-
-
Cloud Connector Standalone Citrix Secure Ticketing Authority (STA) service
-
-
-
-
-
This content has been machine translated dynamically.
Dieser Inhalt ist eine maschinelle Übersetzung, die dynamisch erstellt wurde. (Haftungsausschluss)
Cet article a été traduit automatiquement de manière dynamique. (Clause de non responsabilité)
Este artículo lo ha traducido una máquina de forma dinámica. (Aviso legal)
此内容已经过机器动态翻译。 放弃
このコンテンツは動的に機械翻訳されています。免責事項
이 콘텐츠는 동적으로 기계 번역되었습니다. 책임 부인
Este texto foi traduzido automaticamente. (Aviso legal)
Questo contenuto è stato tradotto dinamicamente con traduzione automatica.(Esclusione di responsabilità))
This article has been machine translated.
Dieser Artikel wurde maschinell übersetzt. (Haftungsausschluss)
Ce article a été traduit automatiquement. (Clause de non responsabilité)
Este artículo ha sido traducido automáticamente. (Aviso legal)
この記事は機械翻訳されています.免責事項
이 기사는 기계 번역되었습니다.책임 부인
Este artigo foi traduzido automaticamente.(Aviso legal)
这篇文章已经过机器翻译.放弃
Questo articolo è stato tradotto automaticamente.(Esclusione di responsabilità))
Translation failed!
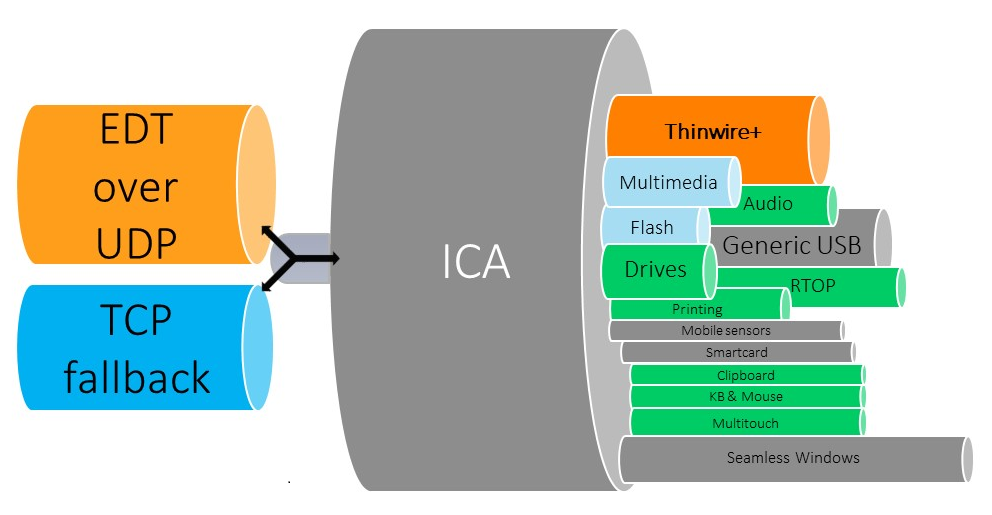
Adaptive transport
Adaptive Transport is a mechanism in Citrix Virtual Apps and Desktops™ that allows establishing connections for HDX sessions using a preferred transport protocol while providing a fallback to TCP if connectivity with the preferred protocol is unavailable.
The following transport protocols are supported:
- Enlightened Data Transport (EDT)
- Transmission Control Protocol (TCP)
Configuration
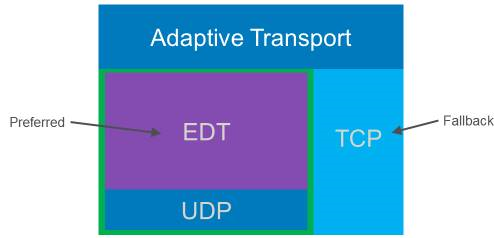
Adaptive Transport is enabled by default. You can configure Adaptive Transport to operate in the following modes:
- Preferred: (Default) The client attempts to connect with the preferred protocol and falls back to TCP if connectivity with the preferred protocol is unavailable.
- Diagnostic mode: The client only attempts to connect using the preferred protocol. Fall back to TCP is disabled.
