Connect SAML as an identity provider to Citrix Cloud™
Citrix Cloud supports using SAML (Security Assertion Markup Language) as an identity provider to authenticate Citrix Cloud administrators and subscribers signing in to their workspaces. You can use the SAML 2.0 provider of your choice with your on-premises Active Directory (AD).
About this article
This article describes the required steps for configuring a connection between Citrix Cloud and your SAML provider. Some of these steps describe actions that you perform in your SAML provider’s administration console. The specific commands you use to perform these actions might vary from the commands described in the article, depending on your chosen SAML provider. These SAML provider commands are provided as examples only. Refer to your SAML provider’s documentation for more information about the corresponding commands for your SAML provider.
Supported SAML providers
SAML providers that support the official SAML 2.0 specification are supported for use with Citrix Cloud.
Citrix has tested the following SAML providers for authenticating Citrix Cloud administrators and for authenticating Citrix Workspace™ subscribers using Single Sign-on (SSO) and Single Logout (SLO). SAML providers that don’t appear in this list are also supported.
- Microsoft ADFS
- Microsoft Azure AD
- Duo
- Okta
- OneLogin
- PingOne SSO
- PingFederate
When testing these providers, Citrix used the following settings to configure the SAML connection in the Citrix Cloud console:
- Binding Mechanism: HTTP Post
- SAML Response: Sign Either Response or Assertion
- Authentication Context: Unspecified, Exact
The values for these settings are configured by default when you configure your SAML connection in Citrix Cloud. Citrix recommends using these settings when configuring the connection with your chosen SAML provider.
For more information about these settings, see Add SAML provider metadata to Citrix Cloud in this article.
Support for scoped Entity IDs
This article describes how to configure SAML authentication using a single SAML application and Citrix Cloud’s default generic Entity ID.
If your SAML authentication requirements include the need for multiple SAML applications within a single SAML provider, refer to Configure a SAML application with a scoped Entity ID in Citrix Cloud.
Prerequisites
Using SAML authentication with Citrix Cloud has the following requirements:
- SAML provider that supports SAML 2.0.
- On-premises AD domain.
- Two Cloud Connectors deployed to a resource location and joined to your on-premises AD domain. The Cloud Connectors are used to ensure Citrix Cloud can communicate with your resource location.
- AD integration with your SAML provider.
Cloud Connectors
You need at least two (2) servers on which to install the Citrix Cloud Connector™ software. Citrix recommends at least two servers for Cloud Connector high availability. These servers must meet the following requirements:
- Meets the system requirements described in Cloud Connector Technical Details.
- Does not have any other Citrix® components installed, is not an AD domain controller, and is not a machine critical to your resource location infrastructure.
- Joined to the domain where your resources reside. If users access resources in multiple domains, you need to install at least two Cloud Connectors in each domain.
- Connected to a network that can contact the resources that subscribers access through Citrix Workspace.
- Connected to the Internet. For more information, see System and Connectivity Requirements.
For more information about installing the Cloud Connector, see Cloud Connector Installation.
Active Directory
Before configuring SAML authentication, perform the following tasks:
- Verify that your workspace subscribers have user accounts in your AD. Subscribers without AD accounts can’t sign in to their workspaces successfully when SAML authentication is configured.
- Connect your AD to your Citrix Cloud account by deploying Cloud Connectors in your on-premises AD.
- Synchronize your AD users to the SAML provider. Citrix Cloud requires the AD user attributes for your workspace subscribers so they can sign in successfully.
AD user attributes
The following attributes are required for all Active Directory user objects and must be populated:
- Common name
- SAM account name
- User Principal Name (UPN)
- Object GUID
- SID
Citrix Cloud uses the Object GUID and SID attributes from your AD to establish the user context when subscribers sign in to Citrix Workspace. If either of these properties isn’t populated, subscribers can’t sign in.
The following attributes aren’t required for using SAML authentication with Citrix Cloud, but Citrix recommends populating them to ensure the best user experience:
- Email address
- Display Name
Citrix Cloud uses the Display Name attribute to show subscribers’ names correctly in Citrix Workspace. If this attribute isn’t populated, subscribers can still sign in, but their names might not be displayed as expected.
SAML integration with Active Directory
Before enabling SAML authentication, you must integrate your on-premises AD with your SAML provider. This integration allows the SAML provider to pass the following required AD user attributes to Citrix Cloud in the SAML assertion:
- objectSID (SID)
- objectGUID (OID)
- userPrincipalName (UPN)
- Mail (email)
- Display Name (displayName)
You can configure a subset of these attributes, provided either the SID or UPN attributes are included in the SAML assertion. Citrix Cloud retrieves the other attributes from your AD as needed.
Note:
To ensure the best performance, Citrix recommends configuring all of the attributes mentioned in this section.
Although the precise integration steps vary among SAML providers, the integration process typically includes the following tasks:
- Install a synchronization agent in your AD domain to establish a connection between your domain and your SAML provider. If you’re using ADFS as your SAML provider, this step isn’t required.
