Compliance Enforcement for Android device (Technical Preview)
Note:
Features in the Technical Preview are available to use in non-production or limited production environments, and to give customers an opportunity to share feedback. Citrix® does not accept support cases for features in technical preview but welcomes feedback for improving them. You can provide feedback on this feature by clicking Send us your feedback. Citrix might act on feedback based on its severity, criticality, and importance.
For Android devices enrolled in Device Owner mode, customer admin can manage the device compliance. They can define custom rules to assess compliance, including:
- Ensuring device password strength meets specified standards.
- Verifying installation of all required apps.
- Confirming removal of any forbidden apps.
In cases where devices are found non-compliant, customers can prompt users to rectify the issues. Additionally, more stringent measures are available, such as freezing apps on the device to restrict user access until compliance is achieved. To enable this functionality, two prerequisites are necessary, as changes are required on both server and client sides:
- Upgrade CEM Server to version 24.8.0.
- Upgrade Secure Hub to version 24.8.0.
Android Device Compliance Management Procedure
- Activate the feature flag
afw.policy.compliancespecifically for the CEM server. - Add and deploy Compliance policy.
-
From the Configure tab, select Device Policies, and click Compliance.
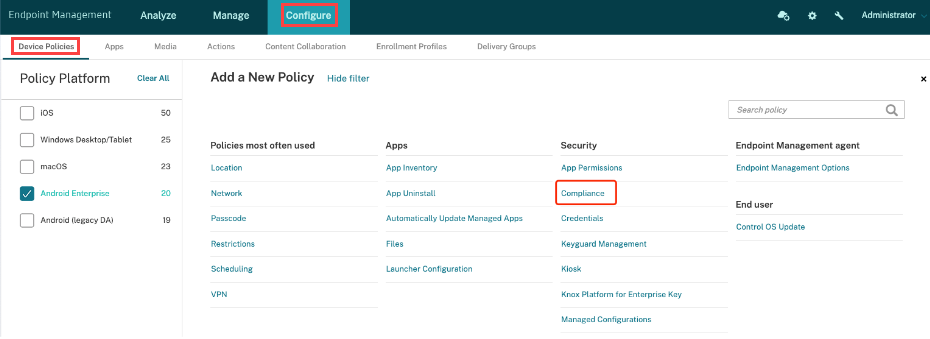
-
Configure the policy with the following settings:
- Enable Compliance Check: This setting controls whether devices undergo compliance checks. To revoke a deployed compliance policy, disable this option and redeploy the policy. Just by removing the policy from the delivery group will not be effective.
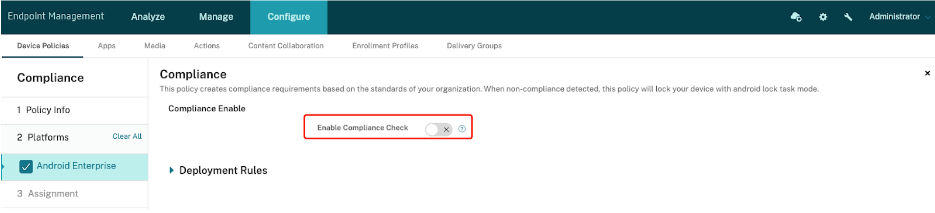
- Non-Compliance Action: Choose between Only Warning and Freeze Apps (only corporate owned device). Selecting Only Warning will notify users in Secure Hub about non-compliant items and request them to address these issues. Choosing Freeze Apps (only corporate owned device) locks all apps on the device, but admins can customize an Unfrozen Apps list to exempt specific apps, such as Secure Hub (for displaying and resolving non-compliant items), Google Play Store (for installing necessary apps), Settings (for factory resets), and SMS (for emergency communication). The Freeze Apps (only corporate owned device) is applicable only to corporate owned devices.
- Verify Passcode Compliance: Checks if device passcodes meet the specified standards. Typically used with passcode policies.
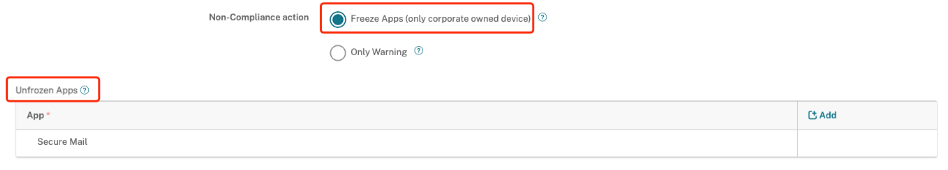
- Verify Required apps: Displays a list of mandatory apps. Ensures these apps are installed on the device.
