Conditional Authentication
Conditional Authentication is a new security feature to help further enhance your Zero Trust framework. Conditional authentication allows Citrix Cloud™ admins to direct end users to different IdPs during the Workspace login flow based on policy conditions you set. As such, different end users will have different levels of access verification based on risk factors established by the Administrator.
At the time of writing, five different switching conditions are supported that will direct your end users to different IdP instances based on the policies you define.
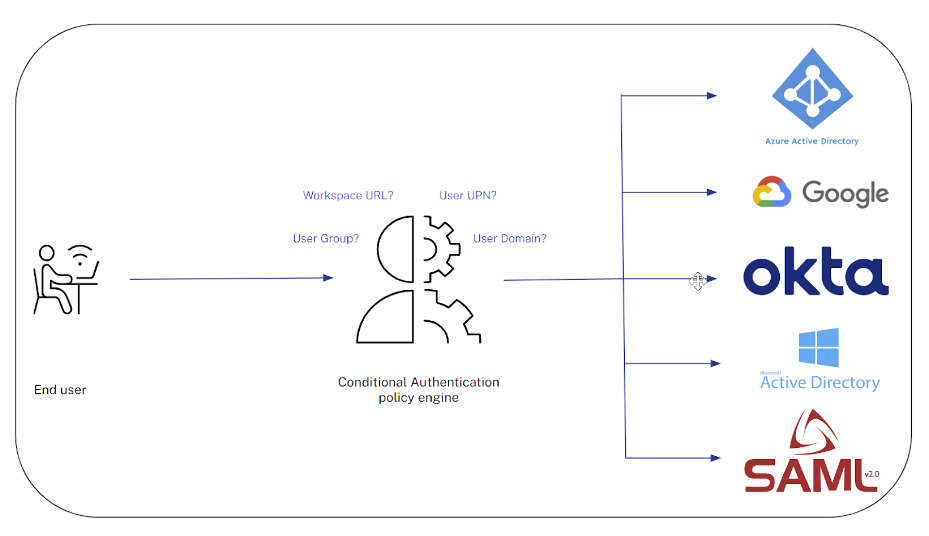
Common use cases
- Mergers and Acquisitions, where a large parent organization contains multiple smaller companies in the process of merging.
- Granting Workspace access to third party users and contractors by directing them to a dedicated IdP, OIDC application or SAML application, which is different from what full time employees within your organization are normally authorized to use.
- Large Organizations with multiple branches or departments that require different authentication mechanisms.
Prerequisites
- Two or more Identity providers created in Citrix Cloud Identity and Access Management page
Multi-IdP
Till now, only a single instance of an Identity type was allowed. Citrix® now supports adding multiple instances of the same Identity provider type (for example, multiple Azure ADs can now be added under the Identity and Access Management tab).
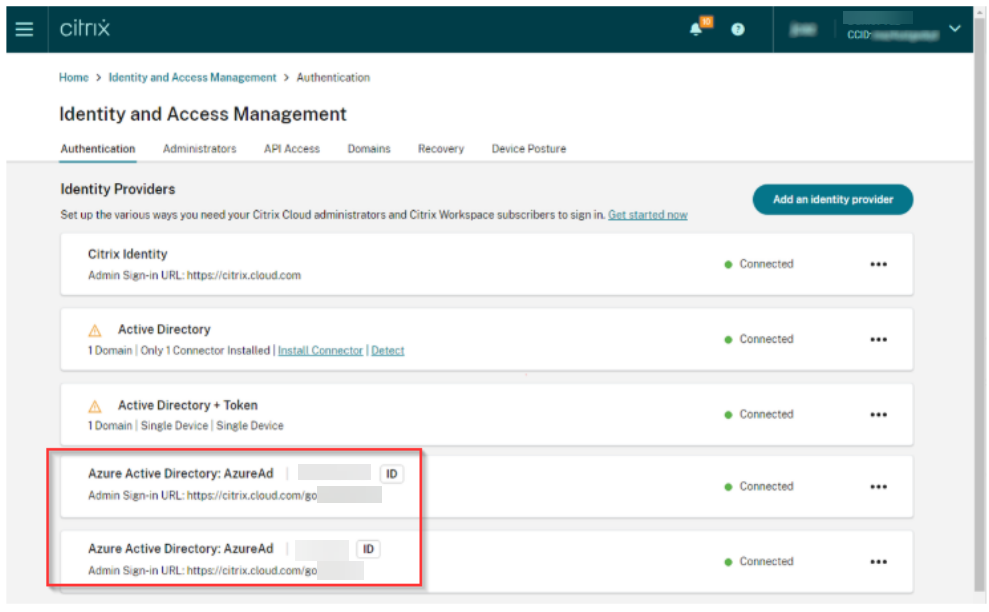
Important:
While DaaS and SPA currently support multiple IdPs, some services are still working on implementing this functionality and will be available shortly.
