-
-
Cloud Connector Standalone Citrix Secure Ticketing Authority (STA) service
-
-
Integrate Citrix Virtual Apps and Desktops with Citrix Gateway
-
Enable TLS on Universal Print Server
-
WebSocket communication between VDA and Delivery Controller™
-
-
-
-
-
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
Enable TLS on Universal Print Server
The Transport Layer Security (TLS) protocol is supported for TCP-based connections between the Virtual Delivery Agent (VDA) and the Universal Print Server.
Warning:
For tasks that include working in the Windows registry—editing, the registry incorrectly can cause serious problems that may require you to reinstall your operating system. Citrix® cannot guarantee that problems resulting from the incorrect use of Registry Editor can be solved. Use Registry Editor at your own risk. Be sure to back up the registry before you edit it.
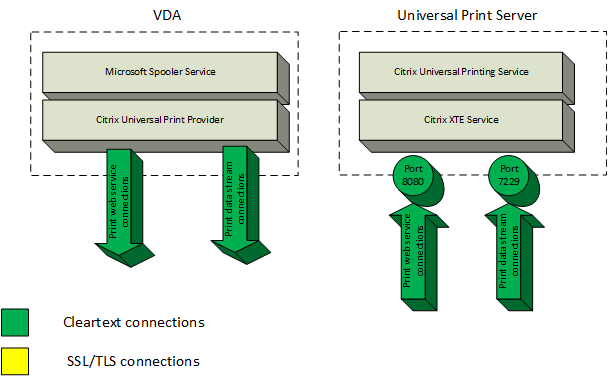
Types of printing connections between the VDA and Universal Print Server
Cleartext connections
The following connections related to printing originate from the VDA and connect to ports on the Universal Print Server. These connections are made only when the SSL enabled policy setting is set to Disabled (the default).
- Cleartext print web service connections (TCP port 8080)
- Cleartext print data stream (CGP) connections (TCP port 7229)
The Microsoft support article Service overview and network port requirements for Windows describes the ports used by the Microsoft Windows Print Spooler Service. The SSL/TLS settings in this document do not apply to the NetBIOS and RPC connections made by the Windows Print Spooler service. The VDA uses the Windows Network Print Provider (win32spl.dll) as a fallback if the Universal Print Server enable policy setting is set to Enabled with fallback to Windows’ native remote printing.
Encrypted connections
These SSL/TLS connections related to printing originate from the VDA and connect to ports on the Universal Print Server. These connections are made only when the SSL enabled policy setting is set to Enabled.
- Encrypted print web service connections (TCP port 8443)
- Encrypted print data stream (CGP) connections (TCP port 443)
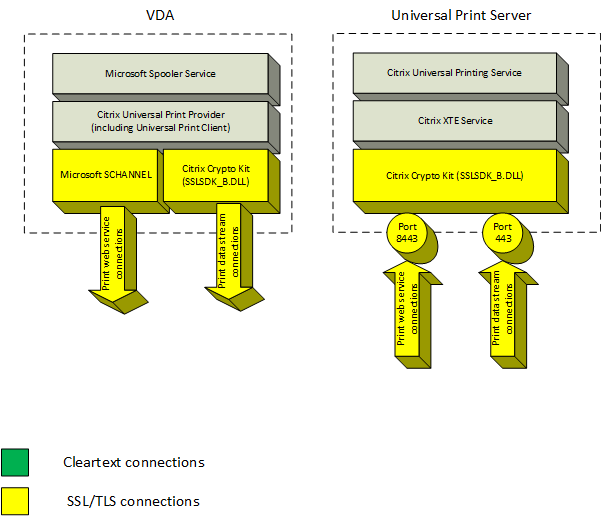
SSL/TLS client configuration
The VDA functions as the SSL/TLS client.
Use Microsoft Group Policy and the registry to configure Microsoft SCHANNEL SSP for encrypted print web service connections (TCP port 8443). The Microsoft support article TLS Registry Settings describes the registry settings for Microsoft SCHANNEL SSP.
