Citrix Advisor
Citrix Advisor is a service that helps you optimize DaaS deployment and enhance its overall health and readiness. It automates environment checks and delivers actionable recommendations, empowering you to proactively identify configuration issues, inefficiencies, resource wastes, deviations from best practices, and more.
Note:
- This service is available exclusively to Full Administrators.
- We recommend submitting your feedback using the feedback icon in the top-right corner of the page.
Benefits
With Advisor, you can:
- Proactively identify and resolve issues: Detect potential problems, configuration drift, and deviations from best practices before they impact users, disrupt business operations, or compromise security.
- Optimize environment performance and stability: Fine-tune configurations, optimize resource allocation, and implement best practices to enhance the stability, security, and performance of your Citrix deployments.
- Streamline operations and reduce overhead: Automate routine checks, simplify complex remediation tasks, and receive guided assistance, thereby reducing operational overhead and freeing up administrative resources.
- Optimize costs and resource utilization: Identify areas of overspending, uncover opportunities for resource optimization, and ensure efficient utilization of Citrix technologies to minimize the total cost of ownership.
- Maintain compliance and adherence to best practices: Ensure that your Citrix deployments adhere to Citrix best practices, security standards, and industry regulations, reducing risk and improving overall governance.
- Simplify complex tasks: Simplify administrative tasks to support a healthy, optimized environment.
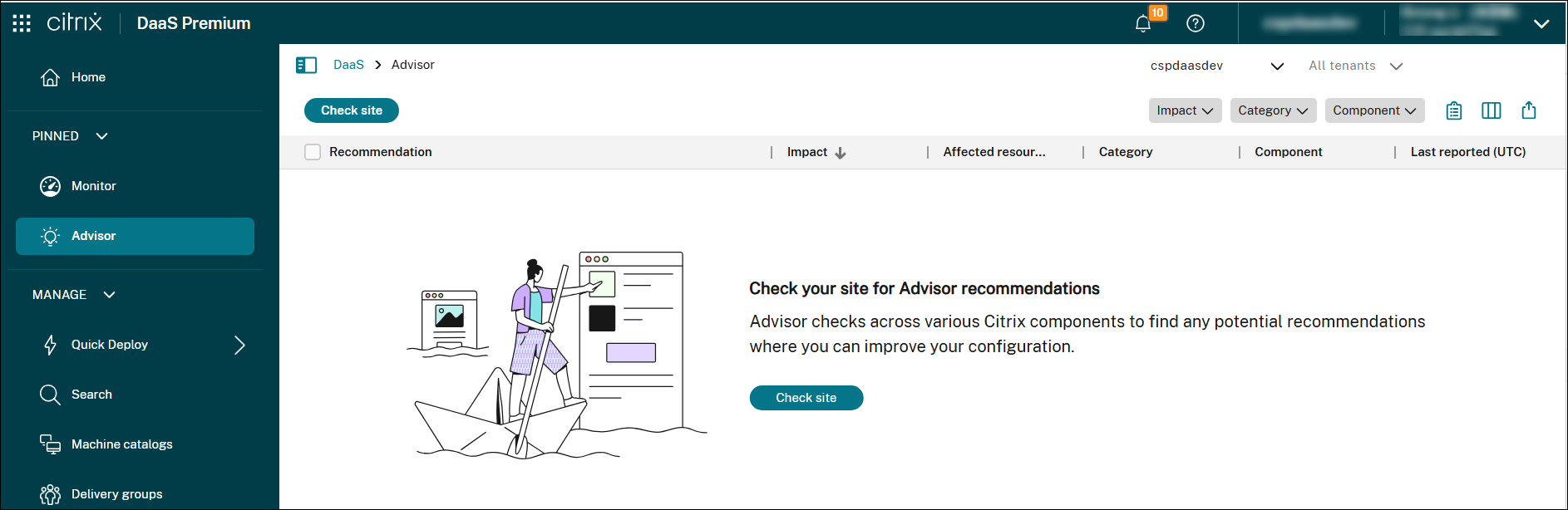
Check for recommendations
To check your site for Advisor recommendations, follow these steps:
- Sign in to Citrix Cloud using an account with the Full Administrator role.
- Click the DaaS tile.
- In the left pane, select Advisor.
-
Click Check site to run a site check and generate updated recommendations based on the current configuration.