Configuring Conditional Authentication
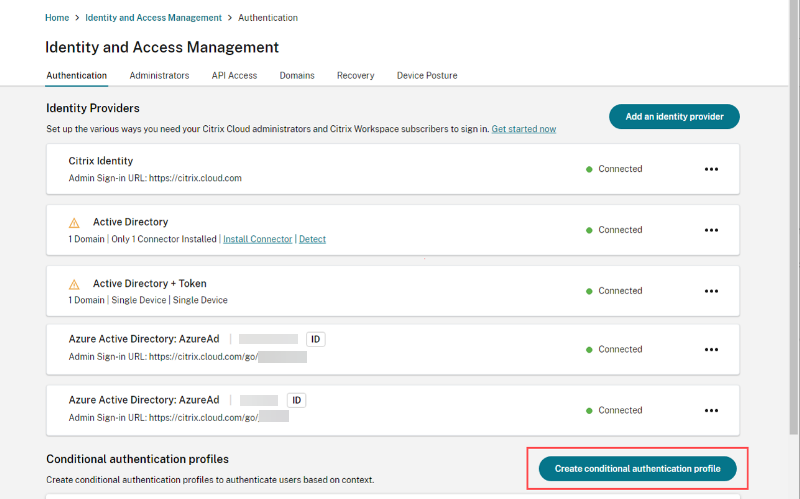
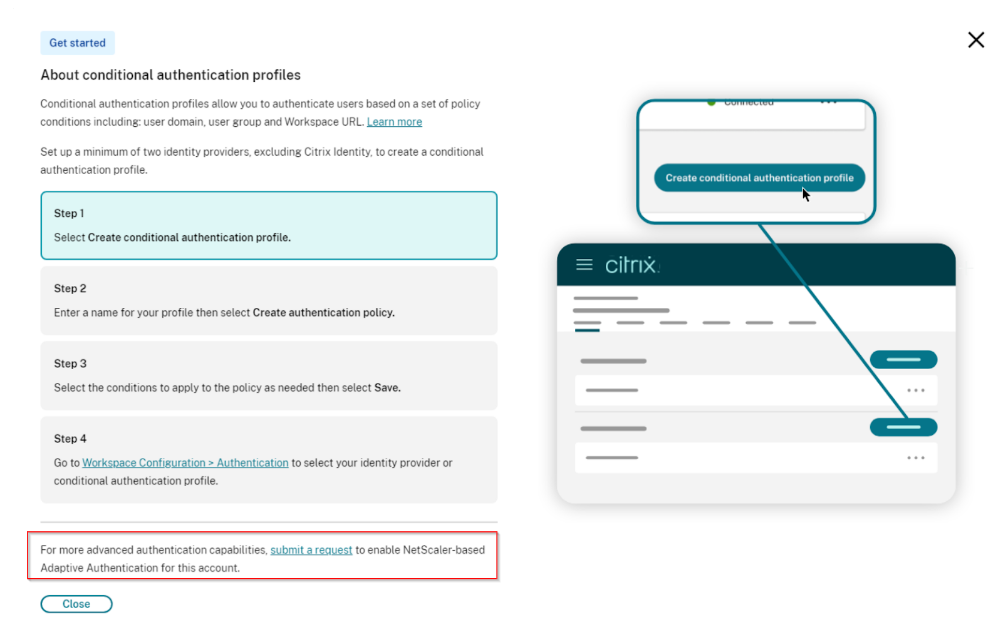
-
Click Create conditional authentication profile.
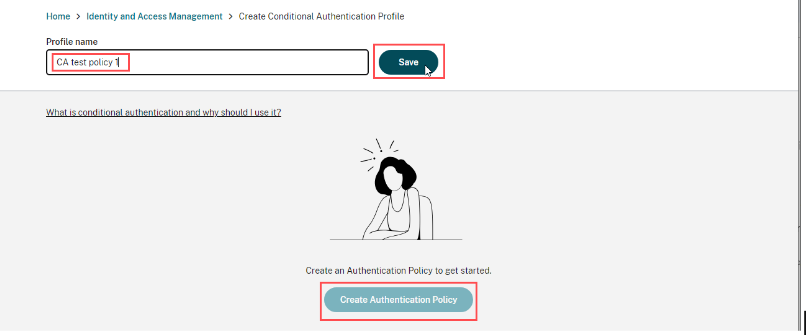
-
Enter a name for your profile and then click Create authentication policy.
-
Select the conditions to apply to the policy as needed then click Save.
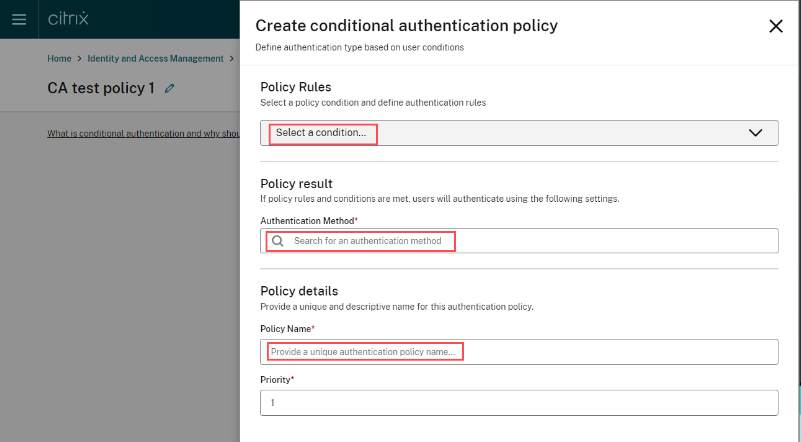
-
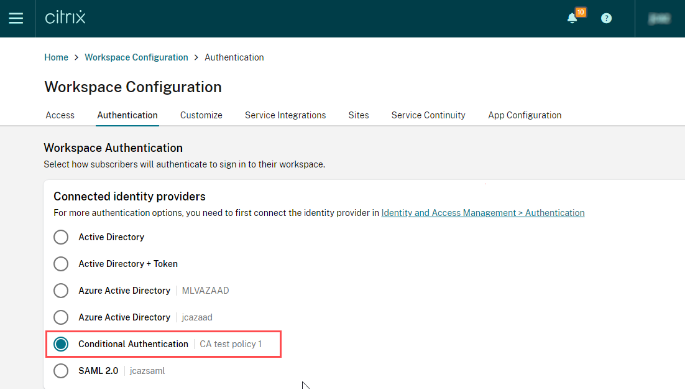
Navigate to Workspace Configuration and click Authentication to select your identity provider or conditional authentication profile.
