Securing StoreFront with HTTPS
Citrix strongly recommends securing communications between StoreFront and users’ devices using HTTPS. This ensures that passwords and other data sent between the client and StoreFront are encrypted. Furthermore, plain HTTP connections can be compromised by various attacks, such as man-in-the-middle attacks, particularly when connections are made from insecure locations such as public Wi-Fi hotspots. In the absence of the appropriate IIS configuration, StoreFront uses HTTP for communications.
Depending on your configuration, users may access StoreFront via a gateway or load balancer. You can terminate the HTTPS connection at the gateway or load balancer. However in this case Citrix still recommends that you have secure connections between the gateway, load balancer and StoreFront using HTTPS. When using a NetScaler load balancer, for certificate requirements, see the link Server certificate support matrix on the ADC appliance.
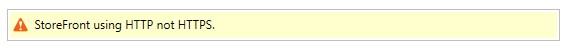
If StoreFront is not configured for HTTPS it displays the following warning:
Create or import certificate
-
Ensure that the StoreFront base URL is included in the DNS field as Common Name or Subject Alternative Name (SANs). When using a load balancer in front of your StoreFront servers, it is recommended that you include both the server FQDN and the load balancer FQDN as SANs. This allows you to connect directly to a specific StoreFront server for troubleshooting.
-
Sign the certificate using an enterprise root CA for your organization or a public CA.
-
If users access StoreFront via a load balancer or gateway, then the certificate only needs to be trusted by the load balancer or gateway. If users connect directly to the StoreFront server then the clients must trust the certificate.
You must create or import a certificate into the Personal certificate store within Windows. To view installed certificate:
- Open IIS Information Services (IIS) Manager.
- In the Connections pane, select the server.
- Open Server Certificates.
For more information on managing certificates, see Manage certificates.
Configure IIS for HTTPS
To configure Microsoft Internet Information Services (IIS) for HTTPS on the StoreFront server:
-
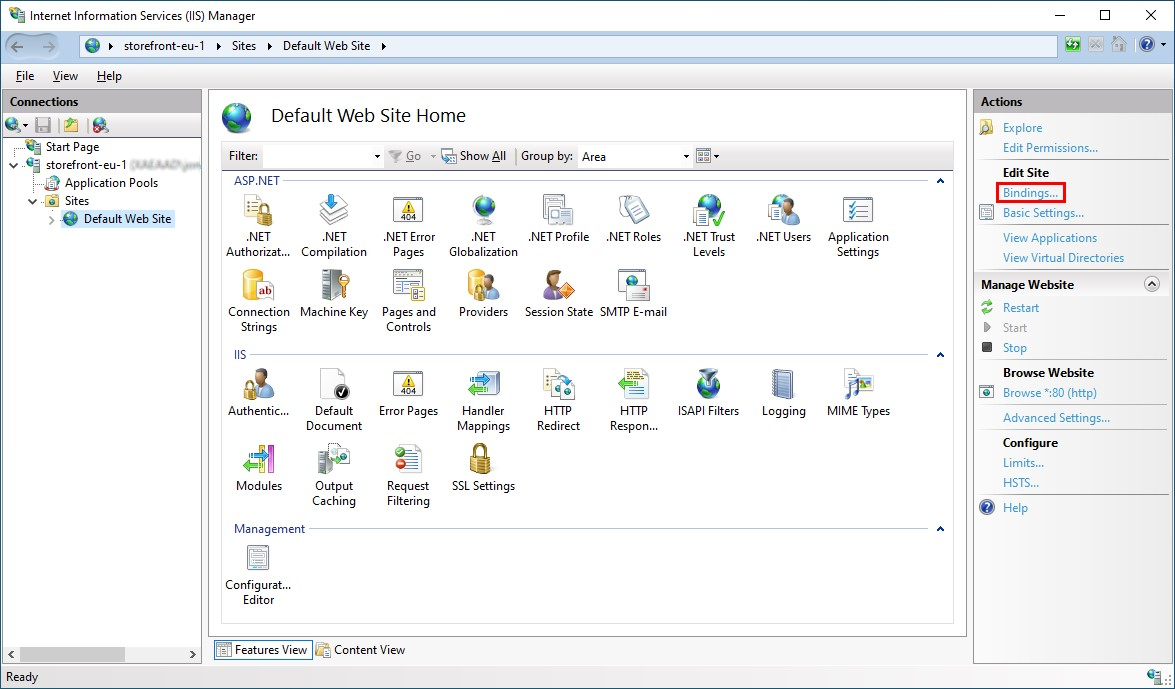
In the tree view on the left select Default Web Site (or the appropriate website)
-
In the Actions pane click Bindings…
-
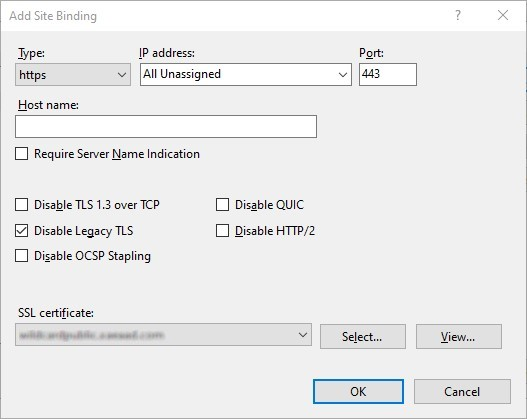
In the bindings window click Add…
-
In the Type drop down select https
-
On Windows Server 2022 or above, click Disable Legacy TLS to disable TLS older than 1.2.
