About Citrix Endpoint Management
Citrix Endpoint Management is a Unified Endpoint Management (UEM) solution that brings every app and endpoint into one unified view to increase security and improve productivity. For an overview of UEM, see the Citrix Tech Zone technical brief, Citrix Endpoint Management.
Citrix Endpoint Management provides Mobile Device Management (MDM) and Mobile App Management (MAM).
MDM features of Citrix Endpoint Management let you:
- Deploy device policies and apps.
- Retrieve asset inventories.
- Carry out actions on devices, such as a device wipe.
MAM features of Citrix Endpoint Management let you:
- Secure apps and data on BYO mobile devices.
- Deliver enterprise mobile apps.
- Lock the apps and wipe their data.
With a combination of MDM and MAM features, you can:
- Manage a corporate-issued device by using MDM
- Deploy device policies and apps
- Retrieve an asset inventory
- Wipe devices
- Deliver enterprise mobile apps
- Lock apps and wipe the data on devices
The following table summarizes the Citrix Endpoint Management features supported for MDM, MAM, or MDM+MAM.
| Feature (by platform) | MDM (1) | MAM (2) | MDM+MAM |
|---|---|---|---|
| Android Enterprise: | |||
| Device enrollment support | Yes | Yes | Yes |
| Domain authentication support | Yes | No | Yes |
| Domain plus security token authentication support | No | No | Yes |
| Client certificate authentication support | No | Yes | Yes |
| Client certificate plus domain authentication support | No | No | Yes |
| Client certificate plus security token support | No | No | Yes |
| Azure AD identity provider support | Yes | No | Yes |
| Okta identity provider support | Yes | No | Yes |
| Single sign on to native SaaS apps | Yes | No | Yes |
| Citrix Content Delivery Network support for enterprise apps | Yes | Yes | Yes |
| Citrix Content Delivery Network support for MDX apps | Yes | Yes | Yes |
| Shared device support by provisioning dedicated Android Enterprise (COSU) devices | Yes | No | Yes |
| Android (legacy): | |||
| Device enrollment support | Yes | Yes | Yes |
| Domain or domain plus security token authentication support | No | No | Yes |
| Client certificate authentication support | No | Yes | Yes |
| Client certificate plus domain authentication support | No | No | Yes |
| Client certificate plus security token support | No | No | Yes |
| Azure AD and Citrix identity provider support | Yes | No | Yes |
| Okta identity provider support | Yes | No | Yes |
| Single sign on to native SaaS apps | Yes | No | Yes |
| Citrix Content Delivery Network support for enterprise apps | Yes | Yes | Yes |
| Citrix Content Delivery Network support for MDX apps | Yes | Yes | Yes |
| Chrome: | |||
| Device enrollment support | Yes | No | Yes |
| User name and password authentication support | Yes | No | Yes |
| iOS: | |||
| Device enrollment support | Yes | Yes | Yes |
| Domain or domain plus security token authentication support | No | No | Yes |
| Client certificate authentication support | No | Yes | Yes |
| Client certificate plus domain authentication support | No | No | Yes |
| Azure AD and Citrix identity provider support | Yes | No | Yes |
| Okta identity provider support | Yes | No | Yes |
| Single sign on to native SaaS apps | Yes | No | Yes |
| Citrix Content Delivery Network support for enterprise apps | Yes | Yes | Yes |
| Citrix Content Delivery Network support for MDX apps | Yes | Yes | Yes |
| Apple Education integration | Yes | No | Yes |
| macOS: | |||
| Device enrollment support | Yes | No | No |
| Domain or domain plus one-time password support | Yes | No | No |
| Invitation URL plus one-time password support | Yes | No | No |
| Windows: | |||
| Device enrollment support | Yes | No | No |
| Automatic enrollment of Windows 10 and Windows 11 devices through Citrix Workspace app | Yes | No | No |
| Domain or domain plus security token authentication support | Yes | No | No |
| Client certificate authentication support | Yes | No | No |
| Client certificate plus domain authentication support | Yes | No | No |
| Federated authentication through Azure AD or Citrix identity provider | Yes | No | No |
| Citrix Content Delivery Network support for enterprise apps | Yes | No | No |
| Workspace Environment Management™ integration (3) | Yes | No | No |
Notes:
(1) Deployment ordering applies only to devices in a delivery group that has an enrollment profile configured for MDM.
