OS Update device policy
The OS Update device policy lets you deploy:
-
The latest OS updates to supervised iOS devices.
The OS Update device policy only works for supervised devices enrolled in the Apple Deployment Program.
-
The latest OS and app updates to the Apple Deployment Program enrolled macOS devices running macOS 10.11.5 and later.
Note:
Apple currently limits OS updates to major versions only. Administrators aren’t allowed to update minor versions. For more information, see this article in Apple’s documentation.
-
The latest OS updates to supervised Desktop and Tablet devices running Windows 10 or Windows 11.
You can also use the OS Update policy to manage delivery optimization settings for desktops and tablets running Windows 10 (version 1607 or later) or Windows 11. Delivery optimization is a peer-to-peer client update service provided by Microsoft for Windows 10 and Windows 11 updates. The goal of delivery optimization is to reduce bandwidth issues during the update process. Bandwidth reduction is achieved by sharing the downloading task among multiple devices. For more information, see the Microsoft article, Configure Delivery Optimization for Windows 10 updates.
-
The latest OS updates to managed Android Enterprise devices (Android 7.0 and later).
Important:
The OS update policy does not allow you to disable updates entirely. To delay updates up to 90 days, create a restriction policy. See Restriction device policy.
To add or configure this policy, go to Configure > Device Policies. For more information, see Device policies.
iOS settings
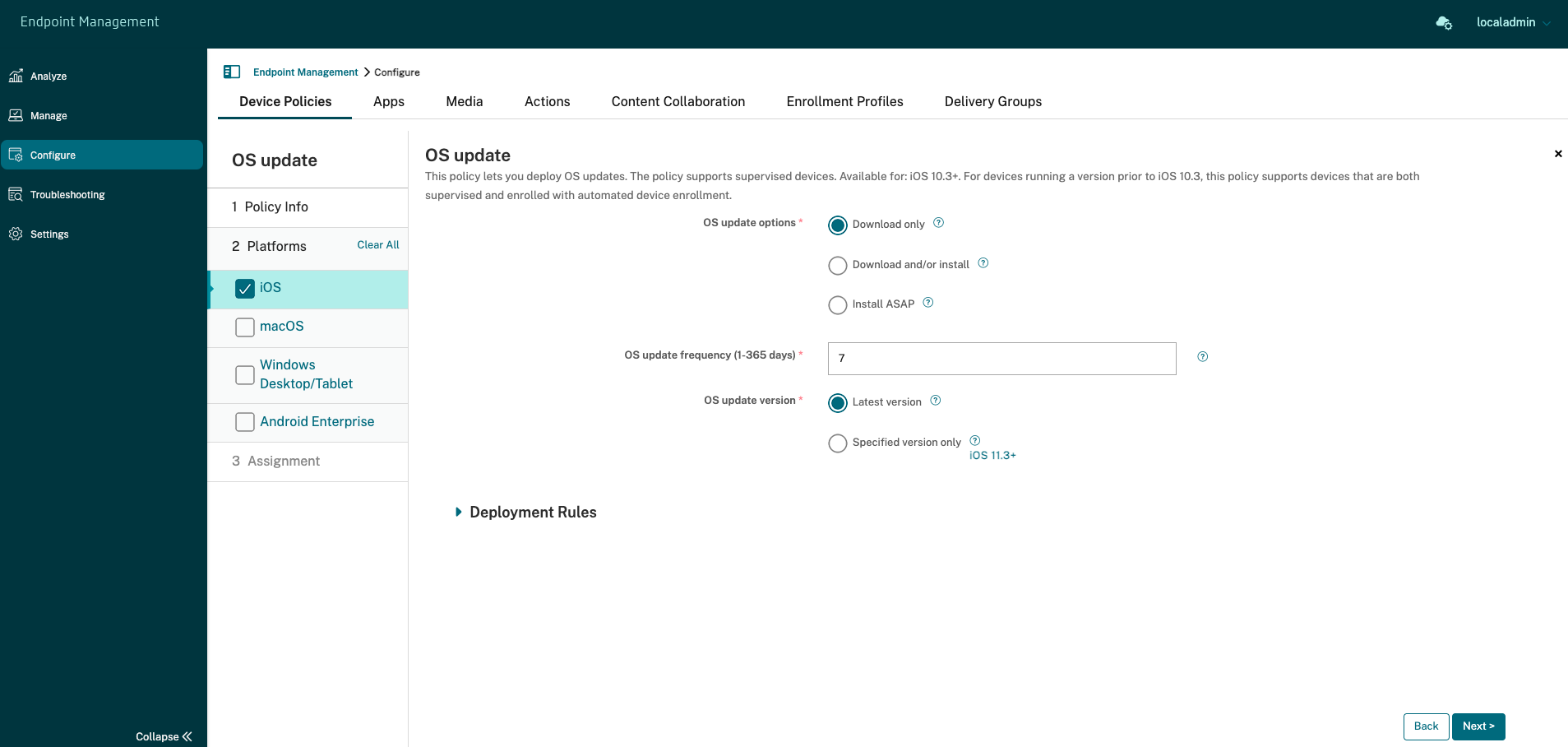
The following settings are for supervised iOS devices.