All recommendations appear in the list.
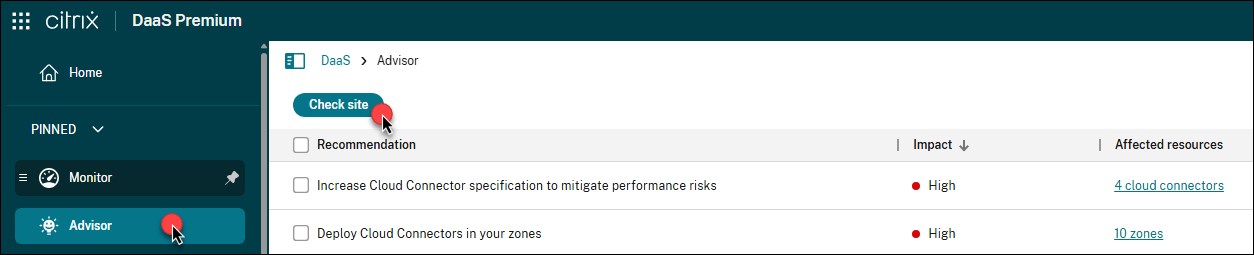
Filter recommendations
You can filter recommendations by Impact, Category, or Component to focus on the information most relevant to your deployment.
-
In Advisor, locate the filters at the top right of the recommendation list.
-
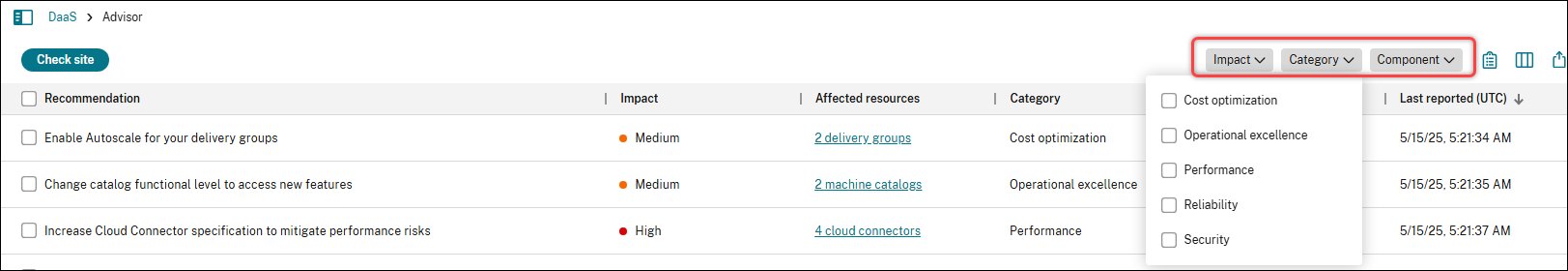
Click a filter (for example, Category) to view available options.
Category Description Reference Security Recommendations for detecting threats and vulnerabilities that might lead to security breaches. Security recommendations Reliability Recommendations for ensuring and improving the continuity of your business-critical applications. Reliability recommendations Performance Recommendations for enhancing performance across applications and desktops to deliver faster, more responsive experiences for end users. Performance recommendations Operational excellence Recommendations for helping you achieve process and workflow efficiency, resource manageability, and deployment best practices. Operational excellence recommendations Cost optimization Recommendations for reducing overall spending by right-sizing resources, minimizing waste, and aligning capacity with actual usage needs. Cost optimization recommendations -
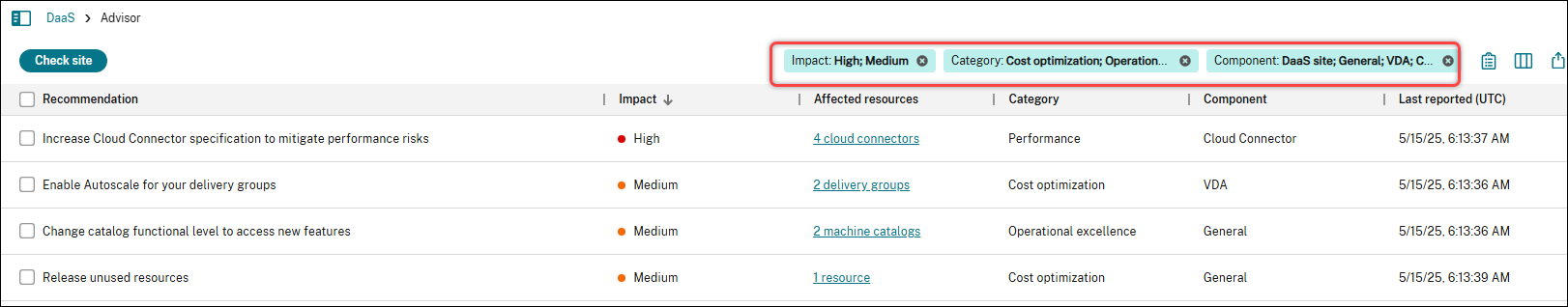
Select one or more checkboxes to apply the filter. The list updates automatically to display only the recommendations that match your selections.
