Technical security overview
Security overview
This document applies to Citrix DaaS (formerly Citrix Virtual Apps and Desktops service) hosted in Citrix Cloud. This information includes Citrix Virtual Apps Essentials and Citrix Virtual Desktops Essentials.
Citrix Cloud manages the operation of the control plane for Citrix DaaS environments. The control plane includes the Delivery Controllers, management consoles, SQL database, license server, and optionally StoreFront and Citrix Gateway (formerly NetScaler Gateway). The Virtual Delivery Agents (VDAs) hosting the apps and desktops remain under the customer’s control in the data center of their choice, either cloud or on-premises. These components are connected to the cloud service using an agent called the Citrix Cloud Connector. If customers elect to use Citrix Workspace™, they can also choose to use the Citrix Gateway Service instead of running Citrix Gateway within their data center. The following diagram illustrates Citrix DaaS and its security boundaries.
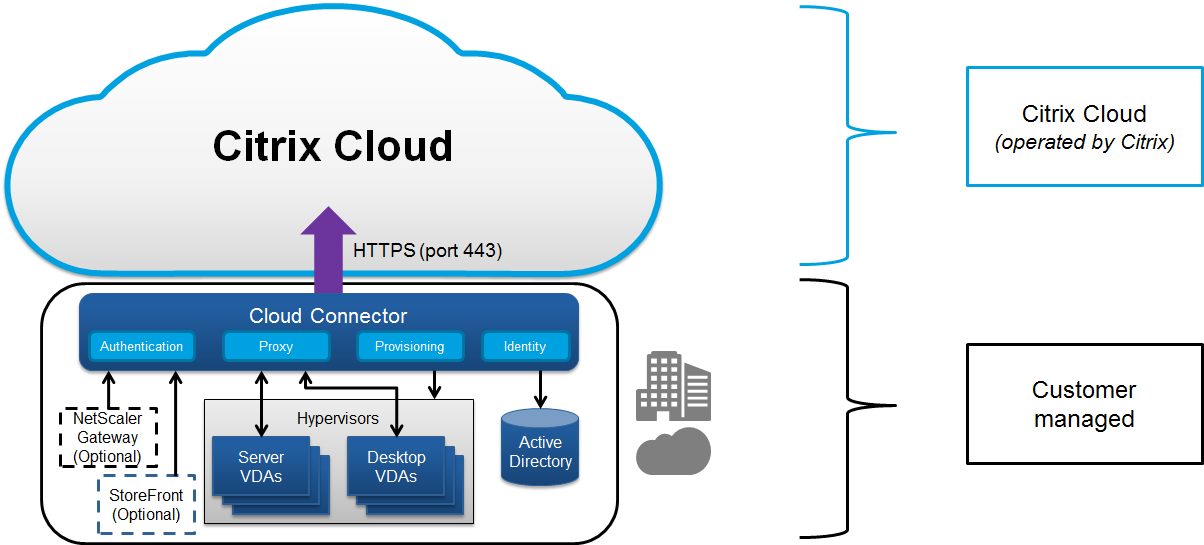
Citrix cloud-based compliance
Visit the Citrix Trust Center for more information regarding Citrix Cloud Certifications, and check back frequently for updates.
Note:
The use of Citrix Managed Azure Capacity with various Citrix DaaS™ editions and Universal Hybrid Multi-Cloud has not been evaluated for Citrix SOC 2 (Type 1 or 2), ISO 27001, HIPAA, or other cloud compliance requirements.
Data flow
Citrix DaaS does not host the VDAs, so the customer’s application data and images required for provisioning are always hosted in the customer setup. The control plane has access to metadata, such as user names, machine names, and application shortcuts, restricting access to the customer’s Intellectual Property from the control plane.
Data flowing between the cloud and customer premises uses secure TLS connections over port 443.
