-
Endpoint Management integration with Microsoft Endpoint Manager
-
Certificates and authentication
-
Client certificate or certificate plus domain authentication
-
Authentication with Azure Active Directory through Citrix Cloud™
-
Authentication with Azure Active Directory Group-Based Administration
-
Authentication with Azure Active Directory through Citrix Gateway for MAM enrollment
-
Authentication with Okta through Citrix Gateway for MAM enrollment
-
Authentication with an on-premises Citrix Gateway through Citrix Cloud
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Windows Agent device policy
Use the Windows Agent device policy to run PowerShell scripts on managed Windows desktops and tablets. You can point to script files uploaded to Citrix Endpoint Management as an enterprise app and to other servers that host scripts. For information about adding enterprise apps, see Add apps.
All scripts run under privileged status, you don’t need to run scripts as an administrator.
After deploying and running the script, you can configure automated actions based on the results of the script. For instance, you run a script that monitors a registry key and returns a result. Based on the returned result, an automated action runs. The action grants or denies access to an app, marks the device as out of compliance, or has other effects.
You can also use this policy to deploy customized MSI installers by configuring a PowerShell script that points to an .msi file and an .mst file.
To add or configure this policy, go to Configure > Device Policies. For more information, see Device policies.
Windows Desktop and Tablet settings
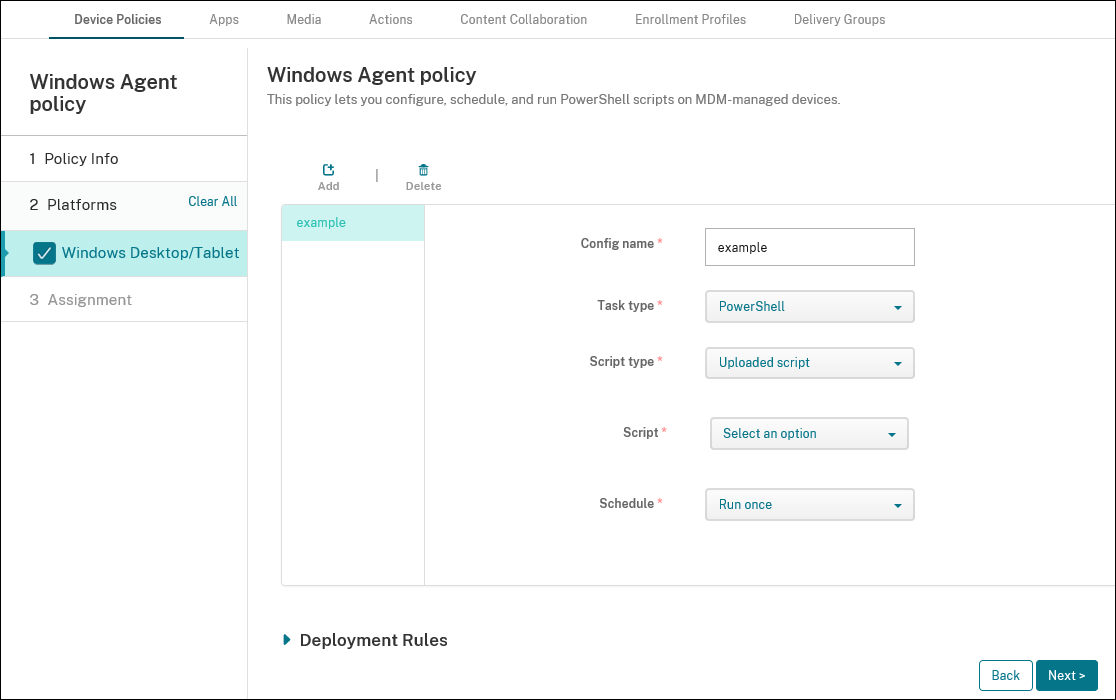
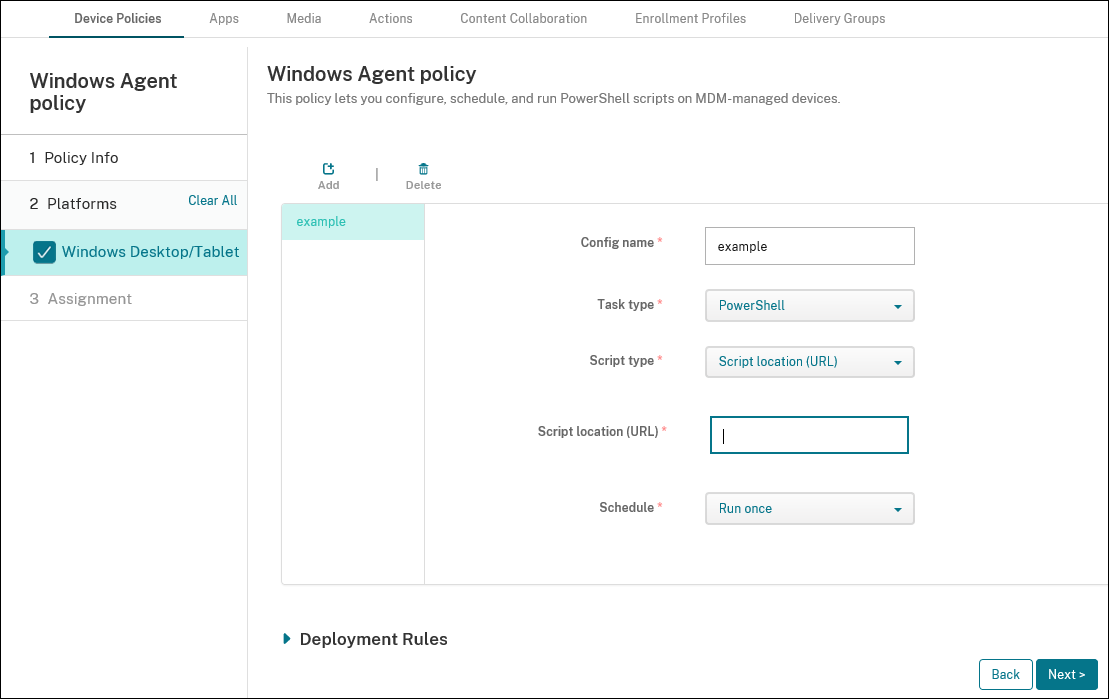
-
Config name: Type a descriptive name for your configuration.
-
Task type: Select PowerShell.
-
Script type: Select Uploaded script for scripts that you’ve uploaded to Citrix Endpoint Management or select Script location (URL) for scripts hosted externally. For more information on how to upload a script to Citrix Endpoint Management, see Add
Win32apps as Enterprise apps.-
Select script: If you chose Uploaded script, select the script to run.
-