-
Use multiple filters together to narrow down the list.
Review and act on recommendations
Use the recommendations list to understand configuration issues or improvement opportunities in your deployment. You can view details, take corrective actions, or dismiss recommendations based on their relevance.
To review and act on recommendations, follow these steps:
-
Select a recommendation to view its details in the lower pane.
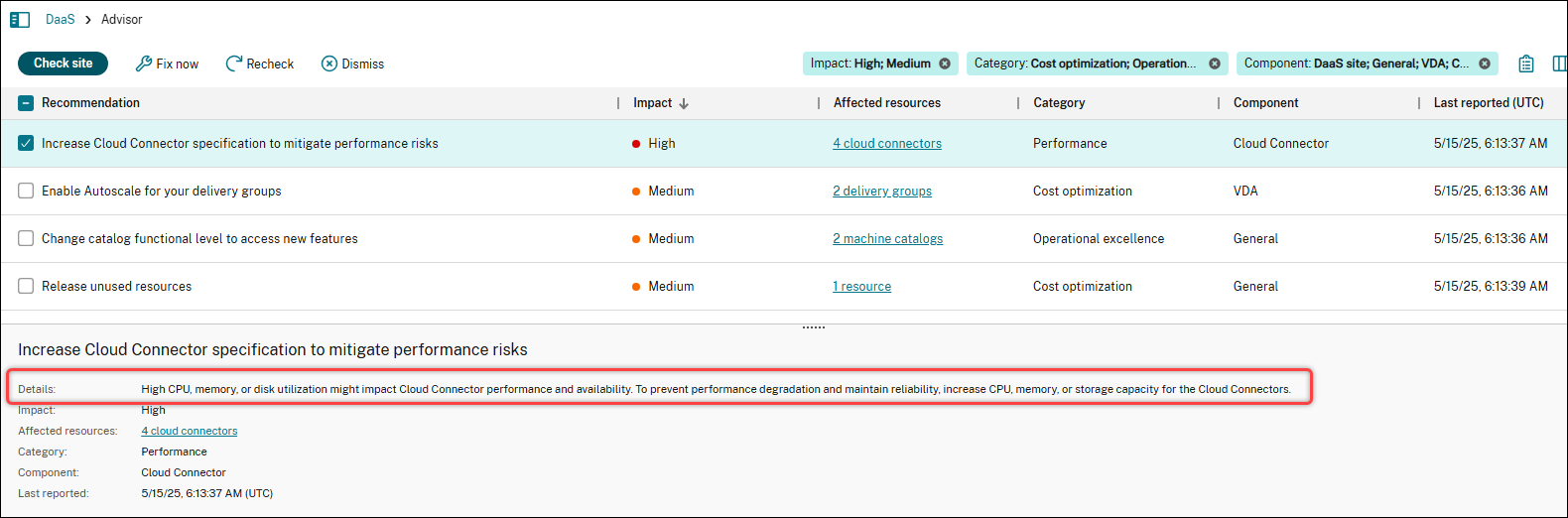
-
To implement the recommendation:
- Click Fix now.
-
Follow the recommended steps to make the necessary updates.
Sometimes, you’re directed to supporting documentation when automated configuration isn’t supported or feasible. We want to make sure that Advisor is designed to provide automated actions directly within the UI wherever possible, minimizing the need for manual setup.
- After making updates, click Recheck to update the status of the affected resources.