- Create custom attributes and map them to the required AD user attributes mentioned earlier in this section. For reference, the general steps for this task are described in Create and map custom SAML attributes in this article.
- Synchronize your AD users to your SAML provider.
For more information about integrating your AD with your SAML provider, consult your SAML provider’s product documentation.
Administrator authentication with SAML 2.0
Citrix Cloud supports using SAML 2.0 to authenticate individual administrators and members of administrator groups in AD. For more information about adding administrator groups to Citrix Cloud, see Manage administrator groups.
Using an existing SAML connection for administrator authentication
If you already have a SAML 2.0 connection in Citrix Cloud and want to use it to authenticate administrators, you must first disconnect SAML 2.0 in Identity and Access Management and then reconfigure the connection. If you’re using your SAML connection to authenticate Citrix Workspace subscribers, you must also disable the SAML authentication method in Workspace Configuration. After reconfiguring the SAML connection, you can add individual administrators or administrator groups to Citrix Cloud.
If you attempt to add individual administrators or administrator groups without first disconnecting and reconnecting SAML 2.0, the Active Directory identity option described in Add an administrator group to Citrix Cloud doesn’t appear.
Task overview for setting up a new SAML connection
To set up a new SAML 2.0 connection in Citrix Cloud, you perform the following tasks:
- In Identity and Access Management, connect your on-premises AD to Citrix Cloud as described in Connect Active Directory to Citrix Cloud.
- Integrate your SAML provider with your on-premises AD as described in SAML integration with Active Directory in this article.
- Configure the sign-in URL that administrators can use to sign in to Citrix Cloud.
- In Identity and Access Management, configure SAML authentication in Citrix Cloud. This task involves configuring your SAML provider with the SAML metadata from Citrix Cloud and then configuring Citrix Cloud with the metadata from your SAML provider to create the SAML connection.
Task overview for using an existing SAML connection for Citrix Cloud administrators
If you already have a SAML 2.0 connection in Citrix Cloud and want to use it for administrator authentication, perform the following tasks:
- If applicable, disable SAML 2.0 workspace authentication: In Workspace Configuration > Authentication, select a different authentication method and then select Confirm when prompted.
- Disconnect your existing SAML 2.0 connection: In Identity and Access Management > Authentication, locate the SAML connection. From the ellipsis menu at the far right, select Disconnect. Select Yes, disconnect to confirm the action.
- Reconnect SAML 2.0 and configure the connection: From the ellipsis menu for SAML 2.0, select Connect.
- When prompted, enter a unique identifier for the sign-in URL that administrators will use to sign in.
- Configure the SAML connection as described in Configure the SAML provider metadata in this article.
After configuring your SAML connection, you can add your AD administrator groups to Citrix Cloud as described in Manage administrator groups. You can also reenable SAML for workspace subscribers as described in this article.
Create and map custom SAML attributes
If you already have custom attributes for the SID, UPN, OID, email, and displayName attributes configured in your SAML provider, you don’t have to perform this task. Proceed to Create a SAML connector application and use your existing custom SAML attributes in Step 5.
Note:
The steps in this section describe actions that you perform in your SAML provider’s administration console. The specific commands you use to perform these actions might vary from the commands described in this section, depending on your chosen SAML provider. The SAML provider commands in this section are provided as examples only. Refer to your SAML provider’s documentation for more information about the corresponding commands for your SAML provider.
- Sign in to the administration console of your SAML provider and select the option for creating custom user attributes. For example, depending on your SAML provider’s console, you might select Users > Custom User Fields > New User Field.
-
Add attributes for the following AD properties. Name the attributes using the default values shown.
AD Property Required or optional Default value userPrincipalName Required if not adding an attribute for SID (recommended). cip_upnobjectSID Required if not adding an attribute for UPN. cip_sidobjectGUID Optional for authentication cip_oidmail Optional for authentication cip_emaildisplayName Required by the Workspace UI displayNamegivenName Required by the Workspace UI firstNamesn Required by the Workspace UI lastNameAD Forest Optional for authentication cip_forestAD Domain Optional for authentication cip_domain - Select the AD that you connected with Citrix Cloud. For example, depending on your SAML provider’s console, you might select Users > Directories.
- Select the option for adding directory attributes. For example, depending on your SAML provider’s console, you might select Directory Attributes.
- Select the option for adding attributes and map the following AD attributes to the custom user attributes you created in Step 2:
- If you added the attribute for SID in Step 2 (for example,
cip_sid), select objectSid and map to the attribute that you created. - If you added the attribute for UPN in Step 2 (for example,
cip_upn), select userPrincipalName and map to the attribute that you created. - If you added the attribute for ObjectGUID in Step 2 (for example,
cip_oid), select ObjectGUID and map to the attribute that you created. - If you added the attribute for Mail in Step 2 (for example,
cip_email), select mail and map to the attribute that you created. - If you added the attribute for Display Name in Step 2 (for example,
displayName), select displayName and map to the attribute that you created.