Using the Group Policy Editor on the VDA, go to Computer Configuration > Administrative Templates > Network > SSL Configuration Settings > SSL Cipher Suite Order. Select the following order when TLS 1.3 is set:
TLS_AES_256_GCM_SHA384 TLS_AES_128_GCM_SHA256
Select the following order when TLS 1.2 is set:
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384_P384 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384_P256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256
Note:
When this Group Policy setting is configured, the VDA selects a cipher suite for encrypted print web service connections (default port: 8443) only if the connections appear in both SSL cipher suite lists:
- Group Policy SSL cipher suite order list
- List corresponding to the selected SSL Cipher Suite policy setting (COM, GOV, or ALL)
This Group Policy configuration also affects other TLS applications and services on the VDA. If your applications require specific cipher suites, you might need to add them to this Group Policy Cipher Suite Order list.
Important:
Group Policy changes for TLS configuration take effect only after an operating system restart.
Use a Citrix policy to configure SSL/TLS settings for encrypted print data stream (CGP) connections (TCP port 443).
SSL/TLS server configuration
The Universal Print Server functions as the SSL/TLS server.
Use the Enable-UpsSsl.ps1 PowerShell script to configure SSL/TLS settings.
Install a TLS certificate on the Universal Print Server
For HTTPS, you must install an SSL server certificate on the Universal Print Server that is trusted by the VDAs. Use Microsoft Active Directory Certificate Services or another certification authority to request a certificate for the Universal Print Server.
Keep in mind the following considerations when enrolling/requesting a certificate using Microsoft Active Directory Certificate Services:
- Place the certificate in the Local Computer Personal certificate store.
- Set the Common Name attribute of the Subject Distinguished Name (Subject DN) of the certificate to the fully qualified domain name (FQDN) of the Universal Print Server. Specify this in the certificate template.
- Set the Cryptographic Service Provider (CSP) used to generate the certificate request and private key to Microsoft Enhanced RSA and AES Cryptographic Provider (Encryption). Specify this in the certificate template.
- Set the Key Size to at least 2048 bits. Specify this in the certificate template.
For more information on creating and installing certificates, see Manage certificates.
Configuring SSL on the Universal Print Server
The XTE Service on the Universal Print Server listens for incoming connections. It functions as an SSL server when SSL is enabled. The incoming connections have two types: print web service connections, which contain printing commands, and print data stream connections, which contain print jobs. SSL can be enabled on these connections. SSL protects the confidentiality and integrity of these connections. By default, SSL is disabled.
The PowerShell script used to configure SSL is on the installation media and has this file name: \Support\Tools\SslSupport\Enable-UpsSsl.ps1.
Configuring listening port numbers on the Universal Print Server
These are the default ports for the XTE Service:
- Cleartext print web service (HTTP) TCP port: 8080
- Cleartext print data stream (CGP) TCP port: 7229
- Encrypted print web service (HTTPS) TCP port: 8443
- Encrypted print data stream (CGP) TCP port: 443
To change the ports used by the XTE Service on the Universal Print Server, run the following commands in PowerShell as administrator (see the later section for notes on the usage of the Enable-UpsSsl.ps1 PowerShell script):
Stop-Service CitrixXTEServer, UpSvc-
Enable-UpsSsl.ps1 -Enable -HTTPSPort <port> -CGPSSLPort <port>orEnable-UpsSsl.ps1 -Disable -HTTPPort <port> -CGPPort <port> Start-Service CitrixXTEServer
TLS settings on Universal Print Server
If you have multiple Universal Print Servers in a load-balanced configuration, ensure that the TLS settings are configured consistently across all Universal Print Servers.
When you configure TLS on Universal Print Server, permissions on the installed TLS certificate are changed, giving the Universal Printing Service read access to the certificate’s private key, and informing the Universal Printing Service of the following:
- Which certificate in the certificate store to use for TLS.
- Which TCP port numbers to use for TLS connections.
The Windows Firewall (if enabled) must be configured to allow incoming connections on these TCP ports. This configuration is done for you when you use the Enable-UpsSsl.ps1 PowerShell script.
- Which versions of the TLS protocol to allow.
Universal Print Server supports TLS protocol versions 1.3 and 1.2. Specify the minimum allowed version.
The default TLS protocol version is 1.2.
Note:
TLS 1.1 and 1.0 are no longer supported from Citrix Virtual Apps and Desktops version 2311.