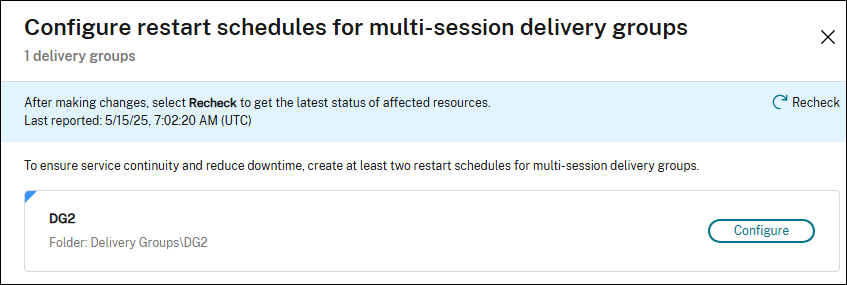
Note:
The UI and steps vary depending on the recommendation. The screenshot shown is for illustration purposes only.
-
If a recommendation isn’t relevant to your deployment or doesn’t require action, click Dismiss to remove it from the current list and future check results.
Tip:
To restore dismissed recommendations, click Check site, then click Manage at the bottom of the page to view and restore them.
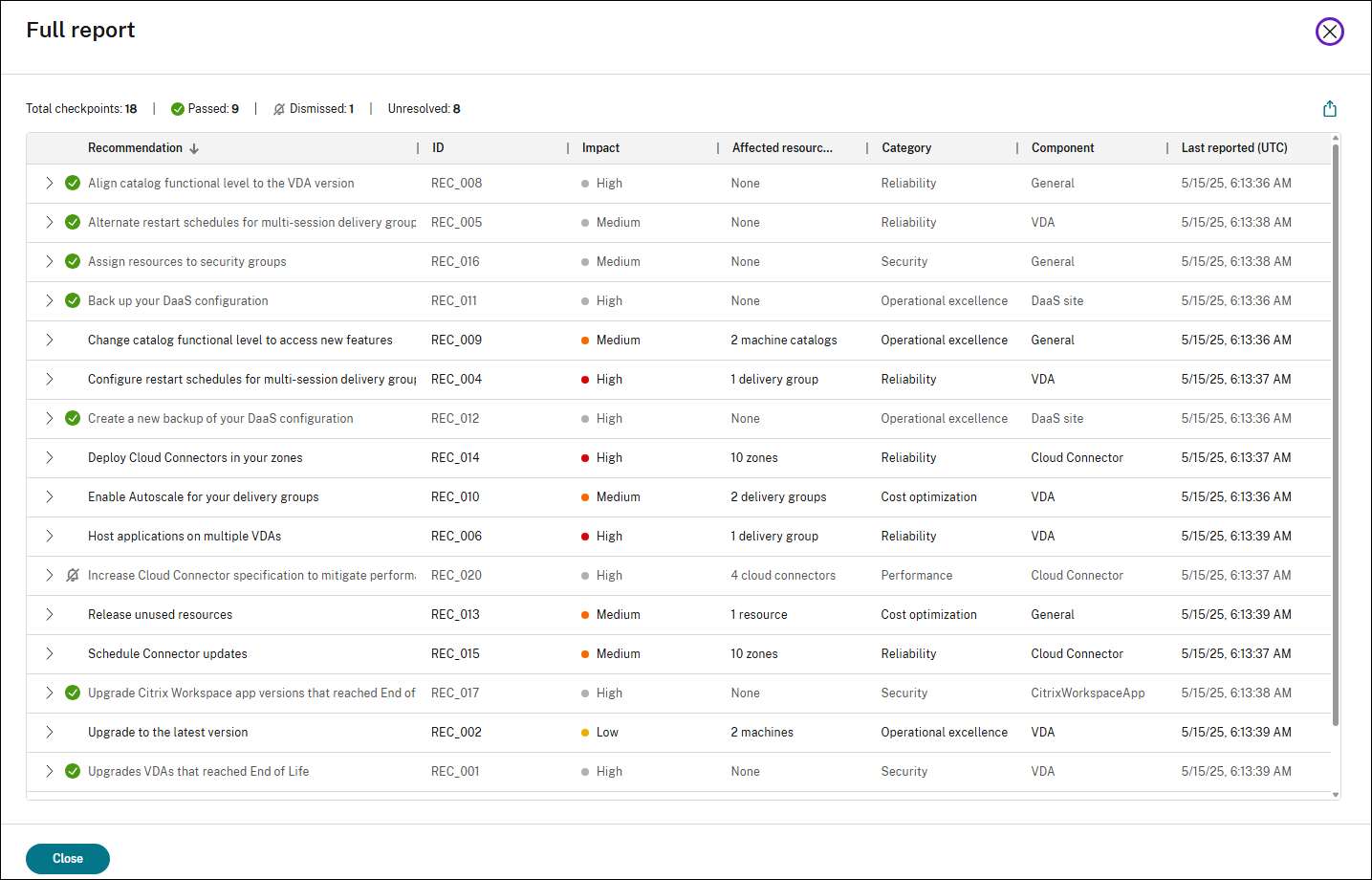
View the full site check report
The full report provides a summary of all Advisor recommendations from the latest site check. It includes passed, dismissed, and unresolved checkpoints, helping you assess the overall health and optimization opportunities in your DaaS site.
