Browser content redirection
Introduction
Browser Content Redirection (BCR) enhances the user experience of web browsing within Citrix Virtual Apps and Desktops™ environments. By offloading the rendering of web pages to the user’s local machine, BCR reduces server load and improves performance, especially for complex or resource-intensive websites.
How it works
BCR utilizes the Citrix Workspace™ app to create a secure browsing environment on the user’s device. When a user accesses an allowed web page, the viewport of the browser window is redirected to the client. The client side browser engine then leverages the local machine’s resources to render the page, resulting in faster loading times and smoother interaction.
Note that only the browser viewport is redirected. The viewport is the rectangular area in your browser where the content is displayed. The viewport doesn’t include things like the Address Bar, Favorites Toolbar, or Status Bar. Those items are in the user interface, which is still running on the browser in the VDA.
Key Benefits
Browser content redirection intelligently manages the web traffic, delivering a superior experience for your users while reducing strain on your infrastructure.
Here’s how they can benefit your organization:
-
Cost Savings: Offload resource-intensive web pages to user devices, freeing up valuable server resources and reducing bandwidth consumption. This translates to lower hardware and network costs.
-
Enhanced User Experience: Provide your users with a smoother, more responsive browsing experience, even with graphics-intensive websites. Deliver native-like performance, eliminating lag and improving productivity.
-
Improved Security: Maintain a secure environment while allowing access to both internal and external resources.
-
Increased Flexibility: Support a wide range of use cases, from basic web browsing to complex web applications that require proxy traversal or SSO authentication. Easily manage redirection settings with granular policy controls in Citrix Web Studio™
System Requirements
Server side components
Citrix Virtual Apps and Desktops
- Long Term Service Release
- Minimum requirements - Any non end-of-life LTSR Citrix Virtual Apps and Desktops release
- Recommended - Citrix Virtual Apps and Desktops 2402 or above
- Current Release
- Minimum requirement - Any non end-of-life CR Citrix Virtual Apps and Desktops release
- Recommended - Latest Citrix Virtual Apps and Desktops release
Browser Components
- Browsers
- Microsoft Edge
- Google Chrome
- Microsoft Edge
-
Note:
For Microsoft Edge, to enable Browser Content Redirection or Bi-directional Content Redirection, ensure you have Virtual Delivery Agent (VDA) version 2503 if you intend to use the Browser redirection extension from the Microsoft Edge Add-ons store. For older VDA versions, you can achieve the same functionality by installing the extension from the Chrome Web Store within your Microsoft Edge browser.
- Browser redirection extension: Published in both Chrome and Edge web stores
- We recommend using the latest version of the browsers for best experience
Note:
To enable Browser Content Redirection or Bi-directional Content Redirection, ensure you have Virtual Delivery Agent (VDA) version 2503 if you intend to use the Browser redirection extension from the Microsoft Edge Add-ons store. For older VDA versions, you can achieve the same functionality by installing the extension from the Chrome Web Store within your Microsoft Edge browser.
Client side components
Windows
- Windows 10 or 11
- Citrix Workspace App
- Minimum Requirement - Any non end-of-life Citrix Workspace App
- Recommended
- Long Term Service Release - Citrix Workspace App for Windows 2402 CU4 or newer, Citrix Workspace App for Windows 2507
- Current Release - Citrix Workspace App 2405 or newer
Note:
-
Browser content redirection is not supported on Citrix Workspace App Windows LTSR releases 1912 and 2203.1
-
Client side browser engine needed for Browser content redirection is installed by default on Citrix Workspace App Current Releases
-
Client side browser engine needed for Browser content redirection is not installed by default on Citrix Workspace App 2402 LTSR release. Administrators can leverage the ADDLOCAL switch to install BCR browser components on top of Citrix Workspace App.
For more details, please refer to Citrix Workspace App Windows documentation.