- Which TLS cipher suites to allow.
A cipher suite selects the cryptographic algorithms that are used for a connection. VDAs and Universal Print Server can support different sets of cipher suites. When a VDA connects and sends a list of supported TLS cipher suites, the Universal Print Server matches one of the client’s cipher suites with one of the cipher suites in its own list of configured cipher suites and accepts the connection. If there is no matching cipher suite, the Universal Print Server rejects the connection.
The Universal Print Server supports the following sets of cipher suites named GOV(ernment), COM(mercial), and ALL for the OPEN, FIPS, and SP800-52 native Crypto Kit modes. The acceptable cipher suites also depend on the SSL FIPS Mode policy setting and on the Windows FIPS Mode. See this Microsoft support article for information about Windows FIPS mode.
| Cipher suite (in decreasing priority order) | OPEN ALL | OPEN COM | OPEN GOV | FIPS ALL | FIPS COM | FIPS GOV | SP800-52 ALL | SP800-52 COM | SP800-52 GOV |
|---|---|---|---|---|---|---|---|---|---|
| TLS_ECDHE_RSA_ AES256_GCM_SHA384 | X | X | X | X | X | X | |||
| TLS_ECDHE_RSA_ AES256_CBC_SHA384 | X | X | X | X | X | X | |||
| TLS_ECDHE_RSA_ AES256_CBC_SHA | X | X | X | X | X | X |
Configure TLS on a Universal Print Server using the PowerShell script
Install the TLS Certificate in the Local Computer > Personal > Certificates area of the certificate store. If more than one certificate resides in that location, supply the thumbprint of the certificate to the Enable-UpsSsl.ps1 PowerShell script.
Note:
The PowerShell script finds the correct certificate based on the FQDN of the Universal Print Server. You do not need to supply the certificate thumbprint when only a single certificate is present for the Universal Print Server FQDN.
The Enable-UpsSsl.ps1 script enables or disables TLS connections originating from the VDA to the Universal Print Server. This script is available in the Support > Tools > SslSupport folder on the installation media.
When you enable TLS, the script disables all existing Windows Firewall rules for the Universal Print Server’s TCP ports. It then adds new rules that allow the XTE Service to accept incoming connections only on the TLS TCP and UDP ports. It also disables the Windows Firewall rules for:
- Cleartext print web service connections (default: 8080)
- Cleartext print data stream (CGP) connections (default: 7229)
The effect is that the VDA can make these connections only when using TLS.
Note:
Enabling TLS does not affect Windows Print Spooler RPC/SMB connections originating from the VDA and going to the Universal Print Server.
Important:
Specify either Enable or Disable as the first parameter. The CertificateThumbprint parameter is optional if only one certificate in the Local Computer Personal certificate store has the Universal Print Server’s FQDN. The other parameters are optional.
Syntax
Enable-UpsSSL.ps1 -Enable [-HTTPPort <port>] [-CGPPort <port>] [–HTTPSPort <port>] [-CGPSSLPort <port>] [-SSLMinVersion <version>] [-SSLCipherSuite <name>] [-CertificateThumbprint <thumbprint>] [-FIPSMode <Boolean>] [-ComplianceMode <mode>]
Enable-UpsSSL.ps1 -Disable [-HTTPPort <portnum>] [-CGPPort <portnum>]
| Parameter | Description |
|---|---|
| Enable | Enables SSL/TLS on the XTE Server. Either this parameter or the Disable parameter is required. |
| Disable | Disables SSL/TLS on the XTE Server. Either this parameter or the Enable parameter is required. |
CertificateThumbprint "<thumbprint>"
|
Thumbprint of the TLS certificate in the Local Computer Personal certificate store, enclosed in quotation marks. The script uses the specified thumbprint to select the certificate you want to use. |
HTTPPort <port>
|
Cleartext print web service (HTTP/SOAP) port. Default: 8080 |
CGPPort <port>
|
Cleartext print data stream (CGP) port. Default: 7229 |
HTTPSPort <port>
|
Encrypted print web service (HTTPS/SOAP) port. Default: 8443 |
CGPSSLPort <port>
|
Encrypted print data stream (CGP) port. Default: 443 |
SSLMinVersion "<version>"
|
Minimum TLS protocol version, enclosed in quotation marks. Valid values: “TLS_1.2” and “TLS_1.3”. Default: TLS_1.2. |
SSLCipherSuite "<name>"
|
Name of TLS cipher suite package, enclosed in quotation marks. Valid values: “GOV”, “COM”, and “ALL” (default). |
FIPSMode <Boolean>
|
Enables or disables FIPS 140 mode in the XTE Server. Valid values: $true to enable FIPS 140 mode, $false to disable FIPS 140 mode. |
Examples
The following script enables TLS. The thumbprint (represented as “12345678987654321” in this example) is used to select the certificate to use.