Data isolation
Citrix DaaS stores only the metadata needed for the brokering and monitoring of the customer’s applications and desktops. Sensitive information, including images, user profiles, and other application data remains on the customer premises or in their public cloud vendor’s subscription.
Service editions
The capabilities of Citrix DaaS vary by edition. For example, Citrix Virtual Apps Essentials™ supports only Citrix Gateway service and Citrix Workspace. Consult that product documentation to learn more about supported features.
ICA® Security
Citrix DaaS provides several options for securing ICA traffic in transit. The following are the options available:
- Basic encryption: The default setting.
- Secure HDX™: Allows true end-to-end encryption of session data using AES-256.
- SecureICA: Allows encrypting session data using RC5 (128-bit) encryption.
- HDX Direct: Allows using network-level encryption using TLS/DTLS.
- VDA TLS/DTLS: Allows using network-level encryption using TLS/DTLS.
- Rendezvous protocol: Available only when using the Citrix Gateway Service. When using the Rendezvous protocol, all segments of the ICA sessions’ connections are encrypted using TLS/DTLS.
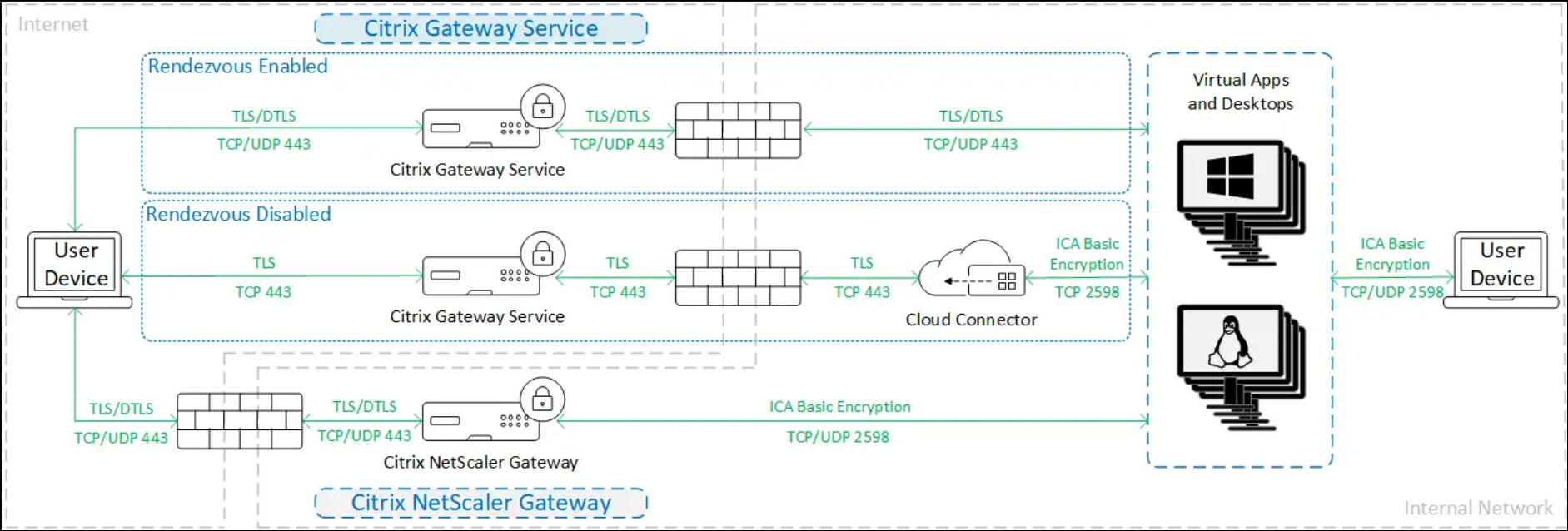
Basic encryption
When using basic encryption, traffic is encrypted as shown in the following diagram.