- OS update options: Both of the options download the latest OS updates to supervised devices according to the OS update frequency. The device prompts users to install updates. The prompt is visible after the user unlocks the device.
- OS update frequency: Determines how frequently Citrix Endpoint Management checks and updates the device OS. The default is 7 days.
-
OS updates version: Specifies the version to use to update supervised iOS devices. The default is Latest version.
- Latest version: Select to update to the latest OS version.
- Specific version only: Select to update to a specific OS version and then type the version number.
macOS settings
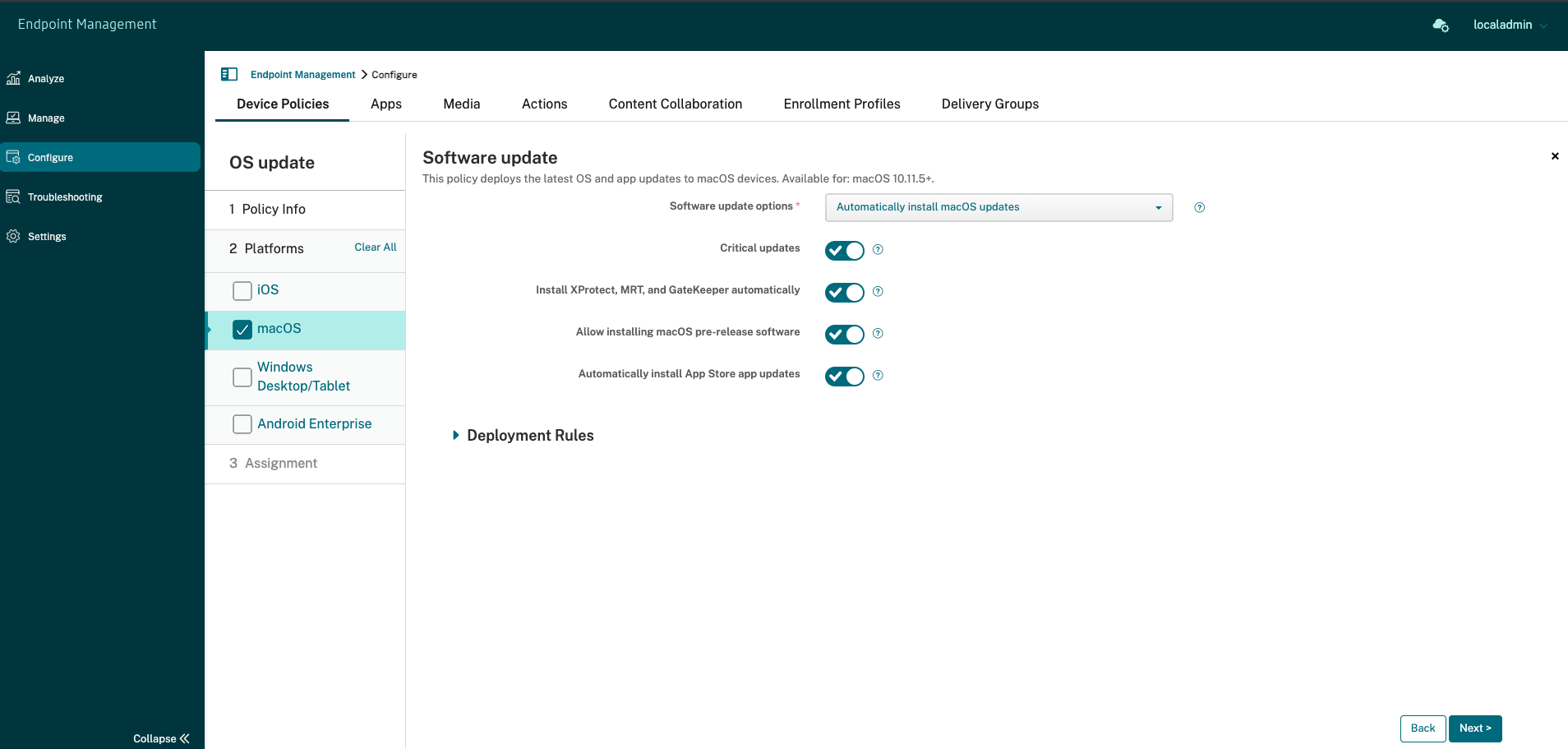
-
Software updates options: Controls how macOS devices check for and install updates. Select from the following options:
- Automatically install macOS updates: Updates download and install automatically.
- Download new updates when available: Updates download but require manual installation.
- Check for updates: Checks to see if updates exist but doesn’t download or install the updates automatically.
- Don’t check for updates: Don’t check for new updates, download the updates, or install the updates automatically. Users can still install updates manually.
- Critical updates: Allow automatic installation of critical macOS updates.
- Install xProtect, MRT, and GateKeeper updates automatically: Allow macOS devices to install updates for security software automatically.
- Allow installation of macOS pre-release software: Allow users to install pre-release versions of macOS software.
- Automatically install App Store app updates: Allow App Store apps to update automatically.