(2) MAM enrollment requires NetScaler Gateway.
(3) Workspace Environment Management (WEM) integration provides access to MDM features on a wide spectrum of Windows operating systems.
For more information, see Management modes.
Architecture
The device and app management requirements of your organization determine the Citrix Endpoint Management components in your Citrix Endpoint Management architecture. The components of Citrix Endpoint Management are modular and build on each other. For example, your deployment includes NetScaler Gateway:
- NetScaler Gateway gives users remote access to mobile apps and tracks user device types.
- Citrix Endpoint Management is where you manage those apps and devices.
The following diagram shows a general architectural overview of an Citrix Endpoint Management cloud deployment and its integration with your data center.
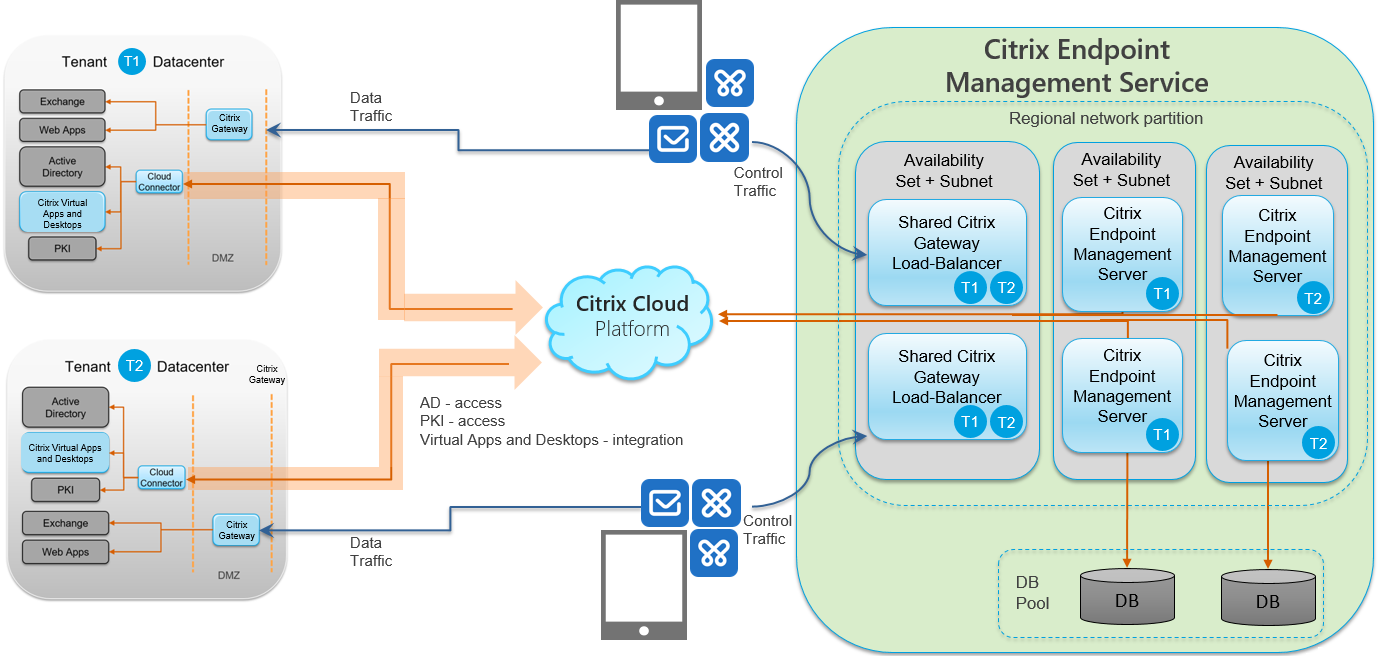
The following subsections have reference architecture diagrams for:
- Citrix Endpoint Management
- Optional components such as an external Certificate Authority, Citrix Endpoint Management connector for Exchange ActiveSync, and Citrix Endpoint Management MDM+MAM and Intune MAM traffic flow.
For more information about Citrix ADC and NetScaler Gateway requirements, see the Citrix product documentation at https://docs.citrix.com/.