Conditional Authentication concepts
Conditional Authentication Profile
A Conditional Authentication Profile consists of several Conditional Authentication Policies that controls how your end users authenticate to Workspace depending on the conditions you define. This profile allows for policy prioritization and reordering, enabling you to specify the sequence in which policies should be evaluated.
Conditional Authentication Policy
A Conditional Authentication Policy is a policy comprising one or more conditions. These conditions, when met using AND logic, guide the end user’s login process to a specific target IdP instance, such as Okta OIDC, SAML, or Gateway IDP connection. Individual policies can be cloned, allowing for modification and renaming as needed.
Each policy consists of the following data:
- Policy Rules which are one or more conditions that must be met to direct the end user to a particular IdP instance. For example, Workspace URL 1 is used AND user is a member of AD Group1.
- Policy Result which is the target IdP instance the user is directed to during the logon process. For example, Workspace URL 1 is used AND user is a member of AD Group1 → AAD SAML IDP Instance.
- Policy Name - which is an admin friendly name used to identify and describe the policy.
For example,
Workspace URL 1 AND Group1 - AAD SAML. - Policy Priority which determines the order in which the policy is evaluated. Priorities are evaluated in descending order. For example: Priority 1 is higher than Priority 2.
Conditional Authentication Pre-Authentication Page
Depending on how your Workspace is configured and the conditions set in your conditional authentication profile, your Workspace users might encounter a pre-authentication page during their login process. This page is essential for capturing the Workspace user’s username format, which is crucial for making decisions based on conditional authentication policies. It ensures that the user’s login flow is directed to the appropriate IdP instance.

Login Auto-Fill
When a pre-authentication page is necessary, we’ve introduced a login auto-fill feature that automatically populates the username field on the login page with the user’s input from the pre-authentication page. This eliminates the need for users to enter their username twice.
The login auto-fill feature is administered and configured by the administrator in the Conditional Authentication Profile settings, as illustrated below:
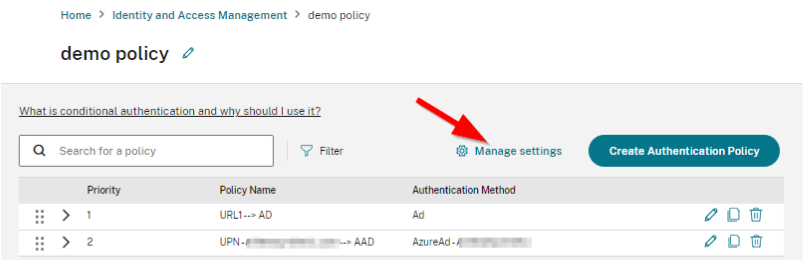
-
Click Manage settings in the Conditional Authentication profile page.
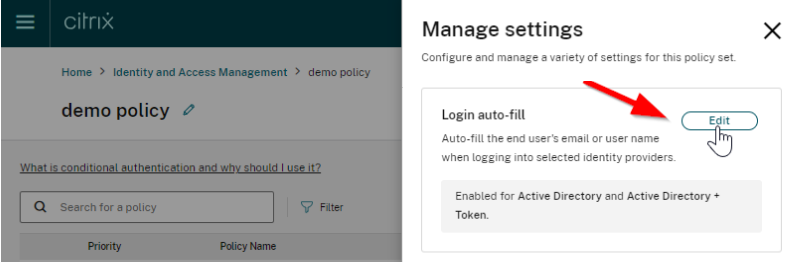
-
Click Edit
-
Select the IdPs you would like to enable Login auto-fill for.
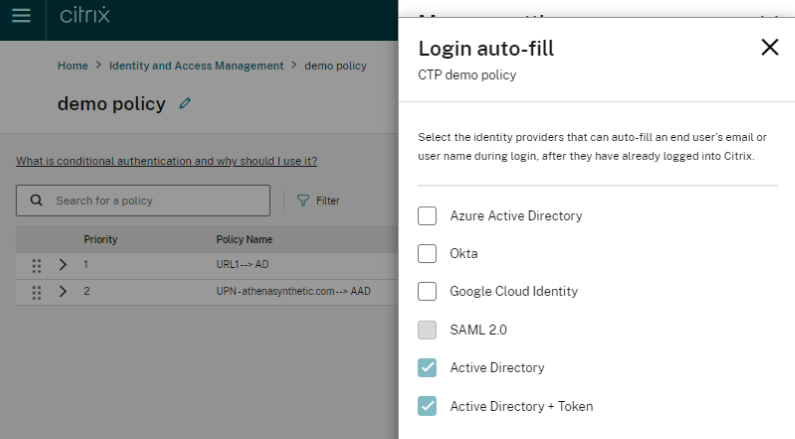
Important:
Login auto-fill is only available for IdPs that support it and will be enabled and enforced by default for AD & AD+TOTP (see screenshot above for the default settings).
Certain IdPs expect a specific login format and some can support more than one type of username format. For example, Google CIoud Identity requires users to login with their email address (
user.name@domain.com), which may sometimes be different from their UPN (username@domain.com). If the Workspace end user enters a down-level logon name (domain\username) in the pre-authentication page, the down-level logon name will be pre-populated within the IdP login page username field and cause an error when the user attempts to logon. Administrators should consider the IdP switching policy condition that is most appropriate and which username formats a particular IdP is expecting to receive during the logon process before configuring the login auto-fill feature.
Policy Condition Types
Note:
If a Conditional Authentication profile only contains policies of just Workspace URL condition type or Network Location Name condition type, then no pre-authentication page will be displayed and users will be redirected straight to the IdP. If the profile contains any other policy condition types, the pre-authentication page will be displayed to the end user. This is true even if the matching policy is of Workspace URL or Network Location Name type.