- If you added the attribute for SID in Step 2 (for example,
Configure the administrator sign-in URL
- Sign in to Citrix Cloud at https://citrix.cloud.com.
- From the Citrix Cloud menu, select Identity and Access Management.
- Locate SAML 2.0 and select Connect from the ellipsis menu.
- When prompted, enter a short, URL-friendly identifier for your company and select Save and continue. The Configure SAML page appears.
- Proceed to the next section to configure the SAML connection to Citrix Cloud.
Configure the SAML provider metadata
In this task, you create a connector application using SAML metadata from Citrix Cloud. After you configure the SAML application, you use the SAML metadata from your connector application to configure the SAML connection to Citrix Cloud.
Note:
Some steps in this section describe actions that you perform in your SAML provider’s administration console. The specific commands you use to perform these actions might vary from the commands described in this section, depending on your chosen SAML provider. The SAML provider commands in this section are provided as examples only. Refer to your SAML provider’s documentation for more information about the corresponding commands for your SAML provider.
Create a SAML connector application
- From your SAML provider’s administration console, add an application for an identity provider with attributes and sign response. For example, depending on your provider’s console, you might select Applications > Applications > Add App and then select SAML Test Connector (IdP w/ attr w/ sign response).
- If applicable, enter a display name and save the app.
- From the Configure SAML screen in Citrix Cloud, in SAML Metadata, select Download. The metadata XML file appears in another browser tab.
Note:
If needed, you can also download this file from
https://saml.cloud.com/saml/metadata.xml. This endpoint might be more friendly to some identity providers when importing and monitoring the SAML provider metadata. - Enter the following details for the connector application:
- In the Audience field, enter
https://saml.cloud.com. - In the Recipient field, enter
https://saml.cloud.com/saml/acs. - In the field for ACS URL validator, enter
https://saml.cloud.com/saml/acs. - In the field for ACS URL, enter
https://saml.cloud.com/saml/acs.
- In the Audience field, enter
-
Add your custom SAML attributes as parameter values in the application:
Create this field Assign this custom attribute cip_sid The custom attribute you created for SID. Example: cip_sid cip_upn The custom attribute you created for UPN. Example: cip_upn cip_oid The custom attribute you created for ObjectGUID. Example: cip_oid cip_email The custom attribute you created for Mail. Example: cip_email displayName The custom attribute you created for Display Name. Example: displayName - Add your Workspace subscribers as users to allow them to access the application.
Add SAML provider metadata to Citrix Cloud
-
Acquire the SAML metadata from your SAML provider. The following image is an example of what this file might look like:

- In the Configure SAML screen in Citrix Cloud, enter the following values from your SAML provider’s metadata file:
-
In Identity Provider Entity ID, enter the entityID value from the EntityDescriptor element in the metadata.

- In Sign Authentication Request, select Yes to allow Citrix Cloud to sign authentication requests, certifying they came from Citrix Cloud and not a malicious actor. Select No if you prefer to add the Citrix ACS URL to an allow list that your SAML provider uses for posting SAML responses safely.
-
In SSO Service URL, enter the URL for the binding mechanism you want to use. You can use either HTTP-POST or HTTP-Redirect binding. In the metadata file, locate the SingleSignOnService elements with Binding values of either HTTP-POST or HTTP-Redirect.
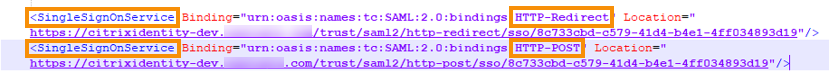
- In Binding Mechanism, select the mechanism that matches the binding for the SSO Service URL you chose from the metadata file. By default, HTTP Post is selected.
- In SAML Response, select the signing method your SAML provider uses for the SAML Response and SAML Assertion. By default, Sign Either Response or Assertion is selected. Citrix Cloud rejects any responses that aren’t signed as specified in this field.
-
- In your SAML provider’s administration console, perform the following actions:
- Select SHA-256 for the SAML signing algorithm.
- Download the X.509 certificate as a Base64-encoded PEM, CRT, or CER file.
- On the Configure SAML page in Citrix Cloud, in X.509 Certificate, select Upload File and select the certificate file you downloaded in the previous step.
- Select Continue to complete the upload.
- In Authentication Context, select the context you want to use and how strictly you want Citrix Cloud to enforce this context. Select Minimum to request authentication at the selected context without enforcing authentication at that context. Select Exact to request authentication at the selected context and enforce authentication only at that context. If your SAML provider doesn’t support authentication contexts or you choose not to use them, select Unspecified and Minimum. By default, Unspecified and Exact are selected.
- For Logout URL (optional), decide whether or not you want users signing out of Citrix Workspace or Citrix Cloud to also sign out of all web applications that they previously signed in to through the SAML provider.
- If you want users to stay signed in to their web applications after signing out of Citrix Workspace or Citrix Cloud, leave the Logout URL field blank.