On older Windows Server versions, you can disable legacy TLS versions using Windows registry settings, see Windows Server Documentation.
-
Select the certificate previously imported. Press OK
-
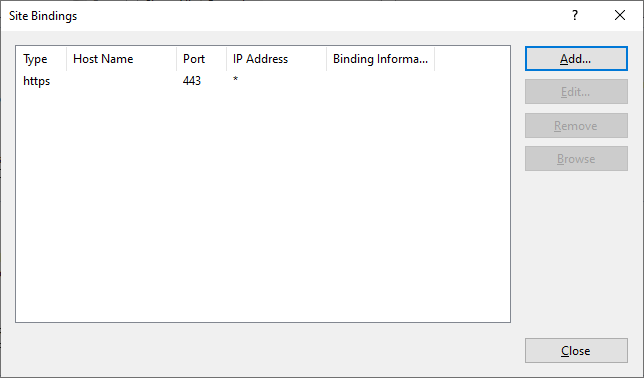
To remove HTTP access, select HTTP and click Remove.
-
Update the base url to use the https protocol.
HSTS
The user’s client device is vulnerable even after you enable HTTPS on the server side. For example, a man-in-the-middle attacker could spoof the StoreFront server and trick the user into connecting to the spoof server over plain HTTP. They could then get access to sensitive information such as the user’s credentials. The solution is to ensure that the user’s browser doesn’t attempt to access the server over HTTP. You can achieve this with the HTTP Strict Transport Security (HSTS).
When HSTS is enabled, the server indicates to web browsers that requests to the web site should only ever be made over HTTPS. If a user attempts to access the URL using HTTP, the browser will automatically switch to using HTTPS instead. This ensures client-side validation of a secure connection as well as the server-side validation in IIS. The web browser maintains this validation for a configured period.
Note:
Enabling HSTS affects all web sites on the same domain. For example, if the website is accessible at
https://www.company.com/Citrix/StoreWeb, then the HSTS policy will apply to all web sites underhttps://www.company.com, which might not be desired.
There are a number of options for enabling HSTS.
Option 1 - IIS
On Windows Server 2019 and above you can configure HSTS in IIS.
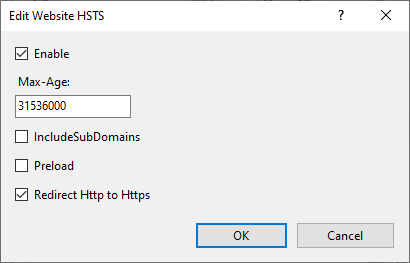
- Open Internet Information Services (IIS) Manager.
- Select Default Web Site (or the appropriate website).
- In the Actions pane on the right hand side, click HSTS….
- Select Enable.
- Enter a max age, e.g. 31536000 for one year.
- Optionally select Redirect HTTP to HTTPS.
- Press OK
Option 2 - StoreFront™ management console
For each store website:
- Select the store and click Manage websites.
- Select the website and click Configure…
- Go to the Advanced Settings tab
- Select Enable strict transport security.
- Update Strict transport security policy duration to the required value.
- Click OK.
Option 3 - NetScaler® load balancer
If you are using a NetScaler load balancer in front of your StoreFront servers then you can configure HSTS on the virtual server. For more information, see NetScaler documentation.