-
-
WebSocket communication between VDA and Delivery Controller™
-
-
Migrate workloads between resource locations using Image Portability Service
-
-
-
NAT Compatibility
-
-
-
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
NAT Compatibility
To establish a direct connection between an external user device and the session host, HDX™ Direct leverages hole punching for NAT traversal and STUN to facilitate the exchange of the public IP address and port mappings for the client device and session host. This is similar to how VoIP, unified communications, and P2P solutions work.
As long as firewalls and other network components are configured to allow the UDP traffic for the STUN requests and the HDX sessions, HDX Direct for external users is expected to work. However, there are certain scenarios where the NAT types of the user and session host networks lead to an incompatible combination, thus causing HDX Direct to fail.
Validations
You can validate the NAT type and filtering on the client and the session host by using STUNTMAN’s STUN client utility:
- Download the appropriate package for the target platform from stunprotocol.org, and extract the contents.
- Open a terminal prompt and navigate to the directory where the contents were extracted.
- Run the following command:
.\stunclient.exe stunserver.stunprotocol.org --mode behavior -
Take note of the output.
If the binding and behavior tests are successful, both binding test and behavior test report the success and a NAT behavior is specified:
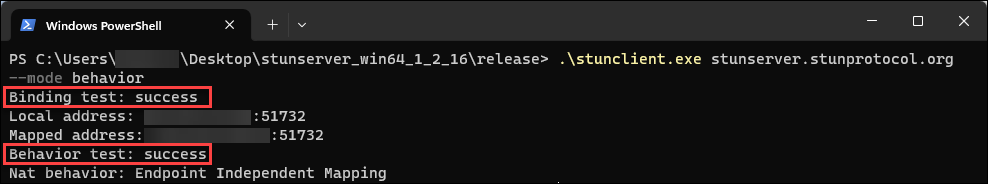
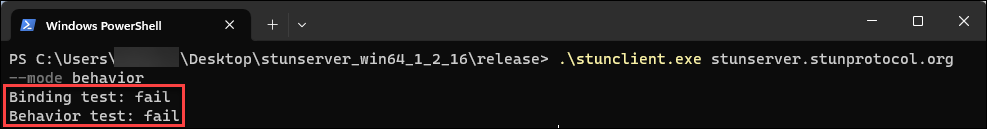
If the tests fail, both binding test and behavior test report the failure.
- Run the following command:
.\stunclient.exe stunserver2024.stunprotocol.org --mode filtering - Take note of the output.
See the following table to determine if HDX Direct for external users is expected to work based on the test results of both the client and session host:
| Client NAT Behavior | Client NAT Filtering | Session Host NAT Behavior | Session Host NAT Filtering | Expected to work? |
|---|---|---|---|---|
| Endpoint Independent Mapping | Any | Endpoint Independent Mapping | Any | Yes |
| Endpoint Independent Mapping | Endpoint Independent Filtering | Address Dedependent Mapping | Any | Yes |
| Endpoint Independent Mapping | Address Dependent Filtering | Address Dedependent Mapping | Any | No |
| Endpoint Independent Mapping | Address and Port Dependent Filtering | Address Dedependent Mapping | Any | No |
| Endpoint Independent Mapping | Endpoint Independent Filtering | Address and Port Dedependent Mapping | Endpoint Independent Filtering | Yes |
| Endpoint Independent Mapping | Address Dependent Filtering | Address Dedependent Mapping | Any | No |
| Endpoint Independent Mapping | Address and Port Dependent Filtering | Address Dedependent Mapping | Any | No |
| Address Dependent Mapping | Any | Endpoint Independent Mapping | Endpoint Independent Filtering | Yes |
| Address Dependent Mapping | Any | Endpoint Independent Mapping | Address Dependent Filtering | No |
| Address Dependent Mapping | Any | Endpoint Independent Mapping | Address and Port Dependent Filtering | No |
| Address Dependent Mapping | Any | Address Dependent Mapping | Any | No |
| Address Dependent Mapping | Any | Address and Port Dependent Mapping | Any | No |
| Address and Port Dependent Mapping | Any | Endpoint Independent Mapping | Endpoint Independent Filtering | Yes |
| Address and Port Dependent Mapping | Any | Endpoint Independent Mapping | Address Dependent Filtering | No |
| Address and Port Dependent Mapping | Any | Endpoint Independent Mapping | Address and Port Dependent Filtering | No |
| Address and Port Dependent Mapping | Any | Address Dependent Mapping | Any | No |
| Address and Port Dependent Mapping | Any | Address and Port Dependent Mapping | Any | No |
| Fail | Any | Any | Any | No |
| Any | Any | Fail | Any | No |
| Fail | Any | Fail | Any | No |
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.