Passcode device policy
You create a passcode policy in XenMobile based on your organization’s standards. You can require passcodes on users’ devices and can set various formatting and passcode rules. You can create policies for iOS, macOS, Android, Samsung Knox, Android Enterprise, and Windows desktop/tablet. Each platform requires a different set of values, which are described in this article.
To add or configure this policy, go to Configure > Device Policies. For more information, see Device policies.
iOS settings
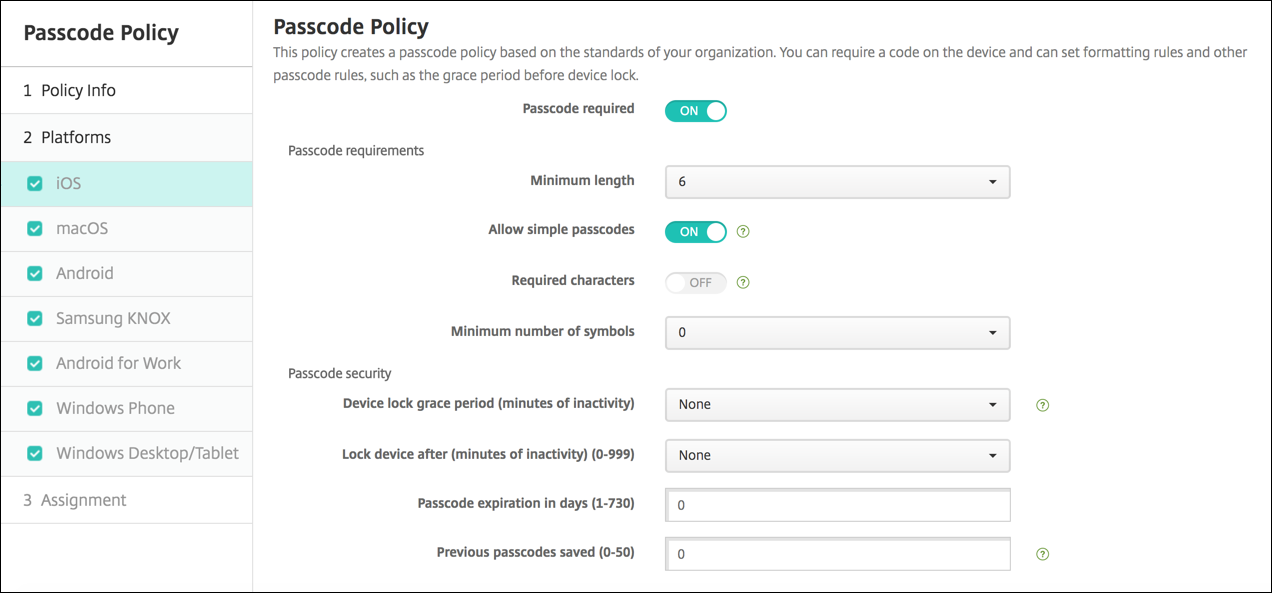
- Passcode required: Select this option to require a passcode and to display the configuration options for an iOS passcode device policy. The page expands to let you configure settings for passcode requirements, passcode security, and policy settings.
-
Passcode requirements
- Minimum length: Click the minimum passcode length in the drop-down list. The default is 6.
- Allow simple passcodes: Select whether to allow simple passcodes. Simple passcodes are a repeated or sequential set of characters. The default is On.
- Required characters: Select whether to require passcodes to have at least one letter. The default is Off.
- Minimum number of symbols: In the list, click the number of symbols the passcode must have. The default is 0.
-
Passcode security
- Device lock grace period (minutes of inactivity): In the list, click the length of time before users must enter a passcode to unlock a locked device. The default is None.
- Lock device after (minutes of inactivity): In the list, click the length of time a device can be inactive before it is locked. The default is None.
- Passcode expiration in days (1-730): Type the number of days after which the passcode expires. Valid values are 1–730. The default is 0, which means the passcode never expires.
- Previous passwords saved (0-50): Type the number of used passwords to save. Users are unable to use any password found in this list. Valid values are 0–50. The default is 0, which means users can reuse passwords.