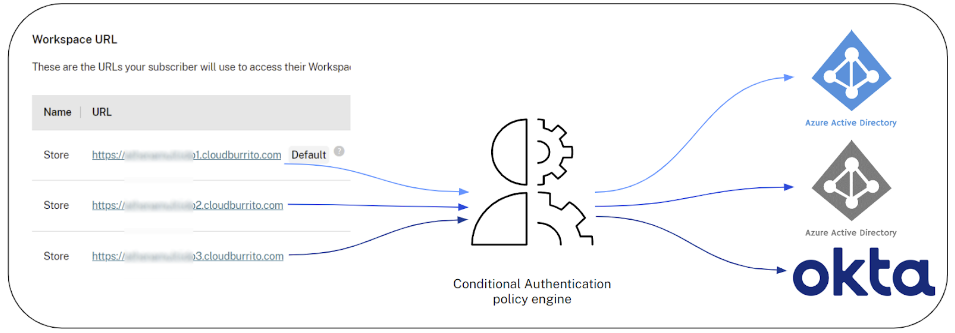
Workspace URL
Within Workspace Configuration > Access, each Workspace URL can be linked to a distinct IdP instance. Furthermore, multiple Workspace URLs can be associated with the same policy, directing your end users to the same IdP instance.
AD user group membership
AD user group membership allows you to designate an IdP instance for a specific group of Active Directory users based on their group membership.
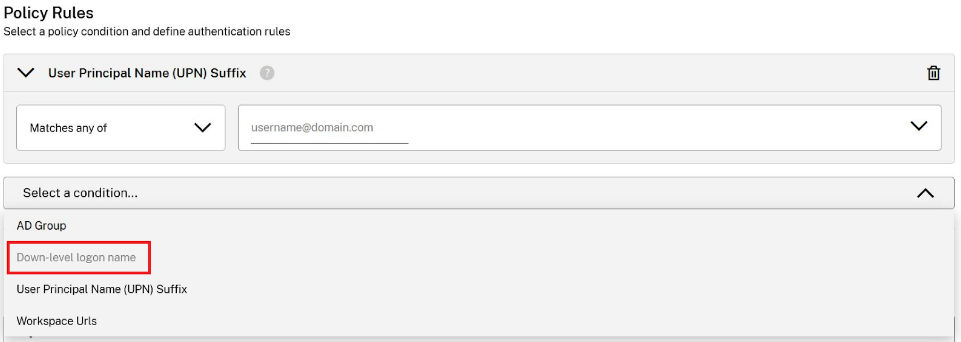
UPN Suffix or Domain Down-Level Logon Name are two mutually exclusive policy conditions. These determine the required username format that your end users must enter into the pre authentication page. You cannot use both of these conditions within the same policy.
UPN Suffix
Configure an IdP instance for one or more UPN suffixes, such as username1@domain.com or username2@domain.net.
Domain Down-Level Logon Name
Assign an IdP instance to one or more domain names, like DOMAIN1\username1 or DOMAIN1.COM\username1.
When one of the two mutually exclusive conditions is selected, the dropdown menu option for the other condition is disabled to prevent it from being added to the same policy.
Network Location Name
Assign an IdP instance based on client public egress IP and network location name.
-
Create the appropriate Network locations.
-
Within your Conditional authentication profile, the location names will be pre-populated. Select the desired location name and assign a target IdP.
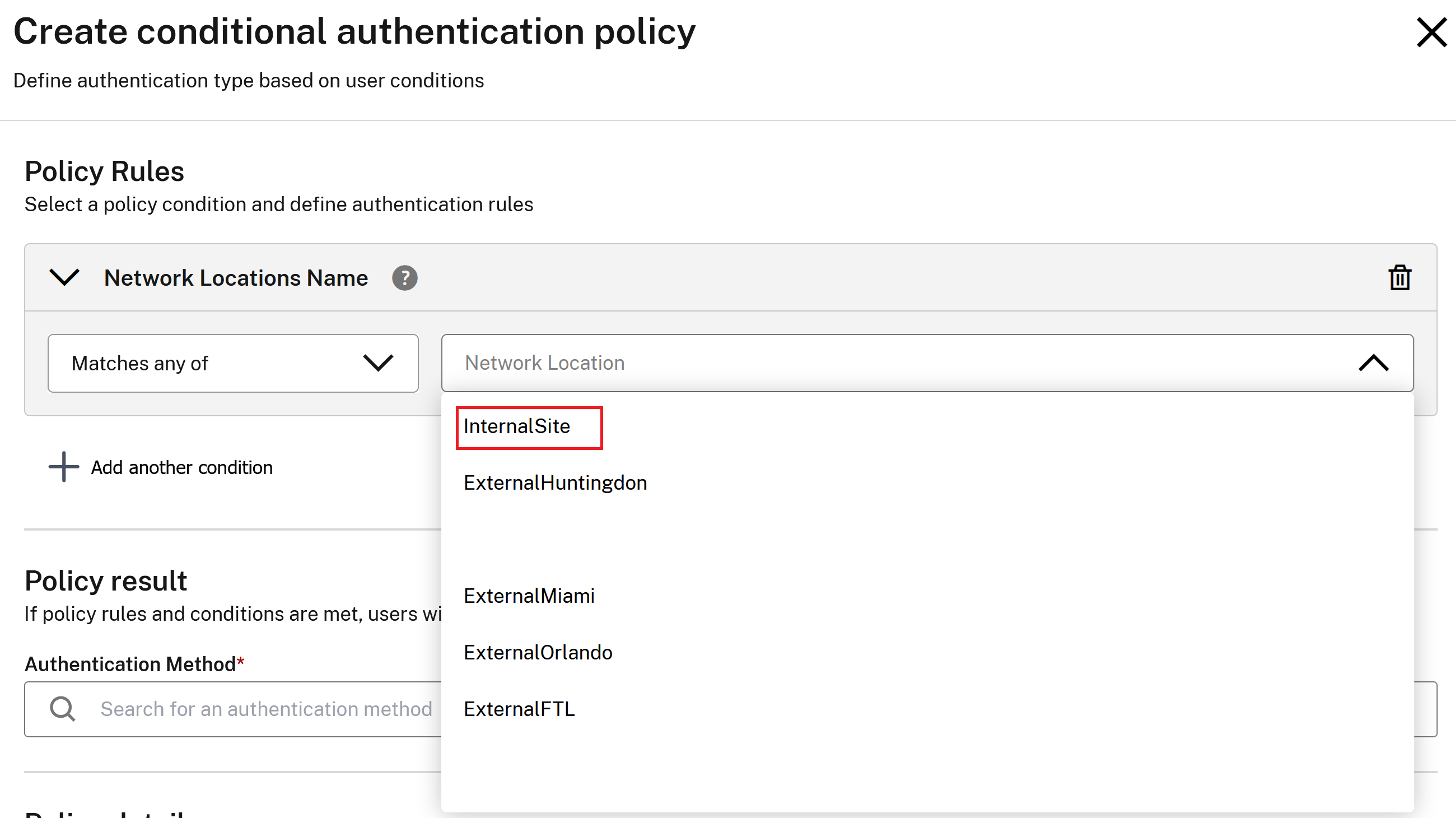
IMPORTANT:
Any client egress IP not explicitly defined inside a Network Location Site AND NOT referenced by a Network Location Name policy is classified as “undefined”.
