Adaptive access and security controls for Enterprise Web and SaaS applications – Preview
In today’s ever changing situations, application security is vital for any businesses. Making context-aware security decisions and then enabling access to the applications reduces the associated risks while enabling access to users.
The Citrix Secure Private Access™ service adaptive access feature offers a comprehensive zero-trust access approach that delivers secure access to the applications. Adaptive access enables admins to provide granular level access to the apps that users can access based on the context. The term “context” here refers to users, user groups, device posture, and the platform (mobile device or a desktop computer) from which the user is accessing the application.
The adaptive access feature applies contextual policies to the applications that are being accessed. These policies determine the risks based on the context and make dynamic access decisions to grant or deny access to the Enterprise Web or SaaS apps.
How it works
To grant or deny access to applications, admins create policies based on the users, user groups, the devices from which the users access the applications, the location (country or network location) from where the user is accessing the application, and the user risk score.
The adaptive access policies take precedence over the application specific security policies that are configured while adding the SaaS or a Web app in the Secure Private Access service.
For example, consider that the Microsoft Word app is subscribed to users, Emp1 and Emp2. The enhanced security options such as restrict printing, restrict downloads, and display watermark are enabled for the application while adding the app in the Secure Private Access service.
The admin must create a policy to apply app level policy. If the contextual policy does not match based on the context, it automatically falls back to app level policy. Then, the admin can create another policy with no contextual security controls for Emp2.
In this scenario, the enhanced security options are applied when the Emp1 accesses the app. However, for Emp2, the adaptive access policy overwrites the app level policies and hence the enhanced security options are not enforced for Emp2.
The adaptive access policies are evaluated in three scenarios:
Customers entitled for adaptive access
Customers entitled for the Citrix Secure Private Access service get the adaptive access feature at no additional cost. In addition, the adaptive access feature must be enabled for that customer.
Create an adaptive access policy
- On the Secure Private Access service tile, click Manage.
- Click the Manage tab and then click Adaptive Access.
-
Click Create Policy.
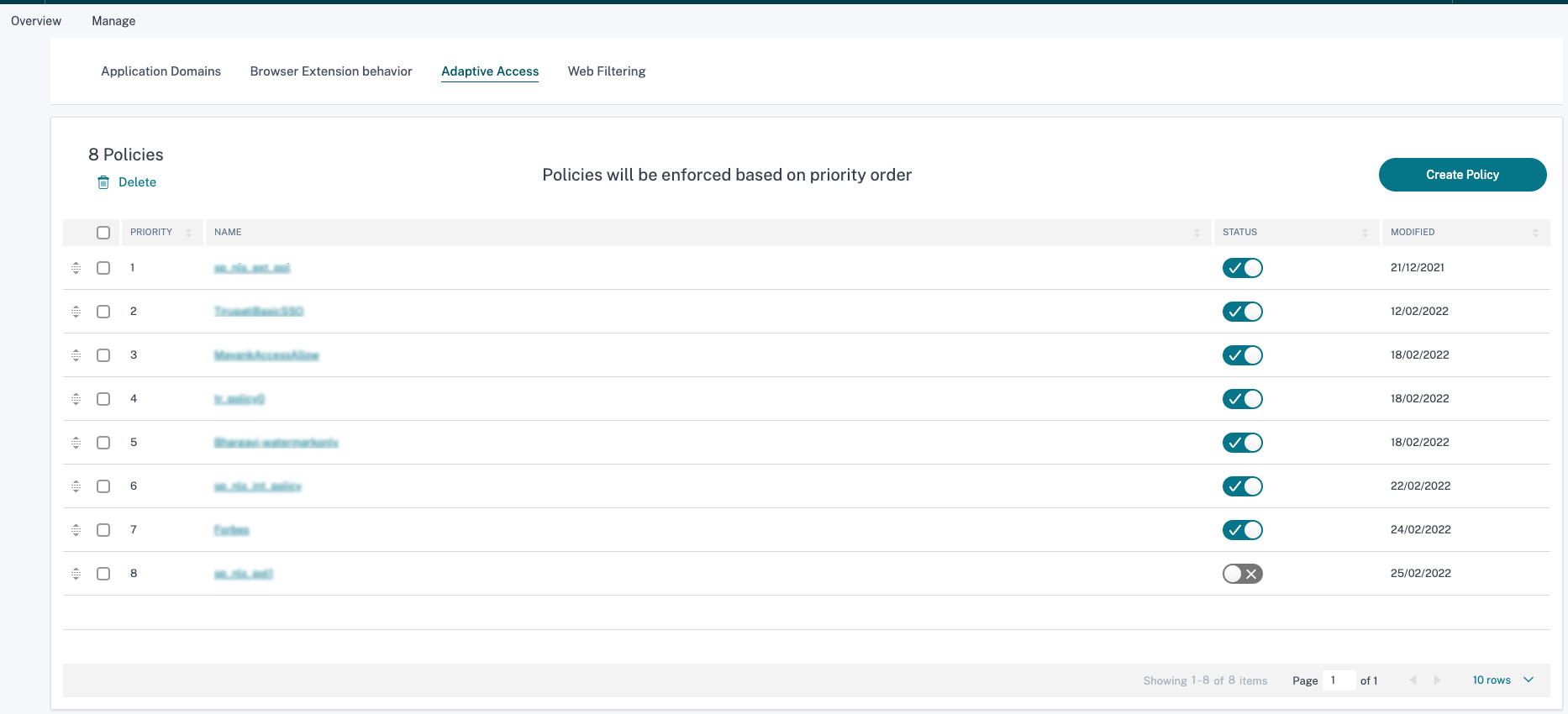
-
FOR USERS OF THESE APPLICATIONS - This field lists all the applications that an admin has configured in the Secure Private Access service. Admins can select the applications to which this contextual policy must be applied.
