System and Connectivity Requirements
Citrix Cloud™ provides administrative functions (through a web browser) and operational requests (from other installed components) that connect to resources within your deployment. This article describes the system requirements, required contactable Internet addresses, and considerations for establishing connectivity between your resources and Citrix Cloud.
System requirements
Citrix Cloud requires the following minimum configuration:
- An Active Directory domain
- Two physical or virtual machines, joined to your domain, for the Citrix Cloud Connector. For more information, see Citrix Cloud Connector Technical Details.
- Physical or virtual machines, joined to your domain, for hosting workloads and other components such as StoreFront. For more information about system requirements for specific services, refer to the Citrix® documentation for each service.
For information about scale and size requirements, see Scale and size considerations for Cloud Connectors.
Supported web browsers
- Latest version of Google Chrome
- Latest version of Mozilla Firefox
- Latest version of Microsoft Edge
- Latest version of Apple Safari
Transport Layer Security requirements
Citrix Cloud supports Transport Layer Security (TLS) 1.2 for TCP-based connections between components. Citrix Cloud doesn’t allow communication over TLS 1.0 or TLS 1.1.
To access Citrix Cloud, you must use a browser that supports TLS 1.2 and have accepted cipher suites configured. For more information, see Encryption and key management.
Citrix Cloud management console
The Citrix Cloud management console is a web-based console that you can access after signing in at https://citrix.cloud.com. The web pages that make up the console might require other resources on the Internet, either when signing in or at a later point when carrying out specific operations.
Proxy configuration
If you’re connecting through a proxy server, the management console operates using the same configuration applied to your web browser. The console operates within the user context, so any configuration of proxy servers that require user authentication should work as expected.
Firewall configuration
For the management console to operate, you must have port 443 open for outbound connections. You can test general connectivity by navigating within the console. For more information about required ports, see Inbound and outbound ports configuration.
Console notifications
The management console uses Pendo to display critical alerts, notifications about new features, and in-product guidance for some features and services. To ensure you can view Pendo content within the management console, Citrix recommends that the address https://citrix-cloud-content.customer.pendo.io/ is contactable.
Services that display Pendo content include:
- Citrix Analytics
- Citrix DaaS™
- Citrix Workspace™
Pendo is a third-party sub-processor that Citrix uses to provide cloud and support services to Citrix customers. For a complete list of these sub-processors, see Sub-Processors for Citrix Cloud & Support Services and Citrix Affiliates.
Session time-outs
After an administrator signs in to Citrix Cloud, the management console session times out after 72 hours have elapsed. This time-out occurs regardless of console activity.
Configurable inactivity timeout for console
As a full-access administrator, you can configure the duration of inactivity on the Citrix Cloud console before administrators are automatically signed out. Once configured, the specified timeout period will be applied to all administrators of the Citrix Cloud account.

When the feature is enabled, administrators will be logged out after the configured period of inactivity, and the session timeout will reset upon each subsequent login.
When the feature is disabled, there is no inactivity timer, and administrators will be logged out only when the 72-hour session limit is reached.
Note:
- By default this feature is disabled.
- The configurable inactivity timeout is 10 minutes to 12 hours.
- The default inactivity timeout is 60 minutes.
License Server connectivity to Citrix Cloud
If you are registering your on-premises Citrix License Server with Citrix Cloud to monitor usage of on-premises deployments, ensure that the following addresses are contactable:
-
https://trust.citrixnetworkapi.net(for retrieving a code) -
https://trust.citrixworkspacesapi.net/(for confirming the license server is registered) -
https://cis.citrix.com(for data upload) https://core.citrixworkspacesapi.netocsp.digicert.com port 80crl3.digicert.com port 80crl4.digicert.com port 80ocsp.entrust.net port 80crl.entrust.net port 80
If you are using a proxy server with Citrix License Server, ensure that the proxy server is configured as described in Configure a proxy server in the Licensing product documentation.