Common NLS use cases / configuration:
-
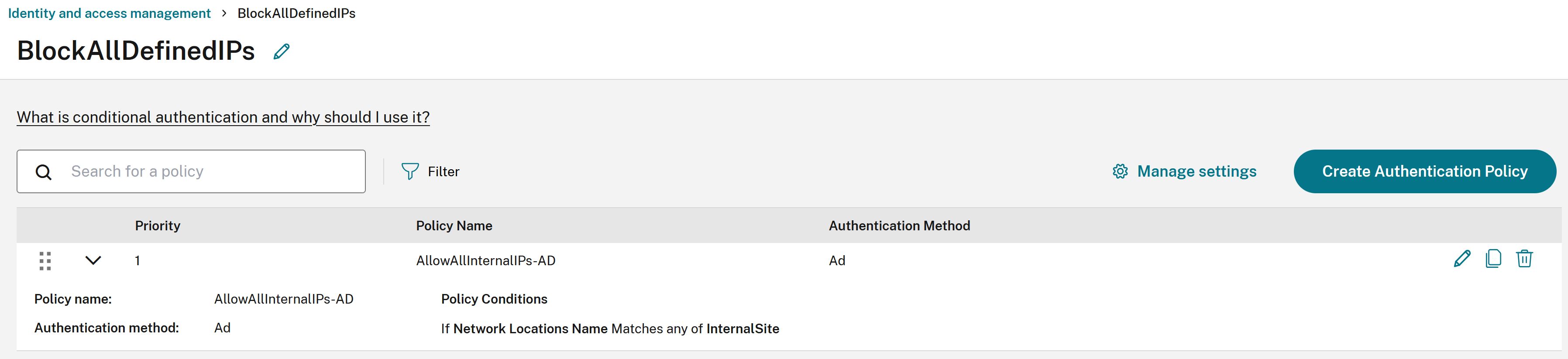
NLS Scenario 1: Block external (undefined) IPs from authenticating and accessing Workspace.
Policy1: Only internal clients with egress IPs defined inside the AllInternalIPs NLS site can log into Workspace using AD.
-
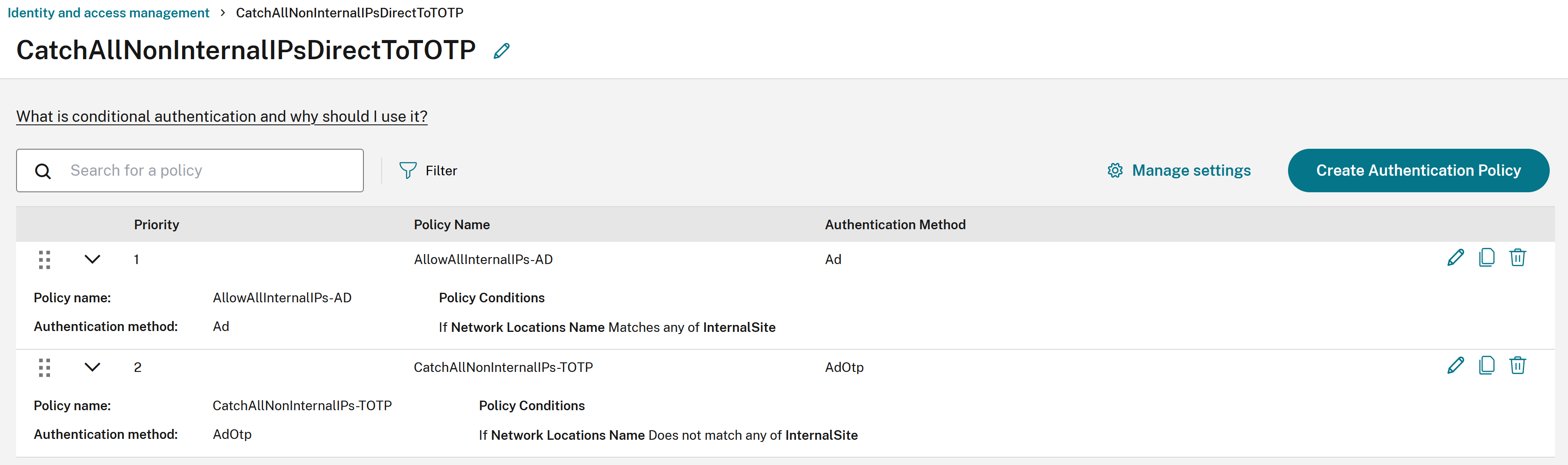
NLS Scenario 2: Direct all “undefined” egress IPs to the “catch all Idp instance” with extra authentication factors and/or increased security. Define a “catch all undefined egress IPs” policy using “Does not match any of” and a list of all your internal NLS sites.
