Configure Authentication
As an administrator, you can choose to have your subscribers authenticate to their workspaces using one of the following authentication methods:
- Active Directory (AD)
- Active Directory plus token
- Azure Active Directory (AAD)
- Citrix Gateway
- Okta
- SAML 2.0
Citrix Workspace™ also supports single sign-on to your virtual apps and desktops. When the user enters their Active Directory credentials, Workspace can use these to provide SSO to resources. When using other IdPs, Workspace can use Citrix Federated Authentication Service (FAS) to provide single sign-on (SSO) to resources.
Choose or change authentication methods
-
Define one or more identity providers in Identity and Access Management. For instructions, visit Identity and access management.
-
Choose or change how subscribers authenticate to their workspace in Workspace Configuration > Authentication > Workspace Authentication.
Important:
Switching authentication modes can take up to five minutes and causes an outage to your subscribers during that time. The outage affects access to the store and has no impact on HDX™ sessions. Citrix recommends limiting changes to periods of low usage. If you do have subscribers logged on to Citrix Workspace using a browser or Citrix Workspace app, advise them to close the browser or exit the app. After waiting approximately five minutes, they can sign in again using the new authentication method.
Active Directory (AD)
By default, Citrix Cloud™ uses Active Directory (AD) to manage subscriber authentication to workspaces.
To use AD, you must have at least two Citrix Cloud Connectors installed in the on-premises AD domain. For more information on installing the Cloud Connector, see Cloud Connector Installation.
Single Sign-on to VDAs with AD
When using AD authentication, Workspace provides SSO capability when launching AD joined virtual apps and desktops.
Active Directory (AD) plus token
For greater security, Citrix Workspace supports a time-based token as a second factor of authentication to AD sign-in.
For each login, Workspace prompts subscribers to enter a token from an authentication app on their enrolled device. Before signing in, subscribers must enroll their device with an authentication app that follows the Time-Based One-Time Password (TOTP) standard, such as Citrix SSO. Currently, subscribers can enroll only one device at a time.
For more information, see Tech Insight: Authentication - TOTP and Tech Insight: Authentication - Push.
Single Sign-on to VDAs with AD plus token
When using AD plus token authentication, Workspace provides SSO capability when launching AD joined virtual apps and desktops.
Requirements for AD plus token
Active Directory plus token authentication has the following requirements:
- A connection between Active Directory and Citrix Cloud, with at least two Cloud Connectors installed in your on-premises environment. For requirements and instructions, see Connect Active Directory to Citrix Cloud.
- Active Directory + Token authentication enabled in the Identity and Access Management page. For information, see To enable Active Directory plus token authentication.
- Subscriber access to email to enroll devices.
- A device on which to download the authentication app.
First-time enrollment
Subscribers enroll their devices using the enrollment process described in Register devices for two-factor authentication.
During first-time sign-in to Workspace, subscribers follow the prompts to download the Citrix SSO app. The Citrix SSO app generates a unique one-time password on an enrolled device every 30 seconds.
Important:
During the device enrollment process, subscribers receive an email with a temporary verification code. This temporary code is used only to enroll the subscriber’s device. Using this temporary code as a token for signing in to Citrix Workspace with two-factor authentication isn’t supported. Only verification codes that are generated from an authentication app on an enrolled device are supported tokens for two-factor authentication.
Re-enroll a device
If a subscriber no longer has their enrolled device or needs to re-enroll it (for example, after erasing content from the device), Workspace provides the following options:
-
Subscribers can re-enroll their devices using the same enrollment process described in Register devices for two-factor authentication. Because subscribers can enroll only one device at a time, enrolling a new device or re-enrolling an existing device removes the previous device registration.
-
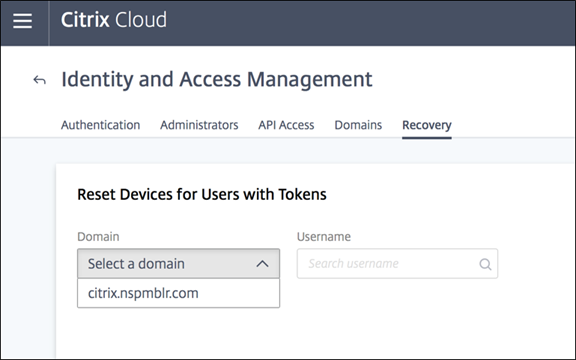
Administrators can search for subscribers by Active Directory name and reset their device. To do that, go to Identity and Access Management > Recovery. During the next sign-on to Workspace, the subscriber experiences the first-time enrollment steps.
Azure Active Directory
Use of Azure Active Directory (AD) to manage subscriber authentication to workspaces has the following requirements:
- Microsoft Entra ID (formerly Microsoft Azure AD) with a user who has global administrator permissions. For more information on the Microsoft Entra ID applications and permissions that Citrix Cloud uses, see Azure Active Directory Permissions for Citrix Cloud.