Get status for iOS and macOS update actions
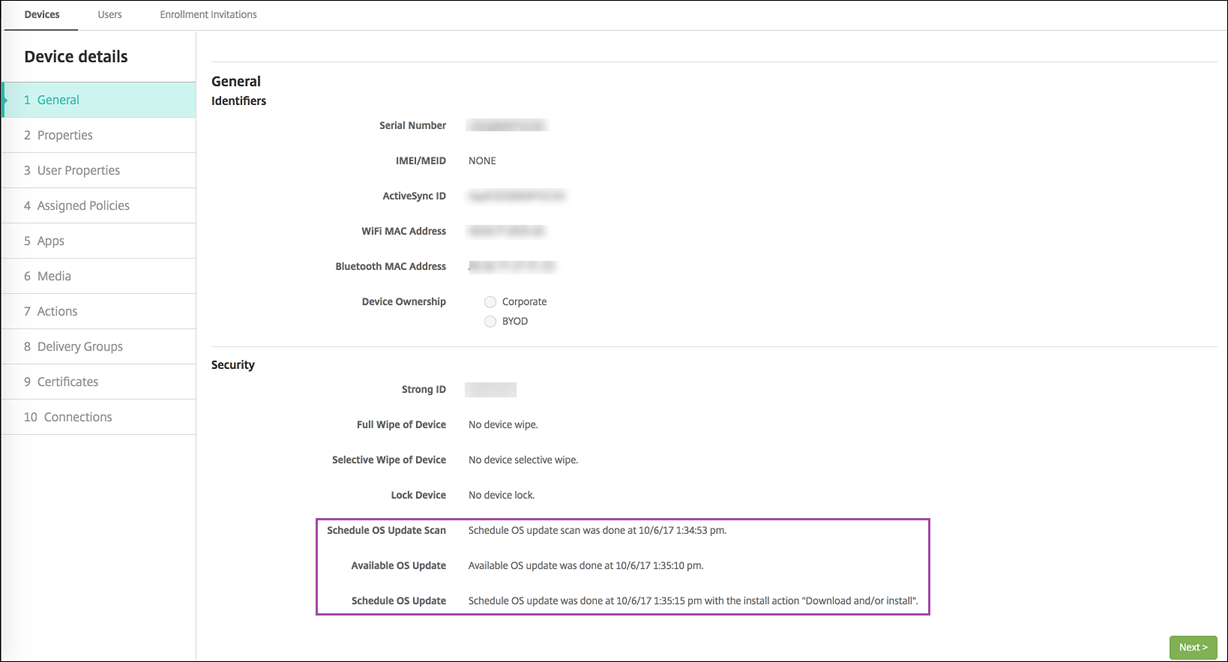
For iOS and macOS, Citrix Endpoint Management doesn’t deploy the Control OS Update policy to devices. Instead, Citrix Endpoint Management uses the policy to send these MDM commands to devices:
- Schedule OS Update Scan: Requests that the device does a background scan for OS updates. (Optional for iOS)
- Available OS Updates: Queries the device for a list of available OS updates.
- Schedule OS Update: Requests that the device does macOS updates, app updates, or both. Thus, the device OS determines when it downloads or installs the OS and app updates.
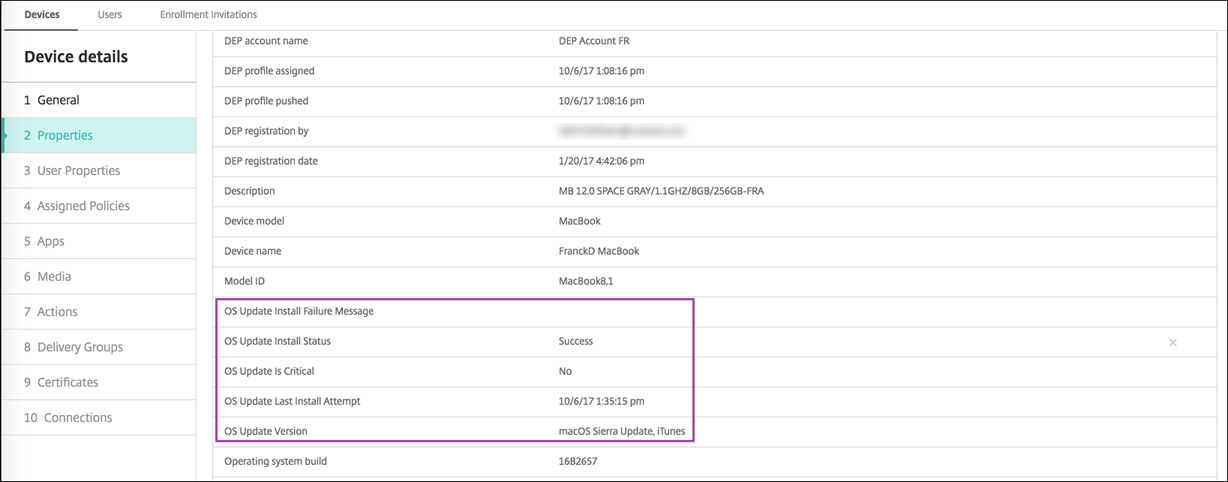
The Manage > Devices > Device details (General) page shows the status of scheduled and available OS update scans, and scheduled macOS and app updates.