Policy1: Only internal clients with egress IPs defined inside the AllInternalIPs NLS site can log into Workspace using AD.
Policy2: Any external egress IPs NOT defined inside the AllInternalIPs NLS site must log into Workspace using TOTP.
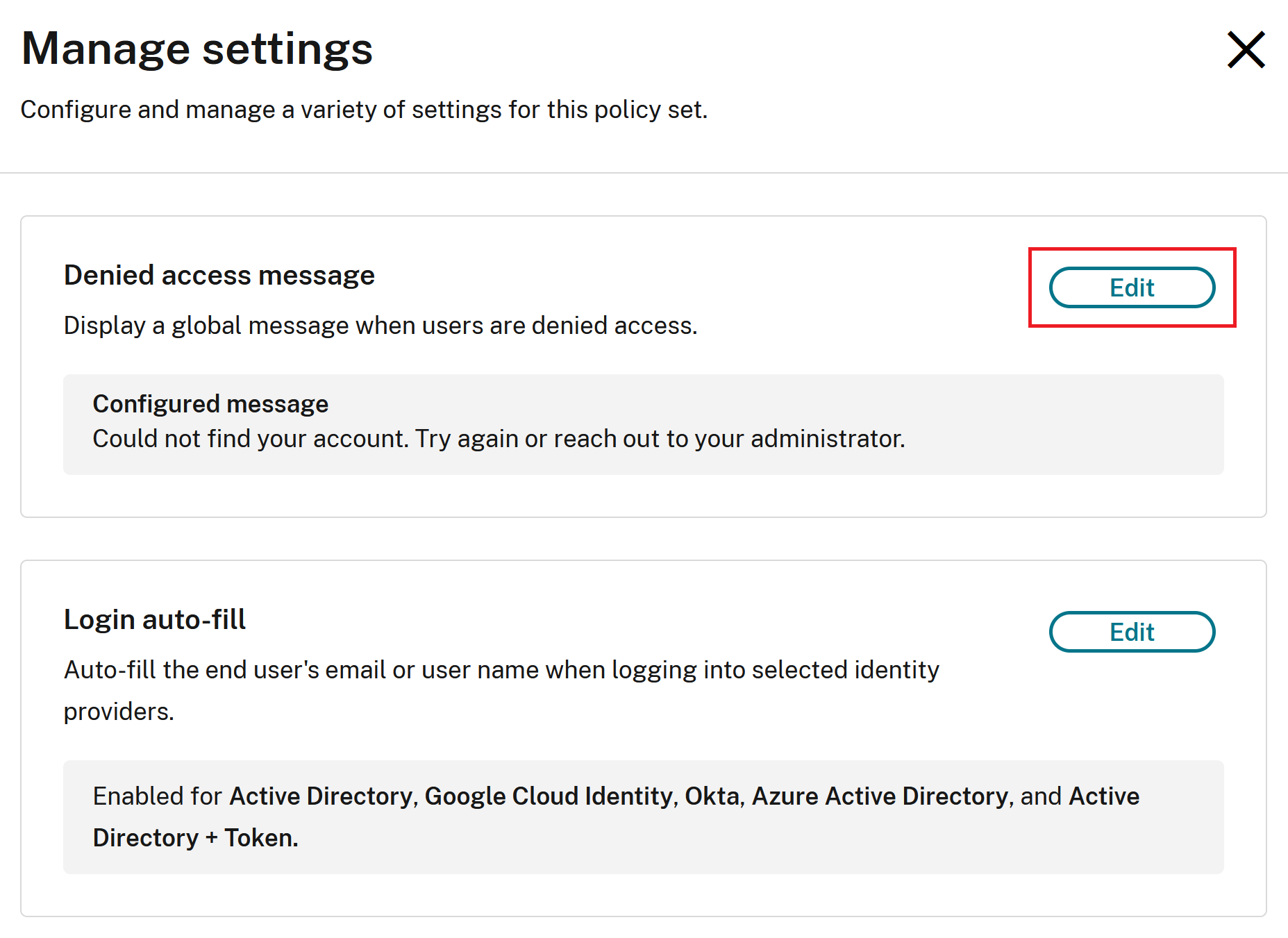
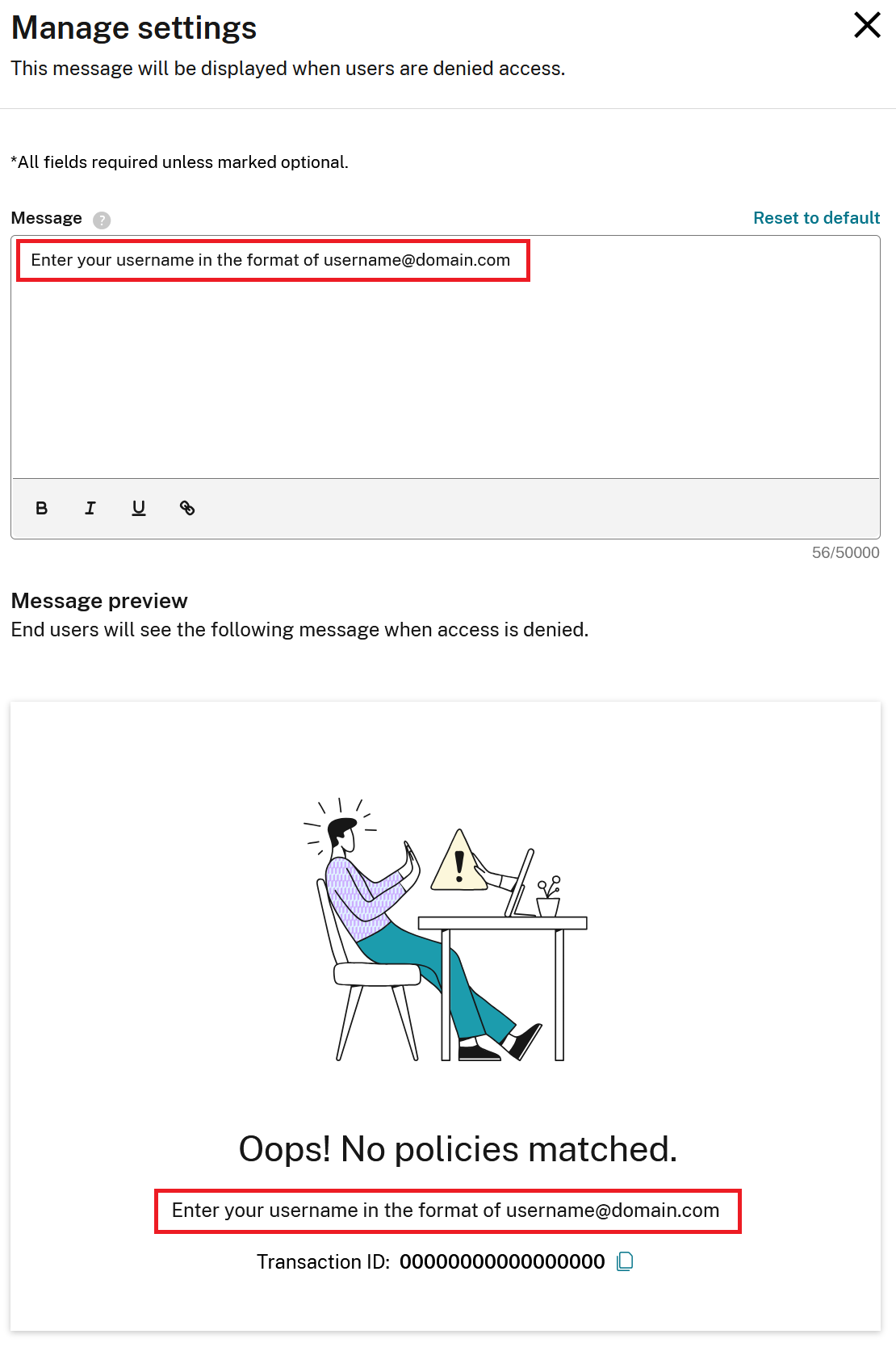
Setting a Custom Error Message for a Conditional Authentication Profile
It is possible to configure user friendly error messages which are shown to the Workspace end user when none of your policy conditions match what the user has entered.
