HDX™ Direct
Overview
When accessing macOS VDA from within an enterprise’s intranet or externally with Citrix Workspace™ app, HDX Direct allows client (CWA) devices to establish a secure and direct connection with the VDA bypassing Citrix Gateway Service or NetScaler® Gateway. When direct communication can be established. It can help organizations achieve the following advantages:
- Reducing bandwidth consumption by establishing a secure and direct user session traffic between VDA and Client.
- Adding resiliency to the session when CGS (Citrix Gateway Service) goes down.
- Improving session performance by avoiding connecting through an intermediary.
How HDX Direct works for internal client
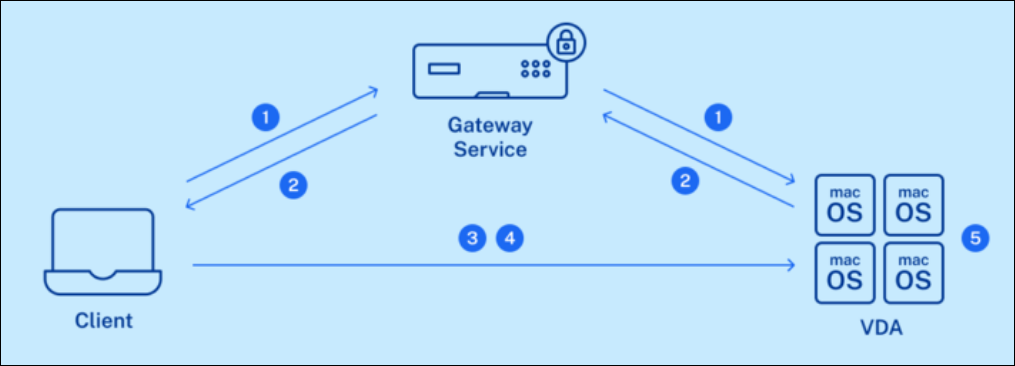
- CWA establishes an HDX session to VDA through the Gateway Service.
- Both CWA and VDA send STUN requests to STUN servers to discover their public IPs and Ports. And STUN server responses to CWA and VDA with their corresponding public IPs and ports.
- CWA and VDA exchange their public IPs and ports through existing HDX sessions.
- VDA sends UDP packets to the CWA’s public IP and port.
- After receiving UDP packets from VDA, CWA establishes a direct DTLS connection with VDA and the session is transferred to the new connection.
How HDX Direct works for client outside intranet
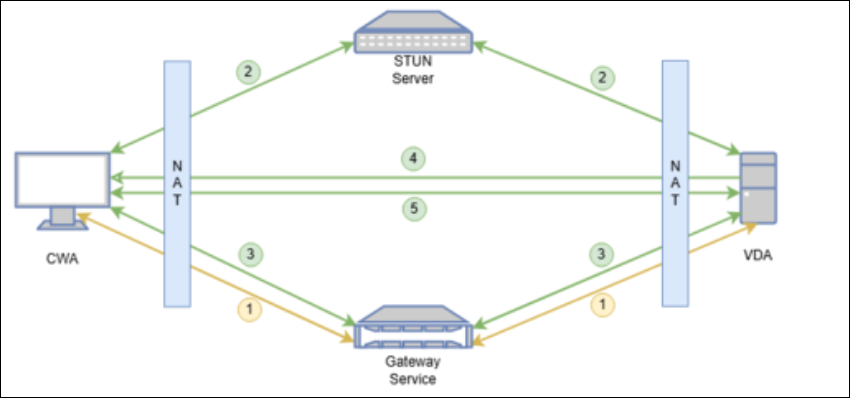
- CWA establishes an HDX session to VDA through the Gateway Service.
- Both CWA and VDA send STUN requests to STUN servers to discover their public IPs and Ports. And STUN server responses to CWA and 1. VDA with their corresponding public IPs and ports.
- CWA and VDA exchange their public IPs and ports through existing HDX sessions.
- VDA sends UDP packets to the CWA’s public IP and port.
- After receiving UDP packets from VDA, CWA establishes a direct DTLS connection with VDA and the session is transferred to the new connection.
STUN protocol is a protocol widely used for identifying an endpoint’s IP address and port allocated by a NAT. Once the initial connection is established, Hdx-Direct public IP discovery is triggered on both CWA and VDA. This involves the endpoints communicating to STUN server using STUN protocol and finding their corresponding public IP addresses. The following image depicts such communication:
STUN Server User can configure local registry to specify STUN Servers which can be used by MacVDA.
| Num | Reg Path | Reg Key | Comments |
|---|---|---|---|
| 1 | HKLM\Software\Citrix\HdxDirect | StunServers | Use “;” to separate multiple STUN Servers. |
| 2 | HKLM\System\CurrentControlSet\Control\Wds\icawd\HdxDirect | CitrixStunServers | Used to identify if a specified STUN server is hosted by Citrix and use “;” to separate multiple STUN Servers. |
If user does not configure STUN Servers in local registry, below default STUN Servers are used by MacVDA.
| STUN Server Address | Port | Host by Citrix |
|---|---|---|
| stun.l.google.com | 19302 | No |
| stun.cloud.com | 3478 | Yes |
| stun-azure.nssvctesting.net | 3478 | Yes |
| stun-aws.citrixngsk8sdev.net | 3478 | Yes |
| stunserver.stunprotocol.org | 3478 | No |
Configuration
HDX Direct is disabled by default. To enable this feature, you can configure the Citrix DDC policies below, please also refer to macOS VDA policy support list for details:
- HDX Direct: enable or disable this feature.
- HDX Direct mode: configure if HDX Direct is available for internal clients or for both internal and external clients. For HDX Direct support in this release, both modes are supported, but it’s available for internal clients only.
Validation
To check whether a HDX session is working with HDX Direct, run the /opt/Citrix/VDA/bin/ctxsession -v command in the terminal.
If HDX Direct is working from an internal client, HDX Direct State shows Connected - Internal.
If HDX Direct is working from an external client, HDX Direct State shows Connected - External.
Troubleshooting
If Citrix DDC policies are configured, but HDX session doesn’t work with HDX Direct, check if the policies are applied to the current macOS VDA by the tool hdxmonitor:
sudo hdxmonitor network dump
The result will show if HDX Direct is applied or not.
Once confirmed, HDX Direct will work in the next new HDX connection. Go to the policy support list for more information on HDX Direct policies.
Note:
Hdx-Direct for external users is only available with EDT (UDP) as the transport protocol. Therefore, Adaptive Transport must be enabled.