Citrix Cloud Connector™
The Citrix Cloud Connector is a software package that deploys a set of services that run on Microsoft Windows servers. The machine hosting the Cloud Connector resides within the network where the resources that you use with Citrix Cloud reside. The Cloud Connector connects to Citrix Cloud, allowing it to operate and manage your resources as needed.
For requirements for installing the Cloud Connector, see System requirements. To operate, the Cloud Connector requires outbound connectivity on port 443. After installation, the Cloud Connector might have additional access requirements depending on the Citrix Cloud service with which it is being used.
The machine hosting the Cloud Connector must have stable network connectivity with Citrix Cloud. Networking components must support HTTPS and long-lived secure web sockets. If a timeout is configured in the networking components, it must be greater than 2 minutes.
For help with troubleshooting connectivity between the Cloud Connector and Citrix Cloud, use the Cloud Connector Advanced Connectivity Checks
Cloud Connector common service connectivity requirements
Connecting to the Internet from your data centers requires opening port 443 to outbound connections. However, to operate within environments containing an Internet proxy server or firewall restrictions, further configuration might be needed. For more information, see Cloud Connector Proxy and Firewall Configuration.
The addresses for each service in this article must be contactable to properly operate and consume the service. The following list includes the addresses that are common to most Citrix Cloud services:
-
https://*.citrixworkspacesapi.net(provides access to Citrix Cloud APIs that the services use) -
https://*.cloud.com(provides access to the Citrix Cloud sign-in interface) -
https://*.blob.core.windows.net(provides access to Azure Blob Storage, which stores updates for Citrix Cloud Connector) -
https://*.servicebus.windows.net(provides access to Azure Service Bus, which is used for logging and the Active Directory agent)
These addresses are provided only as domain names because Citrix Cloud services are dynamic and their IP addresses are subject to routine changes.
As a best practice, use Group Policy to configure and manage these addresses. Also, configure only the addresses that are applicable to the services that you and your end-users are consuming.
If you are using Citrix Cloud with Citrix License Server to register your on-premises products, see License Server connectivity to Citrix Cloud in this article for additional required contactable addresses.
Allowed FQDNs for Cloud Connector
To help you ensure that all the required fully qualified domain names (FQDNs) are allowed through your firewall, Citrix provides the following resources:
When configuring your firewall, consult both of these resources to verify that the FQDNs that your service deployment requires are allowed.
Local Host Cache (High Availability Service)
When using Local Host Cache (LHC) in Connectors, ensure that the Connectors can reach the election endpoint of every other connector in the resource location. The election endpoint is on port 80 and can be accessed through the following URL: http://<FQDN_OR_IP_OF_PEER_CONNECTOR>/Citrix/CdsController/ISecondaryBrokerElection.
If Connectors are unable to communicate at this address, multiple brokers are elected during an LHC event, which can result in intermittent virtual app and desktop launch failures. For more information, see Resource Locations with Multiple Cloud Connectors.
Adaptive Authentication
When using the Cloud Connector for connectivity to an Adaptive Authentication service, you must allow your Citrix Cloud Connector to access the domain or URL you’ve reserved for the Adaptive Authentication instance. For example, allow https://aauth.xyz.com. For more information, see Adaptive Authentication.
Allowlist.json
Where possible, it is recommended to perform whitelisting using the ‘wildcard’ addresses provided in the Cloud Connector common service connectivity requirements. However, where this is not possible refer to the allowlist.json file located at https://fqdnallowlistsa.blob.core.windows.net/fqdnallowlist-commercial/allowlist.json, which lists the fully qualified domain names (FQDNs) that the Cloud Connector accesses. This list is grouped by product. Where FQDNs are required by multiple products that they are contained in the “Connector Common” section of the document.
The allowlist.json file is subject to change. If you are using the allowlist.json it is important to regularly check the file for changes and ensure firewalls or proxies are kept up to date. The file includes a changelog for each group of FQDNs. Notifications of important changes to the allowlist.json will be notified through the Citrix Cloud Console and, if necessary, via direct email to admins.