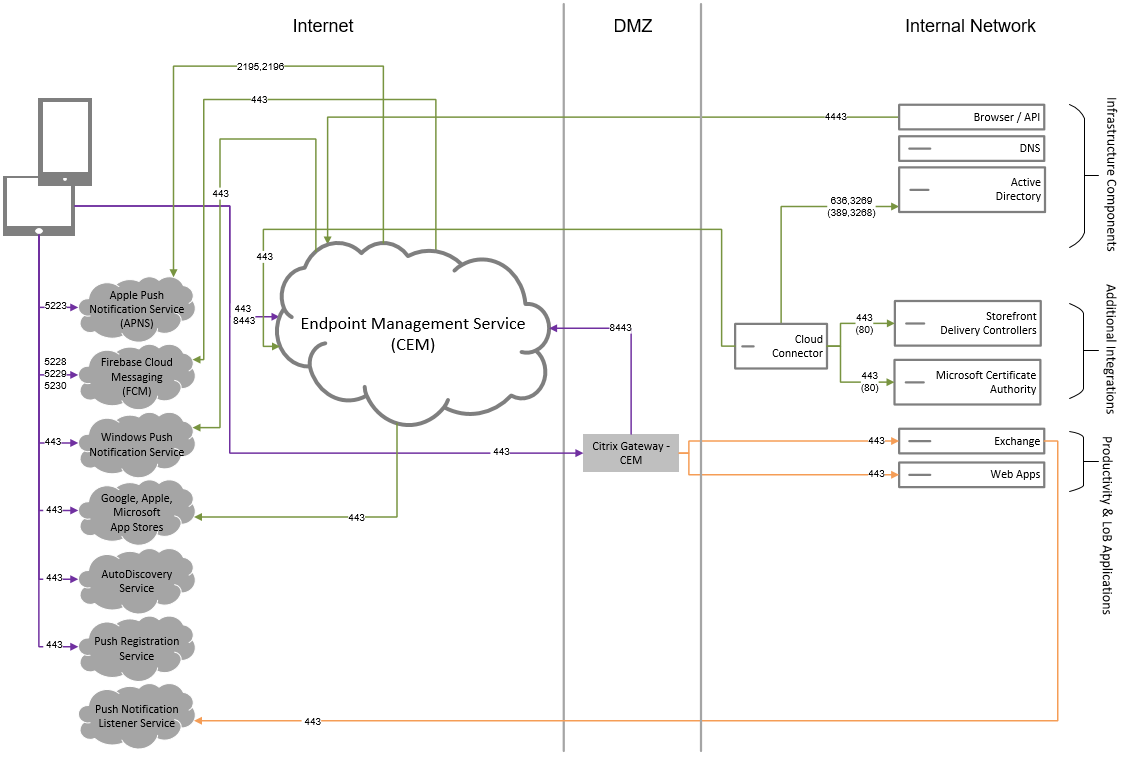
Core reference architecture
For details about port requirements, see System requirements.
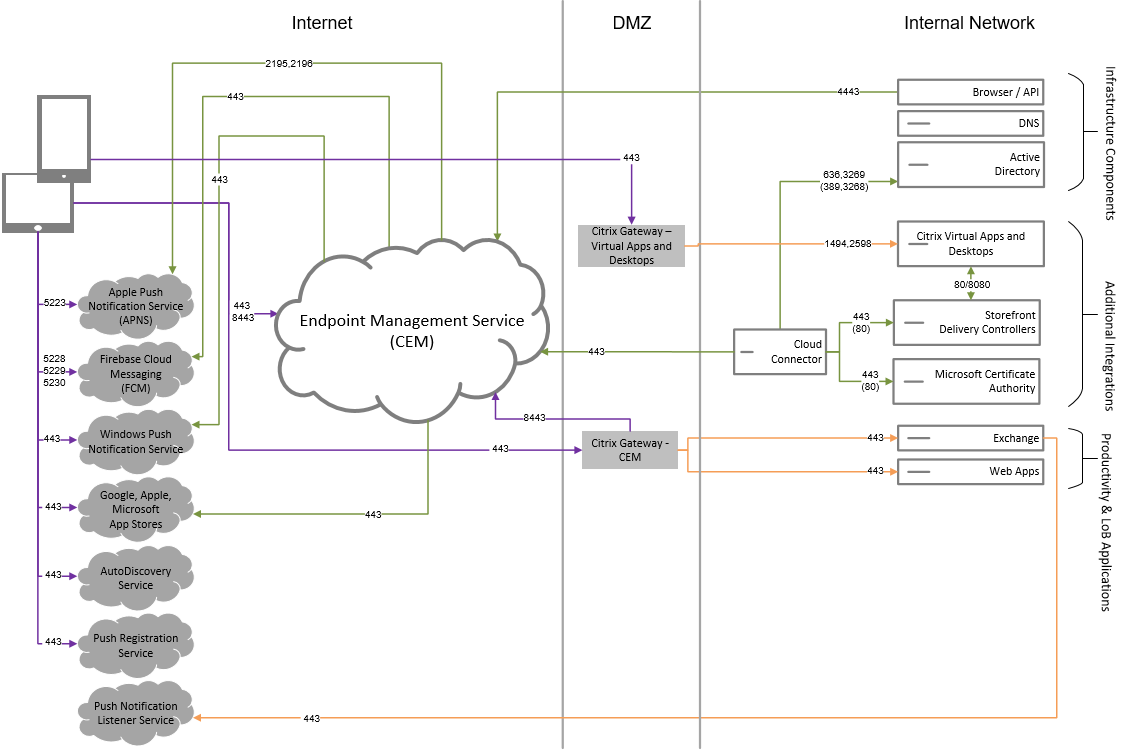
Reference architecture with Citrix Virtual Apps and Desktops™
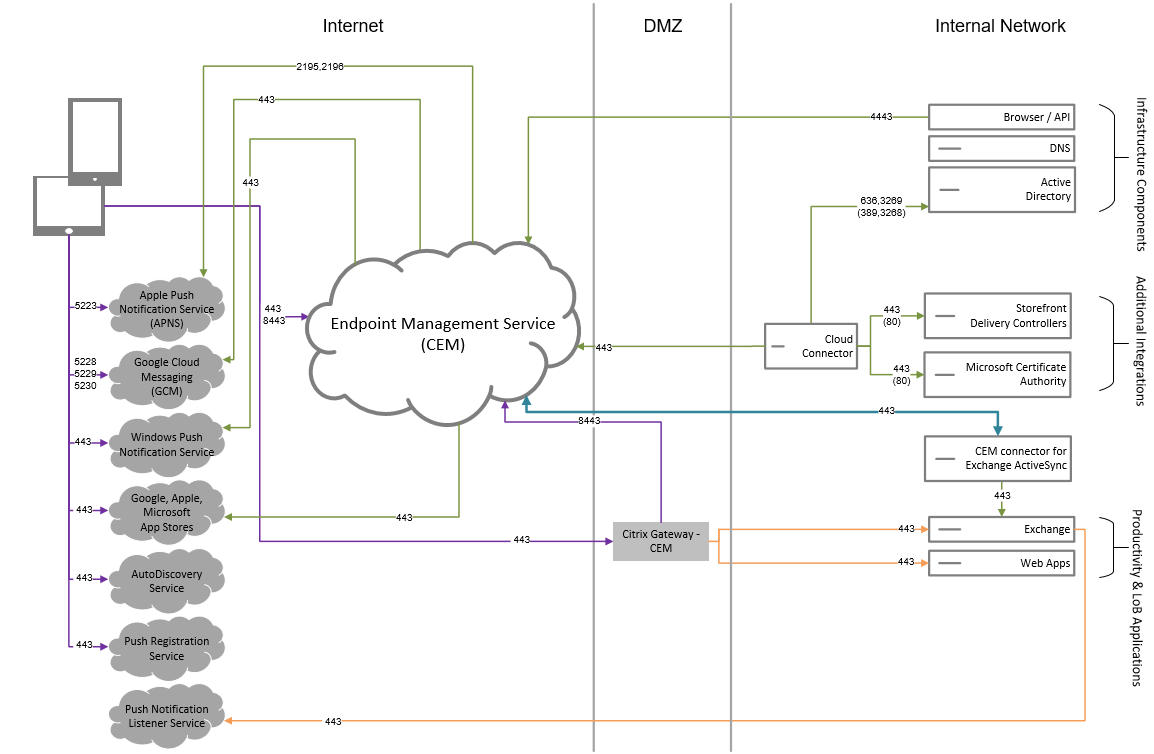
Reference architecture with Citrix Endpoint Management connector for Exchange ActiveSync
Reference architecture with NetScaler Gateway connector for Exchange ActiveSync
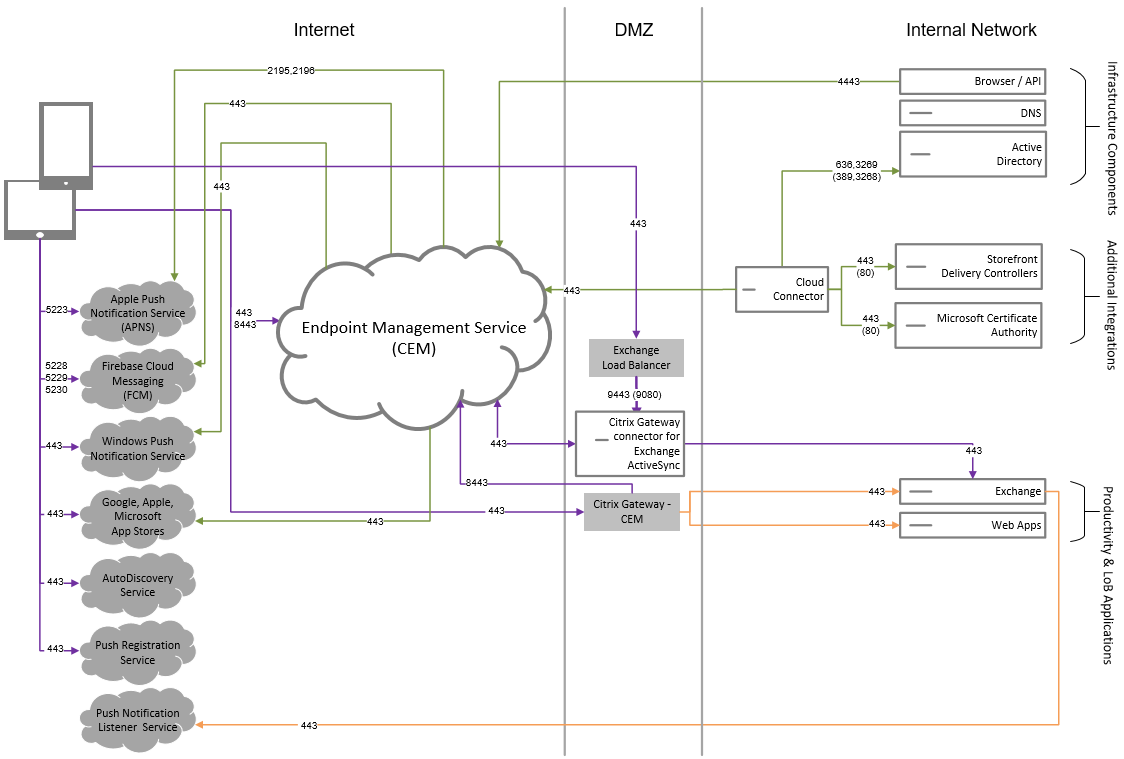
Reference architecture with Citrix Endpoint Management MDM+MAM and Intune MAM
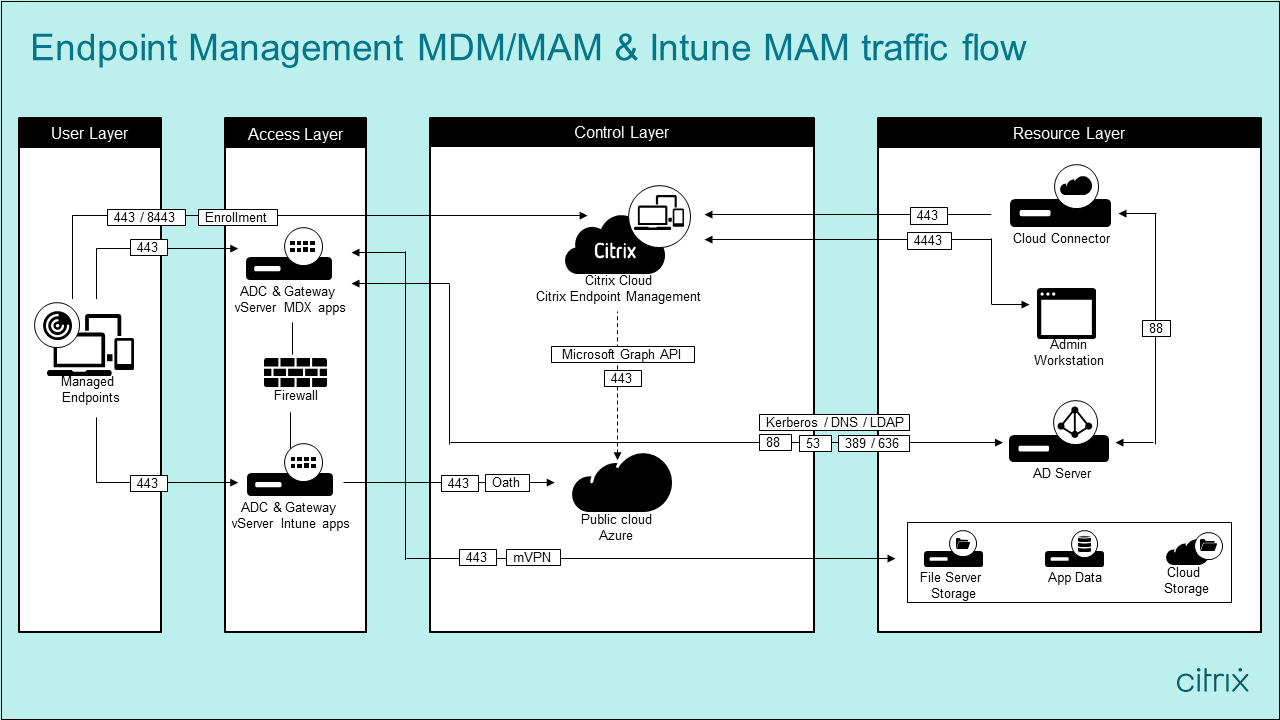
Resource locations
Place resource locations where they best meet your business needs. For example, in a public cloud, in a branch office, a private cloud, or a data center. Factors that determine the choice of location include:
- Proximity to subscribers
- Proximity to data
- Scale requirements
- Security attributes
You can build any number of resource locations. For example, you might:
- Build a resource location in your data center for the head office, based on subscribers and applications that require proximity to the data.