- Maximum failed sign-on attempts: In the list, click the number of times a user can fail to sign in successfully after which the device is fully wiped. The default is Not defined.
macOS settings
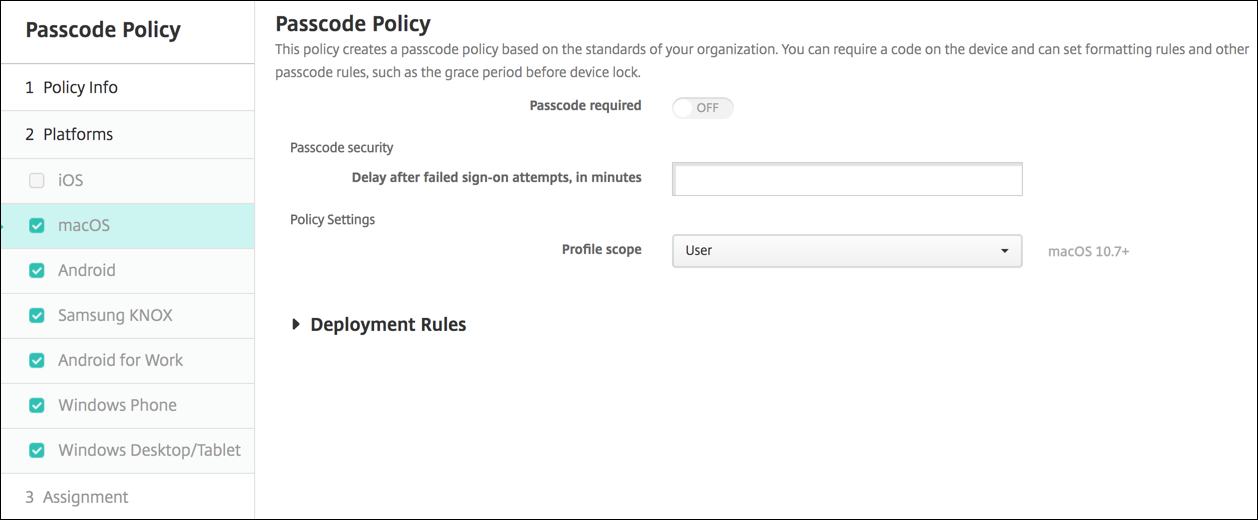
- Passcode required: Select this option to require a passcode and to display the configuration options for an iOS passcode device policy. The page expands to let you configure settings for passcode requirements, passcode security, and policy settings.
- If you do not enable Passcode required, next to Delay after failed sign-on attempts, in minutes, type the number of minutes to delay before allowing users to reenter their passcodes.
- If you enable Passcode required, configure the following settings:
-
Passcode requirements
- Minimum length: In the list, click the minimum passcode length. The default is 6.
- Allow simple passcodes: Select whether to allow simple passcodes. Simple passcodes are a repeated or sequential set of characters. The default is On.
- Required characters: Select whether to require passcodes to have at least one letter. The default is Off.
- Minimum number of symbols: In the list, click the number of symbols the passcode must have. The default is 0.
-
Passcode security
- Device lock grace period (minutes of inactivity): In the list, click the length of time before users must enter a passcode to unlock a locked device. The default is None.
- Lock device after (minutes of inactivity): In the list, click the length of time a device can be inactive before it is locked. The default is None.
- Passcode expiration in days (1-730): Type the number of days after which the passcode expires. Valid values are 1–730. The default is 0, which means the passcode never expires.
- Previous passwords saved (0-50): Type the number of used passwords to save. Users are unable to use any password found in this list. Valid values are 0–50. The default is 0, which means users can reuse passwords.
- Maximum failed sign-on attempts: In the list, click the number of times a user can fail to sign in successfully after which the device is locked. The default is Not defined.
- Delay after failed sign-on attempts, in minutes: Type the number of minutes to delay before allowing a user to reenter a passcode.
- Force passcode reset: The next time a user authenticates, they must reset their passcode.
-
Policy settings
- Profile scope: Select whether this policy applies to a User or an entire System. The default is User. This option is available only on macOS 10.7 and later.