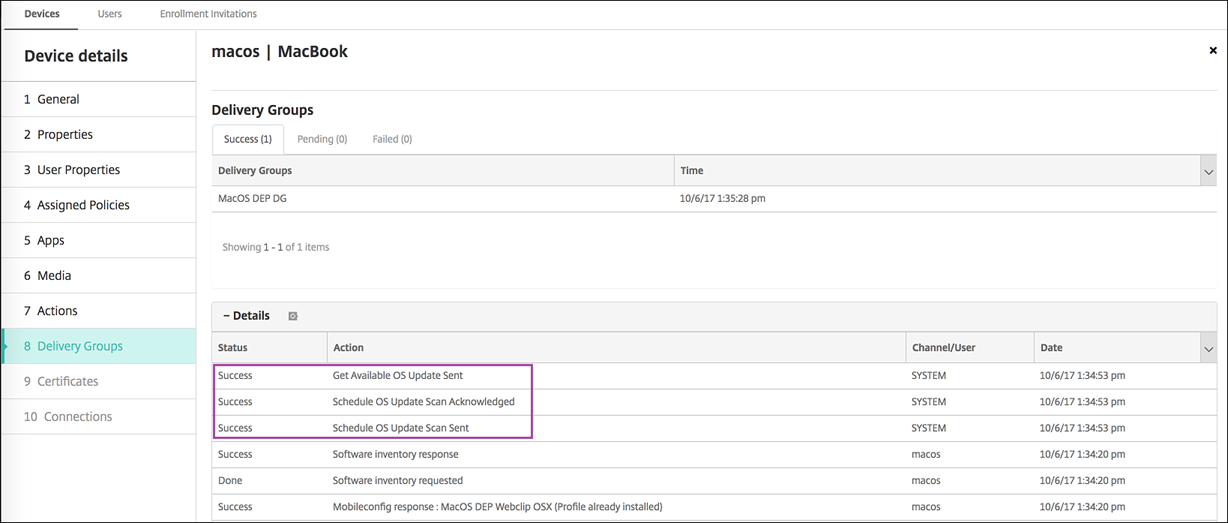
For more details about the status of update actions, go to the Manage > Devices > Device details (Delivery Groups) page.
For details such as available OS updates and the last installation attempt, go to the Manage > Devices > Device details (Properties) page.
Windows Desktop and Tablet settings
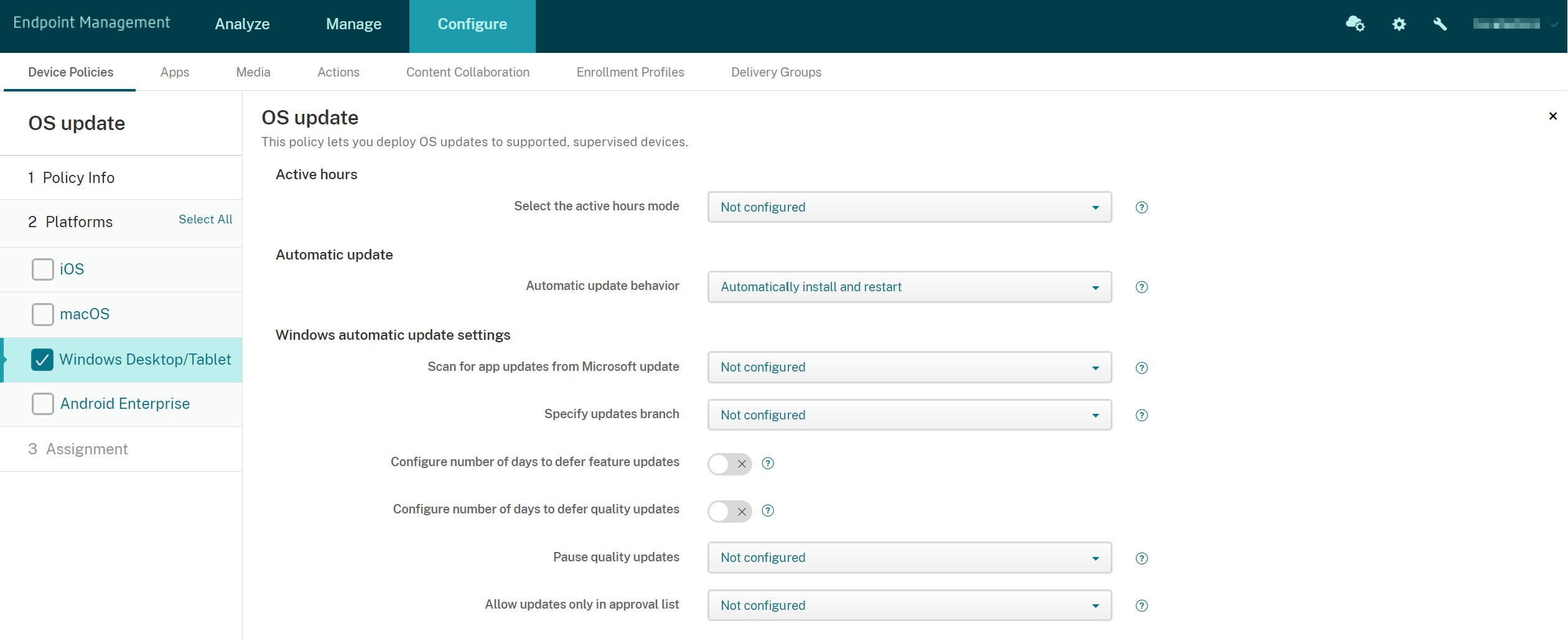
- Select active hours mode: Select a mode to configure the active hours for doing OS updates. You can specify a range of hours or a start and end time. After you select a mode, more settings appear: Specify max range for active hours or Active hours start and Active hours end. Not configured allows Windows to do OS updates at any time. Defaults to Not configured.
