Network device policy
The network device policy lets you manage how users connect their devices to Wi-Fi networks by defining the following items:
- Network names and types
- Authentication and security policies
- Proxy server use
- Other Wi-Fi related details
To add or configure this policy, go to Configure > Device Policies. For more information, see Device policies.
Prerequisites
Before you create a policy, complete the following:
- Create any delivery groups that you plan to use.
- Know the network name and type.
- Know any authentication or security types that you plan to use.
- Know any proxy server information that you might need.
- Install any necessary CA certificates.
- Have any necessary shared keys.
- Create the PKI entity for certificate-based authentication.
- Configure credential providers.
For more information, see Authentication and its subarticles.
iOS settings
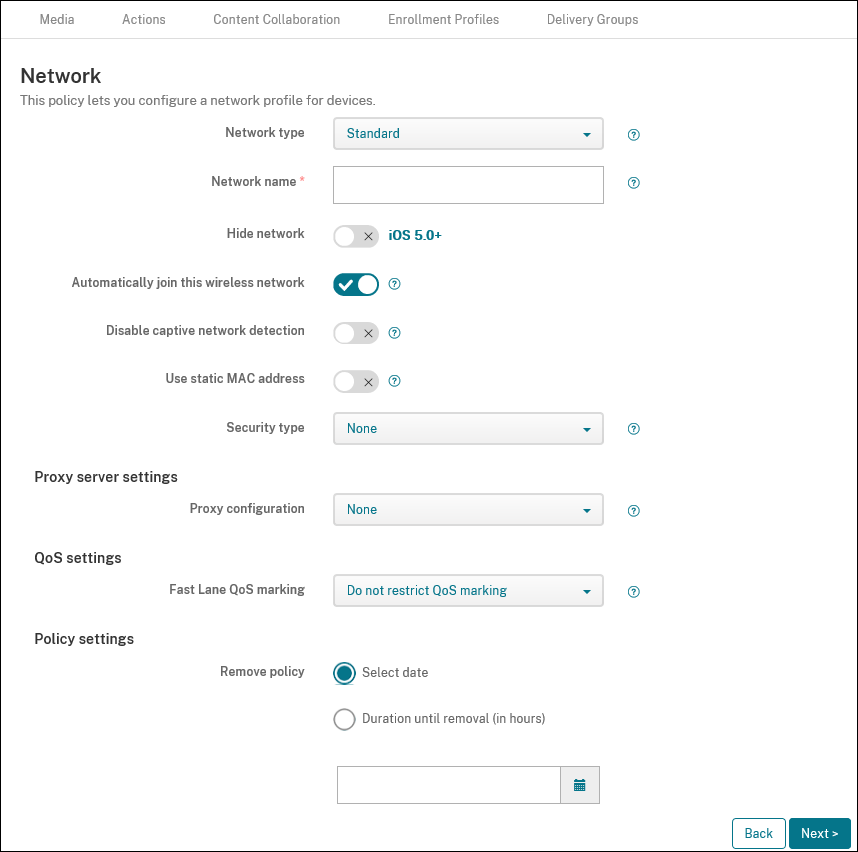
- Network type: In the list, choose Standard, Legacy Hotspot, or Hotspot 2.0 to set the network type you plan to use.
- Network name: Type the SSID that is seen in the list of available networks for the device. Does not apply to Hotspot 2.0.
- Hide network: Choose whether the network is hidden.
- Automatically join this wireless network: Choose whether a device joins the network automatically. If a device is connected to another network, it doesn’t join this network. The user must disconnect from the previous network before the device automatically connects. The default is On.
- Disable captive network detection: The captive network assistant helps users access subscription or Wi-Fi Hotspot networks. You typically find these networks in coffee shops, hotels, and other public locations. If On, devices can still connect to captive networks, but the user must open a browser and log in manually. The default is Off.
- Use static MAC address: MAC addresses are unique identifiers that a device transmits within a network. To increase privacy, iOS and iPadOS devices can use a different MAC address each time they connect to a network. If On, the device always uses the same MAC address when connecting to this network. If Off, the device uses a different MAC address every time it connects to this network. The default is Off.