To view the full report, click the View full report icon at the top right of the recommendation list.
References
This section lists all Citrix Advisor recommendations by category to help you understand their purpose and impact.
Security recommendations
| Recommendation | ID | Impact | Component | Description |
|---|---|---|---|---|
| Upgrade VDAs that reached End of Life | REC_001 | High | VDA | Some machines are using VDA versions that have reached End of Life and are no longer supported by Citrix. Upgrade affected machines to the latest LTSR or CR VDA version. |
| Assign resources to security groups | REC_016 | Medium | General | Some resources are assigned to individual users. It is a Citrix best practice only to assign user access through security groups to streamline management and enhance security. Reconfigure the user assignment for delivery and application groups to include only security groups. |
| Upgrade Citrix Workspace app versions that reached End of Life | REC_017 | High | Workspace app | Some endpoint devices use a Citrix Workspace app version that reached End of Life. Upgrade devices to the latest Workspace app version to reduce supportability and security risks. For simplified version management and automatic update control, use Global App Configuration Service. Additionally, consider using endpoint analysis solutions to enforce a minimum Workspace app version to access the store. |
| Implement device posture policies | REC_021 | Medium | Secure Private Access | The current Secure Private Access configuration lacks device posture policies, allowing unrestricted access to internal applications from any device. To mitigate this risk and enhance security, implement device posture policies that classify devices as: Compliant, Non-compliant, and Denied access. |
| Implement adaptive access policies | REC_022 | Medium | Secure Private Access | The current Secure Private Access configuration lacks adaptive access policies, allowing potentially insecure access to applications. To enhance security, implement adaptive access policies that dynamically control access to enterprise web, SaaS, TCP, and UDP apps based on context. For granular controls, enable restricted access to enterprise web and SaaS apps by adding the security restrictions: Clipboard, Screen capture, Printing, Key logging protection, Downloads, Uploads, Watermark, and Open in remote browser. |
| Upgrade operating systems that reached End of Life | REC_024 | High | VDA | Some machines are running operating systems (OS) that have reached End of Life. This poses significant security risks and may result in loss of support from both Citrix and the OS vendor. To maintain a secure and stable environment, ensure all your VDAs run a supported operating system. |
| Upgrade hypervisor versions that reached End of Life | REC_025 | Security | Hypervisor | Details: Some hypervisors are running versions that have reached End of Life. This poses a risk to environment stability and limits Citrix’s ability to provide full support. To maintain a secure, supportable environment, upgrade to a vendor-supported hypervisor version. Regularly review vendor release notes and compatibility documentation to stay aligned with leading practices and platform requirements. |
| Use HTTPS for host connections | REC_039 | Medium | General | Some host connections are currently configured with HTTP instead of HTTPS. To ensure secure communication with your hypervisor, update these connections to use HTTPS. This requires enabling HTTPS on your hypervisor and ensuring valid TLS certificates are in place. |
Reliability recommendations
| Recommendation | ID | Impact | Component | Description |
|---|---|---|---|---|
| Configure restart schedules for multi-session delivery groups | REC_004 | High | VDA | Some multi-session delivery groups do not have restart schedules configured. Scheduled restarts help maintain optimal performance, stability, and resource availability across multi-session OS VDAs. To ensure service continuity and reduce downtime, create at least two restart schedules. Alternate restart schedules with tag restrictions by tagging VDAs into groups, such as ‘Even’ and ‘Odd.’ |
| Alternate restart schedules for multi-session delivery groups | REC_005 | Medium | VDA | Some multi-session delivery groups only have one restart schedule configured. To ensure service continuity and reduce downtime, create at least two restart schedules. Alternate restart schedules with tag restrictions by tagging VDAs into groups, such as ‘Even’ and ‘Odd.’ |
| Host applications on multiple VDAs | REC_006 | High | VDA | Some published applications are hosted on only a single VDA, which can impact service continuity and lead to downtime risks. Ensure that each application is hosted on multiple VDAs in a delivery group to help maintain availability and reliability. |