Some of these FQDNs are specific to a customer and include templated sections in angular brackets. These templated sections must be replaced with the actual values before use. For example, for <CUSTOMER_ID>.xendesktop.net, you replace <CUSTOMER_ID> with the actual customer ID for your Citrix Cloud account. You can find the customer ID in the following console locations:
-
In the top-right corner of the screen, beneath the customer name for your Citrix Cloud account.
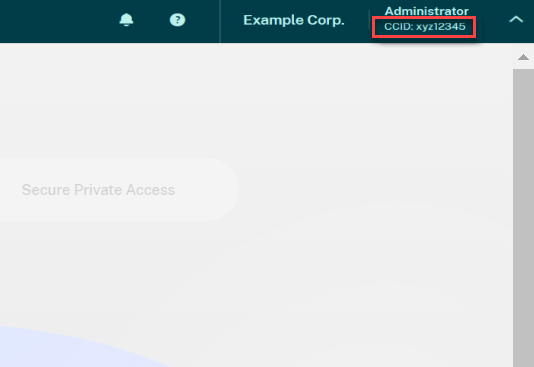
-
On the Account Settings page, under Citrix Cloud Customer ID (CCID).
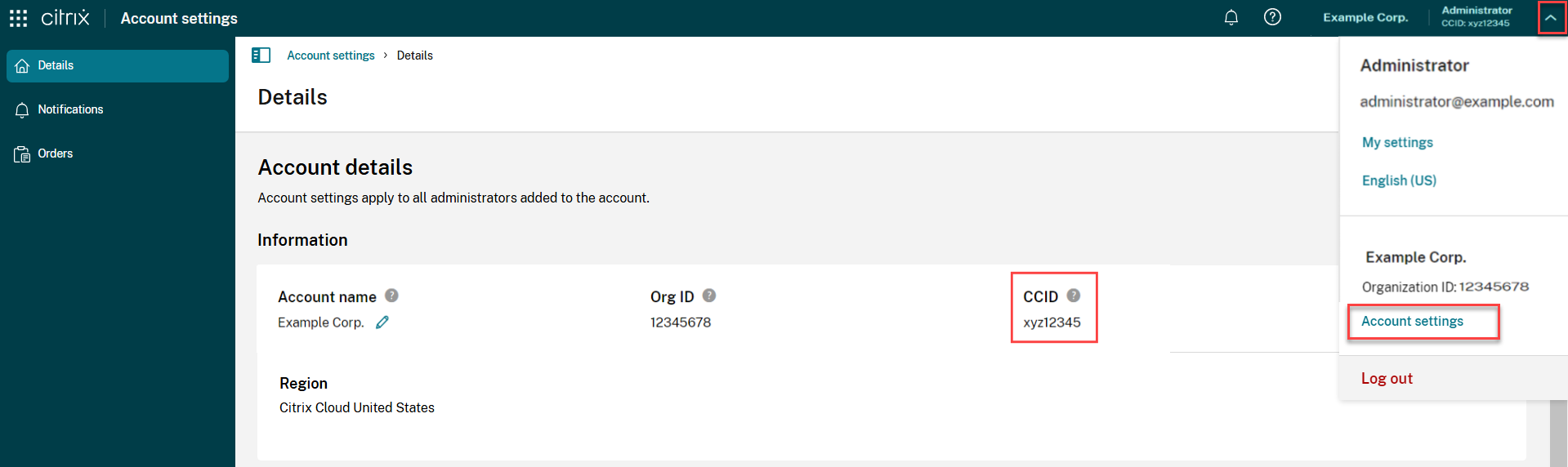
-
On the Secure Clients tab Identity and Access Management > API Access > Secure Clients.