-
IF THE FOLLOWING CONDITION IS MET - Select the context for which this adaptive access policy must be evaluated.

-
Click Add Condition to add extra conditions, based on your requirement. An AND operation is performed on the conditions, and then the adaptive access policy is evaluated.

-
THEN DO THE FOLLOWING - If the set condition matches, admins can select the action to be performed for the users accessing the application.
- Deny access – When selected, access to the apps is denied. All other options are grayed out.
-
Allow app access with the following security controls – Select one of the preset security policy combinations. These security policy combinations are predefined in the system. Admins cannot modify or add other combinations.
To apply a different preset security policy to the same set of applications that you have selected, then admins have to create a policy and the select the security policy combination.
- App access from Citrix Workspace™ desktop clients only - Select this option to allow users to access apps from the Citrix Workspace desktop clients only.
- Launch an application through the secure browser – Select this option to always launch an application in the Remote Browser Isolation service regardless of other enhanced security settings.
Note:
-
The options Preset 4, Preset 5, and Preset 6 are enabled only for Enterprise web apps. If an admin has selected a SaaS app along with web apps in the list of apps, then the options Preset 4, Preset 5, and Preset 6 are disabled.
-
Admins can select a preset security policy and also select the option to launch an application through the secure browser in the same policy. Both the conditions are independent of each other.
- In POLICY NAME, enter the name of the policy.
- Turn the toggle switch ON to enable the policy.
- Click Create Policy.
Adaptive access based on users or groups
To configure an adaptive access policy based on users or groups, use the Create an adaptive access policy procedure with the following changes.
-
In IF THE FOLLOWING CONDITION IS MET, select Users or groups.
- If you have configured multiple users or groups, then select one of the following as per your requirement.
- Match all of – The users or groups must match all the users or groups configured in the database.
- Does not match any – The users or groups do not match with the users or groups configured in the database.
- Complete the policy configuration.

Adaptive access based on devices
To configure an adaptive access policy based on the platform (mobile device or a desktop computer) from which the user is accessing the application, use the Create an adaptive access policy procedure with the following changes.
- In IF THE FOLLOWING CONDITION IS MET, select Desktop or Mobile device.
- Complete the policy configuration.