| Upgrade VDAs to match the catalog functional level | REC_008 | High | VDA | Some machines use an earlier VDA version not supported by the minimum catalog functional level, which can prevent them from registering. To avoid registration issues, upgrade earlier VDA versions to match the catalog functional level. |
| Deploy Cloud Connectors in your zones | REC_014 | High | Cloud Connector | Fewer than two Cloud Connectors are deployed in some of your zones (resource locations). Deploy at least two Cloud Connectors per resource location to maintain availability and resiliency during Connector updates. Resource locations should follow the N + 1 model, where N is the baseline requirement based on deployment size and the additional 1 provides redundancy. |
| Schedule Connector updates | REC_015 | Medium | Cloud Connector | Some zones (resource locations) don’t have a scheduled start time for Connector updates. To ensure that updates only occur during planned maintenance windows and reduce service disruption, schedule Connector updates for a preferred time and day of the week. |
| Place Cloud Connectors in the same domain | REC_028 | Medium | Cloud Connector | Some zones (resource locations) contain Cloud Connectors joined to different domains. This setup can lead to delayed or failed VDA registrations, especially when in Local Host Cache (LHC) mode. To improve reliability and reduce risk, ensure all Cloud Connectors within a given zone belong to the same domain. |
| Enable communication between Cloud Connectors for reliable LHC performance | REC_029 | High | Cloud Connector | Some zones (resource locations) have multiple elected Local Host Cache (LHC) brokers. This can cause VDA registrations to be divided among the Cloud Connectors in LHC mode, leading to intermittent launch failures. To prevent this, ensure all Cloud Connectors in each affected zone can communicate with one another at http:// |
| Check resiliency configurations | REC_030 | Medium | General | Your deployment resiliency configurations have not been verified recently. Maintaining proper resiliency configurations is critical for ensuring uninterrupted access to apps and desktops, especially during unexpected service disruptions. Check your resiliency configurations regularly to ensure your deployment is properly set up to handle potential disruptions and safeguard user productivity. |
| Enable advanced health check for StoreFront stores | REC_036 | Medium | StoreFront | One or more stores on some StoreFront servers do not have advanced health check enabled. StoreFront uses the additional information from the advanced health check results to ensure launch requests are sent to the appropriate resource location (zone) in Local Host Cache (LHC) mode. Without advanced health check, launches may fail when in LHC mode. To improve the resiliency of your Citrix environment, enable advanced health check for all stores on the StoreFront servers. |
| Add all Cloud Connectors as STA servers on StoreFront and NetScaler Gateway | REC_037 | Medium | Cloud Connector | Some Cloud Connectors are not configured as Secure Ticket Authority (STA) servers, which is preventing them from receiving STA requests from StoreFront. To avoid launch failures in Local Host Cache mode, ensure all Cloud Connectors are added as STA servers on both StoreFront and NetScaler Gateway. |
Performance recommendations
| Recommendation | ID | Impact | Component | Description |
|---|---|---|---|---|
| Optimize Cloud Connectors for LHC mode | REC_019 | High | Cloud Connector | Some Cloud Connectors have less than four CPU cores per socket, which can impact users’ ability to enumerate and launch available resources while in LHC mode. To maximize resource availability for LHC and prevent performance bottlenecks, configure Cloud Connector machines to have at least four cores per socket. |
| Enhance Cloud Connector hardware | REC_020 | High | Cloud Connector | High CPU, memory, or disk usage might impact Cloud Connector performance and availability. To prevent performance degradation and maintain reliability, increase CPU, memory, or storage for the Cloud Connectors. |
| Rightsize high resource-consuming machines | REC_023 | Medium | VDA | Some machines show signs of performance strain, such as high CPU or memory utilization, or a high session count. This indicates machines are undersized to handle the workloads they support, which can lead to a poor user experience and reduced performance. Consider changing the machine size to increase the allocated resources for the machine or relocating power users to a delivery group that has high-performance machines. |