Enable-UpsSsl.ps1 –Enable -CertificateThumbprint "12345678987654321"
The following script disables TLS.
Enable-UpsSsl.ps1 –Disable
Configuring FIPS mode
Enabling US Federal Information Processing Standards (FIPS) mode ensures that only FIPS 140 compliant cryptography is used for Universal Print Server encrypted connections.
Configure FIPS mode on the server before configuring FIPS mode on the client.
Consult Microsoft’s documentation site for enabling/disabling Windows FIPS mode.
Enabling FIPS mode on the client
On the Delivery Controller™, run Web Studio and set the UPS FIPS Mode Citrix policy setting to Enabled. Enable the Citrix policy.
Do this on each VDA:
- Enable Windows FIPS mode.
- Restart the VDA.
Enabling FIPS mode on the server
Do this on each Universal Print Server:
- Enable Windows FIPS mode.
- Run this PowerShell command as Administrator:
stop-service CitrixXTEServer, UpSvc - Run the
Enable-UpsSsl.ps1script with the-Enable -FIPSMode $trueparameters. - Restart the Universal Print Server.
Disabling FIPS mode on the client
On Web Studio, set the UPS FIPS Mode Citrix policy setting to Disabled. Enable the Citrix policy. You can also delete the UPS FIPS Mode Citrix policy setting.
Do this on each VDA:
- Disable Windows FIPS mode.
- Restart the VDA.
Disabling FIPS mode on the server
Do this on each Universal Print Server:
- Disable Windows FIPS mode.
- Run this PowerShell command as Administrator:
stop-service CitrixXTEServer, UpSvc - Run the
Enable-UpsSsl.ps1script with the-Enable -FIPSMode $falseparameters. - Restart the Universal Print Server.
Note:
FIPS mode is not supported when the SSL protocol version is set to TLS 1.3.
Configuring SSL/TLS protocol version
The default SSL/TLS protocol version is TLS 1.2. TLS 1.2 and TLS 1.3 are the recommended SSL/TLS protocol versions for production use. For troubleshooting, it might be necessary to temporarily change the SSL/TLS protocol version in a non-production environment.
SSL 2.0 and SSL 3.0 are not supported on the Universal Print Server.
Setting SSL/TLS protocol version on the server
Do this on each Universal Print Server:
- Run this PowerShell command as Administrator:
stop-service CitrixXTEServer, UpSvc - Run the
Enable-UpsSsl.ps1script with the-Enable -SSLMinVersionversion parameters. Remember to set this back to TLS 1.2 or TLS 1.3 when you are done testing. - Restart the Universal Print Server.
Setting SSL/TLS protocol version on the client
In Studio, set the SSL Protocol Version policy setting to the desired protocol version and enable the policy.
Ensure that the VDA’s operating system supports the selected TLS version. For supported TLS versions on Windows, see Microsoft Learn - TLS protocol version support. To configure the registry to override defaults, see Microsoft Learn - TLS, DTLS, and SSL protocol version settings.
Troubleshooting
If a connection error occurs, check the C:\Program Files (x86)\Citrix\XTE\logs\error.log file on the Universal Print Server.
The error message SSL handshake from client failed appears in this log file if the SSL/TLS handshake fails. Such failures can occur if the SSL/TLS protocol version on the VDA and the Universal Print Server do not match.
Use the Universal Print Server FQDN in the following policy settings that contain Universal Print Server host names:
- Session printers
- Printer assignments
- Universal Print Servers for load balancing
Ensure that the system clock (date, time, and time zone) are correct on the Universal Print Servers and the VDAs.
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.