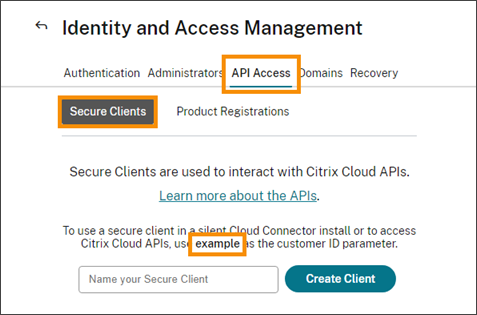
Gateway Service Points of Presence
Some of the FQDNs included in the allowlist.json file are also included in Citrix Gateway Service – Points of Presence (PoPs). However, Citrix Gateway Service – Points of Presence (PoPs) also includes FQDNs that clients access, such as the following:
- global-s.g.nssvc.net
- azure-s.g.nssvc.net
Certificate validation
Cloud Connector binaries and endpoints that the Cloud Connector contacts are protected by X.509 certificates that are verified when the software is installed. To validate these certificates, each Cloud Connector machine must meet certain requirements. For a full list of these requirements, see Certificate validation requirements.
SSL Decryption
Enabling SSL decryption on certain proxies might prevent the Cloud Connector from connecting successfully to Citrix Cloud. For more information about resolving this issue, see CTX221535.
Citrix Connector™ Appliance for Cloud Services
The Connector Appliance is an appliance that you can deploy in your hypervisor. The hypervisor hosting the Connector Appliance resides within the network where the resources that you use with Citrix Cloud reside. The Connector Appliance connects to Citrix Cloud, allowing it to operate and manage your resources as needed.
For requirements for installing the Connector Appliance, see System requirements.
To operate, the Connector Appliance requires outbound connectivity on port 443. However, to operate within environments containing an Internet proxy server or firewall restrictions, further configuration might be needed.
To properly operate and consume the Citrix Cloud services, the following addresses must be contactable:
https://*.cloud.comhttps://*.citrixworkspacesapi.nethttps://*.citrixnetworkapi.net-
https://*.*.nssvc.netCustomers who can’t enable all sub-domains can use the following addresses instead
https://*.g.nssvc.nethttps://*.c.nssvc.net
https://*.servicebus.windows.nethttps://ctxccopspacrconnappprod.azurecr.iohttps://ctxccopspacrconnappprod.eastus.data.azurecr.io
Network requirements
Ensure that your Connector Appliance environment has the following configuration:
- Either the network allows the Connector Appliance to use DHCP to get DNS and NTP servers, an IP address, a host name, and a domain name or you can manually set the network settings in the Connector Appliance console.
- The network is not configured to use the link-local IP ranges 169.254.0.1/24, 169.254.64.0/18 or 169.254.192.0/18, which are used internally by the Connector Appliance.
- Either the hypervisor clock is set to Coordinated Universal Time (UTC) and is synchronized with a time server or DHCP provides NTP server information to the Connector Appliance.
- If you use a proxy with Connector Appliance, the proxy must be unauthenticated or use basic authentication.
Citrix Analytics service connectivity
- For in-product messages including new features and critical communications:
https://citrix-cloud-content.customer.pendo.io/ - Additional requirements: Prerequisites
For more information about onboarding data sources to the service, see Supported data sources.
NetScaler® Console service connectivity
For complete Internet connectivity requirements, see Supported ports in the NetScaler product documentation.
Citrix DaaS connectivity
Cloud Connectors connectivity to DaaS
In addition to the Cloud Connector common service connectivity requirements, when used with DaaS, Cloud Connectors require connectivity to the following:
-
https://[customerid].xendesktop.net, where[customerid]is the customer ID parameter displayed on the Secure Clients tab (Identity and Access Management > API Access > Secure Clients) of the Citrix Cloud management console. - Customers using Quick Deploy to install Citrix DaaS need to make these additional addresses contactable:
https://*.apps.cloud.com- The
AzureCloudservice tag
-
https://*.*.nssvc.net- Customers who can’t enable all subdomains can use the following addresses instead:
https://*.g.nssvc.nethttps://*.c.nssvc.net
- Customers who can’t enable all subdomains can use the following addresses instead:
For an overview of how the Cloud Connector communicates with the service, refer to the Citrix DaaS diagram on the Citrix Tech Zone website.