-
Auto update behavior: Configures the download, install, and restart behavior of the Windows update service on user devices. Defaults to Auto install and restart.
- Notify user before downloading the update: Windows notifies users when updates are available. Windows doesn’t automatically download and install updates. Users must start the download and install actions.
- Auto install and notify to schedule device restart: Windows downloads updates automatically on non-metered networks. Windows installs updates during Automatic Maintenance when the device isn’t in use and isn’t running on battery power. If Automatic Maintenance can’t install updates for two days, Windows Update installs the updates immediately. If the installation requires a restart, Windows prompts the user to schedule the restart time. The user has up to seven days to schedule the restart. After seven days, Windows forces the device to restart. Enabling the user to control the start time reduces the risk of accidental data loss caused by apps that don’t shut down properly on restart.
- Auto install and restart: Default setting. Windows downloads updates automatically on non-metered networks. Windows installs updates during Automatic Maintenance when the device isn’t in use and isn’t running on battery power. If Automatic Maintenance can’t install updates for two days, Windows Update installs the updates immediately. If the installation requires a restart, Windows automatically restarts the device when the device is inactive.
- Auto install and restart at a specified time: When you choose this option, more settings appear so you can specify the day and time. The default is 3 AM daily. Automatic installation happens at the specified time and device restart occurs after a 15-minute countdown. When Windows is ready to restart, a logged-in user can interrupt the 15-minute countdown to delay the restart.
- Auto install and restart without end-user control: Windows downloads updates automatically on non-metered networks. Windows installs updates during Automatic Maintenance when the device isn’t in use and isn’t running on battery power. If Automatic Maintenance can’t install updates for two days, Windows Update installs updates immediately. If the installation requires a restart, Windows automatically restarts the device when the device is inactive. This option also sets the user control panel to read-only.
- Turn off automatic updates: Disables Windows automatic updates on the device.
-
Scan for app updates from Microsoft update: Specifies whether Windows accepts updates for other Microsoft apps from the Microsoft update service. Defaults to Not configured.
- Not configured: Use this setting if you don’t want to configure the behavior. Windows doesn’t change the related UI on user devices. Users can accept or reject updates for other Microsoft apps.
- Yes: Windows allows app updates to be installed from the Windows update service. The related setting on the user device is inactive, so the user can’t modify the setting.
- No: Windows doesn’t allow app updates to be installed from the Windows update service. The related setting on the user device is inactive, so the user can’t modify the setting.
-
Specify updates branch: Specifies which Windows update service branch to use for updates. Defaults to Not configured.
- Not configured: Use this setting if you don’t want to configure the behavior. Windows doesn’t change the related UI on user devices. Users can choose a Windows update service branch.
- Current Branch: Windows receives updates from Current Branch. The related setting on the user device is inactive, so the user can’t modify the setting.
- Current Branch for Business: Windows receives updates from Current Branch for Business. The related setting on the user device is inactive, so the user can’t modify the setting.
- Configure number of days to defer feature updates: If On, Windows defers feature updates by the specified number of days and the user can’t change the setting. If Off, the user can change the number of days to defer feature updates. Defaults to Off.
- Configure number of days to defer quality updates: If On, Windows defers quality updates by the specified number of days and the user can’t change the setting. If Off, the user can change the number of days to defer quality updates. Defaults to Off.
-
Pause quality updates: Specifies whether to pause quality updates for 35 days. Defaults to Not configured.
- Not configured: Use this setting if you don’t want to configure the behavior. Windows doesn’t change the related UI on user devices. Users can choose to pause quality updates for 35 days.
- Yes: Windows pauses the installation of quality updates from the Windows Update Service for 35 days. The related setting on the user device is inactive, so the user can’t modify the setting.
- No: Windows doesn’t pause the installation of quality updates from the Windows Update Service. The related setting on the user device is inactive, so the user can’t modify the setting.
-
Allow updates only in approval list: Specifies whether to install only the updates that an MDM server approves. Citrix Endpoint Management doesn’t support configuring an approved list of updates. Defaults to Not configured.
- Not configured: Use this setting if you don’t want to configure the behavior. Windows doesn’t change the related UI on user devices. Users can choose which updates to allow.
- Yes, install only approved updates: Allows installation of approved updates only.
- No, install all applicable updates: Allows installation of any applicable updates on the device.
-
Use internal update server: Specifies whether to get updates from the Windows update service or an internal update server through Windows Server Update Services (WSUS). If Off, devices use the Windows update service. If On, devices connect to the specified WSUS server for updates. Defaults to Off.