-
Within your Conditional Authentication profile, select Manage settings.

-
Edit the default error message to be displayed to your end users.
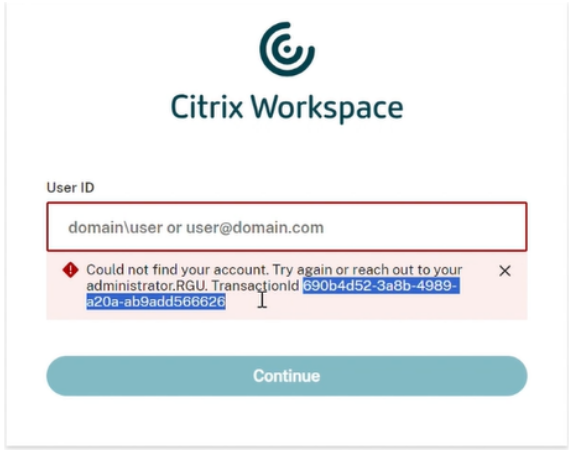
Troubleshooting with the Citrix monitor integration
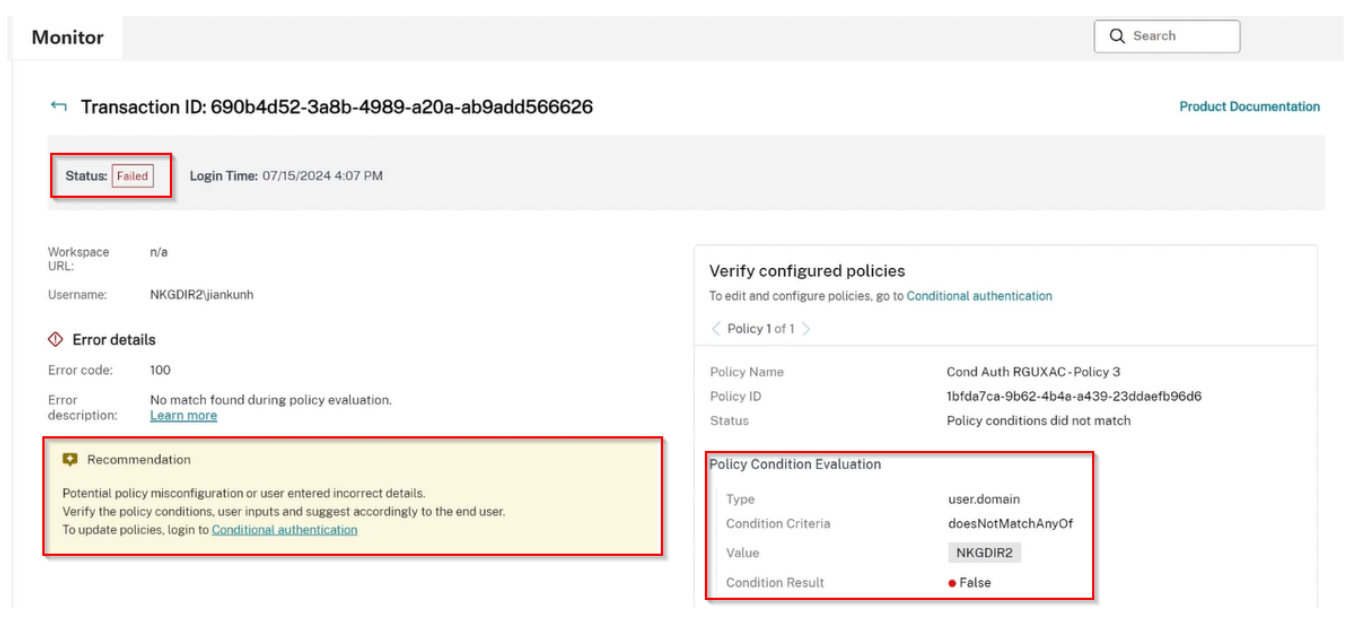
If a user’s login attempt fails due to a lack of matching policy, an error page is displayed, showing a transaction ID. The user can then provide this transaction ID to their Citrix Cloud administrator for further assistance.