Linux
- Citrix Workspace App
- Minimum requirement - Any non end-of-life Citrix Workspace App
- Recommended - Citrix Workspace App 2408 or newer For more details, please refer to Citrix Workspace App for Linux documentation
ChromeOS
- Citrix Workspace App
- Latest version from Chrome Web Store
MacOS
- Citrix Workspace App
- Minimum Requirement - Citrix Workspace App for Mac 2411 or newer
Note:
For MacOS, Browser content redirection package is independent of Citrix Workspace App and is always the latest version. Hence, the package will be compatible with multiple CWA versions above the specified minimum version
As the dependency on Citrix Workspace App Mac is not there, Browser Content Redirection version numbering will not match Citrix Workspace App Mac version
Client side browser engine is not packaged with Citrix Workspace App Mac. Download and install the client side for Mac on Citrix Downloads.
Intel and ARM packages are separate. Hence, you need to install the appropriate version that suits the MacOS endpoint
Steps to Configure
- Install the client side and server side components according to the system requirements
- For details on extension deployment, refer Extension deployment section
- Configure the studio policies
- Web studio policies offer a granular way to configure Browser content redirection to suit a variety of use cases
- The basic policies allow the administrator to configure URLs that need to be allowed / not allowed with Browser content redirection
- The URLs can be configured with wild cards
- Open a supported web browser and navigate to an allowed URL
- If the match is found in the allow list, the website will be redirected to the client
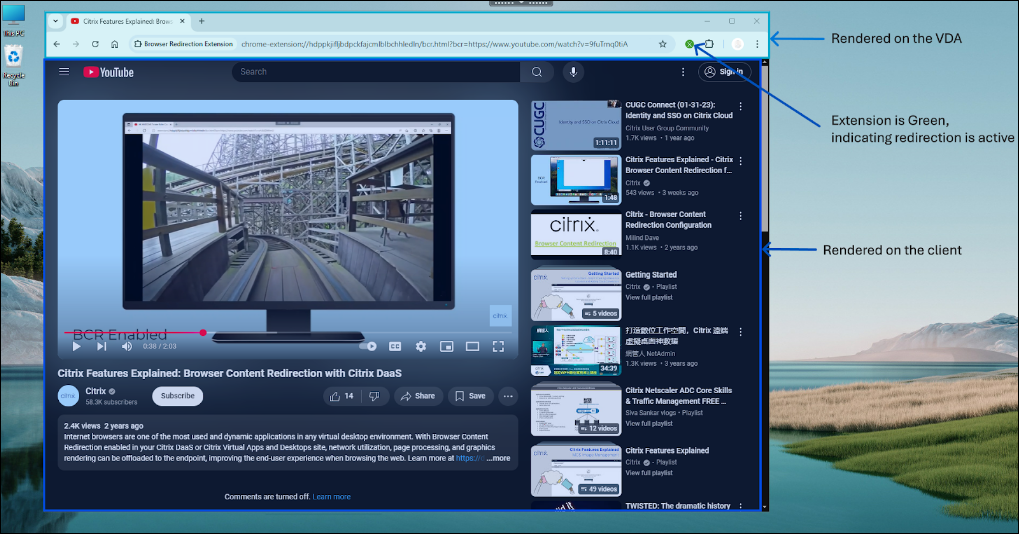
- Citrix Workspace app blends the view port onto the VDA side browser for a seamless experience
- The color of the extension logo specifies the status of the content redirection
- Green: Active and Connected
- Gray: Not active / idle on the current tab
- Red: Broken / Not Working
Note:
HTML5 video redirection and browser content redirection are independent features. The HTML5 video redirection policies aren’t needed for this feature to work. However, the Citrix HDX™ HTML5 Video Redirection Service is used for browser content redirection.
We recommend doing all the configurations through Web Studio and not with registry keys.
Features and Configuration Options
Browser content redirection provides various ways to configure in order to suit the use cases of various customer environments. For detailed information on policy settings, refer Browser content redirection policy settings.
