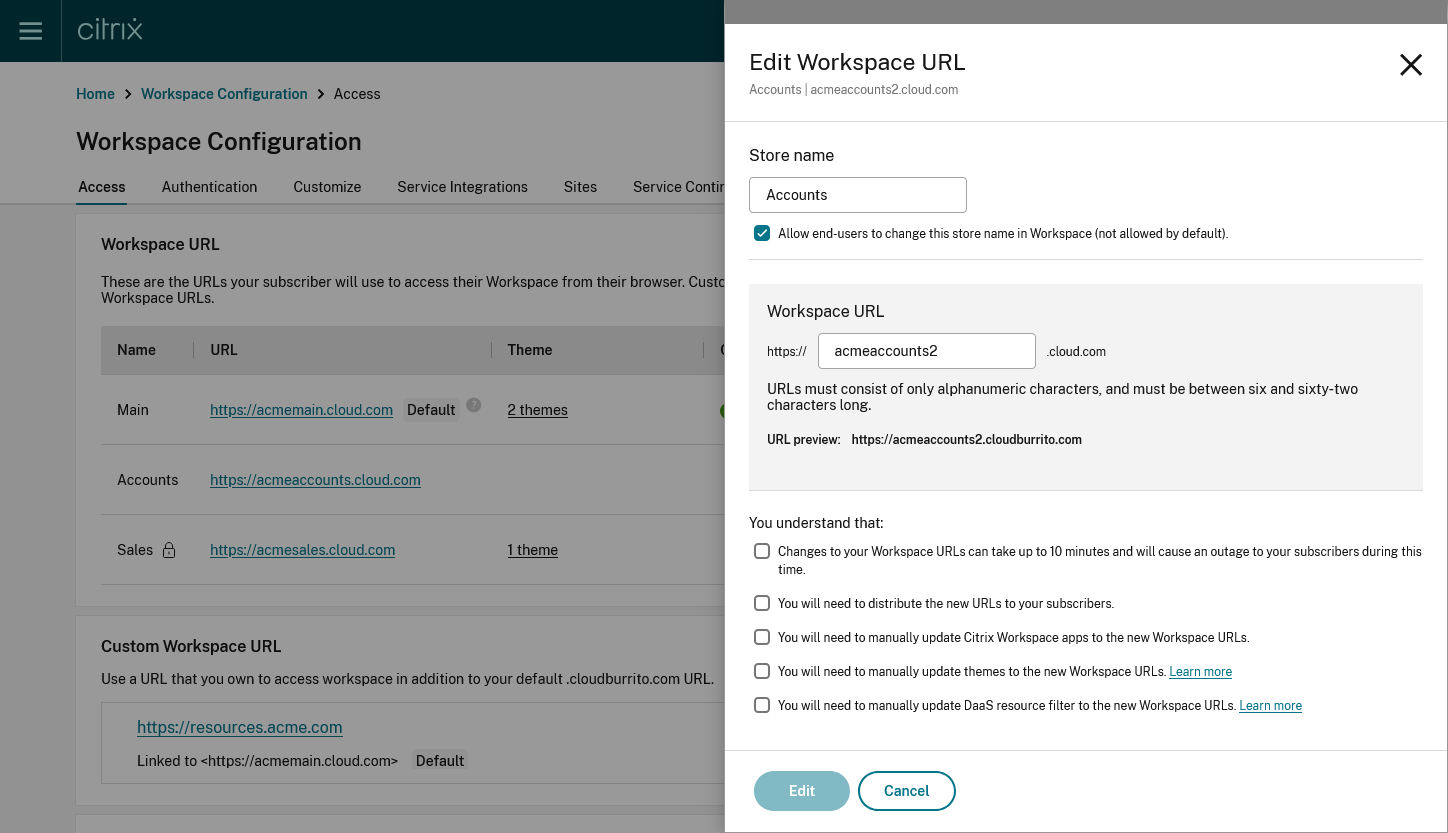
- Press Edit to save the changes
Configure Workspace URLs using PowerShell
You can also use the PowerShell API to add or change Workspace URLs.