- Accept updates signed by entities other than Microsoft: Specifies whether to accept updates signed by third-party entities other than Microsoft. This feature requires that the device trusts the third-party vendor certificate. Defaults to Off.
- Allow connection to Microsoft update service: Allows Windows update on the device to connect periodically to the Microsoft update service, even if the device is configured to get updates from a WSUS server. Defaults to On.
- WSUS server: Specify the server URL for the WSUS server.
- Alternate intranet server to host updates: Specify an alternate intranet server URL to host updates and receive reporting information.
- Configure delivery optimization: Whether to use delivery optimization for Windows 10 and Windows 11 Updates. Default is Off.
- Cache size: The maximum size of the delivery optimization cache. A value of 0 means an unlimited cache. The default is 10 GB.
- Allow VPN peer caching: Whether to allow devices to participate in peer caching when connected to the domain network through VPN. When On, the device can download from or upload to other domain network devices, either on VPN or on the corporate domain network. Default is Off.
-
Download method: The download method that delivery optimization can use for downloads of Windows Updates, app, and app updates. Default is HTTP blended with peering behind the same NAT. Options are:
- HTTP only, no peering: Disables peer-to-peer caching but allows delivery optimization to download content from Windows Update servers or Windows Server Update Services (WSUS) servers.
- HTTP blended with peering behind the same NAT: Enables peer sharing on the same network. The Delivery Optimization cloud service finds other clients that connect to the Internet using the same public IP as the target client. These clients then try to connect to other peers on the same network by using their private subnet IP.
- HTTP blended with peering across a private group: Automatically selects a group based on the device Active Directory Domain Services (AD DS) site or the domain that the device authenticates to. Peering occurs across internal subnets, between devices that belong to the same group, including devices in remote offices.
- HTTP blended with Internet peering: Enable Internet peer sources for Delivery Optimization.
- Simple download mode with no peering: Disable the use of Delivery Optimization cloud services. Delivery Optimization switches to this mode automatically during these conditions: When the Delivery Optimization cloud services are unavailable, unreachable, or when the content file size is less than 10 MB. In this mode, Delivery Optimization provides a reliable download experience, with no peer-to-peer caching.
- Do not use Delivery Optimization and use BITS instead: Enables clients to use BranchCache. For more information, see the Microsoft article, BranchCache.
- Max download bandwidth: The maximum download bandwidth in KBs/second. Default is 0, which means dynamic bandwidth adjustment.
- Percentage of maximum download bandwidth: The maximum download bandwidth that delivery optimization can use across all concurrent download activities. The value is a percentage of the available download bandwidth. Default is 0, which means dynamic adjustment.
- Max upload bandwidth: The maximum upload bandwidth in KBs/second. Default is 0. A value of 0 means unlimited bandwidth.
- Monthly upload data cap: The maximum size in GBs that delivery optimization can upload to Internet peers in each calendar month. The default is 20 GB. A value of 0 means unlimited monthly uploads.
How Citrix Endpoint Management handles approved updates to Windows Desktop and Tablet devices
You can specify whether to install only approved updates. Citrix Endpoint Management handles the updates as follows:
- For a security update, such as for Windows Defender definitions, Citrix Endpoint Management automatically approves the update and sends an install command to the device during the next sync.
- For all other update types, Citrix Endpoint Management waits for your approval before sending the install command to the device.
Prerequisites
- You must upload the Microsoft root certificate to the Citrix Endpoint Management server as a server certificate.
- For information about importing a server certificate, see “To import a certificate” in Certificates and authentication.
To install only approved updates
- Go to Configure > Device Policies and open the OS Update device policy.
- Change the Allow updates only in approval list setting to Yes, install only approved updates.
To approve an update
-
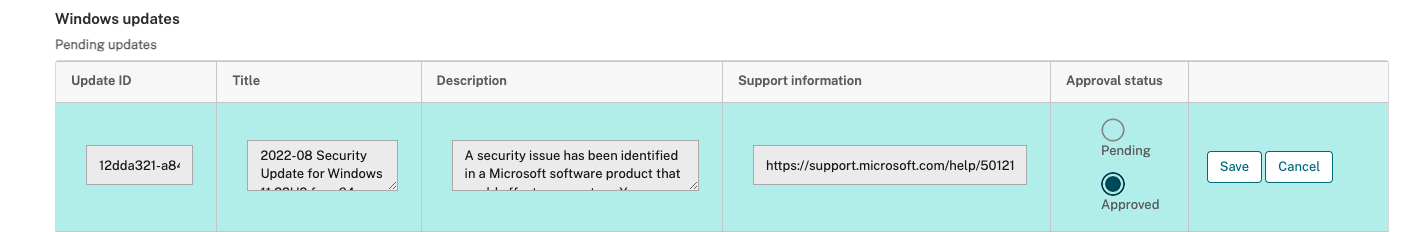
In the OS Update device policy, scroll down to the Pending updates table. Citrix Endpoint Management gets the updates listed in the table from the devices.
-
Search for updates with an Approval status of Pending.
-
Click the row for the update that you want to approve and then click the edit icon for that row (in the Add column).