Android settings
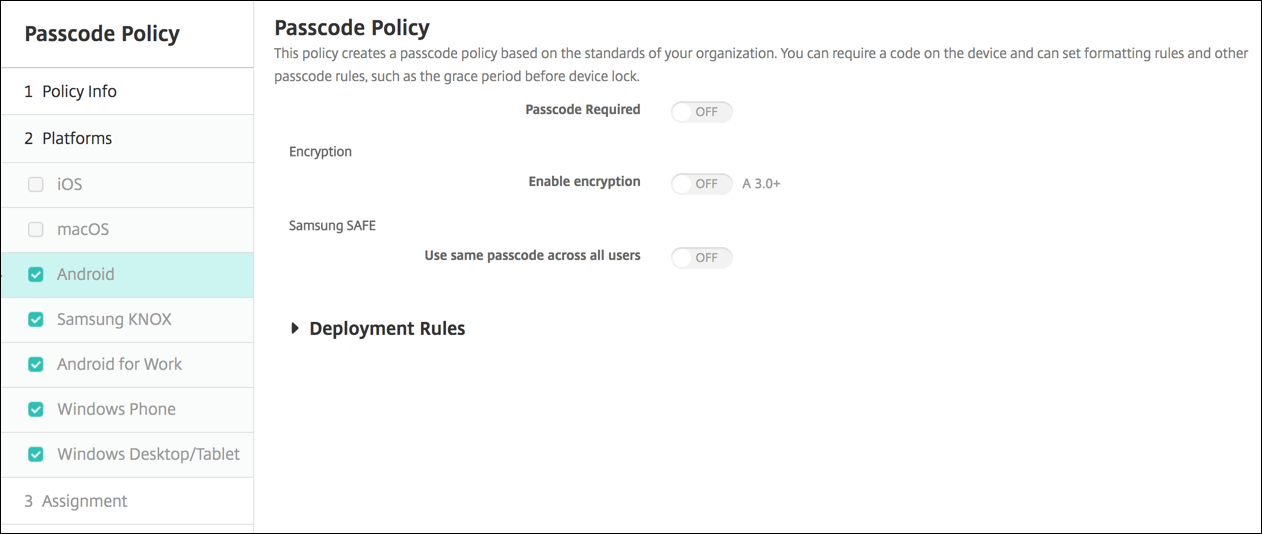
Note:
The default setting for Android is Off.
- Passcode required: Select this option to require a passcode and to display the configuration options for an Android passcode device policy. The page expands to let you configure settings for passcode requirements, passcode security, encryption, and Samsung SAFE.
-
Passcode requirements
- Minimum length: Select the minimum passcode length in the drop-down list. The default is 6.
- Biometric recognition: Select whether to enable biometric recognition. If you enable this option, the Required characters field is hidden. The default is Off.
- Required characters: Select No Restriction, Both numbers and letters, Numbers only, or Letters only in the drop-down list to configure how passcodes are composed. The default is No restriction.
- Advanced rules: Select whether to apply advanced passcode rules. This option is available for Android 3.0 and later. The default is Off.
- When you enable Advanced rules, from each of the following lists, click the minimum number of each character type that a passcode must have:
- Symbols: The minimum number of symbols.
- Letters: The minimum number of letters.
- Lowercase letters: The minimum number of lowercase letters.
- Uppercase letters: The minimum number of uppercase letters.
- Numbers or symbols: The minimum number of numbers or symbols.
- Numbers: The minimum number of numbers.
-
Passcode security
- Lock device after (minutes of inactivity): In the list, click the length of time a device can be inactive before it’s locked. The default is None
- Passcode expiration in days (1-730): Type the number of days after which the passcode expires. Valid values are 1–730. The default is 0, which means the passcode never expires.
- Previous passwords saved (0-50): Type the number of used passwords to save. Users are unable to use any password found in this list. Valid values are 0–50. The default is 0, which means users can reuse passwords.
- Maximum failed sign-on attempts: In the list, click the number of times a user can fail to sign in successfully after which the device is wiped. The default is Not defined.
-
Encryption
-
Enable encryption: Select whether to enable encryption. This option is available for Android 3.0 and later. The option is available regardless of the Passcode required setting.