| Reduce the number of host connections in your zones | REC_026 | High | General | The number of host connections in some zones (resource locations) exceeds the recommended limit, which might result in performance degradation. Reduce the number of host connections in the zones to no more than the recommended limit. |
| Reduce the number of VDAs in your zones | REC_027 | High | VDA | The number of VDAs in some zones (resource location) exceeds the recommended limit, increasing the risk of failed VDA registrations and degraded session brokering, especially when in Local Host Cache (LHC) mode. To mitigate these risks, redistribute VDAs by moving some to other zones. Ensure your method for configuring VDA registration is updated accordingly. |
| Evaluate resource allocation for PVS servers | REC_031 | Medium | Citrix Provisioning | Some Citrix Provisioning (PVS) servers show signs of performance strain, such as high CPU or memory utilization. Insufficient server resource allocation may result in poor performance and extended boot times. Consider increasing the CPU and memory allocation for these PVS servers as needed. |
| Increase resource allocation for PVS servers | REC_032 | High | Citrix Provisioning | Some Citrix Provisioning (PVS) servers show signs of performance strain, such as critical CPU or memory utilization. Insufficient server resource allocation may result in poor performance and extended boot times. Consider increasing the CPU and memory allocation for these PVS servers as needed. |
| Evaluate write cache disk size for PVS target devices | REC_033 | Medium | VDA | The write cache disk usage on some Citrix Provisioning (PVS) target devices is nearing the threshold. To avoid performance issues and user session failures, evaluate the current write cache disk size and increase it as needed. |
| Optimize GPO configuration for VDAs | REC_035 | Medium | VDA | Some user sessions experienced prolonged GPO processing during logon, impacting performance. To increase control over environment settings, block Group Policy inheritance for your VDA organizational units and apply only relevant policies and security configurations. Additionally, consider leveraging Citrix Workspace Environment Management to process settings asynchronously for faster session logons. |
Operational excellence recommendations
| Recommendation | ID | Impact | Component | Description |
|---|---|---|---|---|
| Upgrade VDAs to the latest version | REC_002 | Low | VDA | Some machines are using older VDA versions. Upgrade to the latest LTSR or CR VDA version to access new features, improvements, and security enhancements. |
| Use Citrix Provisioning technology | REC_003 | Medium | Citrix Provisioning | All machines in the site are manually provisioned and do not use Citrix Provisioning technologies such as Machine Creation Services™ (MCS) or Provisioning Services (PVS). Use MCS or PVS to ensure VDA consistency, minimize manual tasks, and streamline environment scaling operations. |
| Low functional level | REC_009 | Low | VDA | Some machine catalogs have a lower functional level than the detected VDA version, limiting access to new features on later VDA versions. To access these features, change the functional level to the latest version supported by all machines in the catalog. |
| Back up your site configuration | REC_011 | High | General | You don’t have a backup of your site configuration. Create on-demand or scheduled backups to ensure you have a ready-to-use copy of your Citrix configurations for quick recovery. |
| Create a new backup of your site configuration | REC_012 | High | General | Your last site configuration backup was over three months ago. Regularly create on-demand or scheduled backups to keep an up-to-date copy of your Citrix configurations ready for quick recovery. |
| Simplify catalog configuration with a machine profile | REC_038 | Low | Provisioning | Some machine catalogs would benefit from using a machine profile. With a machine profile, Machine Creation Services (MCS) captures hardware properties and hypervisor-specific features from the profile and efficiently provisions new virtual machines (VMs) in the catalog with the same configuration. |
Cost optimization recommendations
| Recommendation | ID | Impact | Component | Description |
|---|---|---|---|---|
| Enable Autoscale for your delivery groups | REC_010 | Medium | VDA | Some eligible delivery groups aren’t using Autoscale. Enable Autoscale for consistent machine power management, maintaining availability while effectively balancing costs and user experience. |
| Release unused resources | REC_013 | Medium | General | Some dedicated workloads, such as machines or applications, have not been used for over 30 days. To reduce unnecessary spending and optimize costs, release unused machines back to the available pool and manage unused applications. |