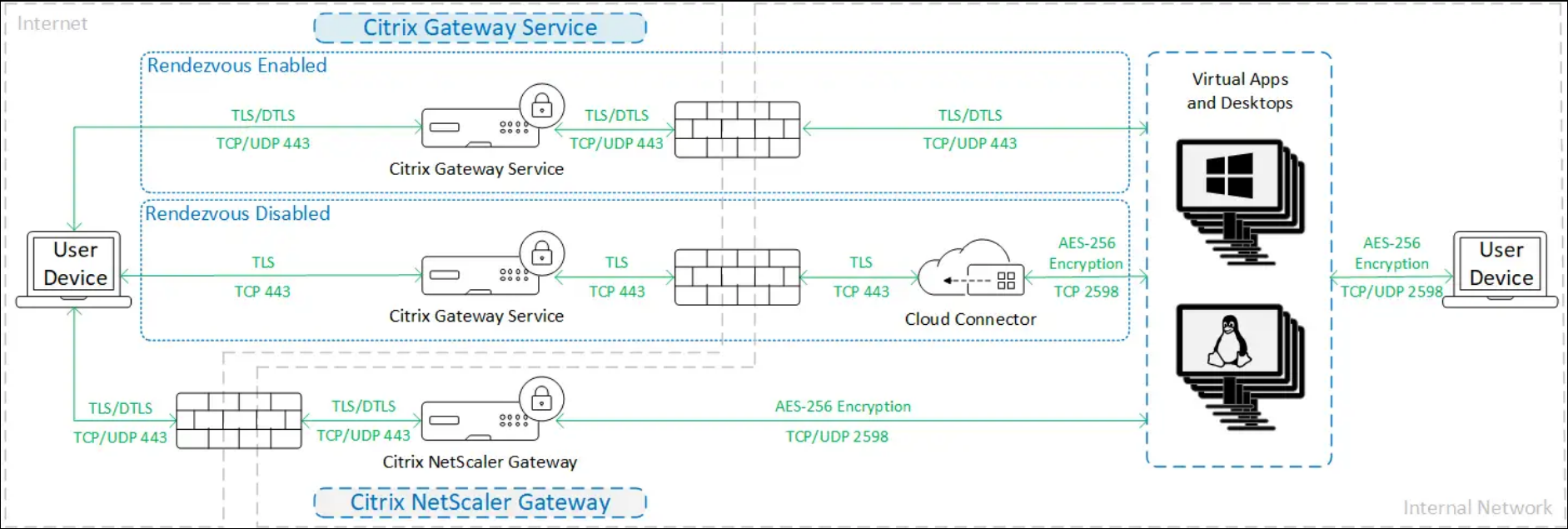
Secure HDX
When using Secure HDX, traffic is encrypted as shown in the following diagram.
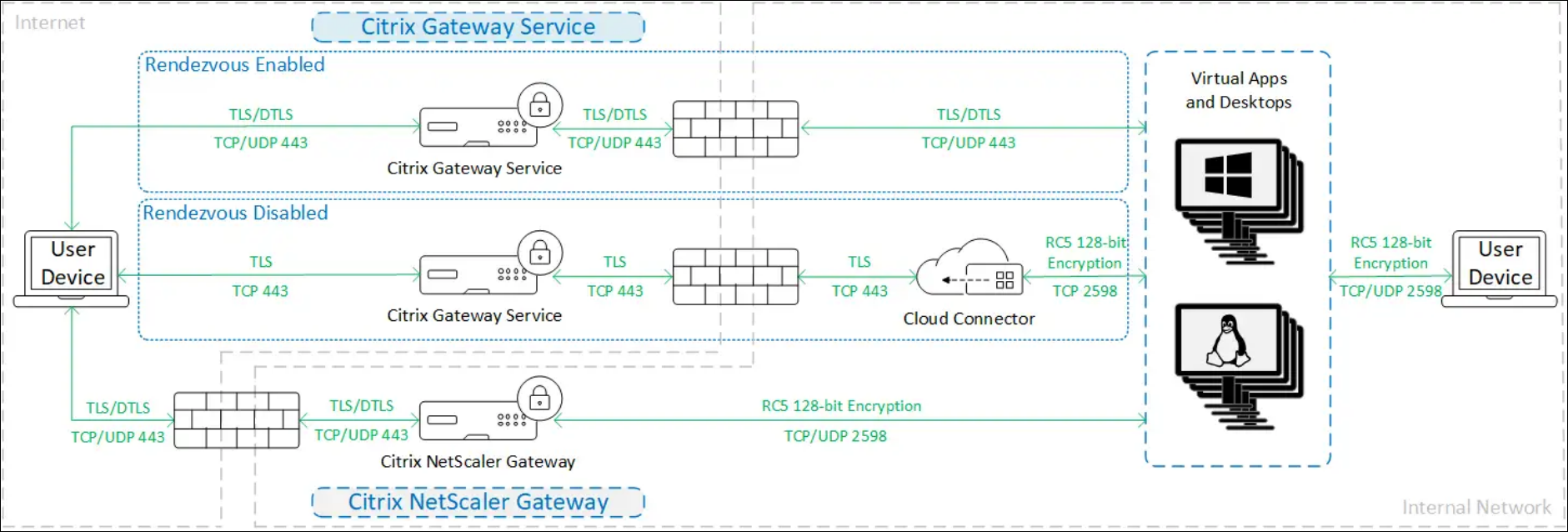
SecureICA
When using SecureICA, traffic is encrypted as shown in the following diagram.
Note:
It is recommended to use Secure HDX instead. Secure ICA was deprecated with the release of Citrix Virtual Apps and Desktops 2402.
SecureICA is not supported when using Workspace app for HTML5.
HDX Direct
Internal
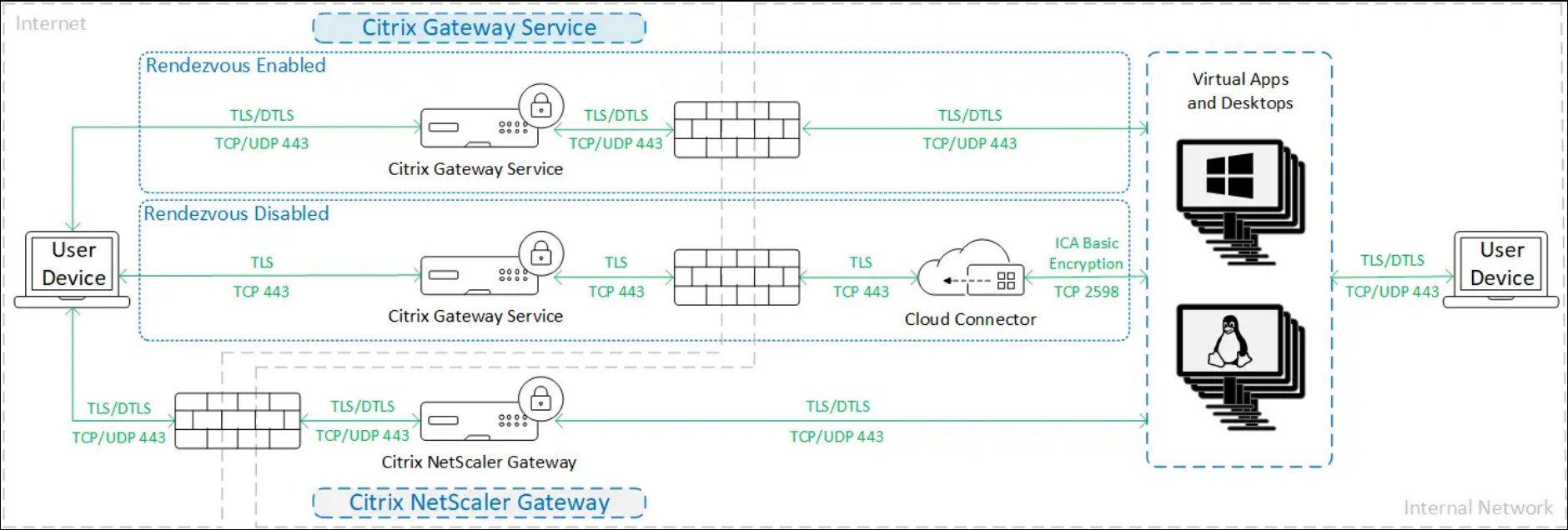
When using HDX Direct in Internal only mode, traffic is encrypted as shown in the following diagram.