-
Security type: In the list, choose the security type you plan to use. Does not apply to Hotspot 2.0.
- None - Requires no further configuration.
- WEP
- WPA/WPA2/WPA3 Personal
- Any (Personal)
- WEP Enterprise
- WPA/WPA2/WPA3 Enterprise: For the latest release of Windows 10, configure the Simple Certificate Enrollment Protocol (SCEP) to use WPA-2 Enterprise. Citrix Endpoint Management can then send the certificate to the devices to authenticate to the Wi-Fi server. To configure SCEP, go to the Distribution page of Settings > Credential Providers. For more information, see Credential providers.
- Any (Enterprise)
The following sections list the options that you configure for each of the preceding connection types.
-
Proxy server settings
- Proxy configuration: In the list, choose None, Manual, or Automatic to set how the VPN connection routes through a proxy server and then configure any additional options. The default is None, which requires no further configuration.
- If you choose Manual, configure these settings:
- Host name or IP address: Type the host name or IP address of the proxy server.
- Port: Type the proxy server port number.
- User name: Type an optional user name to authenticate to the proxy server.
- Password: Type an optional password to authenticate to the proxy server.
- If you choose Automatic, configure these settings:
- Server URL: Type the URL of the PAC file that defines the proxy configuration.
- Allow direct connection if PAC is unreachable: Choose whether to allow users to connect directly to the destination if the PAC file is unreachable. The default is On.
-
Fast Lane QoS marking: If you don’t restrict QoS marking for a Wi-Fi network that supports Cisco Fast Lane QoS, all apps are allowed to use L2 and L3 marking. If you restrict QoS marking, specify the apps that can use L2 and L3 marking.
- Enable QoS marking: If you restrict QoS marking, use this setting to disable it completely or only mark certain apps. If Off, you disable QoS marking entirely. If On, configure a list of apps that can use QoS marking. The default is On.
- Allow Apple audio/video calling: Choose whether audio and video calling apps can use QoS marking. If Off, the quality of video and audio calls can suffer.
- Allow specific apps: Add an app package ID to this list to allow the app to use QoS marking.
-
Hotspot 2.0 settings
- Displayed operator name: The friendly name broadcast by the Hotspot device. Users see this name in their list of available Wi-Fi networks.
- Domain name: The domain name used for Hotspot 2.0 negotiation.
- Allow connecting to roaming partner networks: If On, devices roaming off their home network can connect to partner networks.
- Roaming Consortium Organization Identifiers (OI): Add a list of organization identifiers that the device can access. A Roaming Consortium OI belongs to an organization with shared authentication methods. If the Hotspot you configure isn’t available, the device connects to a Roaming Consortium OI listed here.
-
Network Access Identifier (NAI) realm names: Configure a list of realm names used to identify users to a roaming network. A NAI transmits in the form
user@realm. - Mobile Country Codes (MCCs) and Mobile Network Configurations (MNCs): A Mobile Country Code consists of three digits that identify the country of a network. The Mobile Network Code consists of 2 or 3 unique digits. When used together, the MCC/MNC uniquely identifies a mobile network operator or carrier.
-
Policy settings
-
Remove policy: Choose a method for scheduling policy removal. Available options are Select date and Duration until removal (in hours)
- Select date: Click the calendar to select the specific date for removal.
- Duration until removal (in hours): Type a number, in hours, until policy removal occurs.
- Allow user to remove policy: You can select when users can remove the policy from their device. Select Always, Passcode required, or Never from the menu. If you select Passcode required, type a passcode in the Removal passcode field. Not available for iOS.
-
Remove policy: Choose a method for scheduling policy removal. Available options are Select date and Duration until removal (in hours)
WPA, WPA Personal, Any (Personal) settings for iOS
Password: Type an optional password. If you leave this field blank, users might be prompted for their passwords when they log on.
WEP Enterprise, WPA Enterprise, WPA2 Enterprise, WPA3 Enterprise, Any (Enterprise) settings for iOS
When you choose any of these security types, EAP settings appear after QoS settings.
Important:
If you select the WPA2 Enterprise security type, you must allow at least one EAP protocol.