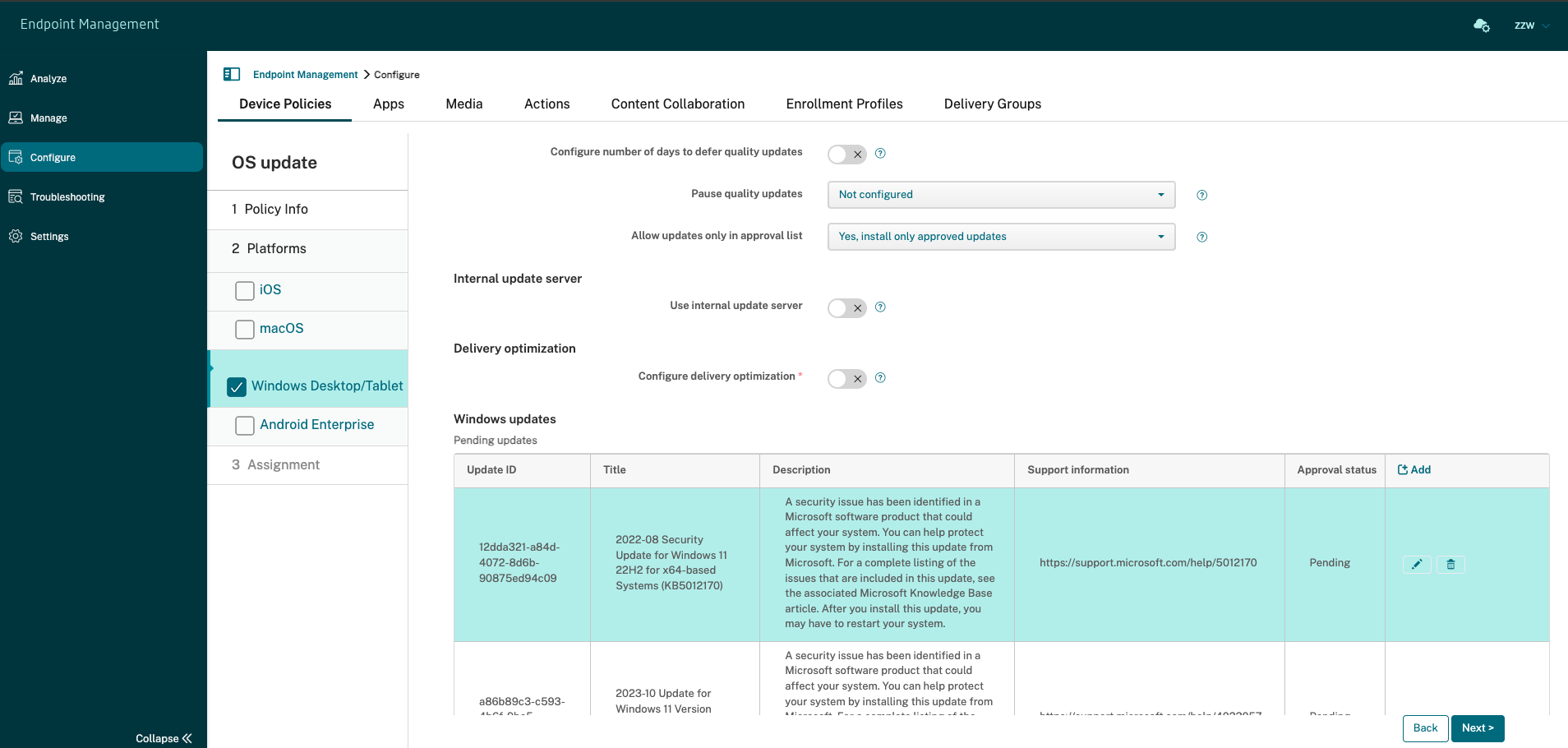
-
To approve the update, click Approved and then click Save.
Note:
Although the Pending updates table includes add and delete commands, those commands don’t result in any changes to the Citrix Endpoint Management database. Editing approval status is the only action available for pending updates.
To view the Windows update status for a device, go to Manage > Devices > Properties.
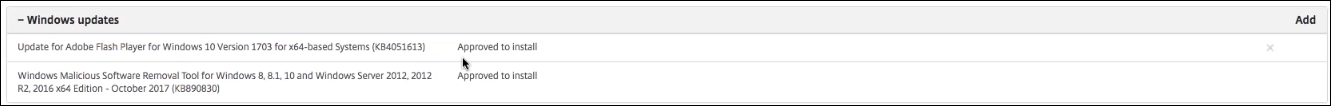
When an update publishes, the Update ID appears in the first column with a status (Success or Failure). You can create a report or an automated action for devices with failed updates. The date and time of the publication also appears.
How updates work for first-time and subsequent deployments
The effect of the OS Update device policy on devices differs for a first-time deployment versus a deployment after devices get updates.
-
For Citrix Endpoint Management to query a device for updates, you must configure and assign to a delivery group at least one OS Update device policy.
Citrix Endpoint Management queries a device for installable updates during a device MDM sync.
- After the first OS Update device policy deploys, the list of Windows updates is empty because no device has reported yet.