Connectivity to DaaS Administration console
To administer DaaS, in addition to the Citrix Cloud Management Console you must be able to connect to the following:
-
https://*.citrixworkspacesapi.net(Not required for Rendezvous protocol) -
https://*.citrixnetworkapi.net(Not required for Rendezvous protocol) -
https://*.cloud.com(Not required for Rendezvous protocol) -
https://[customerid].xendesktop.net, where[customerid]is the customer ID parameter displayed on the Secure Clients tab (Identity and Access Management > API Access > Secure Clients) of the Citrix Cloud management console. -
https://*.*.nssvc.net(Not required for Citrix DaaS Standard for Azure)- Customers who can’t enable all sub-domains can use the following addresses instead:
https://*.g.nssvc.nethttps://*.c.nssvc.net
- Customers who can’t enable all sub-domains can use the following addresses instead:
- For in-product messages including new features and critical communications:
https://citrix-cloud-content.customer.pendo.io/
Citrix DaaS Remote PowerShell SDK
To use the Citrix DaaS Remote PowerShell SDK, whitelist the following URLs:
https://*.cloud.comhttps://*.citrixworkspacesapi.net/[customerid]https://[customerid].xendesktop.net:443
VDAs connectivity when using Rendezvous protocol
When using the Citrix Gateway Service, the Rendezvous protocol allows VDAs to bypass the Citrix Cloud Connectors to connect directly and securely with the Citrix Cloud control plane.
Regardless of the protocol version you’re using, VDAs must be able to contact the addresses for the administration console listed above, unless otherwise noted. For a complete list of the requirements for the Rendezvous protocol, refer to the following sections of the Citrix DaaS product documentation:
Local Host Cache requirement
If your firewall performs packet inspection and you want to use the Local Host Cache feature, ensure that your firewall accepts XML and SOAP traffic. This feature requires the ability to download MDF files, which occurs when the Cloud Connector synchronizes configuration data with Citrix Cloud. These files are delivered to the Cloud Connector through XML and SOAP traffic. If the firewall blocks this traffic, the synchronization between the Cloud Connector and Citrix Cloud fails. If an outage occurs, users can’t continue working because the configuration data residing on the Cloud Connector is out-of-date.
For more information about this feature, see Local Host Cache in the Citrix DaaS product documentation.
VDA upgrade requirement
Using the Full Configuration interface of Citrix DaaS, you can upgrade VDAs on a per-catalog or a per-machine basis. You can upgrade them immediately or at a scheduled time. For more information about the VDA upgrade feature, see Upgrade VDAs using the Full Configuration interface.
When using the feature, make sure that you meet the following connectivity requirements:
-
The following Azure CDN URLs have been added to the allow list. The feature downloads the VDA installers from the Azure CDN endpoints.
- Production - United States (US):
https://prod-us-vus-storage-endpoint.azureedge.net/* - Production - European Union (EU):
https://prod-eu-vus-storage-endpoint.azureedge.net/* - Production - Asia Pacific South (APS):
https://prod-aps-vus-storage-endpoint.azureedge.net/* - Production - Japan (JP):
https://prod-jp-vus-storage-endpoint.azureedge.net/*
- Production - United States (US):
-
The feature verifies that the VDA installer is signed by a valid certificate. Make sure that the following URLs have been added to the allow list for certificate validity and revocation check:
http://crl3.digicert.com/*http://crl4.digicert.com/*http://ocsp.digicert.com/*http://cacerts.digicert.com/*
-
The feature requires VDA Upgrade Agent to work. The VDA Upgrade Agent running on the VDA communicates with Citrix DaaS. Make sure that the following URLs have been added to the allow list:
-
https://[customerId].xendesktop.net/citrix/VdaUpdateService/*, where[customerid]is the customer ID parameter displayed on the Secure Clients tab (Identity and Access Management > API Access > Secure Clients) of the Citrix Cloud management console. http://xendesktop.net/citrix/VdaUpdateService/*
-
Endpoint Management service connectivity
Citrix resource location / Cloud Connector:
- Cloud Connector common service connectivity requirements
- Additional requirements: /en-us/citrix-endpoint-management/endpoint-management.html
Administration console:
https://*.citrix.comhttps://*.citrixworkspacesapi.nethttps://*.cloud.comhttps://*.blob.core.windows.net- Additional requirements: /en-us/citrix-endpoint-management/endpoint-management.html
Citrix Gateway service connectivity
Cloud Connectors connectivity to Citrix Gateway Service
When using Citrix Gateway Service via Cloud connectors (i.e. without Rendezvous v2), in addition to Cloud Connector common service connectivity requirements, Cloud Connectors need access to:
https://*.*.nssvc.net
Customers who can’t enable all subdomains can use the following addresses instead:
https://*.g.nssvc.nethttps://*.c.nssvc.net
Important:
SSL interception cannot be performed on Citrix Gateway addresses. Enabling SSL interception on certain proxies might prevent the Cloud Connector from connecting successfully to Citrix Cloud.