- Allowed EAP protocols: Enable the EAP types that you want to support and then configure the associated settings. The default is Off for each of the available EAP types.
- Inner authentication (TTLS): Required only when you enable TTLS. In the list, choose the inner authentication method to use. Options are: PAP, CHAP, MSCHAP, or MSCHAPv2. The default is MSCHAPv2.
-
EAP-FAST with PAC: Choose whether to use protected access credentials (PACs).
- If you choose Use PAC, choose whether to use a provisioning PAC.
- If you choose Provisioning PAC, choose whether to allow an anonymous TLS handshake between the end-user client and Citrix Endpoint Management.
- Provisioning PAC anonymously
- If you choose Provisioning PAC, choose whether to allow an anonymous TLS handshake between the end-user client and Citrix Endpoint Management.
- If you choose Use PAC, choose whether to use a provisioning PAC.
-
Authentication:
- User name: Type a user name.
- Per-connection password: Choose whether to require a password each time that users log on.
- Password: Type an optional password. If you leave this field blank, users might be prompted for their passwords when they log on.
- Identity credential (keystore or PKI credential): In the list, choose the type of identity credential. The default is None.
- Outer identity: Required only when you enable PEAP, TTLS, or EAP-FAST. Type the externally visible user name. You can increase security by typing a generic term such as “anonymous” so that the user name isn’t visible.
- Require a TLS certificate: Choose whether to require a TLS certificate.
-
Trust
-
Trusted certificates: To add a trusted certificate, click Add and, for each certificate you want to add, do the following:
- Application: In the list, choose the application you want to add.
- Click Save to save the certificate or click Cancel.
-
Trusted server certificate names: To add trusted server certificate common names, click Add and, for each name you want to add, do the following:
- Certificate: Type the name of the server certificate. You can use wildcards to specify the name, such as wpa.*.example.com.
- Click Save to save the certificate name or click Cancel.
-
Trusted certificates: To add a trusted certificate, click Add and, for each certificate you want to add, do the following:
- Allow trust exceptions: Choose whether the certificate trust dialog appears on users devices when a certificate is untrusted. The default is On.
macOS settings
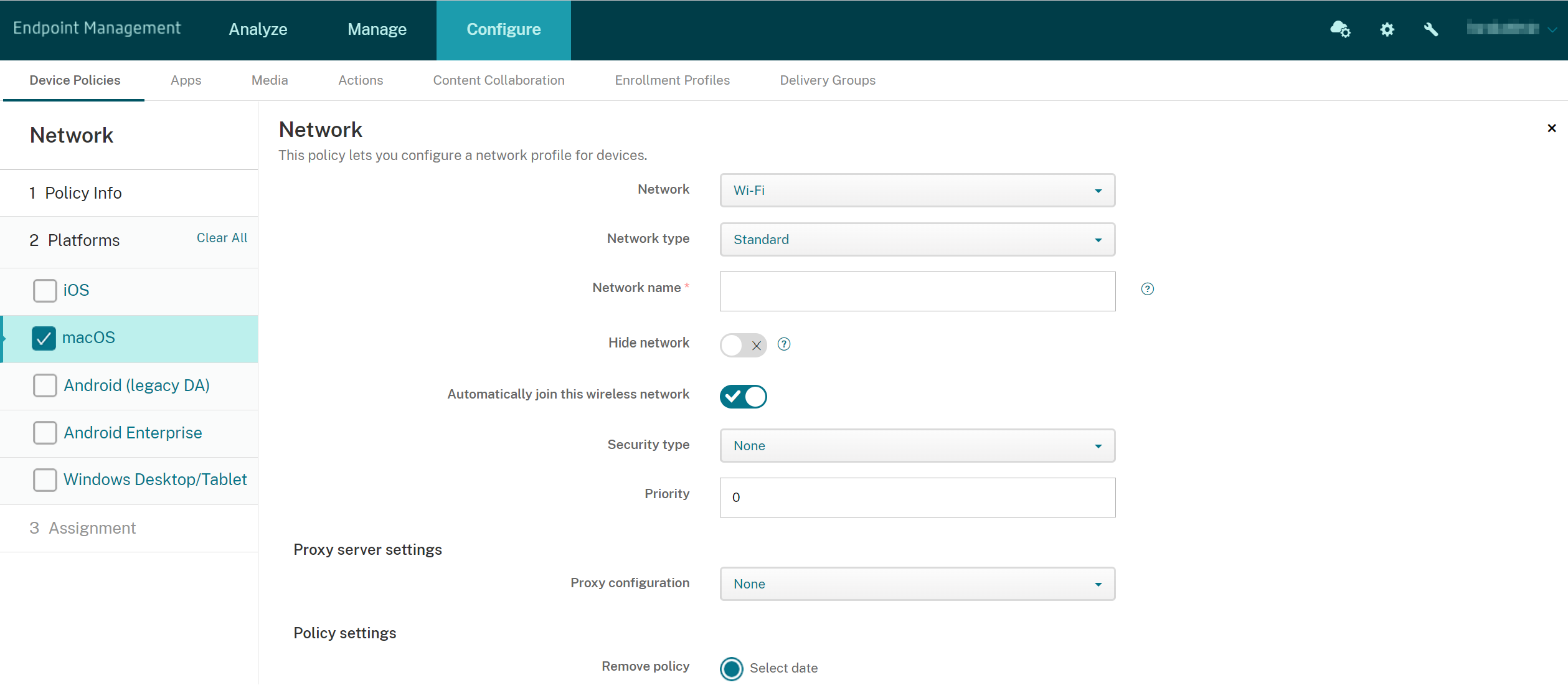
-
Network: In the list, choose the network option you plan to use. The default is Wi-Fi.
- Wi-Fi
- Global Ethernet
- First Active Ethernet
- Second Active Ethernet
- Third Active Ethernet
- First Ethernet
- Second Ethernet