To encrypt their devices, users must start with a charged battery and keep the device plugged in for the hour or more that encryption takes. If they interrupt the encryption process, they might lose some or all the data on their devices. After a device is encrypted, the process can’t be reversed except by doing a factory reset, which erases all the data on the device.
-
-
Samsung SAFE
Note:
As a workaround for disabling face or Iris recognition on Samsung SAFE devices: Create a Restrictions device policy for Samsung SAFE. In the Restrictions policy, turn on Disable Applications and add
com.samsung.android.bio.face.serviceorcom.samsung.android.server.iristo the table. Then, deploy the Restrictions policy.- Use same passcode across all users: Select whether to use the same passcode for all users. The default is Off. This setting applies only to Samsung SAFE devices and is available regardless of the Passcode required setting.
- When you enable Use same passcode across all users, type the passcode to be used by all users in the Passcode field.
- When you enable Passcode required, configure the following Samsung SAFE settings:
- Changed characters: Type the number of characters users must change from their previous passcode. The default is 0.
- Number of times a character can occur: Type the maximum number of times a character can occur in a passcode. The default is 0.
- Alphabetic sequence length: Type the maximum length of an alphabetic sequence in a passcode. The default is 0.
- Numeric sequence length: Type the maximum length of a numeric sequence in a passcode. The default is 0.
- Allow users to make password visible: Select whether users can make their passcodes visible. The default is On.
-
Configure biometric authentication. Select whether to enable biometric authentication. The default is Off. If you set it to On, you can set these options:
- Allow fingerprint. Select to allow users to authenticate using a fingerprint.
- Allow iris. Select to allow users to authenticate using an iris.
-
Forbidden strings: You create forbidden strings to prevent users from using insecure strings that are easy to guess like “password”, “pwd”, “welcome”, “123456”, “111111”. For each string you want to deny, click Add and then do the following:
- Forbidden strings: Type the string users might not use.
- Click Save to add the string or click Cancel to cancel adding the string.
Android Enterprise settings
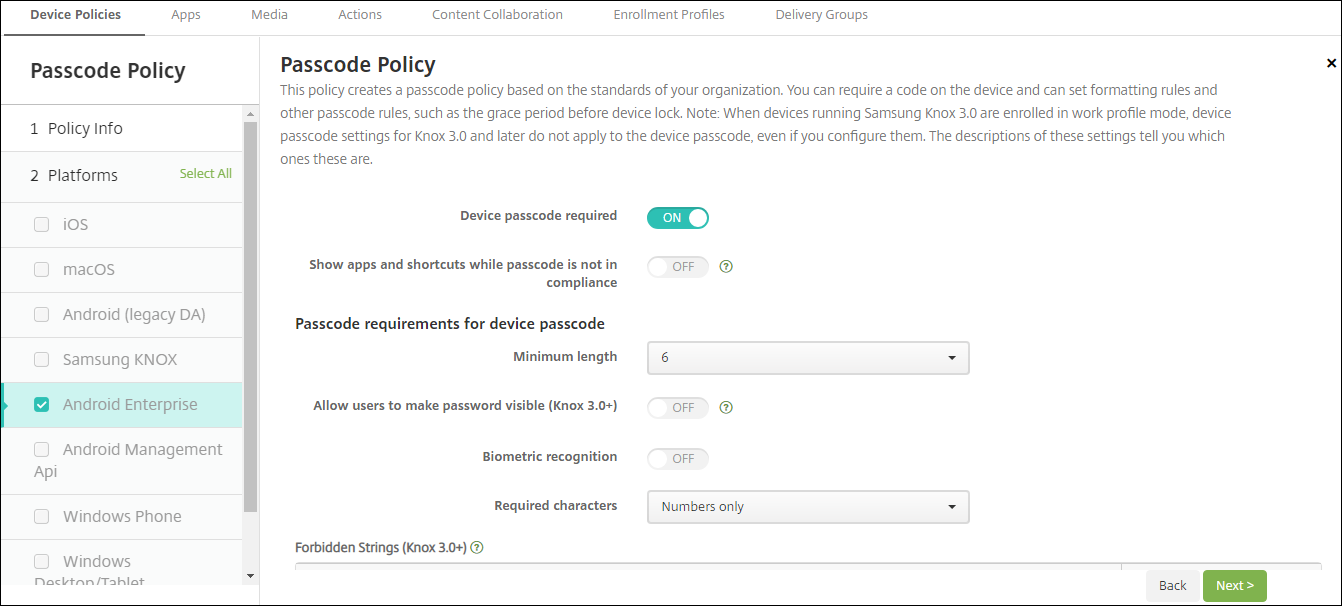
For Android Enterprise devices, you can require a passcode for the device or a security challenge for the Android Enterprise work profile or both.