- Add a separate resource location for your global users in a public cloud. Or, build separate resource locations in branch offices to provide the applications best served close to the branch workers.
- Add a further resource location on a separate network that provides restricted applications. This setup provides restricted visibility to other resources and subscribers without the need to adjust the other resource locations.
Cloud Connector
Cloud Connector authenticates and encrypts all communication between Citrix Cloud and your resource locations. Cloud Connector is required to access the following services: LDAP, IdPs, PKI Server, internal DNS queries, Citrix Virtual Apps, NetScaler Gateway, Citrix Workspace, and Microsoft Endpoint Manager.
The following diagram shows the traffic flow for Cloud Connector.
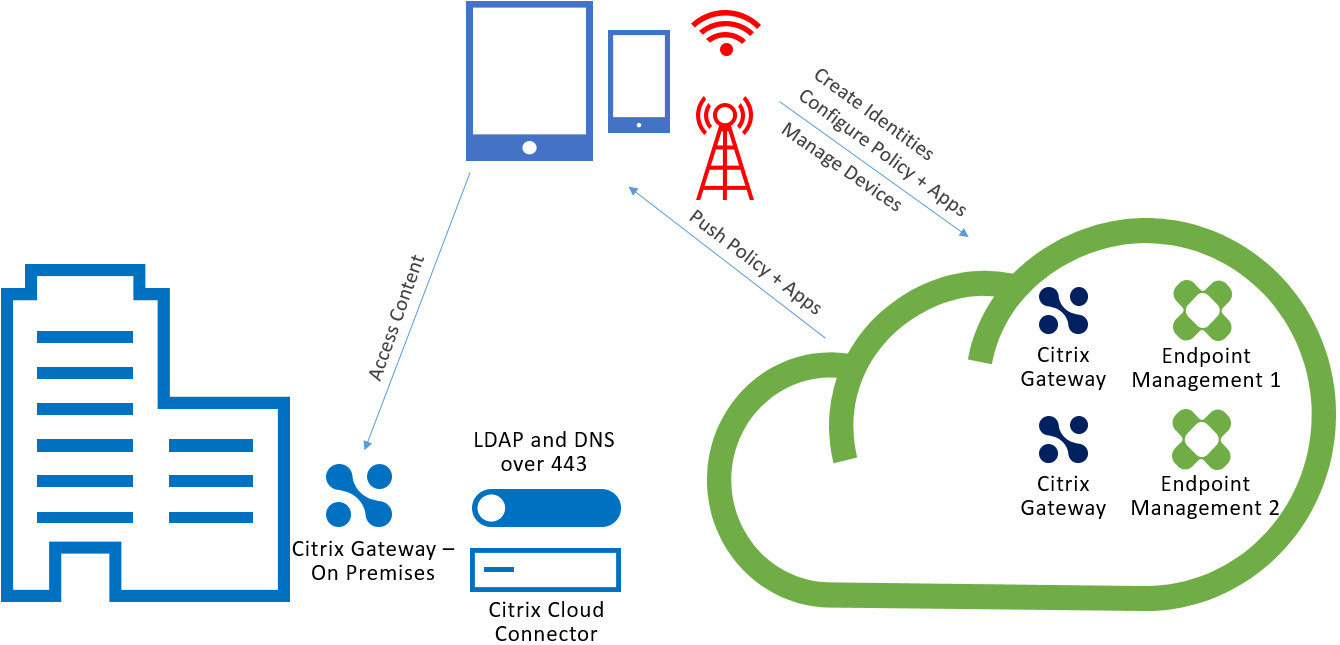
Cloud Connector establishes connections to Citrix Cloud. Cloud Connector doesn’t accept incoming connections.
Cloud Connector is under load only during device enrollment. For more information, see Scale and size considerations for Cloud Connectors.