External
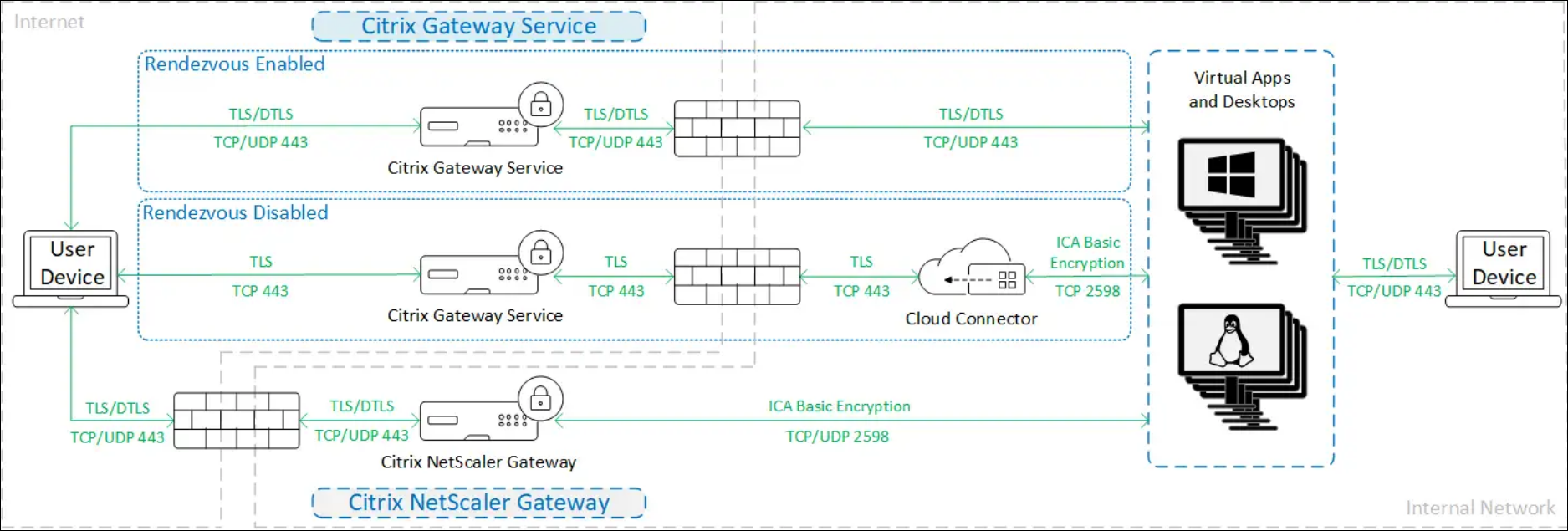
When using HDX Direct in Internal and External mode, traffic is encrypted as shown in the following diagram.