- Third Ethernet
- Network type: In the list, choose Standard, Legacy Hotspot, or Hotspot 2.0 to set the network type you plan to use.
- Network name: Type the SSID that is seen in the list of available networks for the device. Does not apply to Hotspot 2.0.
- Hide network: Choose whether the network is hidden.
- Automatically join this wireless network: Choose whether the network is joined automatically. If a device is already connected to another network, it doesn’t join this network. The user must disconnect from the previous network before the device automatically connects. The default is On.
-
Security type: In the list, choose the security type you plan to use. Does not apply to Hotspot 2.0.
- None - Requires no further configuration.
- WEP
- WPA/WPA2 Personal
- Any (Personal)
- WEP Enterprise
- WPA/WPA2 Enterprise
- Any (Enterprise)
The following sections list the options that you configure for each of the preceding connection types.
- Priority: For multiple networks, type a number to define the priority of the network connection. The device connects to the network with the lowest priority number first. Negative numbers are acceptable. The default is 0.
-
Proxy server settings
- Proxy configuration: In the list, choose None, Manual, or Automatic to set how the VPN connection routes through a proxy server and then configure any additional options. The default is None, which requires no further configuration.
- If you choose Manual, configure these settings:
- Host name or IP address: Type the host name or IP address of the proxy server.
- Port: Type the proxy server port number.
- User name: Type an optional user name to authenticate to the proxy server.
- Password: Type an optional password to authenticate to the proxy server.
- If you choose Automatic, configure these settings:
- Server URL: Type the URL of the PAC file that defines the proxy configuration.
- Allow direct connection if PAC is unreachable: Choose whether to allow users to connect directly to the destination if the PAC file is unreachable. The default is On.
-
Hotspot 2.0 settings
- Displayed operator name: The friendly name broadcast by the Hotspot device. Users see this name in their list of available Wi-Fi networks.
- Domain name: The domain name used for Hotspot 2.0 negotiation.
- Allow connecting to roaming partner networks: If On, devices roaming off their home network can connect to partner networks.
- Roaming Consortium Organization Identifiers (OI): Add a list of organization identifiers that the device can access. A Roaming Consortium OI belongs to an organization with shared authentication methods. If the Hotspot you configure isn’t available, the device connects to a Roaming Consortium OI listed here.
