SSO and proxy considerations for MDX apps
Citrix Endpoint Management integration with NetScaler Gateway enables you to provide users with single sign-on (SSO) to all back end HTTP/HTTPS resources. Depending on your SSO authentication requirements, configure user connections for an MDX app to use Secure Browse (Tunneled - Web SSO), which is a type of clientless VPN.
Important:
Citrix deprecated support for a full VPN tunnel and a Proxy Automatic Configuration (PAC) file with a full VPN tunnel deployment for iOS and Android devices. For more information, see Deprecation.
If NetScaler Gateway isn’t the best way to provide SSO in your environment, you can set up an MDX app with policy-based local password caching. This article explores the various SSO and proxy options, with a focus on Citrix Secure Web. The concepts apply to other MDX apps.
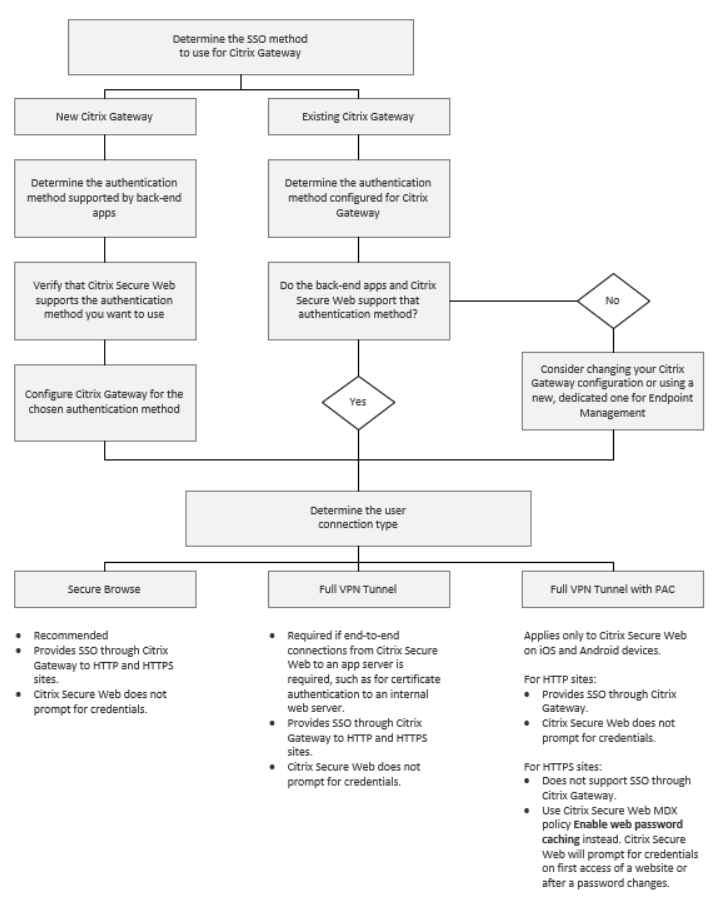
The following flow chart summarizes the decision flow for SSO and user connections.
NetScaler Gateway authentication methods
This section provides general information about the authentication methods supported by NetScaler Gateway.
SAML authentication
When you configure NetScaler Gateway for Security Assertion Markup Language (SAML), users can connect to web apps that support the SAML protocol for single sign-on. NetScaler Gateway supports the identity provider (IdP) single sign-on for SAML web apps.
Required configuration:
- Configure SAML SSO in the NetScaler Gateway Traffic profile.
- Configure the SAML IdP for the requested service.
NTLM authentication
If SSO to web apps is enabled in the session profile, NetScaler Gateway does NTLM authentication automatically.
Required configuration:
- Enable SSO in the NetScaler Gateway Session or Traffic profile.
Kerberos impersonation
Citrix Endpoint Management supports Kerberos for Citrix Secure Web only. When you configure NetScaler Gateway for Kerberos SSO, NetScaler Gateway uses impersonation when a user password is available to NetScaler Gateway. Impersonation means that NetScaler Gateway uses user credentials to get the ticket required to gain access to services, such as Citrix Secure Web.
Required configuration:
- Configure the NetScaler Gateway
WorxSession policy to allow it to identify the Kerberos Realm from your connection. - Configure a Kerberos Constrained Delegation (KCD) account on NetScaler Gateway. Configure that account with no password and bind it to a traffic policy on your Citrix Endpoint Management gateway.
- For those and other configuration details, see the Citrix blog: WorxWeb and Kerberos Impersonation SSO.