-
If you want users to sign out of all web applications after signing out of Citrix Workspace or Citrix Cloud, enter the SingleLogout (SLO) endpoint from your SAML provider. If you’re using Microsoft ADFS or Azure Active Directory as your SAML provider, the SLO endpoint is the same as the single sign-on (SSO) endpoint.

-
Verify that the following default attribute values in Citrix Cloud match the corresponding attribute values configured in your SAML provider. For Citrix Cloud to find these attributes within the SAML assertion, the values entered here must match those in your SAML provider. If you didn’t configure a certain attribute in your SAML provider, you can use the default value in Citrix Cloud or leave the field blank, unless noted otherwise.
-
Attribute name for User Display Name: Default value is
displayName. -
Attribute name for User Given Name: Default value is
firstName. -
Attribute name for User Family Name: Default value is
lastName. -
Attribute name for Security Identifier (SID): You must enter this attribute name from your SAML provider if you didn’t create an attribute for UPN. The default value is
cip_sid. -
Attribute name for User Principal Name (UPN): You must enter this attribute name from your SAML provider if you didn’t create an attribute for SID. The default value is
cip_upn. -
Attribute name for Email: Default value is
cip_email. -
Attribute name for AD Object Identifier (OID): Default value is
cip_oid. -
Attribute name for AD Forest: Default value is
cip_forest. -
Attribute name for AD Domain: Default value is
cip_domain.
-
Attribute name for User Display Name: Default value is
- Select Test and Finish to verify you configured the connection successfully.
Add administrators to Citrix Cloud from AD
For instructions for adding and managing AD groups in Citrix Cloud, see Manage administrator groups.
Enable SAML authentication for workspaces
- From the Citrix Cloud menu, select Workspace Configuration.
- Select the Authentication tab
- Select SAML 2.0.
Cloning an existing SAML connection within identity and access management
Important:
Cloning SAML connections does not clone the existing Scoped Entity ID. You may need to update your SAML application configuration if you add a Scoped Entity ID or generate a new one during the cloning process.
To clone an existing SAML connection follow the steps below:
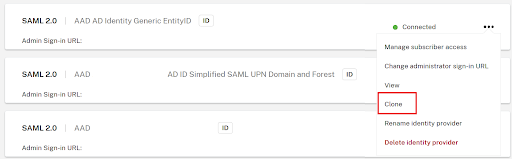
-
Select the 3 dots to the right of an existing SAML connection and select Clone from the list of actions.
-
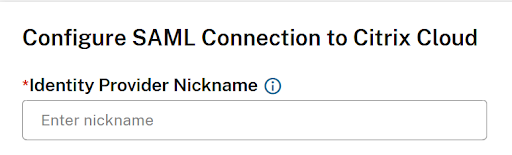
Enter a new and unique GO URL for the new SAML connection. This can be changed later if needed.
-
Enter a new unique nickname for the new SAML connection.
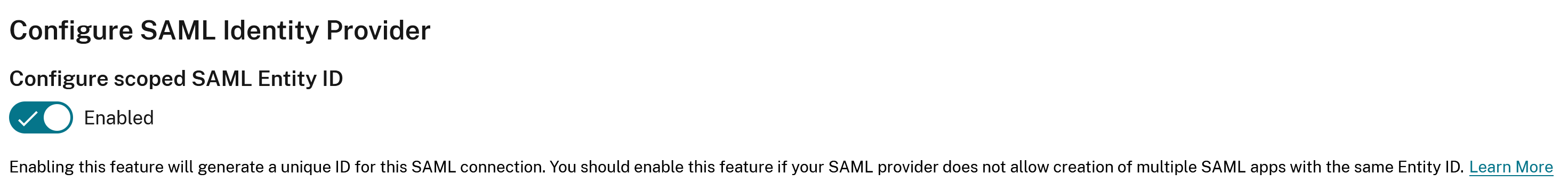
-
Update any settings within the connection such as enable scoped entity ID, signing needs to be enabled, add a missing logout URL, or update the SAML provider cert which has recently expired.
-
Click “Test and finish” to save the new SAML connection.
-
Switch Workspace to use the new SAML connection within Workspace Configuration →Authentication.
-
Update your SAML application configuration with a new scoped entity ID (not always necessary).
Service Provider Initiated SSO vs Identity Provider Initiated SSO
SP-initiated SSO - the end user logs in directly from the web application (SP) such as Workspace and/or Citrix Cloud.
The application then redirects them to the SAML IdP for authentication.
If authentication is successful, the end user is redirected back to the web app (SP) and logged in.
IdP-initiated SSO - the end user logs in first to their SAML IdP and then selects the app (SP) they want to launch from the IDP portal.
Can Identity Provider Initiated SSO be used with Workspace or Citrix Cloud?
No. Workspace and Citrix Cloud both only support SAML Service Provider Initiated SSO logon. All logon flows must be initiated via either a Workspace URL for end user access, or a Citrix Cloud GO URL for Citrix Cloud admin access.