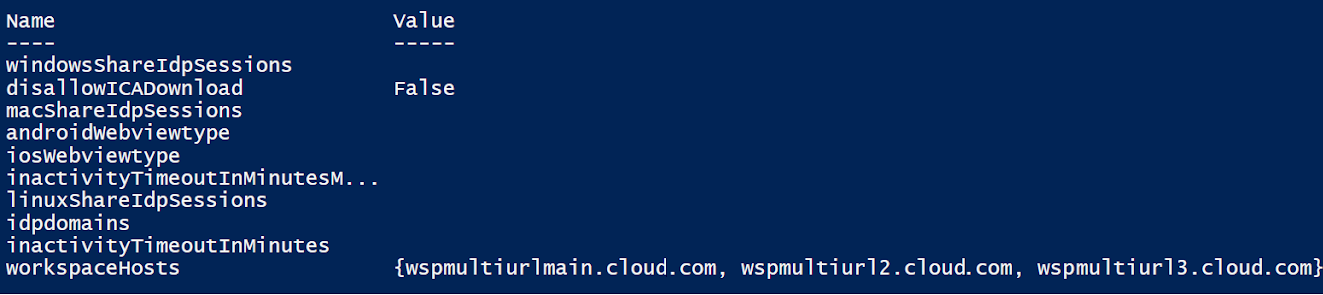
Run the cmdlet Set-WorkspaceCustomConfigurations with the $WorkspaceHosts list as the argument to the -WorkspaceHosts parameter to update the URL list for the workspace. Give the existing URL as the argument to the -WorkspaceUrl parameter. For example:
# Set a variable to the value of existing URL for the workspace.
$WSPURL = "wspmultiurlmain.cloud.com"
# Specify the new URLs that you want to create in a list, including any existing URLs.
$WorkspaceHosts = @($WSPURL,"wspmultiurl2.cloud.com","wspmultiurl3.cloud.com")
# Update the configuration
Set-WorkspaceCustomConfigurations -WorkspaceUrl $WSPURL `
-WorkspaceHosts $WorkspaceHosts `
-ClientId $APIClientID `
-ClientSecret $APIClientSecret `
-Verbose
<!--NeedCopy-->
Configure authentication methods
To configure different authentication methods per URLs:
- Create a conditional authentication profile.
- Add a Policy Condition of type Workspace URL and select the Workspace URL the condition should apply to.
- Choose the authentication method for that Workspace URL.
- Repeat for each Workspace URL.
- In the Workspace Configuration Authentication, choose the conditional authentication profile that you created.
Alternatively if you are using Adaptive Authentication, see Configure Adaptive Authentication policies.
Configure themes and logos
You can create and assign separate themes and logos for each workspace. For more information, see Appearance.
Resource filtering using Secure Private Access
While configuring Citrix DaaS™ with Secure Private Access, you can control the end user’s access to resources. You can implement this by configuring Access policies based on Workspace URLs. Access Policies can be configured for delivery groups using the Workspace URL filter.
For more information, see Citrix Secure Private Access
Send custom announcements
You can display a different custom announcement to your user depending on their Workspace URL. For more information, see Send custom announcements.
Resource Filtering resources from DaaS
You can configure Access Policies for delivery groups based on Workspace URLs. For more information, see Resource filtering using delivery group access policies.
Configure Adaptive Authentication policies
If you are using Adaptive Authentication, you can associate authentication policies with a Workspace URL. This enables you to configure different authentication policies for the end users based on the Workspace URL they’re using.
Step 1: Configure a series of authentication actions and policies that you want to use for the Workspace URLs. The policy configuration depends on the type of authentication and the authentication factors that you want to use. Any supported nFactor authentication flow can be used.
For more information, see Adaptive Authentication
For example, consider the following scenario where:
- The first URL
<https://wspmultiurlmain.cloud.com>must be mapped to LDAP authentication and OTP. - The second URL
<https://wspmultiurl2.cloud.com>must be mapped to LDAP authentication. - The third URL
<https://wspmultiurl3.cloud.com>must have End User Cert authentication
Examples:
Check for a particular Workspace URL using exact string matching.