Kerberos Constrained Delegation
Citrix Endpoint Management supports Kerberos for Citrix Secure Web only. When you configure NetScaler Gateway for Kerberos SSO, NetScaler Gateway uses constrained delegation when a user password is not available to NetScaler Gateway.
With constrained delegation, NetScaler Gateway uses a specified administrator account to get tickets for users and services.
Required configuration:
- Configure a KCD account in the Active Directory with the required permissions and a KDC account on NetScaler Gateway.
- Enable SSO in the NetScaler Gateway Traffic profile.
- Configure the back-end website for Kerberos authentication.
Form Fill Authentication
When you configure NetScaler Gateway for Form-based single sign-on, users can log on one time to access all protected apps in your network. This authentication method applies to apps that use the Tunneled - Web SSO mode.
Required configuration:
- Configure a Form-based SSO in the NetScaler Gateway Traffic profile.
Digest HTTP authentication
If you enable SSO to web apps in the session profile, NetScaler Gateway does digest HTTP authentication automatically. This authentication method applies to apps that use Tunneled - Web SSO mode.
Required configuration:
- Enable SSO in the NetScaler Gateway Session or Traffic profile.
Basic HTTP authentication
If you enable SSO to web apps in the session profile, NetScaler Gateway does basic HTTP authentication automatically. This authentication method applies to apps that use Tunneled - Web SSO mode.
Required configuration:
- Enable SSO in the NetScaler Gateway Session or Traffic profile.
Secure Tunneled - Web SSO
This section describes the Tunneled - Web SSO user connection types for Citrix Secure Web.
Connections that tunnel to the internal network can use a variation of a clientless VPN, referred to as Tunneled - Web SSO. Tunneled - Web SSO is the default configuration specified for the Citrix Secure Web Preferred VPN mode policy. Citrix recommends Tunneled - Web SSO for connections that require single sign-on (SSO).
In Tunneled - Web SSO mode, NetScaler Gateway breaks the HTTPS session into two parts:
- From the client to NetScaler Gateway
- From NetScaler Gateway to the back-end resource server.
In this manner, NetScaler Gateway has full visibility into all transactions between the client and server, enabling it to provide SSO.
You can also configure proxy servers for Citrix Secure Web when used in Tunneled - Web SSO mode. For details, see the blog Citrix Endpoint Management WorxWeb Traffic Through Proxy Server in Secure Browse Mode.
Note:
Citrix announced the deprecation of the Full VPN tunnel with PAC. See Deprecation.
Citrix Endpoint Management supports proxy authentication provided by NetScaler Gateway. A PAC file has rules that define how web browsers select a proxy to access a given URL. PAC file rules can specify handling for both internal and external sites. Citrix Secure Web parses the PAC file rules and sends the proxy server information to NetScaler Gateway. NetScaler Gateway is unaware of the PAC file or proxy server.
For authentication to HTTPS websites: The Citrix Secure Web MDX policy Enable web password caching enables Citrix Secure Web to authenticate and provide SSO to the proxy server through MDX.
NetScaler Gateway Split Tunneling
When planning your SSO and proxy configuration, you must also decide whether to use NetScaler Gateway split tunneling. Citrix recommends that you use NetScaler Gateway split tunneling only if needed. This section provides a high-level look at how split tunneling works: NetScaler Gateway determines the traffic path based on its routing table. When NetScaler Gateway split tunneling is on, Citrix Secure Hub distinguishes internal (protected) network traffic from Internet traffic. Citrix Secure Hub makes that determination based on the DNS suffix and Intranet applications. Citrix Secure Hub then tunnels only the internal network traffic through the VPN tunnel. When NetScaler Gateway split tunneling is off, all traffic goes through the VPN tunnel.
If you prefer to monitor all the traffic because of security considerations, disable NetScaler Gateway split tunneling. As a result, all traffic goes through the VPN tunnel.
NetScaler Gateway also has a micro VPN reverse split tunnel mode. This configuration supports an exclusion list of IP addresses that aren’t tunneled to the NetScaler Gateway. Instead, those addresses are sent by using the device internet connection. For more information about reverse split tunneling, see the NetScaler Gateway documentation.
Citrix Endpoint Management includes a Reverse split tunnel exclusion list. To prevent certain websites from tunneling through NetScaler Gateway: Add a comma-separated list of fully qualified domain names (FQDN) or DNS suffixes that connect by using the LAN instead. This list applies only to Tunneled - Web SSO mode with NetScaler Gateway configured for reverse split tunneling.