Redirection mechanisms
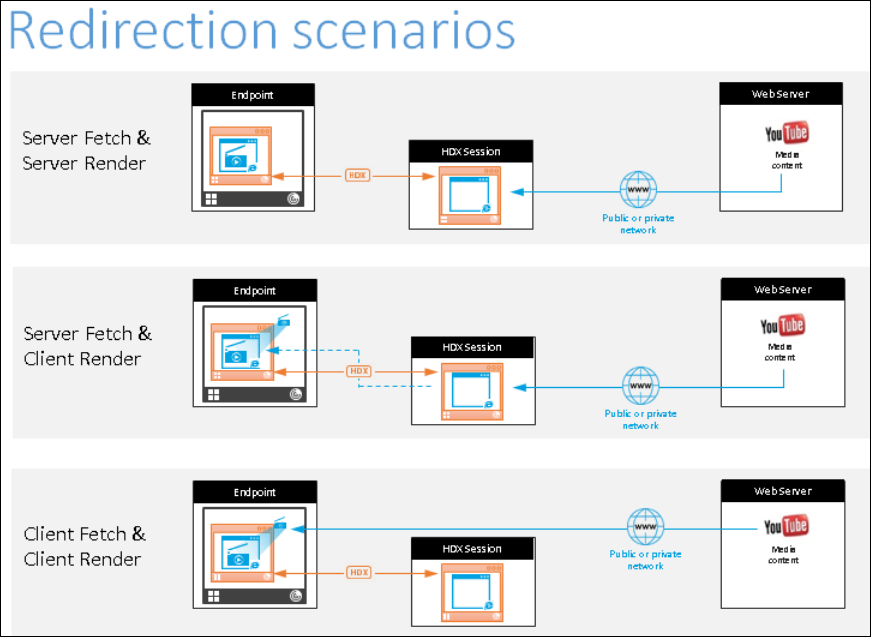
Client fetch client render
By default, Browser content redirection operates in this mode i.e., the client side browser engine reaches out to the web page directly. This requires necessary access from the client network to the web page. Client fetch client render scenario offloads all the network, CPU and RAM usage from Citrix VDA to the client and is the most optimal way to configure Browser content redirection
Policy configuration options
-
Browser content redirection: Allowed
-
Browser content redirection ACL configuration
- Specify the URLs that need to be redirected. By default, YouTube is the only website configured for redirection
-
Browser content redirection block list configuration
- Optional configuration option to block any specific URLs / sub URLs from redirection. Leverage this option with the above to gain maximum customization.
Server fetch client render
In this case, the client side browser engine contacts and fetches content from the web server through the VDA using a virtual channel. This option is useful when the client doesn’t have internet access (for example, thin clients). Low CPU and RAM consumption on the VDA, but bandwidth is consumed on the ICA® virtual channel.
There are three modes of operation in this scenario. The term proxy refers to a proxy device that the VDA accesses to gain Internet access.
Policy configuration options
-
In addition to the policies specified in the Client fetch client render section, configure the following
-
Browser content redirection proxy configuration
- Direct or Transparent: Configure this if you want to leverage server fetch client render and you have direct access or transparent proxy access to the web page from the VDA. The keyword “DIRECT” should be configured in the policy
- Explicit Proxy: Configure this if you want to leverage server fetch client render and you have an explicit proxy access to the web page from the VDA
- PAC files: Configure this if you rely on PAC files browsers in the VDA can automatically choose the appropriate proxy server for fetching a specified URL.
Fallback mode
There might be times when client redirection fails. For example, if the client machine does not have direct internet access, an error response might go back to the VDA. In such cases, the browser on the VDA can then reload and render the page on the server.
You can suppress server rendering of video elements by using the existing Windows Media fallback prevention policy. Set this policy to Play all content only on client or Play only client-accessible content on client. These settings block video elements from playing on the server if there are failures in client redirection. This policy takes effect only when you enable browser content redirection and the Access Control List policy contains the URL that falls back. The URL can’t be in the block list policy.