- Off: The client only attempts to connect using TCP.
How it works
When Adaptive Transport is set to Preferred, the client attempts to connect to the session with both the preferred protocol and TCP in parallel. This allows optimizing the connection time if it’s not possible to connect with the preferred protocol and the client must fall back to using TCP. If the connection is established using TCP, the client attempts to connect with the preferred protocol in the background every five minutes.
When Adaptive Transport is set to Diagnostic mode, the client connects to the session only with the preferred protocol. If the client is unable to establish a connection using the preferred protocol, it doesn’t fall back to using TCP, and the connection fails.
When Adaptive Transport is set to Off, Adaptive Transport is disabled, and the client connects to the session using TCP only.
System requirements
The following are the requirements for using Adaptive Transport and EDT:
- Control plane
- Citrix DaaS (formerly Citrix Virtual Apps™ and Desktops service)
- Citrix Virtual Apps and Desktops: currently supported version
- Virtual Delivery Agent
- Windows: currently supported version (2402 or later is recommended)
- Linux: currently supported version (2402 or later is recommended)
- Citrix Workspace™ app
- Windows: currently supported version (2402 or later is recommended)
- Linux: currently supported version (2402 or later is recommended)
- Mac: currently supported version (2402 or later is recommended)
- iOS: latest version available in the Apple App Store
- Android: latest version available in Google Play
- Citrix NetScaler® Gateway
- 14.1.12.30 or later (recommended)
- 13.1.17.42 or later (13.1-52.19 or later recommended)
Note:
For details on Linux VDA, see the Linux Virtual Delivery Agent documentation.
Network requirements
The following sections are the network requirements for using EDT with Adaptive Transport:
Session hosts
If your session hosts have a firewall such as Windows Defender Firewall, you must allow the following inbound traffic for internal connections.
| Description | Source | Protocol | Port |
|---|---|---|---|
| Internal connection - Session Reliability enabled | Client
|
UDP
|
2598 |
| Internal connection - Session Reliability disabled | 1494 | ||
| Internal connection - HDX™ Direct or VDA SSL | 443 |
Note:
The VDA installer adds the appropriate inbound rules to the Windows Defender Firewall. If you use a different firewall, you must add the rules above.
Internal network
The following table depicts the firewall rules required for using EDT in your network:
| Description | Protocol | Source | Destination | Destination port |
|---|---|---|---|---|
| Direct internal connection - Session Reliability enabled | UDP
|
Client network
|
VDA network
|
2598 |
| Direct internal connection - Session Reliability disabled | 1494 | |||
| Direct internal connection - HDX Direct or VDA SSL | 443 | |||
| NetScaler Gateway | NetScaler SNIP
|
2598 | ||
| NetScaler Gateway - VDA SSL | 443 |
Note:
If you are using Citrix Gateway Service, you must enable Rendezvous to use EDT as your transport protocol. See the Rendezvous documentation for system and network requirements.
Client network
The following table outlines the connectivity requirements for client devices:
| Description | Protocol | Source | Destination | Destination port |
|---|---|---|---|---|
| Internal connection - Session Reliability enabled | UDP
|
Client IP
|
VDA network
|
2598 |
| Internal connection - Session Reliability disabled | 1494 | |||
| Internal connection - HDX Direct or SSL VDA | 443 | |||
| External connection - NetScaler Gateway | NetScaler Gateway public IP address | 443 | ||
| External connection - Citrix Gateway Service | Citrix Gateway Service | 443 |
Note:
If you are using Citrix Gateway Service, clients must be able to reach https://*.*.nssvc.net. If you can’t allow all subdomains using https://*.*.nssvc.net, you can use https://*.c.nssvc.net and https://*.g.nssvc.net instead. For more information, see Knowledge Center article CTX270584.
Share
Share
In this article
This Preview product documentation is Citrix Confidential.
You agree to hold this documentation confidential pursuant to the terms of your Citrix Beta/Tech Preview Agreement.
The development, release and timing of any features or functionality described in the Preview documentation remains at our sole discretion and are subject to change without notice or consultation.
The documentation is for informational purposes only and is not a commitment, promise or legal obligation to deliver any material, code or functionality and should not be relied upon in making Citrix product purchase decisions.
If you do not agree, select I DO NOT AGREE to exit.