Directly Connecting the SAML Provider to Citrix Cloud VS IDP Chaining
Is IDP chaining supported for SAML login to Workspace or Citrix Cloud?
IDP chaining is supported provided the closest SAML IDP in the IDP chain is configured correctly and forwards SAML requests from Citrix Cloud onwards in the IDP chain, and the IDP chain returns the correct SAML response to Citrix Cloud.
Examples of IDP chains
- Citrix Cloud → F5 (directly connected to Citrix Cloud as the SAML provider) → Federated to Entra ID
- Citrix Cloud → Entra ID (directly connected to Citrix Cloud as the SAML provider) → Federated to ADFS
- Citrix Cloud → Entra ID (directly connected to Citrix Cloud as the SAML provider) → Federated to PingFederate
- Citrix Cloud → Entra ID (directly connected to Citrix Cloud as the SAML provider) → Federated to Okta
Can I get assistance and support from Citrix when debugging SAML issues if I am using an IDP chain?
Citrix support and Citrix Engineering can only debug SAML connections directly between Citrix Cloud and the closest SAML IDP in the chain.
Important:
Citrix is not responsible for debugging issues within a complex IDP chain upstream of the directly connected SAML provider.
Should I avoid IDP chaining if possible?
Citrix recommends directly connecting your SAML IDP to Citrix Cloud as this greatly reduces configuration and debugging complexity and minimises end user logon delays, which can be introduced whilst Citrix Cloud waits for responses from the complex IDP chain. Many issues can arise with both SSO and SLO when multiple IDPs are chained together particularly when different SAML bindings are used by different IDPs within the IDP chain. A directly connected SAML provider will always be easier to debug and more performant than one that relies on upstream IDPs.
Which SAML Binding Mechanism should I choose to use?
Whether to use HTTP POST or HTTP Redirect for SSO and SLO is determined by the SAML bindings your SAML IdP supports. If your SAML provider supports multiple binding mechanisms then Citrix recommends you choose HTTP Post over HTTP Redirect as the SAML binding. There is no need to enable both SAML binding mechanisms on your SAML provider if it supports both. It is recommended you choose a single SAML binding type for both SSO and SLO.
SAML Binding Support
| SAML Binding | Supported by Citrix Cloud |
|---|---|
| HTTP POST | Recommended |
| HTTP Redirect | Supported |
| SAML Artifact binding | Not Supported |
| SOAP | Not Supported |
Important:
HTTP Post is the recommended binding mechanism for both SSO and SLO requests for two reasons.
HTTP Post is easier to debug when signing enforcement is enabled on both sides of the SAML connections as the SAML XML contains easily identifiable sections that show the signature and certificate used. This is easier for humans to see and debug than if this signature data is embedded inside a very long Redirect URI which needs to be URL decoded.
HTTP Redirect URIs can grow very long and exceed a critical threshold which then leads to errors during SAML authentication and can cause login or logout failure. The GET binding type is limited to a maximum of 2,048 characters, minus the number of characters in the actual path. The POST method is not limited by the size of the URL for submitting name and value pairs.
SAML Logout Considerations
For Identity Provider Logout URL (SLO), decide the SAML logout behaviour most appropriate for your organization based on whether the SAML application you wish to connect to Citrix Cloud is also shared by other service providers (SPs) or not.
Citrix recommends creating a new dedicated SAML application within your SAML provider, which is used by only Workspace and/or Citrix Cloud. If you have followed one of Citrix’s SAML application setup guides and you are using a dedicated SAML application for Workspace and/or Citrix Cloud then configuring a Logout URL is always the correct course of action.
Option1 SLO Configured (Recommended): Users signing out of Workspace and/or Citrix Cloud also sign out of the connected SAML IDP.