- A Citrix Cloud Connector™ installed in the on-premises AD domain. The machine must also be joined to the domain that is syncing to Microsoft Entra ID.
- VDA version 7.15.2000 LTSR CU VDA or 7.18 current release VDA or higher.
- A connection between Microsoft Entra ID and Citrix Cloud. For information, see Connect Azure Active Directory to Citrix Cloud.
- Any version of Citrix Workspace app. If using legacy Citrix Receiver™ then you must use the following minimum versions:
- Citrix Receiver for Windows 4.11 CR or 4.9 LTSR CU2 or higher
- Citrix Receiver for Linux 13.8
- Citrix Receiver for Android 3.13 and later
When syncing your Active Directory to Microsoft Entra ID, the UPN and SID entries must be included in the sync. If these entries aren’t synchronized, certain workflows in Citrix Workspace fail.
Warning:
- If you’re using Microsoft Entra ID, don’t make the registry change described in CTX225819. Making this change might cause session launch failures for Microsoft Entra ID users.
- Adding a group as a member of another group (nesting) is supported with the
DSAuthAzureAdNestedGroupsfeature enabled. You can enableDSAuthAzureAdNestedGroupsby submitting a request to Citrix Support.
After enabling Microsoft Entra ID authentication:
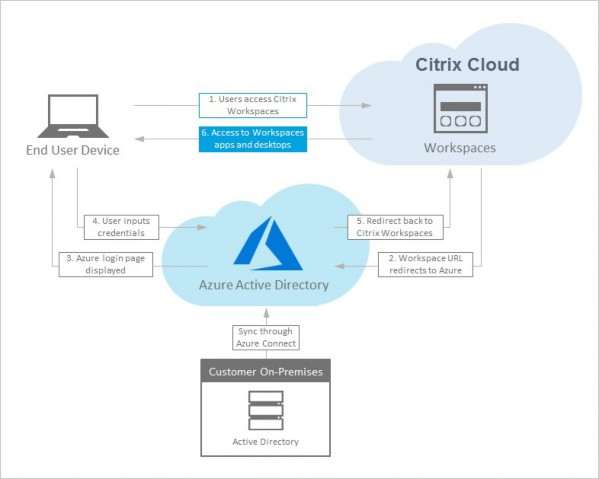
- Added security: For security, users are prompted to sign in again when launching an app or a desktop. The password information flows directly from user’s device to the VDA that is hosting the session.
- Sign-in experience: Microsoft Entra ID authentication provides federated sign-in, not single sign-on (SSO). Subscribers sign in from an Azure sign-in page, and might have to authenticate again when opening Citrix DaaS.
For SSO, enable the Citrix Federated Authentication Service in Citrix Cloud. See Enable single sign-on for workspaces with Citrix Federated Authentication Service for more information.
You can customize the sign-in experience for Microsoft Entra ID. For information, see the Microsoft documentation. Any sign-in customizations (the logo) made in Workspace Configuration do not affect the Microsoft Entra ID sign-in experience.
The following diagram shows the sequence of Microsoft Entra ID authentication.
Sign-out experience
Use Settings > Log Off to complete the sign-out process from Workspace and Microsoft Entra ID. If subscribers close the browser instead of using the Log Off option, they might remain signed in to Microsoft Entra ID.
Important:
If Citrix Workspace times out in the browser due to inactivity, subscribers remain signed in to Microsoft Entra ID. This prevents a Citrix Workspace timeout from forcing other Microsoft Entra ID applications to close.
Single Sign-on to VDAs with EntraId
If the IdP is Entra ID then you can use Entra ID SSO to VDAs. For other cases, to enable Single Sign on to VDAs you must use FAS.
Citrix Gateway
Citrix Workspace supports using an on-premises Citrix Gateway as an identity provider to manage subscriber authentication to workspaces. For more information, see Tech Insight: Authentication - Citrix Gateway.
Requirements for Citrix Gateway
Citrix Gateway authentication has the following requirements:
- A connection between your Active Directory and Citrix Cloud. For requirements and instructions, see Connect Active Directory to Citrix Cloud.
- Subscribers must be Active Directory users to sign in to their workspaces.
- If you’re performing federation, your AD users must be synchronized to the federation provider. Citrix Cloud requires the AD attributes to allow users to sign in successfully.
- An on-premises Citrix Gateway:
- Citrix Gateway 12.1 54.13 Advanced edition or later
- Citrix Gateway 13.0 41.20 Advanced edition or later
- Citrix Gateway authentication enabled in the Identity and Access Management page. This generates the client ID, secret, and redirect URL required to create the connection between Citrix Cloud and your on-premises Gateway.
- On the Gateway, an OAuth IdP authentication policy is configured using the generated client ID, secret, and redirect URL.
For more information, see Connect an on-premises Citrix Gateway as an identity provider to Citrix Cloud.
Subscriber experience of Citrix Gateway
When authentication with Citrix Gateway is enabled, subscribers experience the following workflow:
- The subscriber navigates to the Workspace URL in their browser or launches Workspace app.