Client connectivity to Citrix Gateway Service
To use Citrix Gateway Service, client devices need access to:
https://*.*.nssvc.net
Customers who can’t enable all subdomains can use the following addresses instead:
https://*.g.nssvc.nethttps://*.c.nssvc.net
SD-WAN Orchestrator service connectivity
For complete Internet connectivity requirements, see Prerequisites for Citrix SD-WAN Orchestrator service usage.
Remote Browser Isolation (formerly Secure Browser) service
Cloud Connector connectivity to Remote Browser Isolation service
Cloud Connectors do not need any additional connectivity beyond Cloud Connector common service connectivity requirements.
Connectivity to Administration console
https://*.cloud.comhttps://*.citrixworkspacesapi.nethttps://browser-release-a.azureedge.nethttps://browser-release-b.azureedge.net
Client connectivity to Citrix Secure Private Access™
https://*.netscalergateway.net-
https://*.*.nssvc.net- Customers who can’t enable all subdomains can use the following addresses instead:
https://*.g.nssvc.nethttps://*.c.nssvc.net
- Customers who can’t enable all subdomains can use the following addresses instead:
Client connectivity to Global App Configuration service
https://discovery.cem.cloud.us
For more information about this service, see Customize Workspace app settings.
End user connectivity to Citrix Workspace
This section lists URLs that clients must be able to reach when accessing Citrix Workspace using Citrix Workspace app or a web browser.
Store URL
Users access the store through either a cloud URL, e.g. https://<customername>.cloud.com, or a custom URL. For more information, see Configure access to workspaces.
Authentication
Citrix Cloud:
https://accounts.cloud.comhttps://accounts-dsauthweb.cloud.com-
https://accounts-webassets.cloud.com- for graphical interface assets -
https://login.cloud.com- only required if you are using Active Directory or Active Directory + Token as your identity provider
Citrix Cloud Japan:
https://accounts.citrixcloud.jphttps://accounts-dsauthweb.citrixcloud.jp-
https://accounts-webassets.citrixcloud.jp- for graphical interface assets -
https://login.citrixcloud.jp- only required if you are using Active Directory or Active Directory + Token as your identity provider
Citrix Cloud Government:
https://accounts.cloud.ushttps://accounts-dsauthweb.cloud.us-
https://login.cloud.us- only required if you are using Active Directory or Active Directory + Token as your identity provider
https://accounts-webassets.cloud.us is not required for Citrix Cloud Government. https://accounts.cloud.us is used for graphical interface assets.
If you are using a third party identity provider, contact the vendor for required URLs.
Workspace graphical interface assets
https://ctx-ws-assets.cloud.com
For Citrix Cloud Government, this may change in the future to https://ctx-ws-assets.cloud.us.
Personalization, notifications, and feature rollout
When using Citrix Workspace app, but not a web browser, the following URLs are required according to your organization’s region.