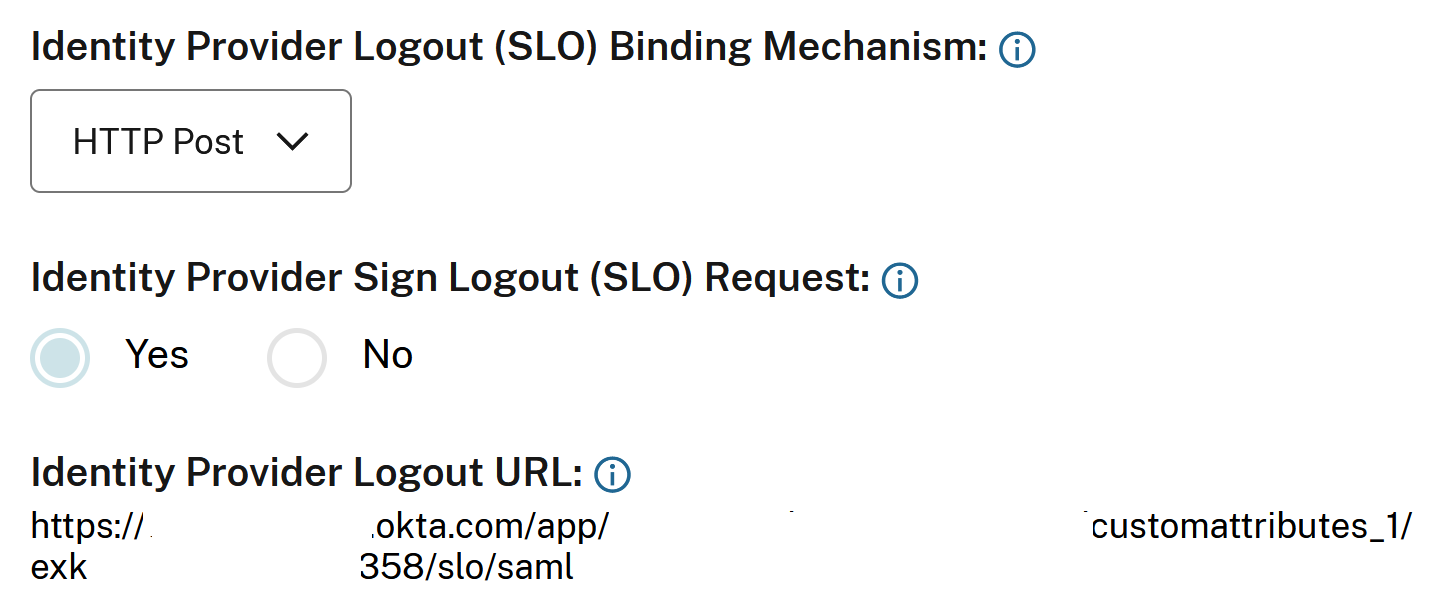
Important:
For SAML SLO to succeed you must configure both sides of the SAML connection to support it. Citrix Cloud expects to receive an SLO response from the SAML application indicating the logout succeeded and the user was logged out of the SAML IDP. Ensure your SAML application is configured to send the SLO response back to Citrix Cloud using this SAML logout endpoint
https://saml.cloud.com/saml/logout/callback.
OR
Option 2 SLO not configured: If you want users to stay signed into your SAML application after signing out of Workspace and/or Citrix Cloud, leave the Logout URL field empty inside the Citrix Cloud SAML connection. When an end user performs an explicit logout in the Workspace or Citrix Cloud UI this will only log the user out of Workspace or Citrix Cloud. The user will not be logged out of the SAML IDP and no SLO request will be sent from Citrix Cloud to the SAML application.
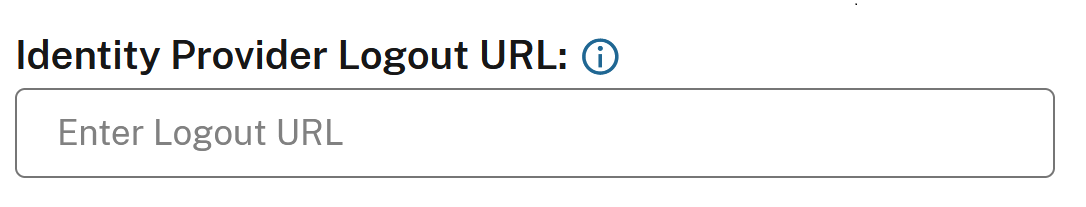
Important:
This SAML Connection configuration without a logout URL configured is only recommended if the SAML application connected to Citrix Cloud is shared by other non Citrix service providers (SPs)
Workspace Session Inactivity Timeout Behaviour
When an end user does not perform any action within Workspaces then the session inactivity timeout will trigger a log off from Workspaces. The Workspaces inactivity timeout is defined in Workspace Configuration → Customize → Preferences → Workspace Sessions.
