Director
Director is a monitoring and troubleshooting console for Citrix Virtual Apps and Desktops.
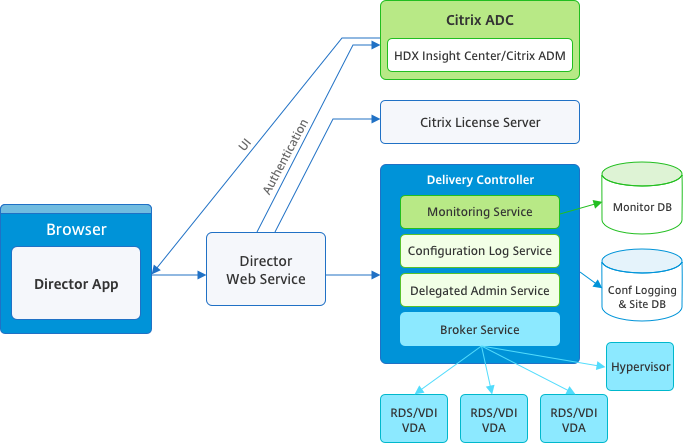
Director can access:
- Real-time data from the Broker Agent using a unified console integrated with Analytics, Performance Manager, and Network Inspector. The following analytics are powered by Citrix ADM to identify bottlenecks due to the network in your Citrix Virtual Apps™ or Desktops environment:
- Performance management for health and capacity assurance
- Historical trending and network analysis
- Historical data stored in the Monitor database to access the Configuration Logging database.
- ICA® data from the Citrix Gateway using Citrix ADM.
- Gain visibility into the end-user experience for virtual applications, desktops, and users for Citrix Virtual Apps or Desktops.
- Correlate network data with application data and real-time metrics for effective troubleshooting.
- Integrate with Citrix Virtual Desktop 7 Director monitoring tool.
Director uses a troubleshooting dashboard that provides real-time and historical health monitoring of the Citrix Virtual Apps or Desktops Site. This feature allows you to see failures in real time, providing a better idea of what the end users are experiencing.
For more information regarding the compatibility of Director features with Delivery Controller (DC), VDA and any other dependent components, see Feature compatibility matrix.
Note:
With the disclosure of the Meltdown and Spectre speculative execution side-channel vulnerabilities, Citrix recommends that you install relevant mitigation patches. These patches might impact SQL Server performance. For more information, see the Microsoft support article, Protect SQL Server from attacks on Spectre and Meltdown side-channel vulnerabilities. Citrix recommends that you test the scale and plan your workloads before rolling out the patches in your production environments.
Director is installed by default as a website on the Delivery Controller. For prerequisites and other details, see the System requirements documentation for this release. For specific information on the installation and configuration of Director, see Install and configure Director.
Log on to Director
The Director website is at https or http://<Server FQDN>/Director.
If one of the Sites in a multi-site deployment is down, the logon takes a little longer while it attempts to connect to the Site that is down.
Use Director with PIV smart card authentication
Director now supports Personal Identity Verification (PIV) based smart card authentication to log on. This feature is useful for organizations and government agencies that use smart card based authentication for access control. Smart card authentication requires specific configuration on the Director server and in the Active Directory. The configuration steps are detailed in Configure PIV smart card authentication.
Note:
Smart card authentication is supported only for users from the same Active Directory domain.
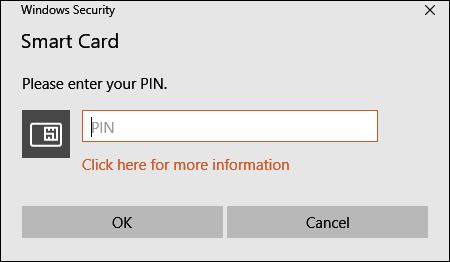
After performing the required configuration, you can log on to Director using a smart card:
-
Insert your smart card into the smart card reader.
-
Open a browser and go to the Director URL,
https://<directorfqdn>/Director. -
Select a valid user certificate from the displayed list.
-
Enter your smart card token.
-
After you are authenticated, you can access Director without keying extra credentials on the Director logon page.
Use Director with Integrated Windows Authentication
With Integrated Windows Authentication(IWA), domain-joined users gain direct access to Director without rekeying their credentials on the Director logon page. The prerequisites for working with Integrated Windows Authentication and Director are:
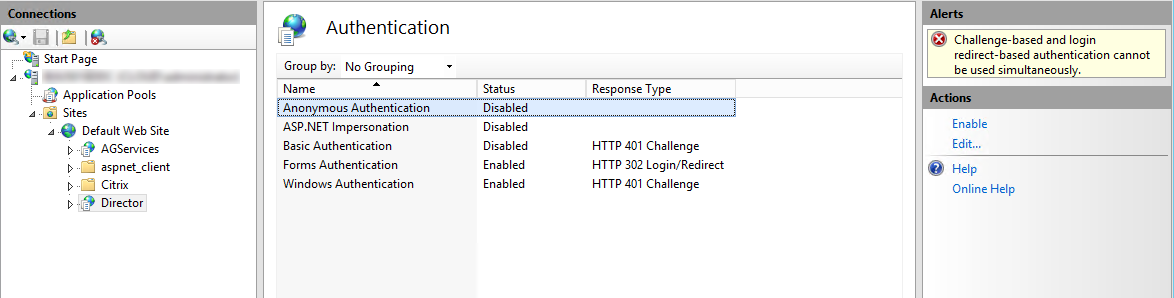
- Enable Integrated Windows Authentication on the IIS website that hosts Director. When you install Director, Anonymous and Forms Authentications are enabled. To support Integrated Windows Authentication and Director, disable Anonymous Authentication and enable Windows Authentication. Forms Authentication must remain set to Enabled for authentication of non-domain users.