Authentication handling
Authentication sites
In the current implementation of Browser Content Redirection, regardless of the redirection mechanism, authentication sites need to be configured in order for Browser content redirection to handle log in into websites.
Example:
-
When only https://www.youtube.com/* is configured in Browser content redirection ACL configuration and no authentication sites are configured, BCR will fall back to server side rendering when signing into the website and will continue there.
-
In this case, in order for BCR to handle authentication sites, configure https://www.accounts.google.com/* and any other auth sites such as IdP website as needed. Each website sign in works differently and hence ensure to list
-
When configured, BCR will handle the authentication. For example, with client fetch client render - the authentication will also happen from the client side browser engine for a seamless sign in experience.
Policy configuration options
Configure the Browser content redirection authentication sites policy in addition to the policies mentioned in the redirection mechanisms section
Note:
BCR client side browser does not persist cookies (including authentication) after the redirected window is closed. This would manifest as the need to re-login into websites when BCR windows are completely closed and re-opened.
BCR client side browser does not read cookies from the VDA side browser. Hence, user personalization and preferences don’t synchronize with the VDA browser.
Integrated Windows Authentication
Browser content redirection can provide a seamless way to authenticate to websites when configured with Integrated Windows Authentation (IWA) within the same domain as the VDA.
Policy configuration options
- Configure the Browser content redirection Integrated Windows Authentication support policy
Before enabling single sign-on, complete the following:
-
Configure the Kerberos infrastructure to issue tickets for service principal names (SPNs) constructed from the host name. For example, HTTP/serverhostname.com.
-
For server fetch client render: When you use browser content redirection in server fetch mode, ensure that DNS is configured properly on the VDA.
-
For client fetch client render: When you use browser content redirection in client fetch mode, ensure that DNS is configured properly on the client device and that you allow TCP connections from the overlay to the web server’s IP address.
Proxy Authentication
Browser content redirection can provide a seamless way to authenticate to your web proxy when fetching content from the server. When enabled, Browser Content Redirection will automatically obtain and use a Kerberos service ticket to authenticate with the proxy
Policy configuration options
- Configure the Browser content redirection Server fetch proxy auth policy
Before enabling the server fetch proxy auth policy, complete the following:
- You need to configure your PAC file to route traffic through a downstream web proxy and set up the proxy to use Kerberos authentication
Server-side certificate validation
Browser Content Redirection is further enhanced with certificate validation support. When accessing a redirected website from the client, the client overlay browser may not trust the certificate from the server or the MitM proxy. In such cases, BCR can now validate the Host or Proxy certificates against the VDAs certificate store.
Minimum requirements
This feature is enabled by default, and no configuration is necessary once the below requirements are met:
-
Citrix Virtual Apps and Desktops 2507
-
Citrix Workspace App for Windows 2511
-
Citrix Workspace App for Linux 2511 (Preview)
-
Browser Redirection Extension (Chrome or Edge) 25.11 or later.
Single sign-on support
Browser Content Redirection now offers streamlined user experience with single sign-on support, enabling VDA-side authentication and cookie sharing. This enhancement eliminates redundant logins, boosting productivity by maintaining authentication and cookie persistence across BCR sessions, even after the BCR window is closed. This seamless experience further enhances security by ensuring authentication originates from the VDA, not the client.
For detailed information on the feature, see Single sign-on support section.
Use Cases
Browser Content Redirection (BCR) can be utilized for a wide range of websites, particularly those that are resource-intensive and frequently accessed by enterprises. This includes video streaming platforms like YouTube, which can significantly benefit from offloading rendering to endpoint devices, thereby reducing server load and saving costs. Additionally, BCR is ideal for unified communications applications, such as video conferencing and collaboration tools (Google meet, Teams web, Zoom web) and contact center applications (Genesys cloud), ensuring smooth performance and enhanced user experience. By leveraging BCR, enterprises can optimize their resources and improve efficiency across various web-based applications. Refer CTX238236 for information on how to configure specific websites.