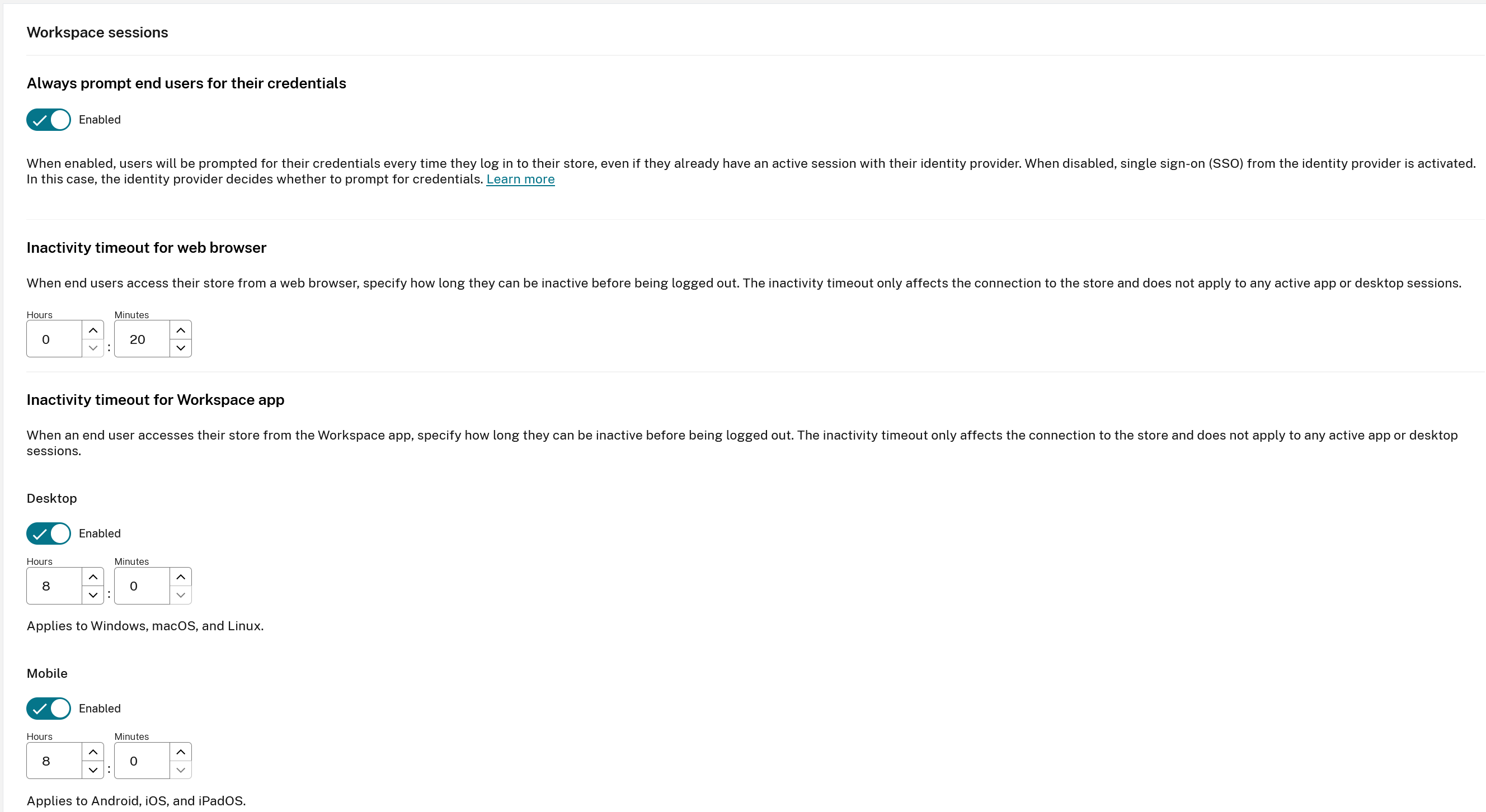
The Workspaces inactivity timeout does not trigger an SLO request to log the end user out of the SAML IdP. The SAML IdP idle session timeout may be a different value to what is set inside Workspace. It is recommended you should set them to be the same duration if possible.
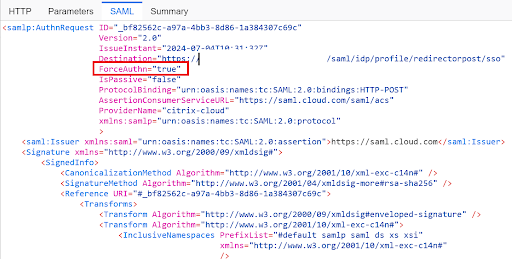
Set Always Prompt End Users for their credentials to Enabled within Workspace Configuration → Customize → Preferences to ensure the end user is always prompted to reauthenticate even if a SAML provider session still exists for the user.
Setting Always Prompt End Users for their credentials to Enabled also sets ForceAuthn to True within the SAML request.
Troubleshooting
Attribute errors
Attribute errors might arise under any of the following conditions:
- The required attributes in your SAML configuration are not encoded correctly.
- The
cip_sidandcip_upnattributes are missing from SAML assertion. - The
cip_sidorcip_oidattributes are missing from the SAML assertion and Citrix Cloud can’t retrieve them from Active Directory due to a connectivity issue.
When an attribute error occurs, Citrix Cloud displays an error message that includes the faulty attributes.
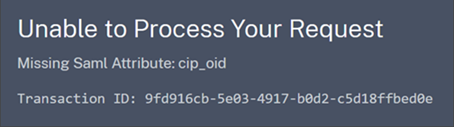
To resolve this type of error:
-
Ensure that your SAML provider sends the required attributes with the correct encoding, as shown in the following table. At a minimum, either the SID or UPN attribute must be included.
Attribute Encoding Required cip_email Must be in String format ( user@domain)cip_oid Must be in Base64 or String format cip_sid Must be in Base64 or String format Yes, if not using cip_upncip_upn Must be String format ( user@domain)Yes, if not using cip_sid -
Verify the Cloud Connectors are online and healthy so Citrix Cloud can retrieve any missing attributes that it needs. For more information, see Cloud Connector advanced health checks.