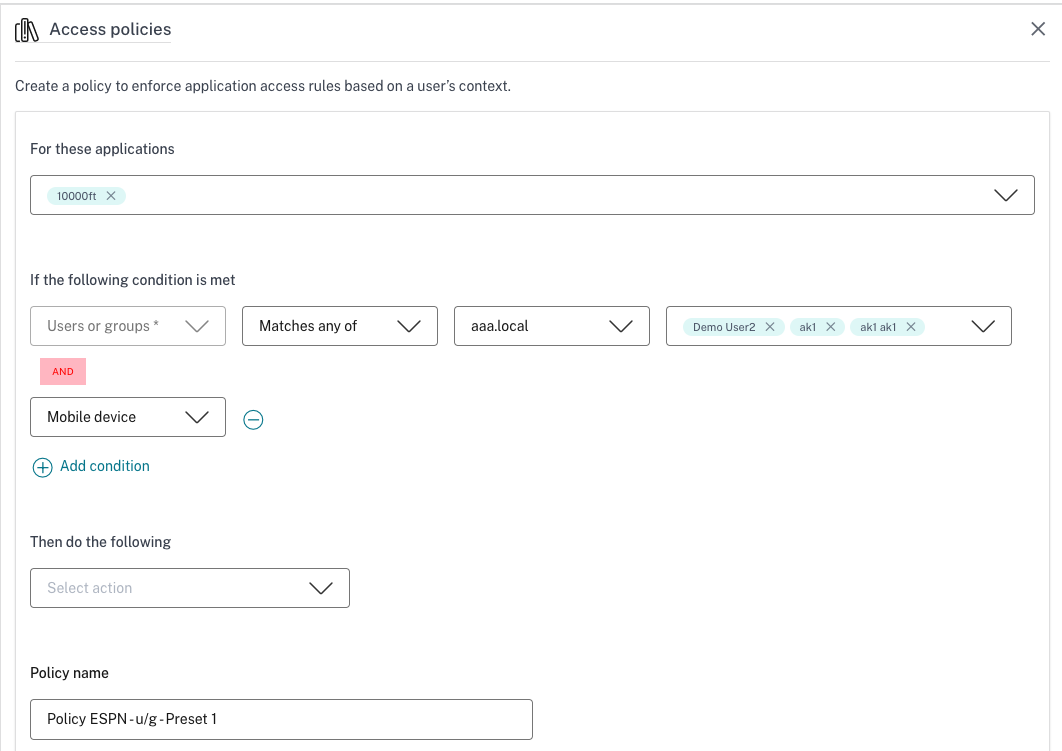
Adaptive access based on the location
An admin can configure the adaptive access policy based on the location from where the user is accessing the application. The location can be the country from where the user is accessing the application or the user’s network location. The network location is defined using an IP address range or subnet addresses.
To configure an adaptive access policy based on the location, use the Create an adaptive access policy procedure with the following changes.
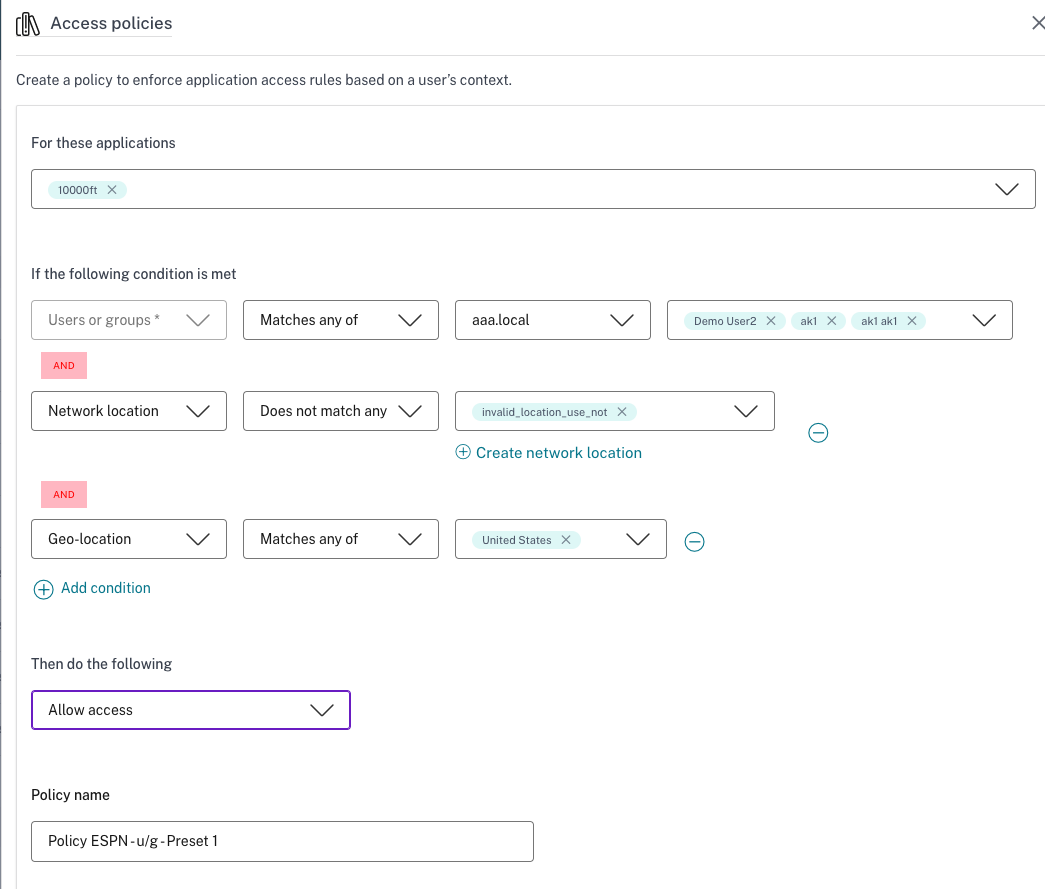
- In IF THE FOLLOWING CONDITION IS MET, select Geo-location or Network location.