US:
https://customer-interface-personalization.us.wsp.cloud.comhttps://user-personalization.us.wsp.cloud.comhttps://admin-notification.us.wsp.cloud.comhttps://feature-rollout.us.wsp.cloud.com
EU:
https://customer-interface-personalization.eu.wsp.cloud.comhttps://user-personalization.eu.wsp.cloud.comhttps://admin-notification.eu.wsp.cloud.comhttps://feature-rollout.eu.wsp.cloud.com
Asia Pacific South:
https://customer-interface-personalization.ap-s.wsp.cloud.comhttps://user-personalization.ap-s.wsp.cloud.comhttps://admin-notification.ap-s.wsp.cloud.comhttps://feature-rollout.ap-s.wsp.cloud.com
Citrix Cloud Japan:
https://customer-interface-personalization.jp.wsp.citrixcloud.jphttps://user-personalization.jp.wsp.citrixcloud.jphttps://admin-notification.jp.wsp.citrixcloud.jphttps://feature-rollout.jp.wsp.citrixcloud.jp
Citrix Cloud Government:
https://customer-interface-personalization.us.wsp.cloud.ushttps://user-personalization.us.wsp.cloud.ushttps://admin-notification.us.wsp.cloud.ushttps://feature-rollout.us.wsp.cloud.us
Branding images
- US:
https://cips-iws-prod-eus2-cip-cdn.azureedge.net - EU:
https://cips-iws-prod-weu-cip-cdn.azureedge.net - AP-S
https://cips-iws-prod-aue-cip-cdn.azureedge.net - Citrix Cloud Japan
https://cips-wspjp-prod-jpe-cip-cdn.azureedge.net - Citrix Cloud Government
https://cips-wspgov-prod-usgv-cip-cdn.azureedge.us
Profile pictures
If users upload profile pictures, access is required to the following URLs:
- US:
https://wups-us-iws-cloud.azureedge.net - EU:
https://wups-eu-iws-cloud.azureedge.net - AP-S:
https://wups-ap-s-iws-cloud.azureedge.net - Citrix Cloud Japan:
https://wups-wspjp-jp-production.azureedge.net
Application Icons
Citrix Cloud:
https://wscs-cdn.wsp.cloud.com/icons
Citrix Cloud Japan:
https://wscs-cdn.wsp.citrixcloud.jp/icons
Citrix Cloud Government:
https://wscs-cdn.wsp.cloud.us/icons
Pendo
For in-product messages including new features and critical communications.
https://citrix-cloud-content.customer.pendo.io
Citrix Analytics Service
locus.analytics.cloud.com
Enable access to the appropriate URL from the following list, depending on the tenant’s GEO:
- US:
citrixanalyticseh.servicebus.windows.net - EU:
citrixanalyticseheu.servicebus.windows.net - APS:
citrixanalyticsehaps.servicebus.windows.net
Other Services
For other services that the client may need to connect to, see:
- Client connectivity to Citrix Gateway Service
- Client connectivity to Citrix Secure Private Access service
- Client connectivity to Global App Configuration service
Citrix Federated Authentication Service (FAS)
See Connections between Citrix Federated Authentication Service and Citrix Cloud.
Workspace Environment Management™ service connectivity
Citrix resource location / Cloud Connector / Agent:
https://*.wem.cloud.com
For complete requirements, see Connectivity prerequisites in the Workspace Environment Management service documentation.
In this article
- System requirements
- Supported web browsers
- Transport Layer Security requirements
- Citrix Cloud management console
- License Server connectivity to Citrix Cloud
- Citrix Cloud Connector™
- Citrix Connector™ Appliance for Cloud Services
- Citrix Analytics service connectivity
- NetScaler® Console service connectivity
- Citrix DaaS connectivity
- Endpoint Management service connectivity
- Citrix Gateway service connectivity
- SD-WAN Orchestrator service connectivity
- Remote Browser Isolation (formerly Secure Browser) service
- Client connectivity to Citrix Secure Private Access™
- Client connectivity to Global App Configuration service
- End user connectivity to Citrix Workspace
- Citrix Federated Authentication Service (FAS)
- Workspace Environment Management™ service connectivity