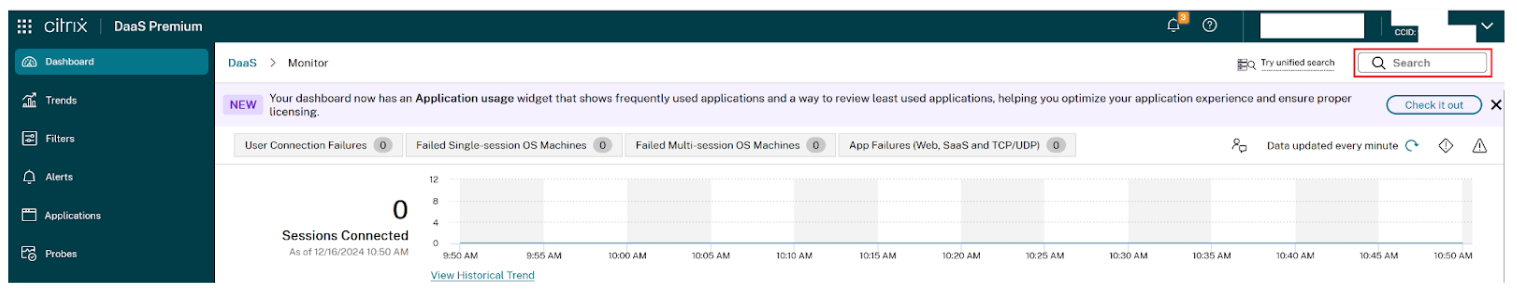
The Citrix Cloud administrator can paste the transaction ID provided by the Workspace end user into Citrix Monitor to access details about the policy, the entered username, and the associated Conditional Authentication policies. This information helps the administrator troubleshoot and resolve the Conditional Authentication issue more efficiently.
-
Select Monitor and then click the Search box in the top-right hand corner.
-
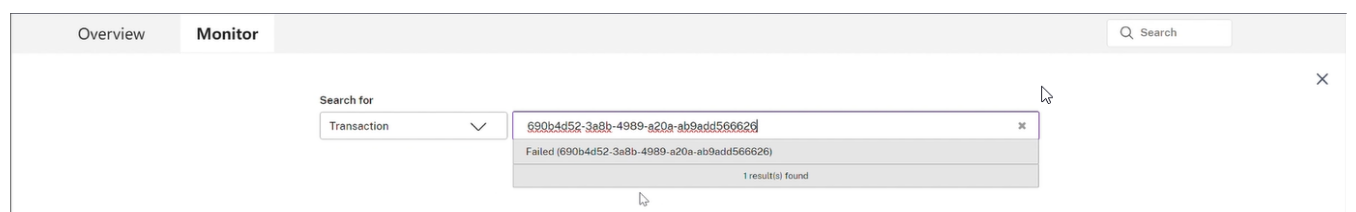
Select the Transaction ID from the dropdown list. Only transactions from the past 3 days are available.
-
View the failed transaction for the end user, along with the details of the Conditional Authentication policies that were evaluated. You can click the chevron buttons to navigate through all the evaluated policies such as <Policy 1 of 3> for the end user.
Comparison between Cloud-native Conditional Authentication and Netscaler-based Adaptive Authentication
The Cloud-native Conditional Authentication feature is designed to cover most conditional authentication use cases. However, for more advanced authentication capabilities, NetScaler-based Adaptive Authentication is available.
To use NetScaler-based Adaptive Authentication, submit a request through the Citrix Cloud Identity and Access Management page > Conditional Authentication profiles section.
Known issues and limitations
- Custom domains are not currently supported with Conditional Authentication. It is a roadmap item for future updates.
- Setting a negative priority to a policy does not behave as expected. Will be addressed in future updates.
- Currently, groups conditions are only supported for Active Directory. The native Entra Id group conditions will be added in the future.
In this article
- Common use cases
- Prerequisites
- Multi-IdP
- Configuring Conditional Authentication
- Conditional Authentication concepts
- Conditional Authentication Pre-Authentication Page
- Login Auto-Fill
- Policy Condition Types
- Setting a Custom Error Message for a Conditional Authentication Profile
- Troubleshooting with the Citrix monitor integration
- Comparison between Cloud-native Conditional Authentication and Netscaler-based Adaptive Authentication
- Known issues and limitations