Note:
- Apps listed under Required Apps must also be included in the required apps section of the delivery group to ensure their functionality. Otherwise, they will not be effective.
- As required apps might be unavailable in managed Google Play, end users will remain in locked mode.
- Verify Forbidden Apps: Displays a list of prohibited apps. Ensures none of these apps are installed.
Note:
Admins should refrain from adding system pre-installed apps to the Forbidden Apps list, as end users do not have permission to remove them.
-
- Deploy Policy.
- In Secure Hub, click Refresh Policy or wait for the 6-hour periodic sync to deploy the policy to devices.
- Upon deployment, a compliance check is immediately triggered. Non-compliant devices in Freeze Apps mode restrict both the device and its apps until compliance is met.
If the admin configures the Non-compliance Action to Freeze Apps, both Secure Hub and the device itself will restrict app usage. Specifically:
- A persistent notification will appear in the notification bar, reminding the user that apps have been frozen.
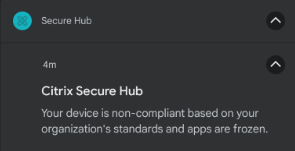
- Apps, excluding those listed as default allowed or in the Unfrozen Apps list, will be frozen and unresponsive when clicked.
- This state persists until the device achieves compliance. Even after restarting or undergoing a system upgrade, the device will immediately return to this frozen state (except during Secure Hub upgrades, which require manual launching by the user).
- Non-Compliance Resolution:
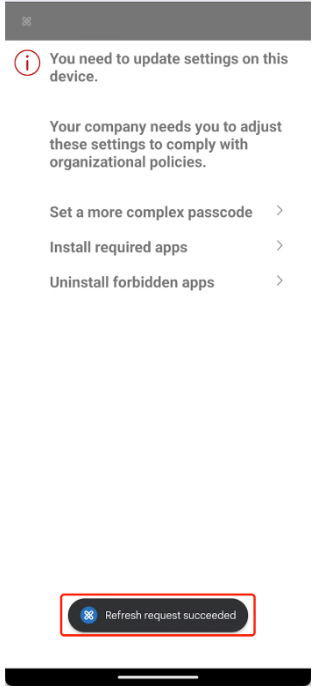
- When a device is non-compliant, Secure Hub is blocked from refreshing the policy through the usual method (clicking the Refresh policy button in Device information page).
- Instead, an alternative solution is provided by pulling down the page that displays the non-compliant items, and the refresh result is conveyed through a toast notification.
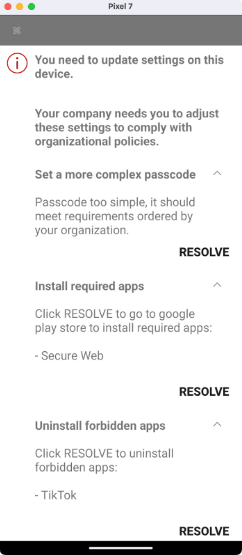
- Specific actions for users:
- Set a more complex passcode to meet standards.
- Install required apps from the Google Play Store.
- Uninstall forbidden apps.
- Monitoring compliance
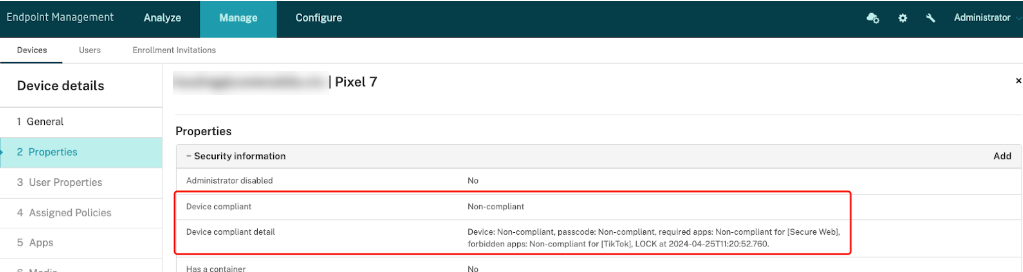
- View compliance status: A new compliance status icon in Manage -> Devices -> Status. Green indicates compliance, while orange indicates non-compliance.