A solution that includes Mobile App Management (MAM) requires a micro VPN that is provided by an on-premises NetScaler Gateway. In this scenario:
- The following components are in your data center:
- Cloud Connector
- NetScaler Gateway
- Your servers for Exchange, web apps, Active Directory, and PKI
- Mobile devices communicate with Citrix Endpoint Management and your on-premises NetScaler Gateway.
Citrix Endpoint Management components
Citrix Endpoint Management console. You use the Citrix Endpoint Management administrator console to configure Citrix Endpoint Management. For details about using the Citrix Endpoint Management console, see the articles under Citrix Endpoint Management. Citrix notifies you when the What’s new articles for Citrix Endpoint Management are updated for a new release.
Note these differences between the Citrix Endpoint Management service and the on-premises releases:
- The Remote Support client is not available for Citrix Endpoint Management.
- Citrix does not support syslog integration in Citrix Endpoint Management with an on-premises syslog server. Instead, you can download the logs from the Troubleshooting and Support page in the Citrix Endpoint Management console. When doing so, you must click Download All.
MAM SDK. The MDX Toolkit is scheduled to reach EOL in July 2023. To continue managing your enterprise applications, you must incorporate the MAM SDK.
- The Mobile Application Management (MAM) SDK provides MDX functionality that isn’t covered by the iOS and Android platforms. You can MDX-enable and secure iOS or Android apps. You make those apps available in either an internal store or public app stores. See MDX App SDK.
Mobile productivity apps. Citrix-developed mobile productivity apps provide a suite of productivity and communication tools within the Citrix Endpoint Management environment. Your company policies secure those apps. For more information, see Mobile productivity apps.
Citrix Endpoint Management connector for Exchange ActiveSync. Citrix Endpoint Management connector for Exchange ActiveSync provides secure email access to users who use native mobile email apps. The connector for Exchange ActiveSync provides ActiveSync filtering at the Exchange service level. As a result, filtering only occurs once the mail reaches the Exchange service, rather than when it enters the Citrix Endpoint Management environment. The connector doesn’t require the use of NetScaler Gateway. You can deploy the connector without changing the routing for the existing ActiveSync traffic. For more information, see Citrix Endpoint Management connector for Exchange ActiveSync.
NetScaler Gateway connector for Exchange ActiveSync. NetScaler Gateway connector for Exchange ActiveSync provides secure email access to users who use native mobile email apps. The connector for Exchange ActiveSync provides ActiveSync filtering at the perimeter. The filtering uses NetScaler Gateway as a proxy for ActiveSync traffic. As a result, the filtering component sits in the path of mail traffic flow, intercepting mail as it enters or leaves the environment. The connector for Exchange ActiveSync acts an intermediary between NetScaler Gateway and Citrix Endpoint Management. For more information, see NetScaler Gateway connector for Exchange ActiveSync.