-
Network Access Identifier (NAI) realm names: Configure a list of realm names used to identify users to a roaming network. A NAI transmits in the form
user@realm. - Mobile Country Codes (MCCs) and Mobile Network Configurations (MNCs): A Mobile Country Code consists of three digits that identify the country of a network. The Mobile Network Code consists of 2 or 3 unique digits. When used together, the MCC/MNC uniquely identifies a mobile network operator or carrier.
-
Policy settings
-
Remove policy: Choose a method for scheduling policy removal. Available options are Select date and Duration until removal (in hours)
- Select date: Click the calendar to select the specific date for removal.
- Duration until removal (in hours): Type a number, in hours, until policy removal occurs.
- Allow user to remove policy: You can select when users can remove the policy from their device. Select Always, Passcode required, or Never from the menu. If you select Passcode required, type a passcode in the Removal passcode field.
- Profile scope: Select whether this policy applies to a User or an entire System. The default is User. This option is available only on macOS 10.7 and later.
-
Remove policy: Choose a method for scheduling policy removal. Available options are Select date and Duration until removal (in hours)
WPA, WPA Personal, WPA 2 Personal, Any (Personal) settings for macOS
- Password: Type an optional password. If you leave this field blank, users might be prompted for their passwords when they log on.
WEP Enterprise, WPA Enterprise, WPA2 Enterprise, Any (Enterprise) settings for macOS
-
Connection mode: If On, choose the connection mode to use when the user joins the network. The default is Off.
- System: If marked, the device uses the system credentials to authenticate the user. The default is cleared.
- Login window: If marked, the device uses the same credentials entered at the login window to authenticate the user. The default is cleared.
When you choose any of these security types, EAP settings appear after QoS settings.
Important:
If you select the WPA2 Enterprise security type, you must allow at least one EAP protocol.
- Allowed EAP protocols: Enable the EAP types that you want to support and then configure the associated settings. The default is Off for each of the available EAP types.
- Inner authentication (TTLS): Required only when you enable TTLS. In the list, choose the inner authentication method to use. Options are: PAP, CHAP, MSCHAP, or MSCHAPv2. The default is MSCHAPv2.
-
EAP-FAST with PAC: Choose whether to use protected access credentials (PACs).
- If you select Use PAC, choose whether to use a provisioning PAC.
- If you choose Provisioning PAC, choose whether to allow an anonymous TLS handshake between the end-user client and Citrix Endpoint Management.
- Provisioning PAC anonymously
- If you choose Provisioning PAC, choose whether to allow an anonymous TLS handshake between the end-user client and Citrix Endpoint Management.
- If you select Use PAC, choose whether to use a provisioning PAC.
-
Authentication:
-
Use Active Directory authentication: Choose whether to enable Active Directory authentication. Available for macOS 10.7 and later. To make this option available, complete the following:
- Set PEAP as the EAP protocol.
- Set the profile scope to System. You can use this setting option only when you apply the policy to the entire system.
- User name: Type a user name.
- Per-connection password: Choose whether to require a password each time users log on.
- Password: Type an optional password. If you leave this field blank, users might be prompted for their passwords when they log on.
- Identity credential (keystore or PKI credential): In the list, choose the type of identity credential. The default is None.
- Outer identity: Required only when you enable PEAP, TTLS, or EAP-FAST. Type the externally visible user name. You can increase security by typing a generic term like “anonymous” so that the user name isn’t visible.
- Require a TLS certificate: Choose whether to require a TLS certificate.
-
Use Active Directory authentication: Choose whether to enable Active Directory authentication. Available for macOS 10.7 and later. To make this option available, complete the following:
-
Trust
-
Trusted certificates: To add a trusted certificate, click Add and, for each certificate you want to add, do the following:
- Application: In the list, choose the application you want to add.
- Click Save to save the certificate or click Cancel.
-
Trusted server certificate names: To add trusted server certificate common names, click Add and, for each name you want to add, do the following:
- Certificate: Type the name of the server certificate that you want to add. You can use wildcards to specify the name, such as wpa.*.example.com.
- Click Save to save the certificate name or click Cancel.