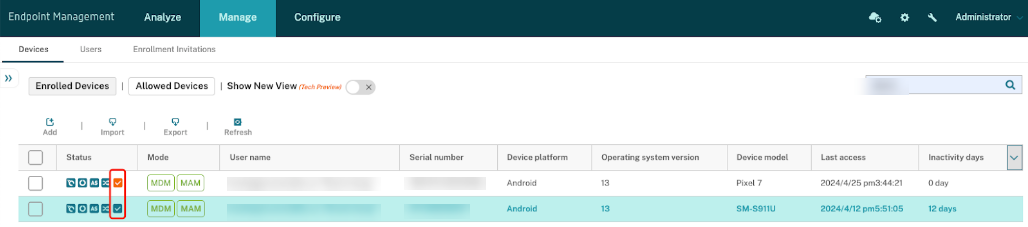
- Detailed compliance status available in Manage -> Devices -> Device details -> Properties -> Security Information.
Troubleshooting
-
The configured required app cannot be found on the Google Play Store, resulting in the device becoming non-compliant and unable to resolve the issue. This is a design flaw.
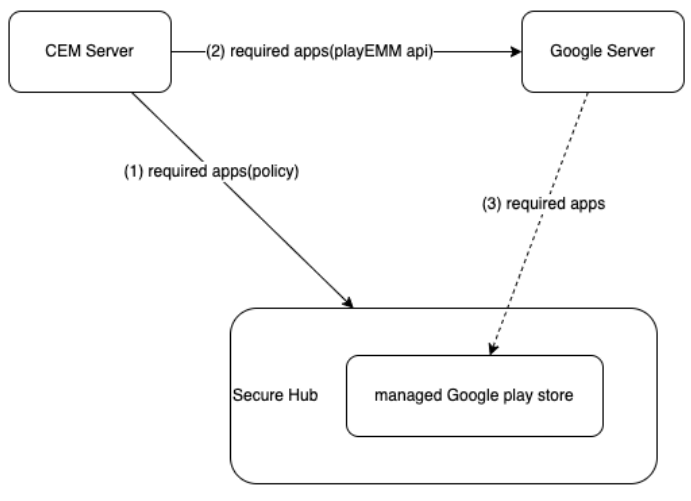
The CEM Server pushes required apps to Secure Hub and Google Servers through links 1 and 2, but link 3 is beyond our control. When Secure Hub checks for required apps using link 1, we cannot guarantee that the managed Google Play Store has these apps available. This discrepancy means that while the compliance policy requires Secure Hub to install these apps, they might not not be found in the store immediately. Typically, Google Servers push the required apps to the device within 24 hours using link 3.
-
Before upgrading Secure Hub, the device was non-compliant, and the apps were frozen. However, after upgrading Secure Hub, all apps were unfrozen. This occurred because during the upgrade process, Secure Hub’s operation was terminated, preventing it from maintaining the app freeze. This issue is known and currently has no solution. We are actively working with Google to address this and expect improvements in future versions. After completing the upgrade, users can manually launch Secure Hub to initiate the process and restore the apps to their frozen state.
- How to unfreeze apps?
The most common method is for users to resolve all non-compliant issues, thereby bringing the device into compliance and automatically unfreezing all apps. If it’s not feasible to achieve compliance quickly, the following steps can be taken:
- Add related apps to the Unfrozen Apps list and perform a pull-down refresh.
- Change the Non-Compliance Action to Warning and perform a pull-down refresh.
- Disable the check switch corresponding to non-compliant items or the master switch, then perform a pull-down refresh.
- If none of the above methods work, enable the feature flag
afw.locktaskmode.disablefor the specific CEM server and perform a pull-down refresh. This action forcibly unfreezes all apps, but Secure Hub remains blocked similar to when Non-Compliance Action is set to Warning. - Disable the feature flag
afw.policy.compliancefor the specific CEM server and perform a pull-down refresh. - In the worst-case scenario where Secure Hub cannot connect to the CEM Server, perform a factory reset from Settings.
-
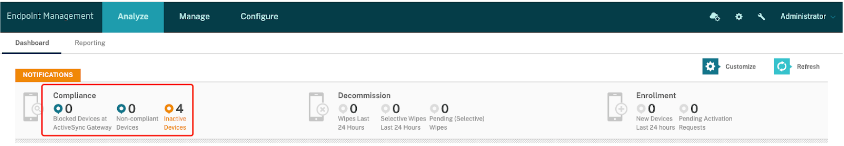
The Compliance status displayed under Analyze -> Dashboard is a different type of compliance in Citrix Endpoint Management™ than the one referenced in this policy. This feature is not yet developed and will be enhanced in future versions.
- This feature does not apply to devices enrolled through COSU/WPCOD/BYOD modes. Currently, it only supports devices enrolled in Device Owner (DO) mode.