Unexpected errors
Citrix Cloud might experience an unexpected error when:
- A user initiates a SAML request using an IDP-initiated flow. For example, the request is made by selecting a tile through the identity provider’s app portal instead of navigating directly to the workspace URL (
customer.cloud.com). - The SAML certificate is invalid or has expired.
- The authentication context is invalid.
- SAML assertion and response signature is mismatched.
When this error occurs, Citrix Cloud displays a generic error message.
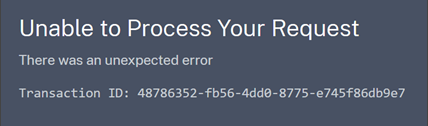
If this error results from navigating to Citrix Cloud through an identity provider’s app portal, you can use the following workaround:
- Create a bookmark app in the identity provider’s app portal that references your workspace URL (for example,
https://customer.cloud.com). - Assign users to both the SAML app and the bookmark app.
- Change the visibility settings of the SAML app and the bookmark app so that the bookmark app is visible and the SAML app is hidden in the app portal.
- Disable the Federated Identity Provider Sessions setting in Workspace Configuration to remove additional password prompts. For instructions, see Federated identity provider sessions in the Citrix Workspace product documentation.
Debugging recommendations
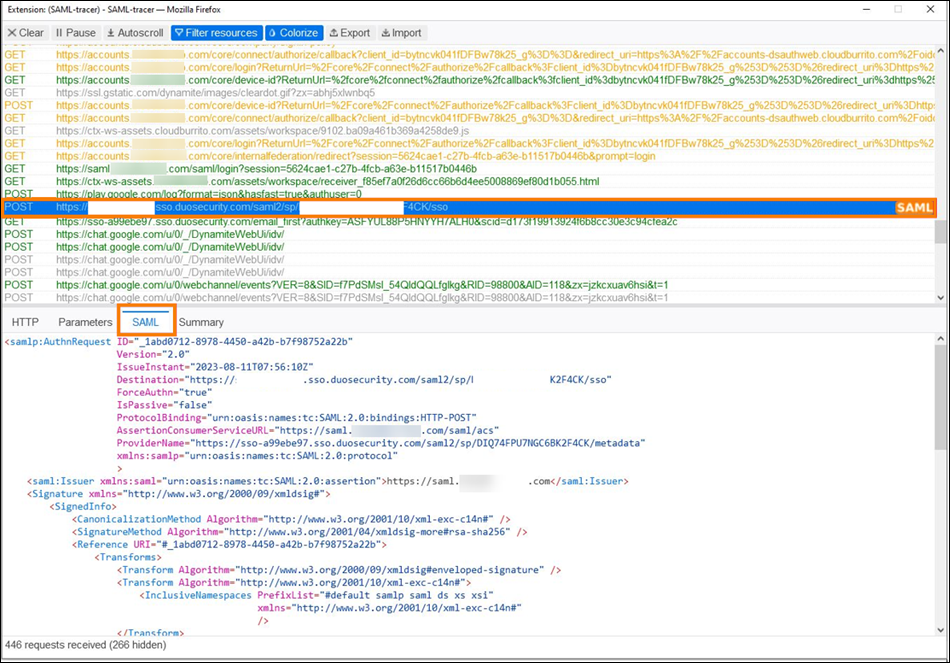
Citrix recommends the use of the SAML-tracer browser extension for all SAML debugging. This extension is available for most common web browsers. The extension decodes Base64-encoded requests and responses into SAML XML, which renders them human-readable.
This tool allows you, as an administrator, to check the value of SAML attributes that are sent for the user and to look for the presence of signatures in SAML requests and responses. In the event you need assistance with a SAML-related issue, Citrix Support requests the SAML-tracer file to understand the issue and resolve your support case.
More information
- Microsoft Docs: Tutorial: Azure Active Directory single sign-on (SSO) integration with Citrix Cloud SAML SSO
- SAML with Active Directory Federated Services (ADFS): Configure SAML authentication in Citrix Cloud using ADFS
- Citrix Tech Zone: Tech Insight: Authentication - SAML
In this article
- About this article
- Supported SAML providers
- Support for scoped Entity IDs
- Prerequisites
- Administrator authentication with SAML 2.0
- Task overview for setting up a new SAML connection
- Task overview for using an existing SAML connection for Citrix Cloud administrators
- Create and map custom SAML attributes
- Configure the administrator sign-in URL
- Configure the SAML provider metadata
- Add administrators to Citrix Cloud from AD
- Enable SAML authentication for workspaces
- Cloning an existing SAML connection within identity and access management
- Service Provider Initiated SSO vs Identity Provider Initiated SSO
- Directly Connecting the SAML Provider to Citrix Cloud VS IDP Chaining
- Which SAML Binding Mechanism should I choose to use?
- SAML Logout Considerations
- Workspace Session Inactivity Timeout Behaviour
- Troubleshooting
- More information