-
Trusted certificates: To add a trusted certificate, click Add and, for each certificate you want to add, do the following:
- Allow trust exceptions: Choose whether the certificate trust dialog appears on user devices when a certificate is untrusted. The default is On.
Android Enterprise settings
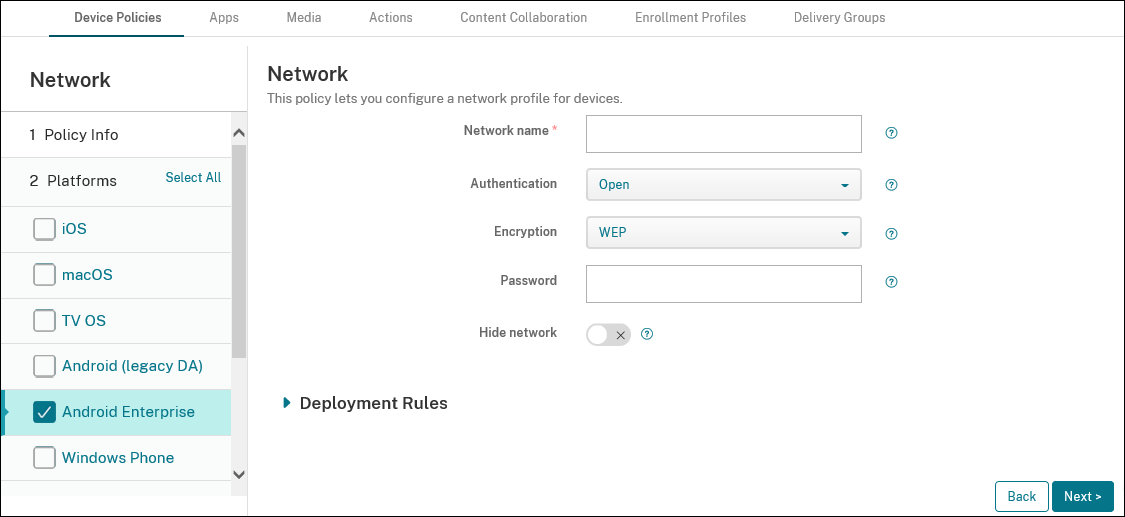
- Network name: Type the SSID that is in the list of available networks on the user device.
-
Authentication: In the list, choose the type of security to use with the Wi-Fi connection.
- Open
- Shared
- WPA
- WPA-PSK
- WPA2
- WPA2-PSK
- 802.1x EAP
The following sections list the options that you configure for each of the preceding connection types. The default is Open.
Open, Shared settings for Android Enterprise
- Encryption: In the list, choose either Disabled or WEP. The default is WEP.
- Password: Type an optional password.
- Hide network: Choose whether the network is hidden.
WPA, WPA-PSK, WPA2, WPA2-PSK settings for Android Enterprise
- Encryption: In the list, choose either TKIP or AES. The default is TKIP.
- Password: Type an optional password.
- Hide network: Choose whether the network is hidden.
802.1x settings for Android Enterprise
- EAP Type: In the list, choose PEAP, TLS, or TTLS. The default is PEAP.
- Password: Type an optional password.
- Authentication phase 2: In the list, choose None, PAP, MSCHAP, MSCHAPPv2, or GTC. The default is PAP.
- Identity: Type the optional user name and domain.
- Anonymous: Type the optional, externally visible user name. You can increase security by typing a generic term like “anonymous” so that the user name isn’t visible.
- CA certificate: In the list, choose the certificate to use.
-
Domain: Type the required domain name. For more information, see Domain.
Note:
When you configure the Wi-Fi policy on devices running on Android 13 or later, the CA certificate and Domain fields must be mandatorily updated. If they aren’t updated, then the configuration fails.
- Identity credential: In the list, choose the identity credential to use. The default is None.
- Hide network: Choose whether the network is hidden.