Citrix Endpoint Management technical security overview
Citrix Cloud manages the control plane for Citrix Endpoint Management environments. The control plane includes the Citrix Endpoint Management server, Citrix ADC load balancer, and a single-tenant database. The cloud service integrates with a customer data center using the Citrix Cloud Connector. Citrix Endpoint Management customers who use Cloud Connector typically manage NetScaler Gateway in their data centers.
The following figure illustrates the service and its security boundaries.
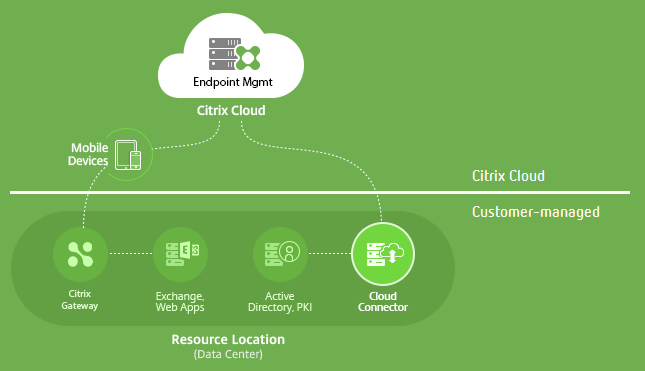
The information in this section:
- Provides an introduction to the security functionality of Citrix Cloud.
- Defines the division of responsibility between Citrix and customers for securing the Citrix Cloud deployment.
- Isn’t the configuration or administration guidance for Citrix Cloud or any of its components or services.
For information about the technology used by Citrix Endpoint Management to deliver comprehensive, end-to-end security, see Security and Productivity for the Mobile Enterprise.
Data flow
The control plane has limited read access to user and group objects. Those objects are in your directory, DNS, and similar services. The control plane accesses those services over Citrix Cloud Connector through secure HTTPS connections.
Company data, such as email, intranet, and web-app traffic, flows directly between a device and the application servers over NetScaler Gateway. NetScaler Gateway is deployed in the customer data center.
Data isolation
The control plane stores metadata needed for managing user devices and their mobile applications. The service itself consists of a mix of multi- and single-tenant components. However, per the service architecture, customer metadata is always stored separately for each tenant and secured by using unique credentials.
Credential handling
The service handles the following types of credentials:
- User credentials: User credentials are transmitted from the device to the control plane over an HTTPS connection. The control plane validates these credentials with a directory in the customer directory over a secure connection.
- Administrator credentials: Administrators authenticate against Citrix Cloud, which uses the sign-on system from Citrix Online. This process generates a one-time signed JSON Web Token (JWT), which gives the administrator access to the service.
- Active Directory credentials: The control plane requires bind-credentials to read user meta-data from the Active Directory. These credentials are encrypted using AES-256 encryption and saved in a per-tenant database.
Deployment considerations
Citrix recommends that you consult the published best practices documentation for deploying NetScaler Gateway within your environments.
More resources
Customers are advised to review security bulletins that relate to their Citrix products. For information on new and updated security bulletins, see Citrix Security Bulletins. Also consider signing up to receive alerts under your Alert Settings.
See the following resources for more security information:
- Citrix Security Site: https://www.citrix.com/security
- Citrix Cloud Documentation: Secure Deployment Guide for the Citrix Cloud Platform
- Secure Deployment Guide for Citrix ADC
Integration with Mobile Threat Defense software
Mobile Threat Defense (MTD) software detects, analyzes, and helps prevent advanced cyberattacks against enterprise mobile devices. The combination of MTD and Unified Citrix Endpoint Management (UEM) increases security and visibility for your organization.
MTD software provides threat data that Citrix Endpoint Management uses to:
- Protect against malware, phishing, network attacks, and man-in-the-middle attacks
- Determine device compliance status
- Determine risk levels
- Take policy-based actions to protect your apps, data, devices, and mobile network
Citrix Endpoint Management integrates with the following MTD vendors:
For more information or to request a demo, contact our MTD partners or your Citrix Sales Representative.