- Start IIS manager.
- Go to Sites > Default Web Site > Director.
- Select Authentication.
- Right-click Anonymous Authentication, and select Disable.
- Right-click Windows Authentication, and select Enable.
- Configure Active Directory delegation permission for the Director machine. Configuration is only required if Director and the Delivery Controller™ are installed on separate machines.
- On the Active Directory machine, open the Active Directory Management Console.
- In the Active Directory Management Console navigate to Domain Name > Computers. Select the Director machine.
- Right-click and select Properties.
- In Properties, select the Delegation tab.
- Select the option, Trust this computer for delegation to any service (Kerberos only).
- The browser that is used to access Director must support Integrated Windows Authentication. Additional configuration steps might be required in Firefox and Chrome. For more information, refer to the browser documentation.
- The Monitoring Service must be running Microsoft .NET Framework 4.5.1 or a later supported version listed in the System Requirements for Director. For more information, see System Requirements.
When a user logs off Director or if the session times out, the logon page is displayed. From the logon page, the user can set the Authentication type to Automatic logon or User credentials.
Interface views
Director provides different views of the interface tailored to particular administrators. Product permissions determine what is displayed and the commands available.
For example, help desk administrators see an interface tailored to help desk tasks. Director allows help desk administrators to search for the user reporting an issue and display activity associated with that user. For example, status of the user’s applications and processes. They can resolve issues quickly by performing actions such as ending an unresponsive application or process, shadowing operations on the user’s machine, restarting the machine, or resetting the user profile.
In contrast, full administrators see and manage the entire Site and can perform commands for multiple users and machines. The Dashboard provides an overview of the key aspects of a deployment, such as the status of sessions, user logons, and the Site infrastructure. Information is updated every minute. If issues occur, details appear automatically about the number and type of failures that have occurred.
For more information about the various roles and their permissions in Director, see Delegated Administration and Director
Usage data collection by Pendo
The Director Service starts using Pendo to collect usage data after Director is installed. Statistics regarding the usage of the Trends pages and OData API call analytics are collected. Analytics collection complies with the Citrix Privacy Policy. Data collection is enabled by default when you install Director.
To opt out of the Pendo data collection, edit the registry key on the machine where Director is installed. If the registry key doesn’t exist, create and set it to the desired value. Refresh the Director instance after changing the registry key value.
Caution: Using the Registry Editor incorrectly can cause serious problems that might require you to reinstall your operating system. Citrix cannot guarantee that problems resulting from the incorrect use of the Registry Editor can be solved. Use the Registry Editor at your own risk. Citrix recommends that you back up Windows Registry before changing it.
Location: HKEY_LOCAL_MACHINE\Software\Citrix\Director
Name: DisableGoogleAnalytics
Note:
Previously, Director Service used Google Analytics to collect the data. The same registry key is now used for Pendo.
Value: 0 = enabled(default), 1 = disabled
You can use the following PowerShell cmdlet to disable data collection by Pendo:
New-Item HKLM:\SOFTWARE\Citrix -Name Director
New-ItemProperty HKLM:\SOFTWARE\Citrix\Director -Name DisableGoogleAnalytics -PropertyType DWORD -Value 1
New features guide
Director has an in-product guide that uses Pendo to give an insight into the new features released in the current version of Director. The quick overview coupled with appropriate in-product messages helps you understand what’s new in the product.
To opt out of this feature, edit the registry key, as described below on the machine where Director is installed. If the registry key doesn’t exist, create and set it to the desired value. Refresh the Director instance after changing the registry key value.
Caution:
Using the Registry Editor incorrectly can cause serious problems that might require you to reinstall your operating system. Citrix cannot guarantee that problems resulting from the incorrect use of the Registry Editor can be solved. Use the Registry Editor at your own risk. Citrix recommends that you back up Windows Registry before changing it.
Location: HKEY_LOCAL_MACHINE\Software\Citrix\Director
Name: DisableGuidedHelp
Value: 0 = enabled(default), 1 = disabled
You can use the following PowerShell cmdlet to disable the in-product guide:
New-Item HKLM:\SOFTWARE\Citrix -Name Director
New-ItemProperty HKLM:\SOFTWARE\Citrix\Director -Name DisableGuidedHelp -PropertyType DWORD -Value 1
Reference articles
- Reduce MTTR from Citrix Director
- Citrix Director - Manage and configure alerts and notifications with PowerShell
- Citrix Virtual Apps and Desktops developer documentation