Android (legacy DA) settings
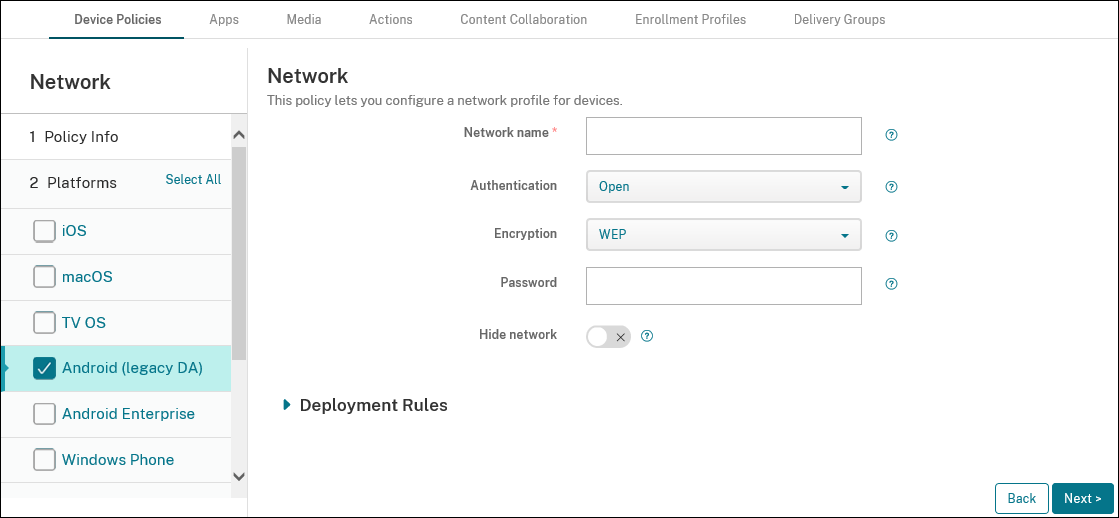
- Network name: Type the SSID that is in the list of available networks on the user device.
-
Authentication: In the list, choose the type of security to use with the Wi-Fi connection.
- Open
- Shared (Android Enterprise only)
- WPA (Android Enterprise only)
- WPA-PSK (Android Enterprise only)
- WPA2
- WPA2-PSK
- 802.1x EAP
The following sections list the options that you configure for each of the preceding connection types.
Open, Shared settings for Android
- Encryption: In the list, choose either Disabled or WEP. The default is WEP.
- Password: Type an optional password.
- Hide network: Choose whether the network is hidden.
WPA, WPA-PSK, WPA2, WPA2-PSK settings for Android
- Encryption: In the list, choose either TKIP or AES. The default is TKIP.
- Password: Type an optional password.
- Hide network: Choose whether the network is hidden.
802.1x settings for Android
- EAP type: In the list, choose PEAP, TLS, or TTLS. The default is PEAP.
- Password: Type an optional password.
- Authentication phase 2: In the list, choose None, PAP, MSCHAP, MSCHAPPv2, or GTC. The default is PAP.
- Identity: Type the optional user name and domain.
- Anonymous: Type the optional, externally visible user name. You can increase security by typing a generic term like “anonymous” so that the user name isn’t visible.
- CA certificate: In the list, choose the certificate to use.
- Identity credential: In the list, choose the identity credential to use. The default is None.
- Hide network: Choose whether the network is hidden.