For devices running Android 9.0 or later and Samsung Knox 3.0 and later, configure the settings for Samsung Knox on the Android Enterprise page. For devices running earlier versions of Android or Samsung Knox, use the Samsung Knox page.
Note:
When devices running Samsung Knox 3.0 are enrolled as work profile devices, device passcode settings for Knox 3.0 and later do not apply to the device passcode, even if you configure them.
- Device Passcode Required: Requires a passcode on the device. When this setting is On, configure the settings under Passcode requirements for device passcode and Passcode security for device passcode. Default is Off.
- Show apps and shortcuts while passcode is not in compliance: When this setting is On, apps and shortcuts on the device aren’t hidden, even when the passcode isn’t compliant. When this setting is Off, apps and shortcuts are hidden when the passcode isn’t compliant. If you enable this setting, Citrix® recommends you create an automated action to mark the device as out of compliance when the passcode isn’t in compliance. Default is Off.
-
Passcode requirements for device passcode:
- Minimum length: Specifies the minimum passcode length. The default is 6.
- Allow users to make password visible: For devices running Samsung Knox 3.0 and later that have a valid Knox license key configured. For fully managed devices only. This setting does not apply to devices enrolled as work profile devices. Allows users to make the password visible. Default is Off.
- Biometric recognition: Enables biometric recognition. If this setting is On, the Required characters field is hidden. The default is Off.
- Required characters: Specifies the types of characters required for passcodes. In the list, choose No Restriction, Both numbers and letters, Numbers only, or Letters only. Use No restrictions only for devices running Android 7.0. Android 7.1 and later don’t honor the No restrictions setting. The default is Both numbers and letters.
- Forbidden strings: For devices running Samsung Knox 3.0 and later that have a valid Knox license key configured. For fully managed devices only. This setting does not apply to devices enrolled as work profile devices. Specifies strings users can’t use as passcodes. You create forbidden strings to prevent users from using insecure strings that are easy to guess like “password”, “pwd”, “welcome”, “123456”, “111111”. For each string you want to deny: click Add. Type the string that you don’t want users to use; click Save to add the string or click Cancel to cancel adding the string.
- Advanced rules: Applies advanced rules for the types of characters that can occur in passcodes. When this setting is On, configure the settings under Minimum number of and Maximum number of. This setting isn’t available for Android devices earlier than Android 5.0. The default is Off.
-
Minimum number of:
- Symbols: Specifies the minimum number of symbols. Default is 0.
- Letters: Specifies the minimum number of letters. Default is 0.
- Lowercase letters: Specifies the minimum number of lowercase letters. Default is 0.
- Uppercase letters: Specifies the minimum number of uppercase letters. Default is 0.
- Numbers or symbols: Specifies the minimum number of numbers or symbols. Default is 0.
- Numbers: Specifies the minimum number of numbers. Default is 0.
- Changed characters: For devices running Samsung Knox 3.0 and later that have a valid Knox license key configured. For fully managed devices only. This setting does not apply to devices enrolled as work profile devices. Specifies the number of characters users must change from their previous passcode. The default is 0.
-
Maximum number of: For devices running Samsung Knox 3.0 and later that have a valid Knox license key configured. For fully managed devices only. This setting does not apply to devices enrolled as work profile devices.
- Number of times a character can occur: Specifies the maximum number of times a character can occur in a passcode. The default is 0, which means there is no maximum limit.