AAA.USER.WSP.EQ("wspmultiurlmain.cloud.com")
<!--NeedCopy-->
Check whether a particular string is contained within a Workspace URL, using substring matching.
AAA.USER.WSP.CONTAINS("wspmultiurlmain")
<!--NeedCopy-->
Step 2: Configure an authentication policy and add your Workspace URL as the expression. The authentication policy is then valid for the Workspace URL that you entered in the Expression text field.
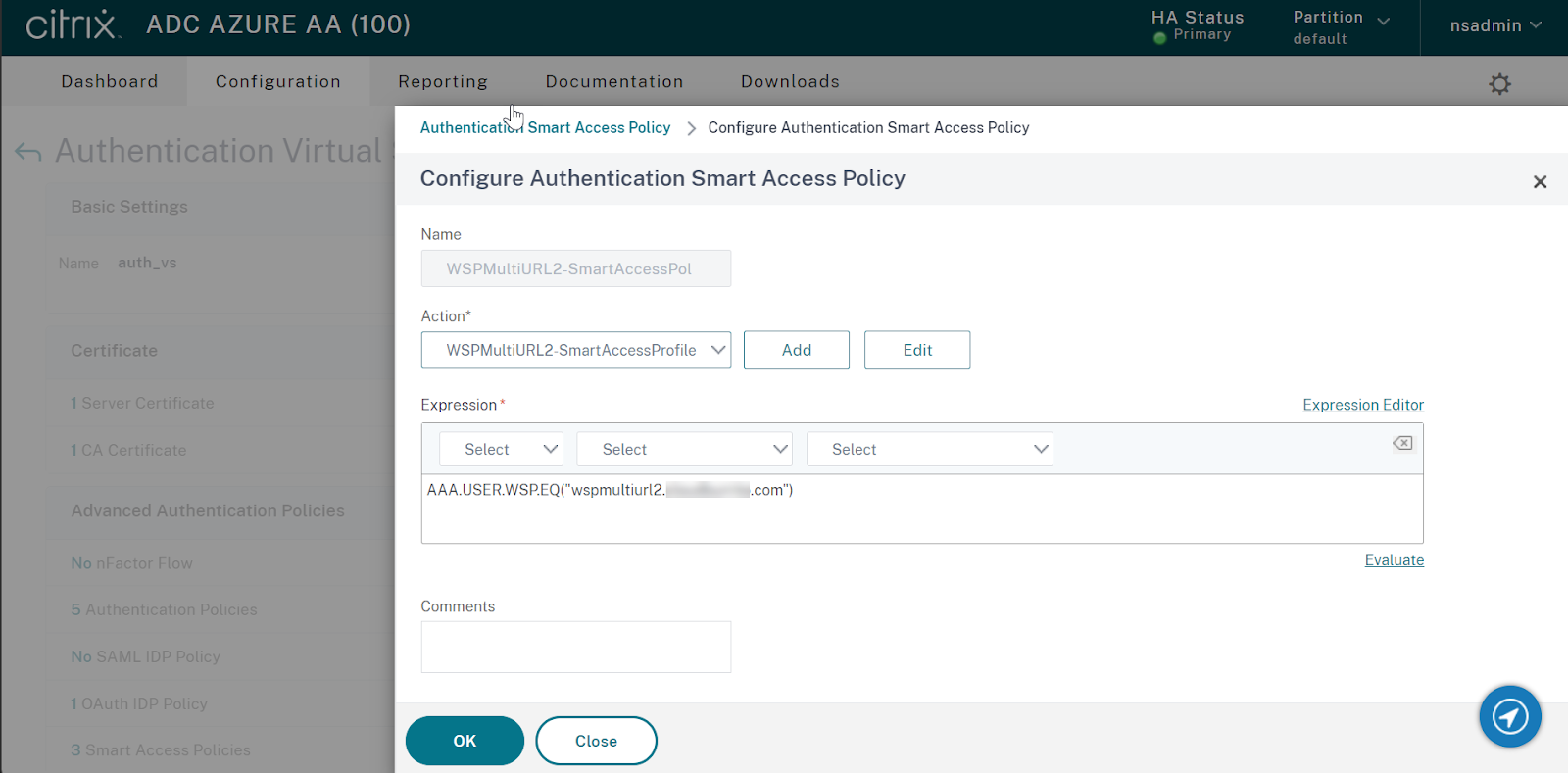
Step 3: Once you have configured authentication policies based on your URLs, you need to bind them to your authentication virtual server. For more information, see Authentication policies.