Windows Desktop/Tablet settings
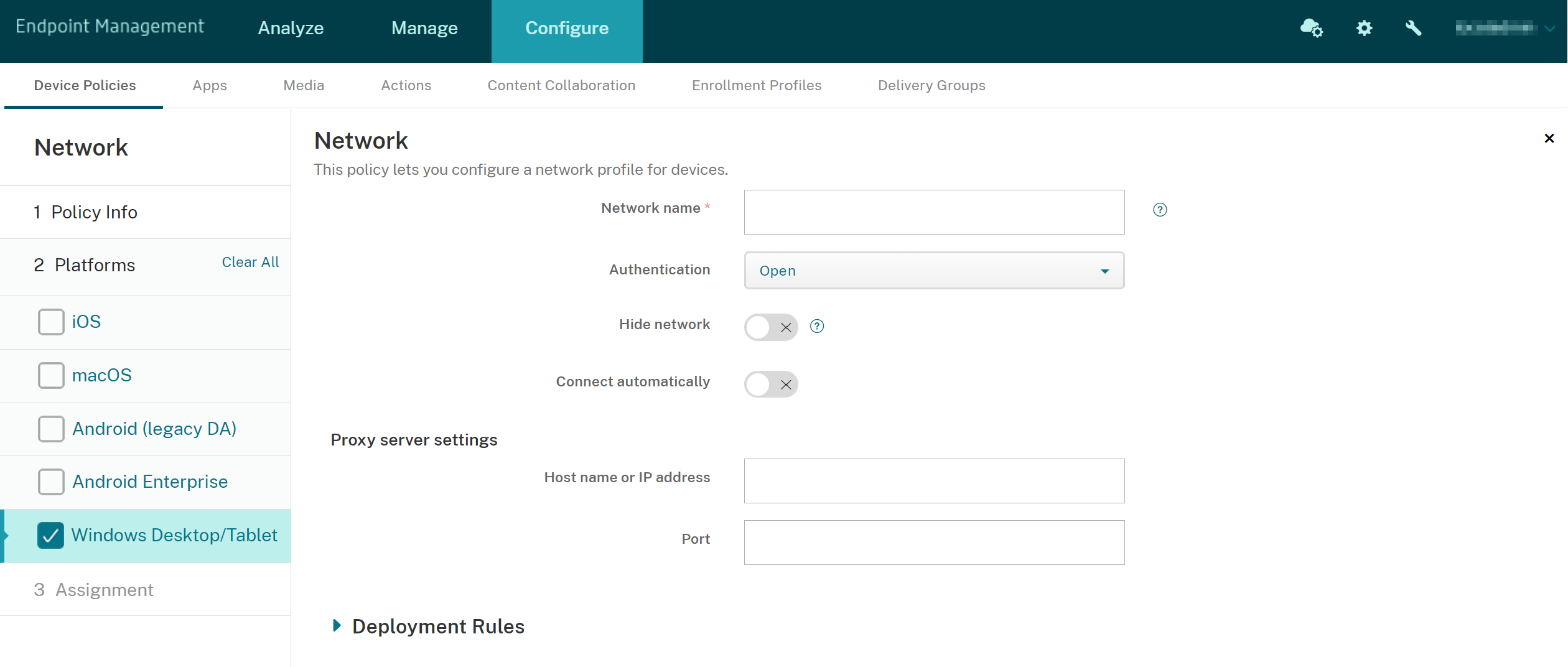
- Network name: The SSID seen in the list of available networks.
-
Authentication: Click the type of security in the drop-down list that you want to use with the Wi-Fi connection.
- Open
- WPA Personal
- WPA-2 Personal
- WPA Enterprise
- WPA-2 Enterprise: For the latest release of Windows 10, configure SCEP to use WPA-2 Enterprise. SCEP configuration enables Citrix Endpoint Management to send the certificate to devices to authenticate to the Wi-Fi server. To configure SCEP, go to Distribution page of Settings > Credential Providers. For more information, see Credential providers.
The following sections list the options that you configure for each of the preceding connection types.
Open settings for Windows 10 and Windows 11
- Hide network: Choose whether the network is hidden.
- Connect automatically: Choose whether to connect to the network automatically.
WPA Personal, WPA-2 Personal settings for Windows 10 and Windows 11
- Encryption: In the list, choose either AES or TKIP to set the type of encryption. The default is AES.
- Shared key: Provide the encryption key for the method that you selected.
- Hide network: Choose whether the network is hidden.
- Connect automatically: Choose whether to connect to the network automatically.
WPA-2 Enterprise settings for Windows 10 and Windows 11
- Encryption: In the list, choose either AES or TKIP to set the type of encryption. The default is AES.
- EAP Type: in the list, choose either PEAP-MSCHAPv2 or TLS to set the EAP type. The default is PEAP-MSCHAPv2.
- Hide network: Choose whether the network is hidden.
- Connect automatically: Choose whether to connect to the network automatically.
- Enable SCEP?: Choose whether to push the certificate to user devices by using SCEP.
- Credential provider for SCEP: In the list, choose the SCEP credential provider. The default is None.