Script location (URL): If you chose Script location (URL), enter the location of the script to run. This URL must deliver the script as a payload. Citrix Endpoint Management doesn’t support URLs that deliver scripts as a JavaScript download. The script must also be publicly available.
-
-
Schedule: Select Run once to run the selected script one time or select Run on a recurring basis to run the script regularly.
- Run every (hours): Type the number of hours between script runs.
To check on the status of a script, navigate to Manage > Devices in your console. Select the device on which you want to check the script status and click Edit. Under Properties, you can check the status of your scripts by clicking Download under the Windows Agent heading.
Deploy a PowerShell script to trigger an automated action
-
Create a PowerShell script to monitor a registry key. The following PowerShell script checks to see if the firewall is enabled.
$body = @{} $firewallEnabled = Get-ItemPropertyValue HKLM:\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile -Name EnableFirewall if($firewallEnabled -eq 1){ $body["firewallEnabled"]="true" } else { $body["firewallEnabled"]="false" } $body | ConvertTo-Json -Depth 10 <!--NeedCopy-->This script returns a value of either
{ "firewallEnabled": "true" } <!--NeedCopy-->or
{ "firewallEnabled": "false" } <!--NeedCopy--> - Upload the script to the Citrix Endpoint Management console as an enterprise app or host the script at an accessible URL.
-
Configure the Windows Agent device policy described in this article. Make sure that the script is scheduled to run immediately.
- After the script runs, determine the script status.
- Navigate to Manage > Devices in your console.
- Select the device to check its script status and then click Edit.
- Click Download under the Windows Agent heading.
- Configure an automated action based on the status received. For more information on configuring automated actions, see Create an automated action based on a Windows Agent device policy result. That section shows the specific automated actions created for the example script and Windows Agent device policy.
Share
Share
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.