- If you have configured multiple geo-locations or network locations, then select one of the following as per your requirement.
- Match all of – The geographic locations or network locations must match all the geographic locations or network locations configured in the database.
- Does not match any – The geographic locations or network locations do not match with the geographic locations or network locations configured in the database.
Note:
-
If you select Geo-location, the source IP address of the user is evaluated with the IP address database. If the IP addresses of the user and the address available in the database match, the policy is applied. If the IP addresses do not match, this contextual policy is skipped and the next contextual policy is evaluated.
-
For Network location, you can select an existing network location or create a network location. To create a new network location, click Create network location.
Important:
When you create a network location, the new network location might not be visible in the drop-down list insantly. It might take around 5 minutes for the new network location to appear in the drop-down list.
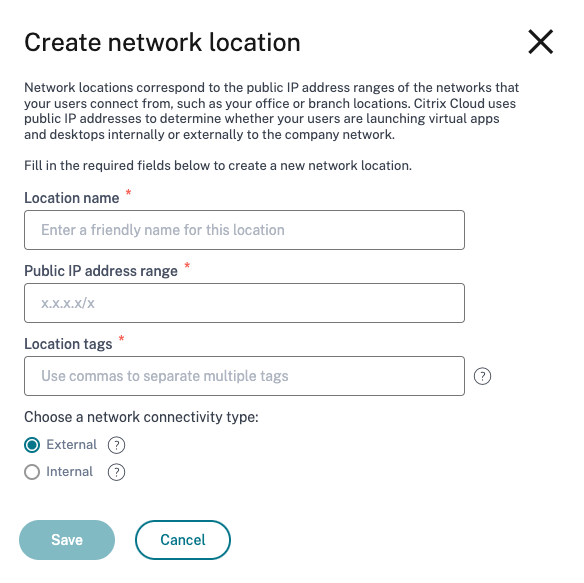
- You can also create a network location from the Citrix Cloud console. For details, see Citrix Cloud network location configuration.
- Complete the policy configuration.
Adaptive access based on the device posture
The Citrix Secure Private Access service provides adaptive access based on a device posture by using an on-premises Citrix Gateway or a customer hosted Citrix Gateway (adaptive authentication) as an IdP to Citrix Workspace. The Enterprise Web or SaaS apps can either be enumerated or hidden from the end user based on the EPA check results and the configured smart access policy.
Note: Adaptive authentication is a Citrix Cloud™ service that enables advanced authentication for users logging in to Citrix Workspace. Adaptive authentication gives a gateway instance running in cloud and you can configure the authentication mechanism for this instance, as required.
Prerequisites
- Citrix Gateway as an IdP must be configured for Citrix Workspace. For details, see Use an on-premises Citrix Gateway as the identity provider for Citrix Cloud.
- Citrix ADC release version 13.0 Build 82.109 or later.
- Smart access tags are configured on the Citrix Gateway appliance.
Understanding the flow of events
- User enters the Workspace URL into a browser or connects to a Workspace Store using a native Citrix Workspace App.
- User is redirected to the Citrix Gateway configured as an IdP.