- Alphabetic sequence length: Specifies the maximum length of an alphabetic sequence in a passcode. The default is 0, which means there is no maximum limit.
- Numeric sequence length: Specifies the maximum length of a numeric sequence in a passcode. The default is 0, which means there is no maximum limit.
-
Passcode security for device passcode:
- Wipe the device after (failed sign-on attempts): Specifies the number of times a user can fail to sign on after which the device is fully wiped. Default is Not defined.
- Lock device after (minutes of inactivity) (0-999): Specifies the number of minutes a device can be inactive before it is locked. The default is None.
- Passcode expiration in days (1-730): Specifies the number of days after which the passcode expires. Valid values are 1–730. The default is 0, which means the passcode never expires.
- Previous passwords saved (0-50): Specifies the number of used passwords to save. Users are unable to use any password found in this list. Valid values are 0–50. Default is 0, which means users can reuse passwords.
- Lock the device after (failed sign-on attempts) For devices running Samsung Knox 3.0 and later that have a valid Knox license key configured. For fully managed devices only. This setting does not apply to devices enrolled as work profile devices. Specifies the number of times a user can fail to sign on, after which the device is locked. Default is Not defined.
- Work profile security challenge: Require users to complete a security challenge for access to apps running in an Android Enterprise work profile. For devices running Android 7.0 and later. When this setting is On, configure the settings under Passcode requirements for work profile security challenge and Passcode security for work profile security challenge. Default is Off.
-
Passcode requirements for work profile security challenge:
- Minimum length: Specifies the minimum passcode length. The default is 6.
- Allow users to make password visible: For devices running Knox 3.0 and later that have a valid Knox license key configured. Allows users to make the password visible. Default is Off.
- Biometric recognition: Enables biometric recognition. If this setting is On, the Required characters field is hidden. The default is Off.
- Required characters: Specifies the types of characters required for passcodes. In the list, choose No Restriction, Both numbers and letters, Numbers only, or Letters only. Use No restrictions only for devices running Android 7.0. Android 7.1 and later don’t honor the No restrictions setting. The default is Both numbers and letters.
- Forbidden strings: For devices running Knox 3.0 and later that have a valid Knox license key configured. Specifies strings users can’t use as passcodes. You create forbidden strings to prevent users from using insecure strings that are easy to guess like “password”, “pwd”, “welcome”, “123456”, “111111”. For each string you want to deny: click Add. Type the string that you don’t want users to use; click Save to add the string or click Cancel to cancel adding the string.
- Advanced rules: Applies advanced rules for the types of characters that can occur in passcodes. When this setting is On, configure the settings under Minimum number of and Maximum number of. This setting isn’t available for Android devices earlier than Android 5.0. The default is Off.
-
Minimum number of:
- Symbols: Specifies the minimum number of symbols. Default is 0.
- Letters: Specifies the minimum number of letters. Default is 0.
- Lowercase letters: Specifies the minimum number of lowercase letters. Default is 0.
- Uppercase letters: Specifies the minimum number of uppercase letters. Default is 0.
- Numbers or symbols: Specifies the minimum number of numbers or symbols. Default is 0.
- Numbers: Specifies the minimum number of numbers. Default is 0.
- Changed characters: For devices running Knox 3.0 and later that have a valid Knox license key configured. Specifies the number of characters users must change from their previous passcode. The default is 0.
-
Maximum number of: For devices running Knox 3.0 and later that have a valid Knox license key configured.
- Number of times a character can occur: Specifies the maximum number of times a character can occur in a passcode. The default is 0, which means there is no maximum limit.
- Alphabetic sequence length: Specifies the maximum length of an alphabetic sequence in a passcode. The default is 0, which means there is no maximum limit.
- Numeric sequence length: Specifies the maximum length of a numeric sequence in a passcode. The default is 0, which means there is no maximum limit.
-
Enable unified passcode: If On, users use one passcode for their device and work profile. If Off:
- Users must use different passcodes for their device and work profile.
- The Use one lock setting on the device, which users set if they want to use one passcode for their device and work profile, is disabled. The user can’t enable it.
- If the passcode requirement for the work profile security challenge is more complex than the device passcode: Users with the Use one lock setting enabled are prompted to change their work profile passcodes.