VDA TLS/DTLS
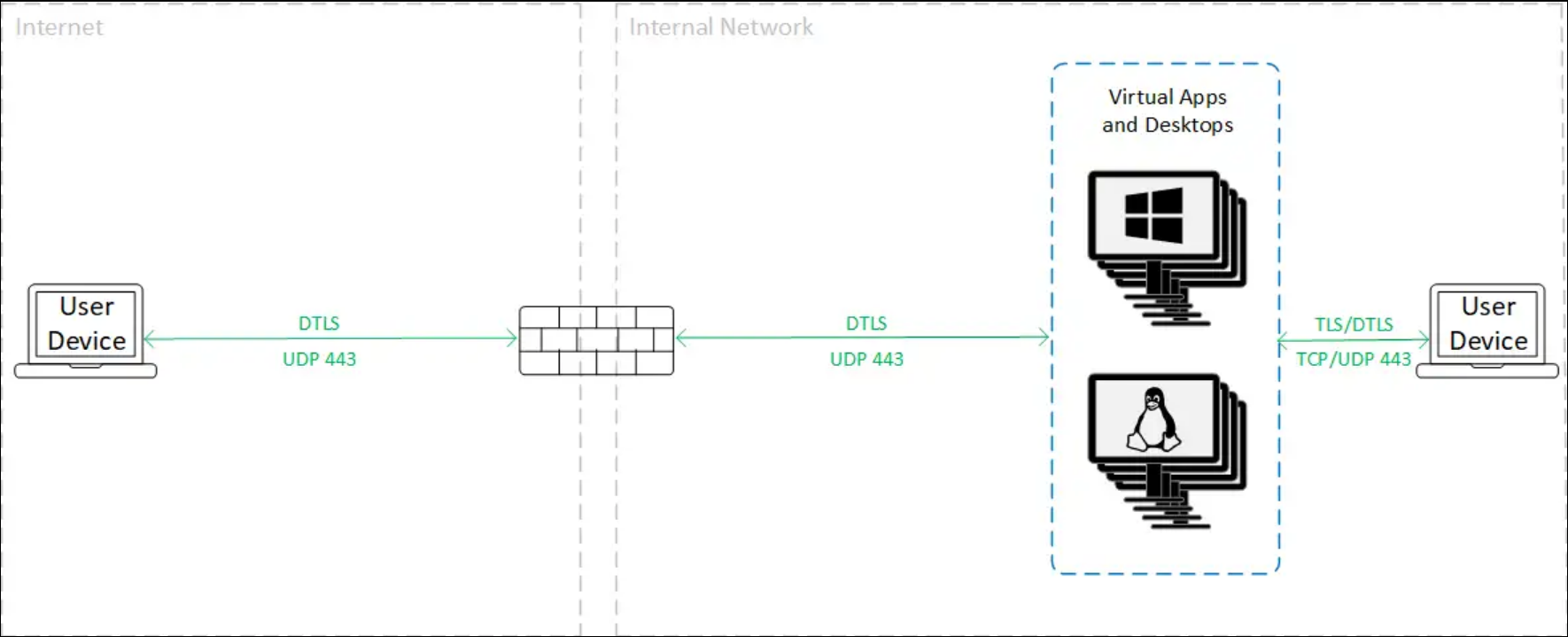
When using VDA TLS/DTLS encryption, traffic is encrypted as shown in the following diagram.
Note:
When using the Gateway Service without Rendezvous, the traffic between the VDA and the Cloud Connector is not TLS encrypted, because the Cloud Connector does not support connecting to the VDA with network-level encryption.
More resources
For more information about the ICA security options and how to configure them, see:
- Secure HDX: Secure HDX
- HDX Direct: HDX Direct
- SecureICA: Security policy settings
- VDA TLS/DTLS: Transport Layer Security
- Rendezvous protocol: Rendezvous protocol
Credential handling
Citrix DaaS handles four types of credentials:
- User Credentials: When users authenticate to Workspace or StoreFront™ using their Active Directory username and password, these are stored to provide single sign on to the VDAs. When using customer-managed StoreFront, these are normally encrypted by the connector before sending to DaaS, for more information see Client access via StoreFront.
- Administrator Credentials: Administrators authenticate against Citrix Cloud. Authentication generates a one-time signed JSON Web Token (JWT) which gives the administrator access to Citrix DaaS.