-
When the devices in the assigned delivery group report updates, Citrix Endpoint Management saves those updates in its database. To approve any reported updates, edit the policy again.
Update approval applies only to the policy that you are editing. Updates approved in one policy don’t show as approved in another policy. The next time that a device syncs, Citrix Endpoint Management sends a command to the device to indicate that the update is approved.
-
For a second OS Update device policy, the update list has the updates stored in the Citrix Endpoint Management database. Approve updates for each policy.
During each device sync, Citrix Endpoint Management queries the device for the approved update state until the device reports that an update installed. For updates that require a restart after an install, Citrix Endpoint Management queries the state of the update until the device reports that the update installed.
- Citrix Endpoint Management doesn’t restrict the updates shown in the policy configuration page by delivery group or device. All updates reported by devices appear in the list.
Android Enterprise settings
-
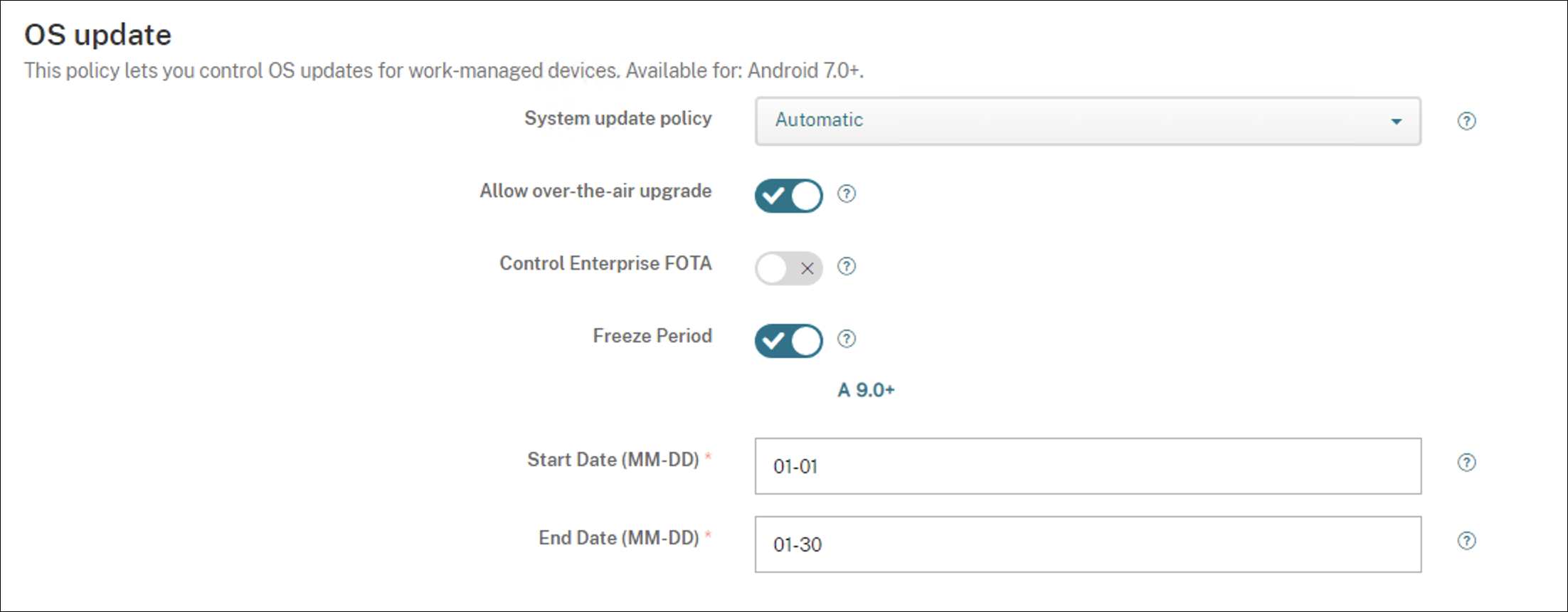
System update policy: Determines when system updates occur.
- Automatic: Installs an update when it’s available.
-
Windowed: Installs an update automatically within the daily maintenance window specified in the Start time and End time.
- Start time: The start of the maintenance window, measured as the number of minutes (0 - 1440) from midnight in the device local time. Default is 0.
- End time: The end of the maintenance window, measured as the number of minutes (0 - 1440) from midnight in the device local time. Default is 120.
- Postpone: Allows a user to postpone an update for up to 30 days.
- Default: Sets the update policy to the system default.
-
Allow over-the-air upgrade: If disabled, user devices can’t receive software updates wirelessly. The default is On.
-
Freeze Period: If On, OS updates aren’t installed on the device during the date range specified for the Automatic, Postpone, and Windowed update policies. Only one freeze period can be set for a device at a time. The length of the freeze period can’t exceed 90 days.
- Start Date/End Date: The date range in which OS updates aren’t installed if Freeze Period is enabled.
-
Freeze Period: If On, OS updates aren’t installed on the device during the date range specified for the Automatic, Postpone, and Windowed update policies. Only one freeze period can be set for a device at a time. The length of the freeze period can’t exceed 90 days.
- Start Date/End Date: The date range in which OS updates aren’t installed if Freeze Period is enabled.