- User is prompted to allow an EPA check to be performed on the device.
- Citrix Gateway performs an EPA check after the user consents to scan the device and writes the smart access tags to CAS against the device ID.
- User logs in to Citrix Workspace using Citrix Gateway IdP and the configured authentication mechanism.
- Citrix Gateway provides smart access policy information to Citrix Workspace and Secure Private Access.
- User is redirected to the Citrix Workspace home page.
- Citrix Workspace processes the smart access tags provided by the Citrix Gateway configured as an IdP, and then determines the apps that must be enumerated and displayed to the end user.
Configuration scenario – Enterprise Web or SaaS app enumeration based on device posture scans
Step 1: Configure smart access policies using Citrix Gateway GUI
- Navigate to Security > AAA-Application Traffic > Policies > Authentication > Advanced Policies> Smart Access > Profiles.
- On the Profiles tab, click Add to create a profile.
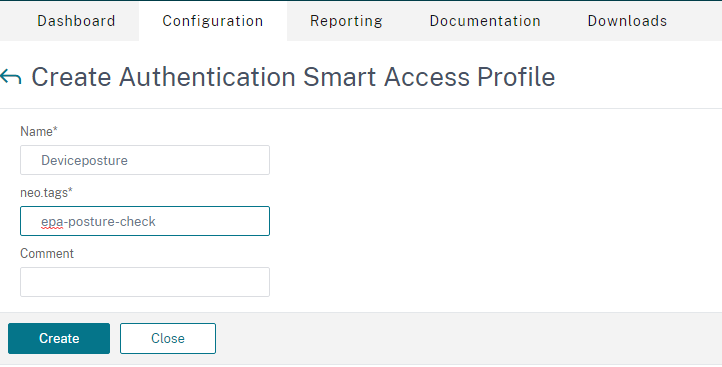
- In Tags, enter the smart access tag name. This is the tag that you must enter manually when creating the adaptive access policy.
- Navigate to Security > AAA-Application Traffic > Policies > Authentication > Advanced Policies> Smart Access > Policies.
- Click Add to create a policy.

- In Action, select the previously created profile and click Add.
- In Expression, create the policy expression and click OK.
Step 2: Create an adaptive access policy
Perform the steps detailed in Create an adaptive access policy.

- In IF THE FOLLOWING CONDITION IS MET, select Device posture check.
- If you have configured multiple smart access tags, then select one of the following as per your requirement.
- Match all of – The device ID must match all the smart access tags written against the device ID when you log in to Citrix Workspace.
- Match any of – The device ID must match one of the tags written against the device ID when you log in to Citrix Workspace.
- Does not match any - The device ID does not match against the device ID when you log into Citrix Workspace.
- In Enter custom tags, manually type the smart access tag. These tags must be similar to the tags configured in Citrix Gateway (Create Authentication Smart Access Profile > Tags).
Points to note
- Posture evaluation occurs only when you log on to Citrix Workspace (only during the authentication).
- In the current release, continuous device posture evaluation is not done. If the device context changes after the user logs on to Citrix Workspace, then the policy conditions do not have any impact on the device posture evaluation.
- Device ID is a GUID generated for each end user device. Device ID might change if the browser used to access Citrix Workspace is changed, cookies are deleted or incognito/private mode is used. However, this change does not impact the policy evaluation.
Adaptive access based on user risk score
User risk score is a scoring system to determine the risks associated with the user activities in your enterprise. Risk indicators are assigned to user activities that look suspicious or can pose a security threat to your organization. The risk indicators are triggered when the user’s behavior deviates from the normal. Each risk indicator can have one or more risk factors associated with it. These risk factors help you to determine the type of anomalies in the user events. The risk indicators and their associated risk factors determine the risk score of a user. The risk score is calculated periodically and there is a delay between the action and the update in the risk score. For details, see Citrix user risk indicators.
To configure an adaptive access policy with risk score, use the Create an adaptive access policy procedure with the following changes.
-
In IF THE FOLLOWING CONDITION IS MET, select User risk score.
-
Configure the adaptive access policy based on the following three types of user risk conditions.
- Preset tags fetched from CAS service
– LOW
- MEDIUM
- HIGH
- Threshold types
- Greater than or equal to
- Less than or equal to
- A number range
- Range
- Preset tags fetched from CAS service
– LOW