- The subscriber is redirected to the Citrix Gateway logon page and is authenticated using any method configured on the Gateway. This method can be MFA, federation, conditional access policies, and so on. You can customize the Gateway logon page so that it looks the same as the Workspace sign-in page using the steps described in CTX258331.
- After successful authentication, the subscriber’s workspace appears.
Single sign-on with Gateway
Depending on how you configure Citrix Gateway, you might not need FAS for SSO to DaaS. For more information on configuring Citrix Gateway, visit Create an OAuth IdP policy on the on-premises Citrix Gateway.
Citrix Workspace supports using Google as an identity provider to manage subscriber authentication to workspaces.
Requirements for Google
- A connection between your on-premises Active Directory and Google Cloud.
- A developer account with access to the Google Cloud Platform console. This account is required for creating a service account and key, and enabling the Admin SDK API.
- An administrator account with access to the Google Workspace Admin console. This account is required for configuring domain-wide delegation and a read-only API user account.
- A connection between your on-premises Active Directory domain and Citrix Cloud, with Google authentication enabled in the Identity and Access Management page. To create this connection, at least two Cloud Connectors are required in your resource location.
For more information, see Connect Google as an identity provider to Citrix Cloud.
Subscriber experience with Google
When authentication with Google is enabled, subscribers experience the following workflow:
- The subscriber navigates to the Workspace URL in their browser or launches the Workspace app.
- The subscriber is redirected to the Google sign-in page and is authenticated using the method configured in Google Cloud (for example, multifactor authentication, conditional access policies, and so on).
- After successful authentication, the subscriber’s workspace appears.
Single Sign-on to VDAs with Google
When using Google authentication, to enable Single Sign on to VDAs you must use FAS.
Okta
Citrix Workspace supports using Okta as an identity provider to manage subscriber authentication to workspaces. For more information, see Tech Insight: Authentication - Okta.
Requirements for Okta
Okta authentication has the following requirements:
- A connection between your on-premises Active Directory and your Okta organization.
- An Okta OIDC web application configured for use with Citrix Cloud. To connect Citrix Cloud to your Okta organization, you must supply the Client ID and Client Secret associated with this application.
- A connection between your on-premises Active Directory domain and Citrix Cloud, with Okta authentication enabled in the Identity and Access Management page.
For more information, see Connect Okta as an identity provider to Citrix Cloud.
Subscriber experience with Okta
When authentication with Okta is enabled, subscribers experience the following workflow:
- The subscriber navigates to the Workspace URL in their browser or launches the Workspace app.
- The subscriber is redirected to the Okta sign-in page and is authenticated using the method configured in Okta (for example, multifactor authentication, conditional access policies, and so on).
- After successful authentication, the subscriber’s workspace appears.
Single Sign-on to VDAs with Okta
When using Okta authentication, to enable Single Sign on to VDAs you must use FAS.
SAML 2.0
Citrix Workspace supports using SAML 2.0 to manage subscriber authentication to workspaces. You can use the SAML provider of your choice, provided it supports SAML 2.0.
Requirements for SAML 2.0
SAML authentication has the following requirements:
- SAML provider that supports SAML 2.0.
- On-premises Active Directory domain.
- Two Cloud Connectors deployed to a resource location and joined to your on-premises AD domain.
- AD integration with your SAML provider.
For more information about configuring SAML authentication for workspaces, see Connect SAML as an identity provider to Citrix Cloud.
Subscriber experience with SAML 2.0
- The subscriber navigates to the Workspace URL in their browser or launches Citrix Workspace app.
- The subscriber is redirected to the SAML identity provider sign-in page for their organization. The subscriber authenticates with the mechanism configured for the SAML identity provider, such as multifactor authentication or conditional access policies.
- After successful authentication, the subscriber’s workspace appears.
Single Sign-on to VDAs with SAML 2.0
If the IdP is Entra ID then you can use Entra ID SSO to VDAs. For other cases, to enable Single Sign on to VDAs you must use FAS.
Citrix Federated Authentication Service (FAS)
Citrix Workspace supports using Citrix Federated Authentication Service (FAS) for single sign-on (SSO) to Citrix DaaS. Without FAS, subscribers using a federated identity provider are prompted to enter their credentials more than once to access their virtual apps and desktops.
For more information, see Citrix Federated Authentication Service (FAS).
Entra ID SSO to VDAs
If where the user has authenticated using Entra ID, Citrix Workspace supports using the Entra ID session to authenticate to the VDAs. For more information, see Microsoft Entra single sign-on.
This functionality is disabled by default and should only be enabled once you have completed the rest of the configuration, otherwise users may experience delayed or failed launches. To enable it, use the PowerShell modules version 1.0.6.
Set-StoreConfigurations -StoreUrl "https://<yourstore>.cloud.com" -ClientId "<clientId>" -ClientSecret "<clientSecret>" -AzureAdSsoEnabled $True
<!--NeedCopy-->