Extension Deployment
Deploy Manually
Browser redirection extension is published in Chrome and Edge web stores. The extension is needed only on the browser on the VDA and not on the client side. To install the extension, navigate to Chrome / Edge webstore, search for Browser redirection extension and Add to the respective browsers. This method works for individual users. To deploy the extension to a large group of users, deploy the extension using group policy
Deploy Using Group Policy
Prerequisites
-
Access: You’ll need administrator privileges on the machine or within your Active Directory environment where you’ll be configuring Group Policy.
-
ADMX Files: Download the Google Chrome ADMX files (administrative templates) for your version of Chrome. You can find these on the Google Chrome Enterprise Help page.
-
Edge Templates: Download the Microsoft Edge administrative templates (ADMX files) from the Microsoft Edge Enterprise landing page.
-
Extension ID and Update URL: The extension ID and update URL for the Citrix Browser Content Redirection extension.
Steps for Google Chrome
- Import ADMX Files:
- Copy the Chrome ADMX files to your central store for administrative templates. This is typically %SystemRoot%\PolicyDefinitions on your domain controller.
- Open Group Policy Management:
- Launch the Group Policy Management Console (gpmc.msc).
- Create or Edit a GPO:
- Either create a new Group Policy Object (GPO) or edit an existing one that applies to the users or computers where you want to deploy the extension.
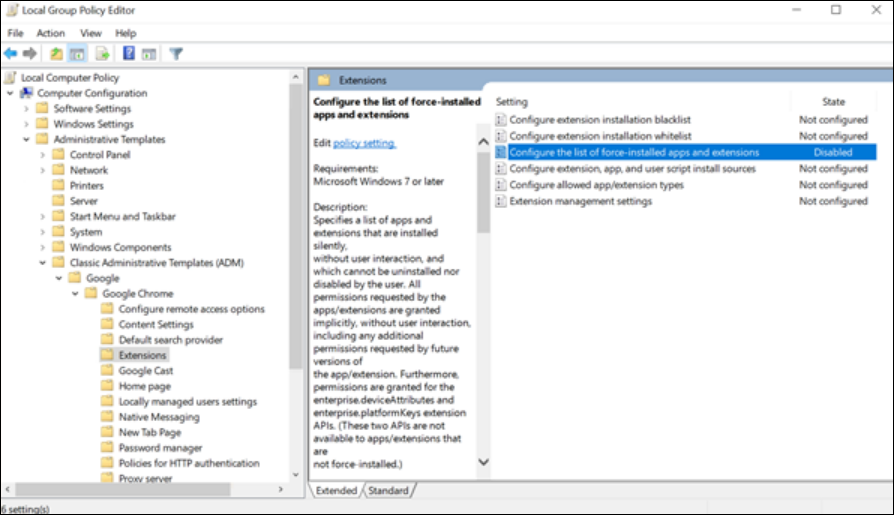
- Navigate to Extensions Settings:
- In the GPO editor, go to:
- User Configuration > Administrative Templates > Classic Administrative Templates (ADM) > Google > Google Chrome > Extensions
- In the GPO editor, go to:
- Enable “Configure the list of force-installed apps and extensions”:
- Double-click this policy setting and select “Enabled.”
- If the Configure the list of force-installed apps and extensions setting is set to Disabled, the extension is automatically removed from Chrome for all users.