- Hypervisor Passwords: On-premises hypervisors that require a password for authentication have an administrator-generated password that is directly stored encrypted in the SQL database in the cloud. Citrix manages peer keys to ensure that hypervisor credentials are only available to authenticated processes.
- Active Directory (AD) Credentials: Machine Creation Services™ uses the Cloud Connector for creating machine accounts in a customer’s AD. Because the machine account of the Cloud Connector has only read access to AD, the administrator is prompted for credentials for each machine creation or deletion operation. These credentials are stored only in memory, and are held only for a single provisioning event.
Deployment considerations
Citrix recommends that users consult the published best practices documentation for deploying Citrix Gateway applications and VDAs within their environments.
Cloud Connectors
Communication with Citrix Cloud
All connections from Citrix Cloud Connectors to DaaS and other Citrix Cloud services use HTTPS with TLS 1.2.
HTTPS for XML service and STA
If you use on-premise StoreFront or NetScaler Gateways, it is recommended that you enable HTTPS and disable HTTP on the connector. For more information, see HTTPS Configuration.
Network access requirements
In addition to the ports described at Inbound and outbound ports configuration, Cloud Connectors have the following network access requirements:
- The Citrix Cloud Connectors require only port 443 outbound traffic to the internet, and can be hosted behind an HTTP proxy.
- Within the internal network, the Cloud Connector needs access to the following for Citrix DaaS:
- VDAs: Port 80, both inbound and outbound. plus 1494 and 2598 inbound if using Citrix Gateway service
- StoreFront servers: Port 443 inbound if using HTTPS (recommended) or port 80 if using HTTP (not recommended).
- Citrix Gateways, if configured as a STA: Port 443 inbound if using HTTPS (recommended) or port 80 if using HTTP (not recommended).
- Active Directory domain controllers
- Hypervisors: Outbound only. See Communications Ports Used by Citrix Technologies for specific ports.
Traffic between the VDAs and Cloud Connectors is encrypted using Kerberos message-level security.
Security Keys
You can use Security Keys to ensure that only authorized StoreFront servers and Citrix Gateway appliances are able to connect to DaaS via the cloud connectors. This is especially important if you have enabled XML trust.
Client access
You can provide client access via either Citrix hosted Workspace or by hosting your own StoreFront deployment.
Users can connect to Workspace or StoreFront using either Citrix Workspace app or a web browser. For security recommendations for Citrix Workspace app, see the documentation for each platform.
Client access via Workspace
Citrix Workspace is a Citrix managed service that enables client apps to access DaaS resources without needing any on-premise infrastructure. For supported versions of Citrix Workspace app and other requirements, see Workspace System Requirements. For information on security, see Citrix Workspace security overview.
Client access via StoreFront
As an alternative to Workspace, you can provide client access by deploying Citrix StoreFront in your local environment. This offers greater security configuration options and flexibility for deployment architecture, including the ability to maintain user credentials on-premises. The StoreFront server can be hosted behind a Citrix Gateway to provide secure remote access, enforce multifactor authentication, and add other security features. For more information see Secure your StoreFront deployment.
User credentials
If the user authenticated to StoreFront with their active directory credentials, when a user launches an application, StoreFront passes the credentials to the Cloud Connector. By default the Cloud Connector encrypts user credentials using AES encryption and a random one-time key generated for each launch. The key is never passed into the cloud, and returned only to Citrix Workspace app. The Citrix Workspace app then passes this key to the VDA to decrypt the user password during session launch for a single sign-on experience. The flow is shown in the following figure.
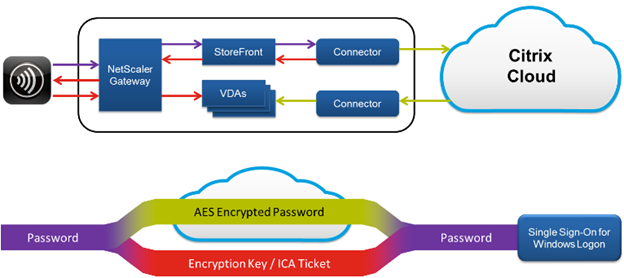
It is important that you configure HTTPS between the client, gateway, storefront and connector to ensure that the password is always encrypted within your network.