Email Discovery to add Workspace URLs to Citrix Workspace app
Email discovery adds all the Workspace URLs configured in the list of service URLs as stores. If you want to add two or more stores through email discovery, configure each Workspace URL as a service URL. It ensures that the URLs are added as stores during the email discovery process. You can use either of the following methods to add stores:
-
Global App Configuration service UI: For more info, see Configure settings for cloud store
-
Global App Configuration API: You can use the preceding portal to make an API call to POST /aca/discovery/app/workspace/domain using your registered domain For more info, see Global App Configuration service API.
If <user@yourdomain.com> is entered in the Citrix Workspace app, the Email Discovery service adds all stores listed in service URLs. You can use a UPN, or an email address when it contains the correct domain suffix mydomain.com.
Known limitations
The following are some limitations that impact the multiple URL feature.
Workspace Configuration
-
The workspace is limited to a single custom domain. It’s always linked to the Workspace URL marked as Default in the admin console.
-
You can’t disable individual URLs. If you disable a Workspace URL within the Citrix Cloud admin console, it disables all the configured URLs.
Citrix Virtual Apps and Desktops™
- Resource filtering using Workspace URL for Citrix Virtual Apps and Desktops (on-premises aggregation) isn’t supported.
Citrix Workspace app
To add multiple URLs from the same customer as stores, users must be on the following versions of the Citrix Workspace app clients:
- Citrix Workspace app for Windows version 2302 or later
- Citrix Workspace app for iOS version 2303 or later
- Citrix Workspace app for Android version 2303 or later
- Citrix Workspace app for Linux version 2303 or later
- Citrix Workspace app for Mac version 2305
- Citrix Workspace app for iOS version 2303
- Older versions of Citrix Workspace app display a Workspace domain selector menu. In this case, the end user must select the same URL they entered when adding the store. Selecting a different URL requires the user to sign in again.
Global App Configuration Service
- If the Global App Configuration service settings are configured for multiple Workspace URLs, then only one Workspace URL can be added to Citrix Workspace app at a time. Adding a second URL to Citrix Workspace app fails. For example, If GACS settings are configured for both
<https://wspmultiurlmain.yourdomain.com:443>and<https://wspmultiurl2.yourdomain.com:443>, then the user can add only one URL to Citrix Workspace app. - Account addition fails if more than one GACS configured URL is found during the Global App Configuration service discovery. For example, consider a case where a user enters
<user@yourdomain.com>in Citrix Workspace app. The domain-based discovery finds two results and GACS settings are configured for both of them. The response returned is:<https://wspmultiurlmain.yourdomain.com:443>and<https://wspmultiurl2.yourdomain.com:443>. In this case, account addition fails with Citrix Workspace app as it supports adding only one account with GACS settings configuration.
{
"items": [
{
"domain": {
"name": "yourdomain.com"
},
"app": {
"workspace": {
"serviceURLs": [
{
"url": "https://wspmultiurlmain.yourdomain.com:443"
},
{
"url": "https://wspmultiurl2.yourdomain.com:443"
},
{
"url": "https://wspmultiurl3.yourdomain.com:443"
}
]
}
}
}
],
"nextToken": "None",
"count": 1
}
<!--NeedCopy-->
In this article
- Overview
- Store name
- Enable or Disable Workspace URL
- View URLs
- Add Workspace URLs
- Modify Workspace URL
- Configure Workspace URLs using PowerShell
- Configure authentication methods
- Configure themes and logos
- Resource filtering using Secure Private Access
- Send custom announcements
- Resource Filtering resources from DaaS
- Configure Adaptive Authentication policies
- Email Discovery to add Workspace URLs to Citrix Workspace app
- Known limitations