The default is Off. Available starting with Android 9.0.
-
Passcode security for work profile security challenge
- Wipe the container after (failed sign-on attempts): Specifies the number of times a user can fail to sign on, after which the work profile and its data are wiped from the device. Users must reinitialize the work profile after the wiping occurs. Default is Not defined.
- Lock container after (minutes of inactivity): Specifies the number of minutes a device can be inactive before the work profile is locked. The default is None.
- Passcode expiration in days (1-730): Specifies the number of days after which the passcode expires. Valid values are 1–730. The default is 0, which means the passcode never expires.
- Previous passwords saved (0-50): Specifies the number of used passwords to save. Users are unable to use any password found in this list. Valid values are 0–50. The default is 0, which means users can reuse passwords.
- Lock the container after (failed sign-on attempts): For devices running Knox 3.0 and later that have a valid Knox license key configured. Specifies the number of times a user can fail to sign on, after which the device is locked. Default is Not defined.
Windows Desktop/Tablet settings
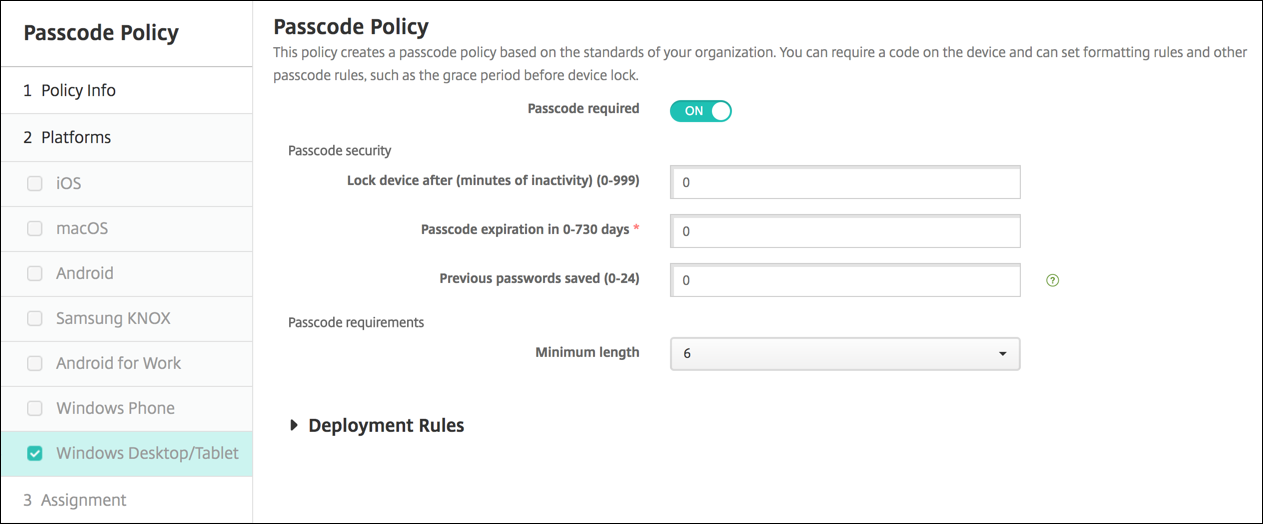
- Disallow convenience logon: Select whether to allow users to access their devices with picture passwords or biometric logons. The default is Off.
- Minimum passcode length: Select the minimum passcode length in the drop-down list. The default is 6.
- Maximum passcode attempts before wipe: In the list, click the number of times a user can fail to sign in successfully after which corporate data is wiped from the device. The default is 4.
- Passcode expiration in days (0-730): Type the number of days after which the passcode expires. Valid values are 0–730. The default is 0, which means the passcode never expires.
- Passcode history: (1-24): Type the number of used passcodes to save. Users are unable to use any passcode found in this list. Valid values are 1–24. You must enter a number between 1 and 24 in this field. The default is 0.
- Maximum inactivity before device lock in minutes (1-999): Type the length of time in minutes that a device can be inactive before it is locked. Valid values are 1–999. You must enter a number between 1 and 999 in this field. The default is 0.