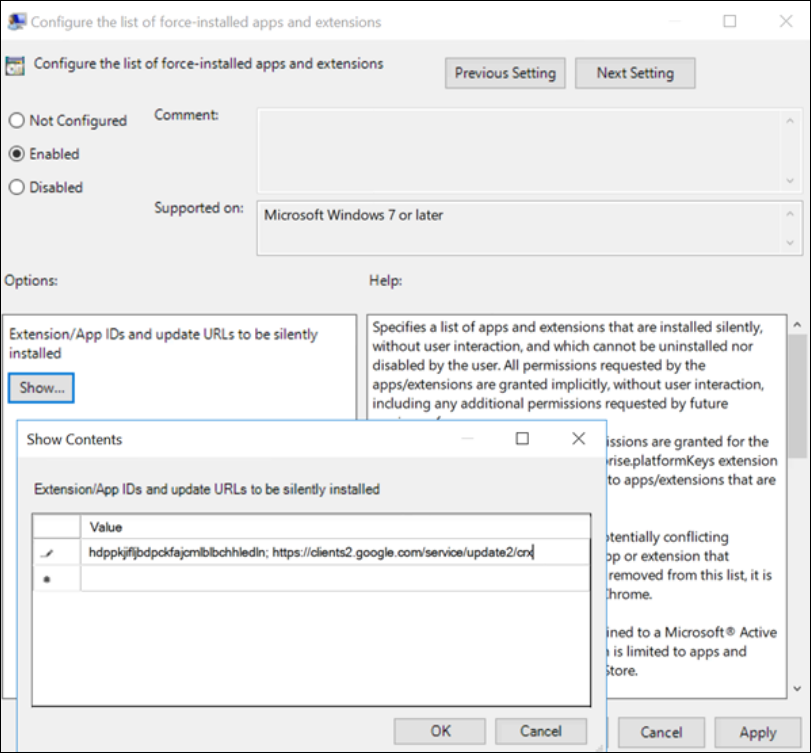
- Add the Extension ID and Update URL:
- Click the “Show” button.
- Enter the extension ID and update URL in the format:
; - Value: hdppkjifljbdpckfajcmlblbchhledln; https://clients2.google.com/service/update2/crx (Update URL)
- Apply the GPO:
- Link the GPO to the appropriate Organizational Unit (OU) in your Active Directory structure.
- Update Group Policy:
- On the target machines, run gpupdate /force to apply the policy immediately, or wait for the policy to update automatically.
Steps for Microsoft Edge
- Import ADMX Files:
- Copy the Edge ADMX files to your central store for administrative templates (%SystemRoot%\PolicyDefinitions).
- Open Group Policy Management:
- Launch the Group Policy Management Console (gpmc.msc).
- Create or Edit a GPO:
- Create a new GPO or edit an existing one.
- Navigate to Extensions Settings:
- In the GPO editor, go to:
- Computer Configuration > Policies > Administrative Templates > Microsoft Edge > Extensions
- In the GPO editor, go to:
- Enable “Control which extensions are installed silently”:
- Double-click this policy setting and select “Enabled.”
- Add the Extension ID and Update URL:
- Click the “Show” button.
- Enter the extension ID and update URL in the format:
; - Value: hdppkjifljbdpckfajcmlblbchhledln; https://clients2.google.com/service/update2/crx (Update URL)
- Apply the GPO:
- Link the GPO to the appropriate Organizational Unit (OU) in your Active Directory structure.
- Update Group Policy:
- On the target machines, run gpupdate /force or wait for the automatic update.
Troubleshooting
For troubleshooting information, see the How to troubleshoot browser content redirection knowledge center article.
Browser Content Redirection Limitations
Server side limitations (VDA)
Browser content redirection cannot support the following use cases. In case an enhancement is required for any mentioned scenarios or new scenarios, please reach out to the Citrix product team.
- Pop-up windows are not supported with Browser content redirection.
- HTML5 video redirection policy must be disabled with Browser content redirection is in use.
- In scenarios of session disconnect / reconnect, the VDA browser window needs to be refreshed in order for BCR to kick in again.
- Printing and file downloads from BCR’ed windows are not supported.
- When using Browser Content redirection with Browser Profile Sharing, SSO persistence with multiple profiles is not supported.
Client side limitations (CWA)
- Browser content redirection is not supported on ARMhf framework.
- Browser content redirection is not supported on ARMhf framework.
- BCR supports a maximum of 25 redirected tabs on one browser and a combined 30 redirected tabs in two browsers.