With the default behavior, as Citrix Cloud does not have access to the credentials, it is unable to forward the credentials to other Cloud Connectors or Connector Appliances for validation. This is required if you use multiple domains without trust relationships. You can disable this behavior and allow credentials to be uploaded to Citrix cloud so that it can forward them to other cloud connectors and Connector Appliances for validation. To configure this use the DaaS PowerShell SDK cmdlet Set-Brokersite with parameter CredentialForwardingToCloudAllowed.
Connecting to Cloud Connectors using HTTPS
It is recommended that you configure StoreFront to connect to the Cloud Connectors using HTTPS to ensure all communication is encrypted. This requires that you have enabled HTTPS for XML service and STA. To Configure StoreFront to connect using HTTPS, see Add resource feeds for Citrix Desktops as a Service and Add Citrix Gateway appliance.
XML trust
By default, when StoreFront connects to DaaS for actions such as enumeration and launch, StoreFront must pass through the user’s Active Directory credentials so that DaaS can authenticate the user and check the user’s group membership. However when using other authentication methods such as domain pass-through, smart cards or SAML, StoreFront does not have the active directory password. In this case you must enable “XML Trust”. With XML trust enabled, DaaS allows StoreFront to perform actions on behalf of a user such as enumerating and launching applications without validating the user’s password. Before enabling XML trust, use Security Keys or another mechanism such as firewalls or IPsec to ensure that only trusted StoreFront servers are able to connect to the Cloud Connectors.
To enable XML trust in Studio, go to Settings > Site settings and turn on Enable XML trust.
To use the Citrix DaaS SDK to check the XML trust current value, run Get-BrokerSite and inspect the value of TrustRequestsSentToTheXMLServicePort.
To use the Citrix DaaS SDK to enable or disable XML trust, run Set-BrokerSite with parameter TrustRequestsSentToTheXMLServicePort.
Citrix Gateway service
Using the Citrix Gateway service avoids the need to deploy Citrix Gateway within customer data centers.
For details, see Citrix Gateway service.
All TLS connections between the Cloud Connector and Citrix Cloud are initiated from the Cloud Connector to the Citrix Cloud. No in-bound firewall port mapping is required.
On-premise NetScaler® gateway
You can use an on-premise NetScaler gateway to provide access to resources. The Gateway must be able to reach cloud connectors to redeem STA tickets. It is recommended you configure the gateway to connect to the Cloud Connectors using HTTPS, see HTTPS for XML service and STA. If you have enabled Security keys then you must configure the gateway to include the keys.
More information
The following resources contain security information:
-
Citrix Trust Center: The trust center has documentation about standards and certifications that are important in maintaining a secure and compliant IT environment.
-
Secure Deployment Guide for the Citrix Cloud Platform: This guide provides an overview of security best practices when using Citrix Cloud and describes the information Citrix Cloud collects and manages. This guide also contains links to comprehensive information about the Citrix Cloud Connector.
Note:
This document is intended to provide the reader with an introduction to and overview of the security functionality of Citrix Cloud; and to define the division of responsibility between Citrix and customers with regard to securing the Citrix Cloud deployment. It is not intended to serve as a configuration and administration guidance manual for Citrix Cloud or any of its components or services.
In this article
- Security overview
- Citrix cloud-based compliance
- Data flow
- Data isolation
- Service editions
- ICA® Security
- Credential handling
- Deployment considerations
- Cloud Connectors
- Security Keys
- Client access
- Client access via Workspace
- Client access via StoreFront
- Citrix Gateway service
- On-premise NetScaler® gateway
- More information